Abstract
We present methods for implementing arbitrary permutations of qubits under interaction constraints. Our protocols make use of previous methods for rapidly reversing the order of qubits along a path. Given nearest-neighbor interactions on a path of length , we show that there exists a constant such that the quantum routing time is at most , whereas any SWAP-based protocol needs at least time . This represents the first known quantum advantage over swAP-based routing methods and also gives improved quantum routing times for realistic architectures such as grids. Furthermore, we show that our algorithm approaches a quantum routing time of in expectation for uniformly random permutations, whereas SWAP-based protocols require time asymptotically. Additionally, we consider sparse permutations that route qubits and give algorithms with quantum routing time at most on paths and at most on general graphs with radius .
1. Introduction
Qubit connectivity limits quantum information transfer, which is a fundamental task for quantum computing. While the common model for quantum computation usually assumes all-to-all connectivity, proposals for scalable quantum architectures do not have this capability [MK13; Mon +14; Bre+16]. Instead, quantum devices arrange qubits in a fixed architecture that fits within engineering and design constraints. For example, the architecture may be grid-like [MG19; Aru +19] or consist of a network of submodules [MK13; Mon+14]. Circuits that assume all-to-all qubit connectivity can be mapped onto these architectures via protocols for routing qubits, i.e., permuting them within the architecture using local operations.
Long-distance gates can be implemented using SWAP gates along edges of the graph of available interactions. A typical procedure swaps pairs of distant qubits along edges until they are adjacent, at which point the desired two-qubit gate is applied on the target qubits. These swap subroutines can be sped up by parallelism and careful scheduling [SWD11; SSP13; SSP14; PS16; LWD15; Mur+19; ZW19]. Minimizing the sWaP circuit depth corresponds to the Routing ViA Matchings problem [ACG94; CSU19]. The minimal swAP circuit depth to implement any permutation on a graph is given by its routing number, [ACG94]. Deciding is generally NP-hard [BR17], but there exist algorithms for architectures of interest such as grids and other graph products [ACG94; Zha99; CSU19]. Furthermore, one can establish lower bounds on the routing number as a function of graph diameter and other properties.
Routing using SWAP gates does not necessarily give minimal circuit evolution time since it is effectively classical and does not make use of the full power of quantum operations. Indeed, faster protocols are already known for specific permutations in specific qubit geometries such as the path [Rau05; Bap +20]. These protocols tend to be carefully engineered and do not generalize readily to other permutations, leaving open the general question of devising faster-than-SWAP quantum routing. In this paper, we give a positive answer to this question.
Following [Rau05; Bap+20], we consider a continuous-time model of routing, where the protocol is defined by a Hamiltonian that can only include nearest-neighbor interactions. To make consistent comparisons with a gate-based model of routing, we bound the spectral norm of interactions [Bap+20] so that a SWAP gate takes unit time [VHC02], as determined by the canonical form of a two-qubit Hamiltonian [Ben+02]. We suppose that single-qubit operations can be performed arbitrarily fast, a common assumption [VHC02; Ben+02] that is practically well-motivated due to the relative ease of implementing single-qubit rotations.
Rather than directly engineering a quantum routing protocol, we consider a hybrid strategy that leverages a known protocol for quickly performing a specific permutation to implement general quantum routing. Specifically, we consider the reversal operation
| (1) |
that swaps the positions of qubits about the center of a length- path. Fast quantum reversal protocols are known in the gate-based [Rau05] and time-independent Hamiltonian [Bap+20] settings. The reversal operation can be implemented in time [Bap+20]
| (2) |
where is the parity of . Both protocols exhibit an asymptotic time scaling of , which is asymptotically three times faster than the best possible swaP-based time of (bounded by the diameter of the graph) [ACG94]. The odd-even sort algorithm provides a nearly tight time upper bound of [LDM84] and will be our main point of comparison.
The Hamiltonian protocol of [Bap+20] can be understood by looking at the time evolution of the site Majorana operators obtained by a Jordan-Wigner transformation of the spin chain. In this picture, the protocol can be interpreted as the rotation of a fictitious particle of spin whose magnetization components are in one-to-one correspondence with the Majoranas on the chain. A reversal corresponds to a rotation of the large spin by an angle of . The gate-based reversal protocol [Rau05] is a special case of a quantum cellular automaton with a transition function given by the -fold product of nearest-neighbor controlled-Z (CZ) operations—an operation that can be done 3 times faster than a SWAP gate—and Hadamard operations. In an open spin chain, this process spreads out local Pauli observables at site over the chain and “refocuses” them at site in steps for every . The ability to spread local observables (which is present in the gate-based and Hamiltonian protocols but not in SWAP-based protocols) may be key to obtaining a speedup over SWAP-based algorithms.
We expect both the gate-based and Hamiltonian protocols to be implementable on near-term quantum devices. The gate-based protocol uses nearest-neighbor CZ gates and Hadamard gates, both of which are widely used on existing quantum platforms. The Hamiltonian protocol involves nearest-neighbor Pauli XX interactions with non-uniform couplings, which is within the capabilities of, e.g., superconducting architectures [Kja+20].
Routing using reversals has been studied extensively due to its applications in comparative genomics (where it is known as sorting by reversals) [BP93; KS95]. References [Ben+08; PS02; NNN05] present routing algorithms where, much like in our case, reversals have length-weighted costs. However, these models assume reversals are performed sequentially, while we assume independent reversals can be performed in parallel, where the total cost is given by the evolution time, akin to circuit depth. To our knowledge, results from the sequential case are not easily adaptable to the parallel setting and require a different approach.
Routing on paths is a fundamental building block for routing on more general graphs. For example, a two-dimensional grid graph is the Cartesian product of two path graphs, and the best known routing routine applies a path routing subroutine 3 times [ACG94]. A quantum protocol for routing on the path in time , for a constant , would imply a routing time of on the grid. A similar speedup follows for higher-dimensional grids. More generally, routing algorithms for the generalized hierarchical product of graphs can take advantage of faster routing of the path base graph [CSU19]. For other graphs, it is open whether fast reversals can be used to give faster routing protocols for general permutations.
In the rest of this paper, we present the following results on quantum routing using fast reversals. In Section 2, we give basic examples of using fast reversals to perform routing on general graphs to indicate the extent of possible speedup over swAP-based routing, namely a graph for which routing can be sped up by a factor of 3, and another for which no speedup is possible. Section 3 presents algorithms for routing sparse permutations, where few qubits are routed, both for paths and for more general graphs. Here, we obtain the full factor 3 speedup over swAP-based routing. Then, in Section 4, we prove the main result that there is a quantum routing algorithm for the path with worst-case constant-factor advantage over any swAP-based routing scheme. Finally, in Section 5, we show that our algorithm has average-case routing time and any swAP-based protocol has average-case routing time at least .
2. Simple bounds on routing using reversals
Given the ability to implement a fast reversal with cost given by Eq. (2), the largest possible asymptotic speedup of reversal-based routing over swAP-based routing is a factor of 3. This is because the reversal operation, which is a particular permutation, cannot be performed faster than , and can be performed in time classically using odd-even sort. As we now show, some graphs can saturate the factor of 3 speedup for general permutations, while other graphs do not admit any speedup over swaps
Maximal speedup:
For odd, let denote two complete graphs, each on vertices, joined at a single “junction” vertex for a total of vertices (Figure 1a). Consider a permutation on in which every vertex is sent to the other complete subgraph, except that the junction vertex is sent to itself. To route with SWAPs, note that each vertex (other than that at the junction) must be moved to the junction at least once, and only one vertex can be moved there at any time. Because there are non-junction vertices on each subgraph, implementing this permutation requires a SWAP-circuit depth of at least .
Figure 1:

admits the full factor of 3 speedup in the worst case when using reversals over swAPs, whereas admits no speedup when using reversals over SWAPS.
On the other hand, any permutation on can be implemented in time using reversals. First, perform a reversal on a path that connects all vertices with opposite-side destinations. After this reversal, every vertex is on the side of its destination and the remainder can be routed in at most 2 steps [ACG94]. The total time is at most , exhibiting the maximal speedup by an asymptotic factor of 3.
No speedup:
Now, consider the complete graph on vertices, (Figure 1b). Every permutation on can be routed in at most time 2 using swAPs [ACG94]. Consider implementing a 3-cycle on three vertices of for using reversals. Any reversal sequence that implements this permutation will take at least time 2. Therefore, no speedup is gained over swAPs in the worst case.
We have shown that there exists a family of graphs that allows a factor of 3 speedup for any permutation when using fast reversals instead of SWAPs, and others where reversals do not grant any improvement. The question remains as to where the path graph lies on this spectrum. Faster routing on the path is especially desirable since this task is fundamental for routing in more complex graphs.
3. An algorithm for sparse permutations
We now consider routing sparse permutations, where only a small number of qubits are to be moved. For the path, we show that the routing time is at most . More generally, we show that for a graph of radius , the routing time is at most . (Recall that the radius of a graph is , where is the distance between and in .) Our approach to routing sparse permutations using reversals is based on the idea of bringing all qubits to be permuted to the center of the graph, rearranging them, and then sending them to their respective destinations.

3.1. Paths
A description of the algorithm on the path, called MiddleExchange, appears in Algorithm 3.1. Figure 2 presents an example of MiddleExchange for .
Figure 2:

Example of MiddleExchange (Algorithm 3.1) on the path for .
In Theorem 3.1, we prove that Algorithm 3.1 achieves a routing time of asymptotically when implementing a sparse permutation of qubits on the path graph. First, let denote the set of permutations on , so !. Then, for any permutation that acts on a set of labels , let denote the destination of label under . We may then write . Let denote an ordered series of reversals , and let be the concatenation of two reversal series. Finally, let and denote the result of applying and to a sequence , respectively, and let denote the length of the reversal , i.e., the number of vertices it acts on.
Theorem 3.1.
Let with (i.e., elements are to be permuted, and elements begin at their destination). Then Algorithm 3.1 routes in time at most .
Proof.
Algorithm 3.1 consists of three steps: compression (Line 4–Line 9), inner permutation (Line 11), and dilation (Line 12). Notice that compression and dilation are inverses of each other.
Let us first show that Algorithm 3.1 routes correctly. Just as in the algorithm, let denote the labels with such that , that is, the elements that do not begin at their destination and need to be permuted. It is easy to see that these elements are permuted correctly: After compression, the inner permutation step routes to the current location of the label in the middle. Because dilation is the inverse of compression, it will then route every to its correct destination. For the non-permuting labels, notice that they lie in the support of either no reversal or exactly two reversals, in the compression step and in the dilation step. Therefore reverses the segment containing the label and re-reverses it back into place (so ). Therefore, the labels that are not to be permuted end up exactly where they started once the algorithm is complete.
Now we analyze the routing time. Let for . As in the algorithm, let be the largest index for which . Then, for , we have , and, for , we have . Moreover, we have and . From all reversals in the first part of Algorithm 3.1, , consider those that are performed on the left side of the median (position of the path). The routing time of these reversals is
| (3) |
By a symmetric argument, the same bound holds for the compression step on the right half of the median. Because both sides can be performed in parallel, the total cost for the compression step is at most . The inner permutation step can be done in time at most using odd-even sort. The cost to perform the dilation step is also at most because dilation is the inverse of compression. Thus, the total routing time for Algorithm 3.1 is at most . □
It follows that sparse permutations on the path with can be implemented using reversals with a full asymptotic factor of 3 speedup.
3.2. General graphs
We now present a more general result for implementing sparse permutations on an arbitrary graph.
Theorem 3.2.
Let be a graph with radius and a permutation of vertices. Let . Then can be routed in time at most .
Proof.
We route using a procedure similar to Algorithm 3.1, consisting of the same three steps adapted to work on a spanning tree of : compression, inner permutation, and dilation. Dilation is the inverse of compression and the inner permutation step can be performed on a subtree consisting of just nodes by using the Routing ViA MATCHings algorithm for trees in time [Zha99]. It remains to show that compression can be performed in time.
We construct a token tree that reduces the compression step to routing on a tree. Let be a vertex in the center of , i.e., a vertex with distance at most to all vertices. Construct a shortest-path tree of rooted at , say, using breadth-first search. We assign a token to each vertex in . Now is the subtree of formed by removing all vertices for which the subtree rooted at does not contain any tokens, as depicted in Figure 3. In , call the first common vertex between paths to from two distinct tokens an intersection vertex, and let be the set of all intersection vertices. Note that if a token lies on the path from another token to , then the vertex on which lies is also an intersection vertex. Since has at most leaves, .
Figure 3:

Illustration of the token tree in Theorem 3.2 for a case where is the 5 × 5 grid graph. Blue circles represent vertices in and orange circles represent vertices not in . Vertex denotes the center of . Red-outlined circles represent intersection vertices. In particular, note that one of the blue vertices is an intersection because it is the first common vertex on the path to of two distinct blue vertices.
For any vertex in , let the descendants of be the vertices in whose path on to includes . Now let be the subtree of rooted at , i.e., the tree composed of and all of the descendants of . We say that all tokens have been moved up to a vertex if for all vertices in without a token, also does not contain a token. The compression step can then be described as moving tokens up to .

We describe a recursive algorithm for doing so in Algorithm 3.2. The base case considers the trivial case of a subtree with only one token. Otherwise, we move all tokens on the subtrees of descendant up to the closest intersection using recursive calls as illustrated in Figure 4. Afterwards, we need to consider whether the path between and has enough room to store all tokens. If it does, we use a Routing via Matchings algorithm for trees to route tokens from onto , followed by a reversal to move these tokens up to . Otherwise, the path is short enough to move all tokens up to by the same Routing via Matchings algorithm.
Figure 4:

An example of moving the tokens in up to (Line 14-Line 18 in Algorithm 3.2).
We now bound the routing time on of MoveUpTo , for any vertex . First note that all operations on subtrees of are independent and can be performed in parallel. Let be the sequence of intersection vertices that MoveUpTo(·) is recursively called on that dominates the routing time of MoveUpTo . Let , for , be the distance of to the furthest leaf node in . Assuming that the base case on Line 2 has not been reached, we have a routing time of
| (4) |
where bounds the time required to route tokens on a tree of size at most following the recursive MoveUpTo call [Zha99]. We expand the time cost of recursive calls until we reach the base case of to obtain
| (5) |
Since and , this shows that compression can be performed in time. □
In general, a graph with radius and diameter will have . Using Theorem 3.2, this implies that for a graph and a sparse permutation with , the bound for the routing time will be between and . Thus, for such sparse permutations, using reversals will always asymptotically give us a constant-factor worst-case speedup over any swAP-only protocol since . Furthermore, for graphs with , we can asymptotically achieve the full factor of 3 speedup.
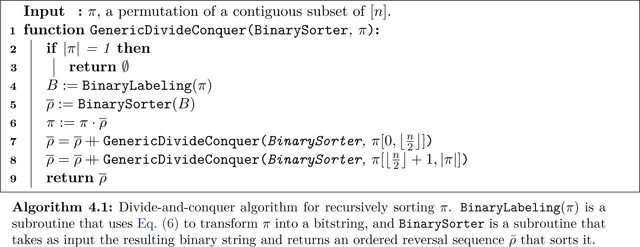
4. Algorithms for routing on the path
Our general approach to implementing permutations on the path relies on the divide-and-conquer strategy described in Algorithm 4.1. It uses a correspondence between implementing permutations and sorting binary strings, where the former can be performed at twice the cost of the latter. This approach is inspired by [PS02] and [Ben+08] who use the same method for routing by reversals in the sequential case.
First, we introduce a binary labeling using the indicator function
| (6) |
This function labels any permutation by a binary string . Let be the target permutation, and any permutation such that . Then it follows that divides into permutations , acting only on the left and right halves of the path, respectively, i.e., . We find and implement via a binary sorting subroutine, thereby reducing the problem into two subproblems of length at most that can be solved in parallel on disjoint sections of the path. Proceeding by recursion until all subproblems are on sections of length at most 1, the only possible permutation is the identity and has been implemented. Because disjoint permutations are implemented in parallel, the total routing time is .
We illustrate Algorithm 4.1 with an example, where the binary labels are indicated below the corresponding destination indices:
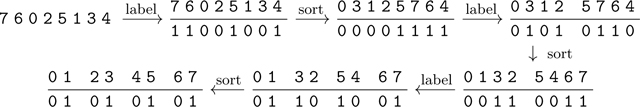 |
(7) |
Each labeling and sorting step corresponds to an application of Eq. (6) and BinarySorter, respectively, to each subproblem. Specifically, in Eq. (7), we use TBS (Algorithm 4.2) to sort binary strings.

We present two algorithms for BinarySorter, which perform the work in our sorting algorithm. The first of these binary sorting subroutines is Tripartite Binary Sort (TBS, Algorithm 4.2). TBS works by splitting the binary string into nearly equal (contiguous) thirds, recursively sorting these thirds, and merging the three sorted thirds into one sorted sequence. We sort the outer thirds forwards and the middle third backwards which allows us to merge the three segments using at most one reversal. For example, we can sort a binary string as follows:
 |
(8) |
where the arrows with TBS indicate recursive calls to TBS and the bracket indicates the reversal to merge the segments. Let GDC (TBS) denote Algorithm 4.1 when using TBS to sort binary strings, where GDC stands for GenericDivideConquer.
The second algorithm is an adaptive version of TBS (Algorithm 4.3) that, instead of using equal thirds, adaptively chooses the segments’ length. Adaptive TBS considers every pair of partition points, , that would split the binary sequence into two or three sections: , , and (where corresponds to no middle section). For each pair, it calculates the minimum cost to recursively sort the sequence using these partition points. Since each section can be sorted in parallel, the total sorting time depends on the maximum time needed to sort one of the three sections and the cost of the final merging reversal. Let GDC(ATBS) denote Algorithm 4.1 when using Adaptive TBS to sort binary strings.
Notice that the partition points selected by TBS are considered by the Adaptive TBS algorithm and are selected by Adaptive TBS only if no other pair of partition points yields a faster sorting time. Thus, for any permutation, the sequence of reversals found by Adaptive TBS costs no more than that found by TBS. However, TBS is simpler to implement and will be faster than Adaptive TBS in finding the sorting sequence of reversals.

4.1. Worst-case bounds
In this section, we prove that all permutations of sufficiently large length can be sorted in time strictly less than using reversals. Let denote the number of times character appears in a binary string , and let (resp., ) denote the best possible sorting time to sort (resp., implement ) with reversals. Assume all logarithms are base 2 unless specified otherwise.
Lemma 4.1.
Let such that , where and . Then, .
Proof.
To achieve this upper bound, we use TBS (Algorithm 4.2). There are steps in the recursion, which we index by , with step 0 corresponding to the final merging step. Let denote the size of the longest reversal in recursive step that merges the three sorted subsequences of size . The size of the final merging reversal can be bounded above by because is maximized when every is contained in the leftmost third if or the rightmost third if . So we have
| (9) |
| (10) |
where we used for . □
Now we can prove a bound on the cost of a sorting series found by Adaptive TBS for any binary string of length .
Theorem 4.2.
For all bit strings of arbitrary length , , where .
Proof.
Let for some . Partition into three sections such that and . Since where , we write for the purposes of this proof. Recall that if segments and are sorted forwards and segment is sorted backwards, the resulting segment can be sorted using a single reversal, (see the example in Eq. (8)). Then we have
| (11) |
where is the time to sort backwards using reversals.
We proceed by induction on . For the base case, it suffices to note that every binary string can be sorted using reversals and, for finitely many values of , any time needed to sort a binary string of length exceeding can be absorbed into the term. Now assume for all , .
Case 1:
or . In this case, , so
| (12) |
by the induction hypothesis.
Case 2:
and . In this case, adjust the partition such that and consequently , as depicted in Figure 5. In this adjustment, at most zeros are added to the segment and likewise with ones to . Thus, . Since , we have
| (13) |
Let . Applying Lemma 4.1 with this value of yields
| (14) |
Since , we obtain the same bound by applying Lemma 4.1 with the same value of .
Figure 5:

Case 2 of Theorem 4.2. If there are few zeros and ones in the leftmost and rightmost thirds, respectively, we can shorten the middle section so that it can be sorted quickly. Then, because each of the outer thirds contain far more zeros than ones (or vice versa), they can both can be sorted quickly as well.
By the inductive hypothesis, can be bounded above by
| (15) |
Using Eq. (11) and the fact that , we get the bound
as claimed. □
This bound on the cost of a sorting series found by Adaptive TBS for binary sequences can easily be extended to a bound on the minimum sorting sequence for any permutation of length .
Corollary 4.3.
For a length-n permutation .
Proof.
To sort , we turn it into a binary string using Eq. (6). Then let be a sequence of reversals to sort . If we apply the sequence to get , every element of will be on the same half as its destination. We can then recursively perform the same procedure on each half of , continuing down until every pair of elements has been sorted.
This process requires steps, and at step , there are binary strings of length being sorted in parallel. This gives us the following bound to implement :
| (16) |
where . Applying the bound from Theorem 4.2, we obtain
5. Average-case performance
So far we have presented worst-case bounds that provide a theoretical guarantee on the speedup of quantum routing over classical routing. However, the bounds are not known to be tight, and may not accurately capture the performance of the algorithm in practice.
In this section we show better performance for the average-case routing time, the expected routing time of the algorithm on a permutation chosen uniformly at random from . We present both theoretical and numerical results on the average routing time of swap-based routing (such as odd-even sort) and quantum routing using TBS and ATBS. We show that on average, GDC (TBS) (and GDC (ATBS), whose sorting time on any instance is at least as fast) beats swap-based routing by a constant factor . We have the following two theorems, whose proofs can be found in Appendices A and B, respectively.
Theorem 5.1.
The average routing time of any SWAP-based procedure is lower bounded by .
Theorem 5.2.
The average routing time of GDC(TBS) is for a constant .
These theorems provide average-case guarantees, yet do not give information about the non-asymptotic behavior. Therefore, we test our algorithms on random permutations for instances of intermediate size.
Our numerics [KSS21] show that Algorithm 4.1 has an average routing time that is well-approximated by , where , using TBS or Adaptive TBS as the binary sorting subroutine, for permutations generated uniformly at random. Similarly, the performance of odd-even sort (OES) is well-approximated by . Furthermore, the advantage of quantum routing is evident even for fairly short paths. We demonstrate this by sampling 1000 permutations uniformly from for , and running OES and GDC(TBS) on each permutation. Due to computational constraints, GDC(ATBS) was run on sample permutations for lengths . On an Intel i7–6700HQ processor with a clock speed of 2.60 GHz, OES took about 0.04 seconds to implement each permutation of length 512; GDC(TBS) took about 0.3 seconds; and, for permutations of length 200, GDC(ATBS) took about 6 seconds.
The results of our experiments are summarized in Figure 6. We find that the mean normalized time costs for OES, GDC(TBS), and GDC(ATBS) are similar for small , but the latter two decrease steadily as the lengths of the permutations increase while the former steadily increases. Furthermore, the average costs for GDC(TBS) and GDC(ATBS) diverge from that of OES rather quickly, suggesting that GDC(TBS) and GDC(ATBS) perform better on average for somewhat small permutations as well as asymptotically.
Figure 6:

The mean routing time and fit of the mean routing time for odd-even sort (OES), and routing algorithms using Tripartite Binary Sort (GDC(TBS)) and Adaptive TBS (GDC (ATBS)). We exhaustively search for and sample 1000 permutations uniformly at random otherwise. We show data for GDC(ATBS) only for because it becomes too slow after that point. We find that the fit function fits the data with an (all three algorithms). For OES, the fit gives ; for GDC(TBS), ; and for GDC(ATBS), . Similarly, for the standard deviation, we find that the fit function fits the data with (all three algorithms), suggesting that the normalized deviation of the performance about mean scales as asymptotically.
The linear coefficient of the fit of for OES is , which is consistent with the asymptotic bound proven in Theorems 5.1 and 5.2. For the fit of the mean time costs for GDC(TBS) and GDC(ATBS), we have and respectively. The numerics suggest that the algorithm routing times agree with our analytics, and are fast for instances of realistic size. For example, at , GDC(TBS) and GDC(ATBS) have routing times of and , respectively. On the other hand, OES routes in average time . For larger instances, the speedup approaches the full factor of monotonically. Moreover, the fits of the standard deviations suggest asymptotically, which implies that as permutation length increases, the distribution of routing times gets relatively tighter for all three algorithms. This suggests that the average-case routing time may indeed be representative of typical performance for our algorithms for permutations selected uniformly at random.
6. Conclusion
We have shown that our algorithm, GDC(ATBS) (i.e., Generic Divide-and-Conquer with Adaptive TBS to sort binary strings), uses the fast state reversal primitive to outperform any sWAP-based protocol when routing on the path in the worst and average case. Recent work shows a lower bound on the time to perform a reversal on the path graph of , where [Bap+20]. Thus we know that the routing time cannot be improved by more than a factor over SwAPs, even with new techniques for implementing reversals. However, it remains to understand the fastest possible routing time on the path. Clearly, this is also lower bounded by . Our work could be improved by addressing the following two open questions: (i) how fast can state reversal be implemented, and (ii) what is the fastest way of implementing a general permutation using state reversal?
We believe that the upper bound in Corollary 4.3 can likely be decreased. For example, in the proof of Lemma 4.1, we use a simple bound to show that the reversal sequence found by GDC(TBS) sorts binary strings with fewer than ones sufficiently fast for our purposes. It is possible that this bound can be decreased if we consider the reversal sequence found by GDC(ATBS) instead. Additionally, in the proof of Theorem 4.2, we only consider two pairs of partition points: one pair in each case of the proof. This suggests that the bound in Theorem 4.2 might be decreased if the full power of GDC(ATBS) could be analyzed.
Improving the algorithm itself is also a potential avenue to decrease the upper bound in Corollary 4.3. For example, the generic divide-and-conquer approach in Algorithm 4.1 focused on splitting the path exactly in half and recursing. An obvious improvement would be to create an adaptive version of Algorithm 4.1 in a manner similar to GDC(ATBS) where instead of splitting the path in half, the partition point would be placed in the optimal spot. It is also possible that by going beyond the divide-and-conquer approach, we could find faster reversal sequences and reduce the upper bound even further.
Our algorithm uses reversals to show the first quantum speedup for unitary quantum routing. It would be interesting to find other ways of implementing fast quantum routing that are not necessarily based on reversals. Other primitives for rapidly routing quantum information might be combined with classical strategies to develop fast general-purpose routing algorithms, possibly with an asymptotic scaling advantage. Such primitives might also take advantage of other resources, such as long-range Hamiltonians or the assistance of entanglement and fast classical communication.
Acknowledgements
We thank William Gasarch for organizing the REU-CAAR program that made this project possible.
A.B. and A.V.G. acknowledge support by the DoE ASCR Quantum Testbed Pathfinder program (award number de-sc0019040), ARO MURI, DoE ASCR Accelerated Research in Quantum Computing program (award number de-sc0020312), U.S. Department of Energy award number de-sc0019449, NSF PFCQC program, AFOSR, and AFOSR MURI. A.M.C. and E.S. acknowledge support by the U.S. Department of Energy, Office of Science, Office of Advanced Scientific Computing Research, Quantum Testbed Pathfinder program (award number de-sc0019040) and the U.S. Army Research Office (MURI award number W911NF-16–1-0349). S.K. and H.S. acknowledge support from an NSF REU grant, REU-CAAR (CNS-1952352). E.S. acknowledges support from an IBM Ph.D. Fellowship.
A. Average routing time using only SWAPs
In this section, we prove Theorem 5.1. First, define the infinity distance to be . Note that . Finally, define the set of permutations of length with infinity distance at most to be .
The infinity distance is crucially tied to the performance of odd-even sort, and indeed, any SWAP-based routing algorithm. For any permutation of length , the routing time of any SWAP-based algorithm is bounded below by , since the element furthest from its destination must be swapped at least times, and each of those swAPs must occur sequentially. To show that the average routing time of any SWAP-based protocol is asymptotically at least , we first show that for all .
Schwartz and Vontobel [SV17] present an upper bound on that was proved in [Klø08] and [TS10]:
Lemma A.1.
For all , , where
| (17) |
Proof.
Note that . For the case of , refer to [Klø08] for a proof. For the case of , refer to [TS10] for a proof. □
Lemma A.2.
| (18) |
Proof.
This follows from well-known precise bounds for Stirling’s formula:
| (19) |
| (20) |
(see for example [Rob55]). □
With Lemmas A.1 and A.2 in hand, we proceed with the following theorem:
Theorem A.3.
For all , . In other words, the proportion of permutations of length with infinity distance less than vanishes asymptotically.
Proof.
Lemma A.1 implies that . The constraint stipulates that we are in the regime where , since . Then we use Lemma A.2 to simplify any factorials that appear. Substituting Eq. (17) and simplifying, we have
| (21) |
We note that terms can be bounded by
| (22) |
since . Now we have
| (23) |
| (24) |
| (25) |
| (26) |
| (27) |
Since for , this vanishes in the limit of large . □
Now we prove the theorem.
Proof of Theorem 5.1.
Let denote the average routing time of any SWAP-based protocol. Consider a random permutation drawn uniformly from . Due to Theorem A.3, will belong in with vanishing probability, for all . Therefore, for any fixed as , . This translates to an average routing time of at least because we have, asymptotically, for all such . □
B. Average routing time using TBS
In this section, we prove Theorem 5.2, which characterizes the average-case performance of TBS (Algorithm 4.2). This approach consists of two steps: a recursive call on three equal partitions of the path (of length each), and a merge step involving a single reversal.
We denote the uniform distribution over a set as . The set of all -bit strings is denoted , where . Similarly, the set of all -bit strings with Hamming weight is denoted . For simplicity, assume that is even. We denote the runtime of TBS on by .
When running GDC(TBS) on a given permutation , the input bit string for TBS is , where the indicator function is defined in Eq. (6). We wish to show that, in expectation over all permutations , the corresponding bit strings are quick to sort. First, we show that it suffices to consider uniformly random sequences from .
Lemma B.1.
If , then .
Proof.
We use a counting argument. The number of permutations such that is , since we can freely assign index labels from to the 0 bits of , and from to the 1 bits of . Therefore, for a uniformly random and arbitrary ,
| (28) |
Therefore, . □
While is easier to work with than , the constraint on the Hamming weight still poses an issue when we try to analyze the runtime recursively. To address this, Lemma B.2 below shows that relaxing from to does not affect expectation values significantly.
We give a recursive form for the runtime of TBS. We use the following convention for the substrings of an arbitrary -bit string : if is divided into 3 segments, we label the segments from left to right. Subsequent thirds are labeled analogously by ternary fractions. For example, the leftmost third of the middle third is denoted , and so on. Then, the runtime of TBS on string can be bounded by
| (29) |
where is the bitwise complement of bit string and denotes the Hamming weight of . Logically, the first term on the right-hand side is a recursive call to sort the thirds, while the second term is the time taken to merge the sorted subsequences on the thirds using a reversal. Each term can be broken down recursively until all subsequences are of length 1. This yields the general formula
| (30) |
where indicates the empty string.
Lemma B.2.
Let and . Then
| (31) |
where is a constant.
The intuition behind this lemma is that by the law of large numbers, the deviation of the Hamming weight from is subleading in , and the TBS runtime does not change significantly if the input string is altered in a subleading number of places.
Proof.
Consider an arbitrary bit string , and apply the following transformation. If , then flip ones chosen uniformly randomly to zero. If , flip zeros to ones. Call this stochastic function . Then, for all , , and for a random string , we claim that . In other words, maps the uniform distribution on to the uniform distribution on .
We show this by calculating the probability , for arbitrary . A string can map to under only if and disagree in the same direction: if, WLOG, , then must take value 1 wherever , disagree (and 0 if ). We denote this property by . The probability of picking a uniformly random such that with disagreements between them is , since . Next, the probability that maps to is . Combining these, we have
| (32) |
| (33) |
| (34) |
| (35) |
Therefore, . Thus, allows us to simulate the uniform distribution on starting from the uniform distribution on .
Now we bound the runtime of TBS on in terms of the runtime on a fixed . Fix some . We know that , and suppose . Since differs from in at most places, then at level of the TBS recursion (see Eq. (30)), the runtimes of and differ by at most . This is because the runtimes can differ by at most two times the length of the subsequence. Therefore, the total runtime difference is bounded by
| (36) |
| (37) |
| (38) |
| (39) |
On the other hand, if , we simply bound the runtime by that of OES, which is at most .
Now consider and . Since has the binomial distribution , where is the sum of Bernoulli random variables with success probability , the Chernoff bound shows that deviation from the mean is exponentially suppressed, i.e.,
| (40) |
Therefore, the deviation in the expectation values is bounded by
| (41) |
where is a constant. Finally, we conclude that
| (42) |
as claimed. □
Next, we prove the main result of this section, namely, that the runtime of GDC(TBS) is up to additive subleading terms.
Proof of Theorem 5.2.
We first prove properties for sorting a random -bit string and then apply this to the problem of sorting using Lemmas B.1 and B.2.
The expected runtime for TBS can be calculated using the recursive formula in Eq. (30):
| (43) |
The summand contains an expectation of a maximum over Hamming weights of i.i.d. uniformly random substrings of length , which is equivalent to a binomial distribution where we have Bernoulli trials with success probability . Because of independence, if we sample , then . Using Lemma B.3 with , the expected maximum can be bounded by
| (44) |
since the second term is largest when . Therefore,
| (45) |
Lemma B.2 then gives .
The routing algorithm GDC(TBS) proceeds by calling TBS on the full path, and then in parallel on the two disjoint sub-paths of length . We show that the distributions of the left and right halves are uniform if the input permutation is sampled uniformly as . There exists a bijective mapping such that for any since
| (46) |
In particular, can be defined so that specifies which entries are taken to the first positions—say, without changing the relative ordering of the entries mapped to the first positions or the entries mapped to the last positions—and and specify the residual permutations on the first and last positions, respectively. Given , TBS only has access to . After sorting, TBS can only perform deterministic permutations , on the left and right halves, respectively, that depend only on . Thus TBS performs the mappings and on the output. Now it is easy to see that when , the output is also uniform because the TBS mapping is independent of the relative permutations on the left and right halves.
More generally, we see that a uniform distribution over permutations is mapped to two uniform permutations on the left and right half, respectively. Symbolically, for, , we have that
| (47) |
As shown earlier, given uniform distributions over left and right permutations, the output is also uniform. By induction, all permutations in the recursive steps are uniform.
We therefore get a sum of expected TBS runtime on bit strings of lengths , i.e.,
| (48) |
where, by Lemma B.1 and the uniformity of permutations in recursive calls, we need only consider and we bound the expected runtime using Lemma B.2 with . □
We end with a lemma about the order statistics of binomial random variables used in the proof of the main theorem.
Lemma B.3.
Given i.i.d. samples from the binomial distribution with , and , the maximum satisfies
| (49) |
Proof.
We use Hoeffding’s inequality for the Bernoulli random variable , which states that
| (50) |
Pick , where is a constant. For this choice, we have
| (51) |
for every . Then the probability that is identical to the probability that for every , which for i.i.d is given by
| (52) |
Using Bernoulli’s inequality ( for ), we can simplify the above bound to
| (53) |
Finally, we bound the expected value of by an explicit weighted sum over its range:
| (54) |
| (55) |
| (56) |
| (57) |
| (58) |
Since for ,
| (59) |
as claimed. □
References
- [ACG94].Alon N, Chung FRK, and Graham RL “Routing Permutations on Graphs via Matchings”. In: SIAM Journal on Discrete Mathematics 7.3 (1994), pp. 513–530. DOI: 10.1137/s0895480192236628. [DOI] [Google Scholar]
- [Aru+19].Arute F et al. “Quantum supremacy using a programmable superconducting processor”. In: Nature 574.7779 (2019), pp. 505–510. DOI: 10.1038/s41586-019-1666-5. [DOI] [PubMed] [Google Scholar]
- [BP93].Bafna V and Pevzner PA “Genome rearrangements and sorting by reversals”. In: Proceedings of 1993 IEEE 34th Annual Foundations of Computer Science. 1993, pp. 148–157. DOI: 10.1137/S0097539793250627. [Google Scholar]
- [BR17].Banerjee I and Richards D “New Results on Routing via Matchings on Graphs”. In: Fundamentals of Computation Theory. Lecture Notes in Computer Science 10472. Springer, 2017, pp. 69–81. DOI: 10.1007/978-3-662-55751-8_7. [DOI] [Google Scholar]
- [Bap+20].Bapat A, Schoute E, Gorshkov AV, and Childs AM Nearly optimal time-independent reversal of a spin chain. 2020. arXiv: 2003.02843v1 [quant–ph]. [Google Scholar]
- [Ben+08].Bender MA, Ge D, He S, Hu H, Pinter RY, Skiena S, and Swidan F “Improved bounds on sorting by length-weighted reversals”. In: Journal of Computer and System Sciences 74.5 (2008), pp. 744–774. DOI: 10.1016/j.jcss.2007.08.008. [DOI] [Google Scholar]
- [Ben+02].Bennett CH, Cirac JI, Leifer MS, Leung DW, Linden N, Popescu S, and Vidal G “Optimal simulation of two-qubit Hamiltonians using general local operations”. In: Physical Review A 66.1 (2002). DOI: 10.1103/physreva.66.012305. [DOI] [Google Scholar]
- [Bre+16].Brecht T, Pfaff W, Wang C, Chu Y, Frunzio L, Devoret MH, and Schoelkopf RJ “Multilayer microwave integrated quantum circuits for scalable quantum computing”. In: npj Quantum Information 2.16002 (2016). DOI: 10.1038/npjqi.2016.2. [DOI] [Google Scholar]
- [CSU19].Childs AM, Schoute E, and Unsal CM “Circuit Transformations for Quantum Architectures”. In: 14th Conference on the Theory of Quantum Computation, Communication and Cryptography (TQC 2019). Vol. 135. Leibniz International Proceedings in Informatics (LIPIcs). Schloss Dagstuhl–Leibniz-Zentrum fuer Informatik, 2019, 3:1–3:24. DOI: 10.4230/LIPIcs.TQC.2019.3. [DOI] [Google Scholar]
- [KS95].Kececioglu J and Sankoff D “Exact and approximation algorithms for sorting by reversals, with application to genome rearrangement”. In: Algorithmica 13.1–2 (1995), pp. 180–210. DOI: 10.1007/BF01188586. [DOI] [Google Scholar]
- [KSS21].King S, Schoute E, and Shastri H reversal-sort. 2021. URL: https://gitlab.umiacs.umd.edu/amchilds/reversal-sort. [DOI] [PMC free article] [PubMed]
- [Kja+20].Kjaergaard M, Schwartz ME, Braumüller J, Krantz P, Wang JI-J, Gustavsson S, and Oliver WD “Superconducting qubits: Current state of play”. In: Annual Review of Condensed Matter Physics 11 (2020), pp. 369–395. DOI: 10.1146/annurev-conmatphys-031119-050605. [DOI] [Google Scholar]
- [Klø08].Kløve T Spheres of Permutations under the Infinity Norm–Permutations with limited displacement. Research rep. 376. Department of Informatics, University of Bergen, Norway, 2008. URL: http://www.ii.uib.no/publikasjoner/texrap/pdf/2008-376.pdf. [Google Scholar]
- [LDM84].Lakshmivarahan S, Dhall SK, and Miller LL “Parallel Sorting Algorithms”. In: vol. 23. Advances in Computers. Elsevier, 1984, pp. 321–323. DOI: 10.1016/S0065-2458(08)60467-2. [DOI] [Google Scholar]
- [LWD15].Lye A, Wille R, and Drechsler R “Determining the minimal number of swap gates for multi-dimensional nearest neighbor quantum circuits”. In: The 20th Asia and South Pacific Design Automation Conference. IEEE, 2015, pp. 178–183. DOI: 10.1109/aspdac.2015.7059001. [DOI] [Google Scholar]
- [MG19].McClure D and Gambetta J Quantum computation center opens. Tech. rep. IBM, 2019. URL: https://www.ibm.com/blogs/research/2019/09/quantum-computation-center/ (visited on 03/30/2020).
- [MK13].Monroe C and Kim J “Scaling the Ion Trap Quantum Processor”. In: Science 339.6124 (2013), pp. 1164–1169. DOI: 10.1126/science.1231298. [DOI] [PubMed] [Google Scholar]
- [Mon+14].Monroe C, Raussendorf R, Ruthven A, Brown KR, M0061unz P, Duan L-M, and Kim J “Large-scale modular quantum-computer architecture with atomic memory and photonic interconnects”. In: Physical Review A 89.2 (2014). DOI: 10.1103/physreva.89.022317. [DOI] [Google Scholar]
- [Mur+19].Murali P, Baker JM, Abhari AJ, Chong FT, and Martonosi M “Noise-Adaptive Compiler Mappings for Noisy Intermediate-Scale Quantum Computers”. In: ASPLOS ‘19. Proceedings of the Twenty-Fourth International Conference on Architectural Support for Programming Languages and Operating Systems. The Association for Computing Machinery, 2019, pp. 1015–1029. DOI: 10.1145/3297858.3304075. [Google Scholar]
- [NNN05].Nguyen TC, Ngo HT, and Nguyen NB “Sorting by Restricted-Length-Weighted Reversals”. In: Genomics, Proteomics & Bioinformatics 3.2 (2005), pp. 120–127. DOI: 10.1016/S1672-0229(05)03016-0. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [PS16].Pedram M and Shafaei A “Layout Optimization for Quantum Circuits with Linear Nearest Neighbor Architectures”. In: IEEE Circuits and Systems Magazine 16.2 (2016), pp. 62–74. DOI: 10.1109/MCAS.2016.2549950. [DOI] [Google Scholar]
- [PS02].Pinter R and Skiena S “Genomic sorting with length-weighted reversals”. In: Genome informatics. International Conference on Genome Informatics 13 (2002), pp. 103–11. DOI: 10.11234/gi1990.13.103. [DOI] [PubMed] [Google Scholar]
- [Rau05].Raussendorf R “Quantum computation via translation-invariant operations on a chain of qubits”. In: Physical Review A 72.5 (2005). DOI: 10.1103/physreva.72.052301. [DOI] [Google Scholar]
- [Rob55].Robbins H “A remark on Stirling’s formula”. In: The American Mathematical Monthly 62.1 (1955), pp. 26–29. DOI: 10.2307/2315957. [DOI] [Google Scholar]
- [SWD11].Saeedi M, Wille R, and Drechsler R “Synthesis of quantum circuits for linear nearest neighbor architectures”. In: Quantum Information Processing 10.3 (2011), pp. 355–377. DOI: 10.1007/s11128-010-0201-2. [DOI] [Google Scholar]
- [SV17].Schwartz M and Vontobel PO “Improved Lower Bounds on the Size of Balls Over Permutations With the Infinity Metric”. In: IEEE Transactions on Information Theory 63.10 (2017), pp. 6227–6239. DOI: 10.1109/TIT.2017.2697423. [DOI] [Google Scholar]
- [SSP13].Shafaei A, Saeedi M, and Pedram M “Optimization of Quantum Circuits for Interaction Distance in Linear Nearest Neighbor Architectures”. In: Proceedings of the 50th Annual Design Automation Conference. DAC ‘13. ACM, 2013, 41:1–41:6. DOI: 10.1145/2463209.2488785. [Google Scholar]
- [SSP14].Shafaei A, Saeedi M, and Pedram M “Qubit placement to minimize communication overhead in 2D quantum architectures”. In: 2014 19th Asia and South Pacific Design Automation Conference (ASP-DAC). IEEE, 2014. DOI: 10.1109/aspdac.2014.6742940. [Google Scholar]
- [TS10].Tamo I and Schwartz M “Correcting Limited-Magnitude Errors in the Rank-Modulation Scheme”. In: IEEE Transactions on Information Theory 56.6 (2010), pp. 2551–2560. DOI: 10.1109/TIT.2010.2046241. [DOI] [Google Scholar]
- [VHC02].Vidal G, Hammerer K, and Cirac JI “Interaction Cost of Nonlocal Gates”. In: Physical Review Letters 88.23 (2002), p. 237902. DOI: 10.1103/PhysRevLett.88.237902. [DOI] [PubMed] [Google Scholar]
- [Zha99].Zhang L “Optimal Bounds for Matching Routing on Trees”. In: SIAM Journal on Discrete Mathematics 12.1 (1999), pp. 64–77. DOI: 10.1137/s0895480197323159. [DOI] [Google Scholar]
- [ZW19].Zulehner A and Wille R “Compiling SU(4) quantum circuits to IBM QX architectures”. In: ASP-DAC ‘19. Proceedings of the 24th Asia and South Pacific Design Automation Conference. ACM Press, 2019, pp. 185–190. DOI: 10.1145/3287624.3287704. [Google Scholar]


