Summary
Aiming at the problem of insufficient security of image encryption technology, a secure image encryption algorithm using chaos-based block permutation and weighted bit planes chain diffusion is proposed, which is based on a variant structure of classical permutation-diffusion. During the permutation phase, the encryption operations of dividing an image into sub-block, block scrambling, block rotation and block inversion, negative-positive transformation, color component shuffling are performed sequentially with chaotic sequences of plaintext association. In the chain diffusion stage, different encryption strategies are adopted for the high and low 4-bit planes according to the weight of image information. Theoretical analyses and empirical results substantiate that the algorithm conforms to the cryptographic requirements of confusion, diffusion, and avalanche effects, while possessing excellent numerical statistical properties with a large cryptographic space. Therefore, the cryptanalysis-propelled security enhancement mechanism proposed in this paper effectively amplifies the aptitude of the algorithm to withstand cryptographic attacks.
Subject areas: Physics, Quantum theory
Graphical abstract

Highlights
-
•
The proposed encryption algorithm can effectively resist the chosen-plaintext attack
-
•
Bit level is used as the basic unit of image encryption to ensure higher level of security
-
•
Chaos-based dynamic block permutation achieves good confusion with low complexity
-
•
The receiver can decrypt the message without transmitting additional plaintext related keys
Physics; Quantum theory
Introduction
Today, a variety of emerging information technologies are developing by leaps and bounds. As individuals revel in the dividends of information technologies, latent security concerns are progressively unveiled. The exploration of reliable and efficient security algorithms is gaining significance in the big data environment.1,2,3 In the era of big data, the secure transmission of digital images has emerged as a pivotal concern, garnering substantial academic attention. Ensuring that these images remain confidential during transmission, safeguarding against theft or leakage has become a prominent research focus.4,5,6 However, due to the distinctiveness of digital images,7,8,9 such as high correlation of adjacent pixel points, scattering distribution of critical information, and high information redundancy, cryptographic protection using traditional text encryption algorithms struggles to meet real-time performance requirements. Furthermore, chaos itself exhibits inherent qualities10,11,12,13 such as high sensitivity to initial conditions and control parameters, excellent pseudo-randomness, ergodicity, and long-term unpredictability of orbits, and it has many similarities with confusion, diffusion, and so on in cryptography.14,15,16,17 Hence, in the context of the big data era, it is crucial to explore the image encryption algorithm that is firmly rooted in chaos theory.18,19,20,21
Throughout the international research status,22,23,24,25 exploration of chaotic image encryption algorithms26,27,28,29 has been going through more than 20 years. In as early as 1998, Fridrich30 firstly reported the use of chaotic system to encrypt digital images. In recent years, numerous scholars have dedicated their efforts to this field, leading to significant progress and enrichment in the theory and methods of chaotic image encryption.31,32,33 Various new mechanisms and methods are introduced into chaotic image encryption to enhance the security of the algorithm and elevate the performance of secure transmission. Zheng et al.34 in 2022 outlined an image encryption technique that uses cascaded chaotic maps and an extended zigzag transform. The simulation results demonstrate that the algorithm provides fast encryption, high security, and effective protection to withstand a broad spectrum of attacks. In 2023, Jiang et al.35 introduced an image encryption algorithm based on a two-dimensional Chebyshev logistic infinite collapse map. The results provide a solid foundation and practical solutions for chaos generation and image encryption.36,37,38,39 These achievements mean that many encryption algorithms have shown satisfactory results in several areas,40,41,42,43 which have significantly advanced the field of information security technology.44,45,46,47 However, as society develops, the exponential growth of information poses significant challenges to previous algorithms.48,49,50,51 The limitations of these algorithms become increasingly prominent.52,53,54,55
Most previous algorithms perform operations at the pixel level, and the granularity of their encryption units is coarse. To meet this challenge, there has been significant interest in chaotic image encryption methods employing bit plane decomposition56,57,58 in recent years. Numerous encryption algorithms based on bit planes have been proposed, garnering widespread attention. Bit planes decomposition is an algorithm that divides a digital image by bit to obtain eight subgraphs and encrypts each of these subgraphs independently. Although some progress has been made in chaotic image encryption research, the designed algorithms still have certain limitations due to the existing defects in bit encryption. In 2019, Shafique et al.59 introduced an encryption algorithm that incorporates binary bit plane extraction and multiple chaotic maps. The system comprises two parts, bit-level permutation of the high 4-bit planes and bitwise XOR diffusion. They presented several security analyses and experimental simulations demonstrating the system’s ability to withstand various attacks. However, the study found that the diffusion and permutation components could be separately attacked using a divide-and-conquer approach, highlighting their inherent vulnerabilities.60 In 2020, a novel image encryption algorithm leveraging DNA coding and spatiotemporal chaos was unveiled.61 The algorithm involves a sequential implementation of pixel diffusion, DNA encoding, DNA base permutation, and DNA decoding to create a cipher image from a plaintext image. However, this algorithm ultimately represents a fusion of fixed DNA base permutation and bit complement. Consequently, the algorithm can be compromised by chosen-plaintext attacks and chosen-ciphertext attacks. From a security perspective, existing bit-level chaotic encryption algorithms need further improvement, mainly because 1) the present algorithms are susceptible to chosen-plaintext attacks or chosen-ciphertext attacks as the key employed for generating chaotic sequences lacks correlation with the original image; 2) the granularity of encryption units of existing algorithms is coarse; 3) existing bit planes decomposition algorithms do not consider the correlation between each sliced plane after decomposition.
This paper presents a secure image encryption algorithm that utilizes chaos-based block permutation and weighted bit planes chain diffusion. The proposed algorithm is based on a variant structure of classical permutation-diffusion, which first performs a block permutation based on chaotic sequences yet executes a bit-level chain diffusion. During the permutation phase, the encryption operations of dividing an image into sub-block, block scrambling, block rotation and block inversion, negative-positive transformation, color component shuffling are performed sequentially based on the chaotic sequences of plaintext association. In the bit-level diffusion stage, the high and low 4-bit planes are encrypted according to the information weight contained in the image. A chain-substitution-diffusion encryption with bit-by-bit planes is adopted for the high 4-bit planes, followed by a lightweight encryption for the low 4-bit planes. Among them, the intermediate ciphertext association mechanism is used in all the diffusion encryption processes. Thus, the algorithm possesses the prowess to fend off both known-plaintext attack and chosen-plaintext attack due to the closed-loop feedback of plaintext and ciphertext. The primary contributions and innovations of this study are delineated as follows.
-
a.
The existing image encryption algorithms are not structured rationally enough, which leads to their insufficient security against plaintext-type attacks. For this reason, this color image encryption algorithm proposes a plaintext and intermediate ciphertext association mechanism and also adopts chain diffusion to effectively enhance the resistance to cryptographic attacks.
-
b.
Pixel-level image encryption is so coarse in granularity that it is not secure enough, and traditional bit-level encryption is too complex to meet the efficiency requirements. To cope with these challenges, this paper proposes a new strategy. We adopt an elastic processing unit in the weighted bit plane, which effectively balances the tension between security and efficiency.
-
c.
Different from the traditional permutation methods, this paper designs a new block permutation based on several algebraic operations. Since each module adopted in the permutation is all low-complexity units that are easily implemented by computers, they have good confusion characteristics. The experimental results also effectively support the feasibility of the block permutation method in this paper.
-
d.
In image encryption using plaintext correlation, extra channels must be communicated to transmit the feature values of the plaintext. In contrast, we embed the feature values associated with the plaintext and the intermediate ciphertext into the cipher image, and the receiver can achieve normal decryption without additional key exchange, which ensures the usability in practical applications.
The remaining sections of this paper are organized as follows. Section Related theory briefly outlines the relevant theory behind the proposed algorithm. Section Proposed encryption algorithm explains the precise details of our encryption algorithm. Section Experimental results and analysis discussion presents experimental results and analysis discussion. The final section concludes the study.
Related theory
The used chaotic system
2D logistic-sine-coupling map
The chaos62 utilized in this research is sourced from two established one-dimensional chaotic maps, namely the logistic map and the sine map. By coupling the logistic map and the sine map, we can acquire a new chaotic map of considerable complexity, namely the 2D-LSCM, which can be determined as follows:
| (Equation 1) |
where θ is the control parameter. As the definition suggests, the 2D-LSCM is generated by coupling the logistic and sine maps; the results are further subjected to sine transformation and expanding from one dimension to two. Through this process, the intricacies of the logistic map and the sine map are intertwined, resulting in a complex chaotic behavior.
NIST test results of chaos
A collection of 16 unique test sets is provided by the NIST-800-22 test suite, with the aim of assessing binary sequences generated by cryptographic or pseudo-random number generators that depend on random values and lengths. Notably, all sequences intended for encryption have passed this test correctly, and some of the results are presented in the Table 1.
Table 1.
The test results for NIST-800-22
| Statistical | p values |
||
|---|---|---|---|
| Sequence1 | Sequence2 | Results | |
| Frequency (Monobit) Test | 0.534146 | 0.739918 | successful |
| Block-frenquency test | 0.739918 | 0.350485 | successful |
| Cumulative-sums test | 0.000954 | 0.122325 | successful |
| Runs test | 0.911413 | 0.739918 | successful |
| Longest-run test | 0.350485 | 0.911413 | successful |
| Binary matrix rank test | 0.534146 | 0.534146 | successful |
| Discrete Fourier transform test | 0.534146 | 0.534146 | successful |
| Non-overlapping templates test | 0.000439 | 0.008879 | successful |
| Overlapping templates test | 0.017912 | 0.122325 | successful |
| Maurer’s universal statistical test | 0.035174 | 0.534146 | successful |
| Approximate entropy test | 0.534146 | 0.991468 | successful |
| Random-excursions test(x = −4) | 0.022503 | 0.048716 | successful |
| Random-excursions variant test(x = −9) | 0.022503 | 0.122325 | successful |
| Serial test-1 | 0.911413 | 0.739918 | successful |
| Serial test-2 | 0.066882 | 0.213309 | successful |
| Linear-complexity test | 0.739918 | 0.911413 | successful |
0-1 Test results of chaos
The 0–1 Gottwald Melbourne test is a tool that calculates parameters very close to 0 or 1 to accurately distinguish between regular and chaotic motion. Our team used the 0–1 Gottwald Melbourne test to obtain 10,000 results, which reflect the average value of 0.9979, exhibiting the remarkable performance of the chaotic system. The test results are illustrated in the following Figure 1.
Figure 1.
0–1 Gottwald Melbourne test
Bit planes decomposition
A digital image is created by converting an analog image into a digital format, where the pixels serve as the basic element that can be stored and processed by a digital computer or circuit. In computing, a bit is a unit of information and the smallest unit of measurement for bits and information within a binary number. The range of pixel values in an image is . Bit plane decomposition involves converting the pixel values of a digital image into binary form and then dividing the binary representation into eight-bit planes. Taking a digital image P as an example, the bit planes decomposition can be expressed as
| (Equation 2) |
where denotes the bit plane, , , ; denotes the highest bit planes, and denotes the lowests bit planes. Taking the grayscale image of “Lena” as an example, the bit planes decomposition diagram is shown in Figure 2.
Figure 2.
Information ratio of pixels occupied by 8-bit planes
Block permutation
Standard scrambling algorithms, which simply rearrange the pixel positions within the primitive image, can be easily deciphered and are susceptible to chosen-plaintext attacks. To address this problem, this paper introduces a new scrambling algorithm that uses chaotic sequences based on the plaintext feedback mechanism, as shown in Figure 3. Firstly, the image feature values are extracted as chaotic keys to generate an initial pseudo-random sequence. Then, the original image and initial chaotic sequence are preprocessed. Finally, different encryption rules can be selected according to the preprocessed sequences, and the generated cipher images can be obtained by block scrambling, block rotation and block inversion, negative-positive transformation, and color component shuffling. The empirical data demonstrate that the permutation mechanism proposed in this manuscript significantly enhances the algorithm’s resilience against attacks.
Figure 3.
Block permutation flowchart
Proposed encryption algorithm
The proposed encryption algorithm is specified based on the following four sections: the first part, key generation and initial value scrambling; the second part, an explanation of the user-defined “chain function”; the third part, the process of image encryption; and the fourth part, the image decryption process. In this paper, assuming an original image P is input, the process of encrypting into a cipher image C consists of three modules. First, the original image is block permuted. Next, a random order substitution is executed on the permuted image. Finally, the resulting intermediate cipher image is layered according to Equation 2, after which the final cipher image can be obtained. The overall block diagram illustrating the flow of the encryption algorithm is depicted Figure 4.
Figure 4.
Diagram depicting the procedural flow of the proposed encryption algorithm
Key generation and initial value scrambling
This algorithm utilizes the MD5 hash function to establish the correspondence between plaintext and ciphertext. The hash function’s one-way property and anti-collision feature substantially enhance the algorithm’s capability to withstand attacks from chosen-plaintext attacks and known-plaintext attacks.
: read image feature values
After reading the image features by MD5 function, we can get a 32-bit hexadecimal number with fixed bit length, and each bit is represented as , where .
: disturb the initial value
After obtaining the eigenvalues, the initial value of the chaotic map is perturbed. This allows different images to correspond to different key sequences and improves their resistance to differential attacks. The specific procedure is defined as
| (Equation 3) |
where denotes the XOR operator; denote the scrambled keys.
Chain function
Chain encryption function
For ease of description, we define the details of the operation for each plane as a self-named function , where P represents the plain image, denotes the initial value utilized to generate the chaotic sequence for encrypting the image plane, and C denotes the cipher image. The function contains two parts: sequence preprocessing and permutation-diffusion encryption. Take the example of encrypting an image with size as described below:
: preprocess chaotic sequence
For the chain encryption module, a total of two chaotic sequences are required. is introduced into the 2D-LSCM chaotic system, and the initial chaotic sequences and are obtained after iterating times. The corresponding sorted indexes and can be described as
| (Equation 4) |
where function represents the sorting of each sequence value in the input sequence from lowest to highest, and indicate the result of reordering the sequences, and and indicate sorted indexes.
: permutation and diffusion encryption
By sequence and , performing row-column permutation on the layered images to be encrypted results in permuted image . Then it is bit-level diffused to secure the cipher image C. The operation is shown as
| (Equation 5) |
where and .
Chain decryption function
For the convenience of a detailed exposition on the decryption process in subsequent sections, the definition of the chain decryption function will be given, where P denotes the recovered image, C denotes the image that is waiting to be decrypted, and denotes the initial key to generate the desired chaotic sequences. After putting the into the chaotic system, it iterates times to obtain two chaotic sequences and . Substituted into the Equation 4, the sorted index sequence and can be obtained, respectively. The decryption process is shown in Equation 6.
| (Equation 6) |
Encryption process
In this section, an original image P of size will be used as an example to illustrate the encryption process. The first encryption is a block permutation operation after chunking the original image. In this article, we choose to divide the image into small blocks with a length of 8, and the process is as follows.
: preprocess image and sequence
Initially, the plaintext image P is divided into segments and transformed into a matrix format, ensuring that the matrix dimensions are multiples of 8 for both rows and columns. If there are not enough elements in the matrix, the zeroes are filled. Then, the hash eigenvalues of the image P are read and are obtained as chaotic initial values according to Equation 3. The four initial values are iterated by the 2D-LSCM system to obtain four pseudo-random sequences . And they are preprocessed according to the Equation 7 to obtain sequences that can be used for block scrambling operation. The pretreatment Equation 7 is described as
| (Equation 7) |
where indicates rounding down, and represents modulo operation.
: block scrambling
The specific diagram of block scrambling is shown in Figure 5. The operation of block scrambling is as follows:
| (Equation 8) |
where , , , z signifies the dimension of the matrix, t indicates the intermediate variable, and B represents the matrix after block scrambling.
Figure 5.
Diagram illustrating block scrambling
: block rotation and block inversion
Based on the sequence , block rotation and block inversion are performed on the data in the sub-block. Taking the matrix after block scrambling encryption as an example, the matrix after inverse encryption is obtained by using the method constructed in Algorithm 1, and the schematic of block rotation and inversion is shown in Figure 6.
Algorithm 1. Block rotation and block inversion.
Input: pseudo-random sequence , intermediate ciphertext , block side length , image length H, and image width W:
Output: block rotation and block inversion encrypt ciphertext
1: for to do
2: for to do
3: for to do
4: for to do
5: if then
6:
7:
8:
9: else if then
10:
11:
12: else if then
13:
14:
15:
16: else if then
17:
18:
19: else if then
20:
21:
22: end if
23: end for
24: end for
25: end for
26: end for
Figure 6.
Schematic diagram of block rotation and block inversion
: negative-positive transformation
after the operation of taking modulo 2, the obtained has two values of 0 or 1, and their respective corresponding operations are shown as
| (Equation 9) |
B represents the matrix after block rotation and block inversion.
: color component shuffling
Based on the sequence , the corresponding color transformation is applied to the processed matrix using Algorithm 2. The specific color component shuffling schematic is shown in Figure 7.
Algorithm 2. Color component shuffling.
Input: pseudo-random sequence , intermediate cipher image , block side length , image block length H, and image block width W
Output: block permutated image
1: for to do
2: for to do
3: if then
4:
5: else if then
6:
7: else if then
8:
9: else if then
10:
11:
12: else if then
13:
14:
15: end if
16: end for
17: end for
Figure 7.
Schematic diagram of color component shuffling
The matrix after block encryption is merged to get block permutated image .
Next, it will be subjected to a random order substitution operation.
: random order substitution
The and are substituted into the chaotic system iteration to obtain the sequences S and . The index matrix I is achieved by arranging the sequence . Random order substitution of cipher images is carried out using index matrix I with sequence S. The random order substitution can be explained as follows:
| (Equation 10) |
After obtaining image Q, it will be subjected to bit-layered and chained encryption.
: bit planes decomposition
After reading the image Q and splitting it according to the three channels, three grayscale images , , and are obtained, which are bit planes decomposition, respectively. It can be expressed as
| (Equation 11) |
where function denotes the bit value at position k in A is returned, , , and denote the images obtained by layering , , and , and k denotes the bit plane, .
Taking R channel as an example, the other two channels are the same. Specifically, the obtained 8 layered images are .
: hide original image feature values in the first bit plane
In order to facilitate the decryption operation by the recipient, the hash value of the original image needs to be stored in the first line of layered image . It is worth noting that, as shown by the analysis in Section Bit planes decomposition, the first layer of the bit plane contains very little information. Taking a 256 256 size image as an example, the proportion of the feature value in the original image is only 0.000586%. Even if the decrypted image is enlarged, it is difficult to observe the difference with the naked eye.
: encrypt with
| (Equation 12) |
: chain encrypt
After the fifth layer cipher image is obtained, the hash eigenvalue is read and substituted into the Equation 3 (a), and the chaotic initial value used to encrypt the next layer is obtained. The encryption of the sixth layer bit plane is given below:
| (Equation 13) |
The encryption method for the images is the same as earlier and can be expressed by the Equation 14.
| (Equation 14) |
: chain encrypt
For the low-order bit plane, only a small amount of image information is contained, so the same chaotic sequence will be used to encrypt the four layers of . Similarly, after reading the eigenvalues of and performing the processing as in Equation 3 (a), the is obtained, and the encryption of these four layers can be expressed as
| (Equation 15) |
: compound bit planes
The encrypted images are planes compounded as
| (Equation 16) |
where denotes the final cipher image of the R channel after reduction.
Similarly, we can get the cipher image after the chain encryption of G channel and B channel, and the resulting cipher image C is obtained after the reduction of three channels.
Decryption process
Decryption is the reverse process of encryption. The flow chart of decryption is shown in Figure 8. For simplicity, a brief description of the decryption process is as follows.
Figure 8.
The flow chart of decryption
: bit planes decomposition
After dividing the cipher image C into three channels, we get . Take the R channel as an example; the remaining two channels are the same. According to Equation 11, 8-bit planes are obtained.
: extract the original image feature values and decrypt
The recipient extracts the eigenvalues of the original image stored in the first line of and obtains the according to the Equation 3 (a). The decrypted image of the fifth layer plane can be obtained. The specific operation is described as
| (Equation 17) |
: chain decryption of the remaining bit planes decomposition
| (Equation 18) |
: recovery bit planes decomposition
| (Equation 19) |
So far, we get the image of R channel after chain decryption. Similarly, the decrypted image of the remaining two channels can be obtained, and the image Q is obtained after compounding the three channels.
: decrypt random order substitution
After substituting the extracted hash eigenvalue of the original image into the formula Eq. (3)(b), the can be obtained. After substituting the and into the chaotic system, two chaotic sequences S and can be obtained, respectively. The index matrix I is obtained after is sorted by the sort() function. The random order substitution decryption formula is given as follows:
| (Equation 20) |
So far, the decrypted image can be obtained, which is the cipher image only encrypted by block permutation.
: decrypt block permutation
Deblock permutation is the inverse operation of block permutation encryption. Firstly, pseudo-random sequences are generated through 2D-LSCM chaotic system using the key, followed by the image being segmented into blocks, and then block the image . According to the generated sequence, the decryption operations of color component scrambling, positive-negative transformation, block rotation and block inversion, and block permutation are performed in turn. Finally, the decrypted images are combined to obtain the final decrypted image P.
Experimental results and analysis discussion
Experimental environment
We utilized a personal computer (PC) equipped with MATLAB R2023a software as our experimental platform. The system was powered by an AMD Ryzen 9 5950X central processing unit (CPU), featuring a clock frequency of 3.88 GHz. The device had 32 GB of memory and a 4TB hard drive, operating on the Windows 10 operating system. USC-SIPI image database was used in the experimental data selection.
Experimental results and analysis
Histogram analysis
Figure 9 displays the 3D visualization of the pixel distribution prior to and following the encryption of three channels, enabling an observation of the cross-plane encryption effect. This visualization serves as a simple yet effective demonstration of the algorithm’s ability to achieve high-performance encryption. Meanwhile, we selected five other images of different types and encrypted them. The renderings and histograms are presented in Figure 10. The original image shows a certain statistical law, while the statistical characteristics of the encrypted image histograms show a noise-like distribution, which well hides the gray value information of the images. This measure strengthens the resilience against statistical analysis attacks.
Figure 9.
Images before and after encryption and their 3D histograms
(A) Plain image and cipher image.
(B) Red channel.
(C) Green channel.
(D) Blue channel.
Figure 10.
The images before and after encryption and their 2D histogram
(A) Plain images.
(B) Histogram of (A).
(C) Cipher images.
(D) Histogram of (C).
Adjacent pixel correlation analysis
Ordinary images are typically composed of pixels that have a high degree of neighborhood correlation. However, when using a robust encryption algorithm, the encrypted image should ideally have no association between individual pixels and their nearby counterparts. Therefore, a reliable encryption scheme should transform a regular image into an encrypted image with minimal correlation among neighboring pixels.
To evaluate the correlation between adjacent pixels in both plaintext and cipher images, we took the following measures. First, we randomly selected 3,000 pairs of neighboring pixel points from both the plaintext and cipher images. Secondly, we computed the correlation coefficients of the neighboring pixels in diverse orientations such as horizontal, vertical, diagonal, and anti-diagonal directions individually. In accordance with Equation 21, the correlation coefficients are calculated as follows:
| (Equation 21) |
where and form the first pair of horizontal/vertical/diagonal/anti-diagonal adjacent pixels and M is the total number of horizontal/vertical/diagonal/anti-diagonal adjacent pixels. The correlation between adjacent pixels data of the encrypted image is shown in Figure 11. Figure 11 shows the adjacent pixel distribution of the channels before and after "Lena" image encryption. Experimental data indicate a pronounced contrast in the correlation coefficients between typical images and their encrypted counterparts. In particular, the correlation coefficient for a normal image has a value close to 1, while that for an encrypted image is approximately equal to 0. This highlights the ability of the proposed encryption scheme to generate images with uncorrelated neighboring pixels, emphasizing its resistance to statistical attacks. Therefore, the scheme presented in this study can be considered as highly secure.
Figure 11.
Analysis results of adjacent pixels of plain and cipher images
(A) Red channel.
(B) Green channel.
(C) Blue channel.
Differential statistical analysis
Two standards are typically used to measure the dissimilarity between the source image and its encrypted version: the number of pixel change rate (NPCR) and the uniform average change intensity (UACI). In standard disparate attacks, attackers tend to make subtle modifications to the source image and then encrypt the original image using the proposed algorithm. This approach allows them to reveal the underlying relationship between the original and encrypted images. NPCR and UACI criteria are commonly used to evaluate the resistance of an encryption scheme to disparate attacks. The equations for calculating NPCR and UACI are as follows:
| (Equation 22) |
where represents the size of the image, and is the cipher image before and after changing one pixel of the plaintext image. D can be defined by the Equation 23.
| (Equation 23) |
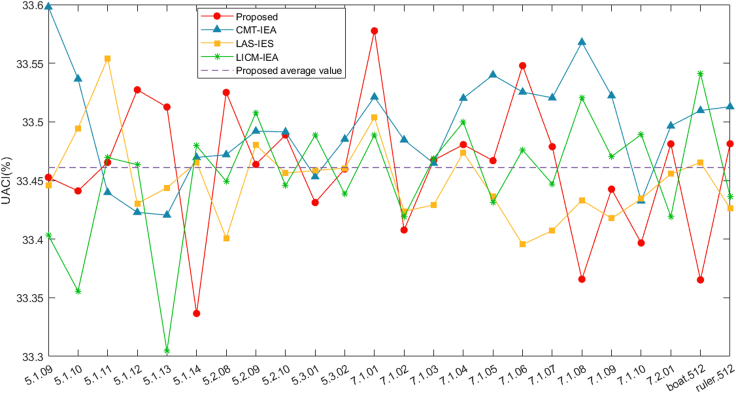
Tables 2 and 3 show the algorithm’s outcomes as computed per Equation 22. These tables reveal that NPCR and UACI align closely with their expected values of 99.6094% and 33.4635%, respectively. Our algorithm has been further compared with classical algorithms63,64 and other algorithms,65 with the comparative results presented in both Figures 12 and 13. The results obtained indicate that the proposed encryption scheme exhibits sensitivity to variations in the source image, allowing the generation of two unique encrypted images even in the presence of a single difference bit. This substantiates the effectuality and robustness of the presented cryptosystem to changes in the input image, increasing its overall reliability and viability for various real-world applications.
Table 2.
NPCR values of the matching cipher images by distinct algorithms
| Images | Description | Size | Type | Proposed | CMT-IEA63 | LAS-IES64 | LICM-IEA65 |
|---|---|---|---|---|---|---|---|
| 5.1.09.tiff | Moon surface | 256 | gray | 99.6429 | 99.6658 | 99.6064 | 99.6140 |
| 5.1.10.tiff | Aerial | 256 | gray | 99.6643 | 99.6475 | 99.6154 | 99.5880 |
| 5.1.11.tiff | Airplane | 256 | gray | 99.5865 | 99.6674 | 99.6244 | 99.6033 |
| 5.1.12.tiff | Clock | 256 | gray | 99.5422 | 99.5941 | 99.5703 | 99.5651 |
| 5.1.13.tiff | Resolution chart | 256 | gray | 99.6078 | 99.6445 | 99.6109 | 99.5789 |
| 5.1.14.tiff | Chemical plant | 256 | gray | 99.6002 | 99.5975 | 99.6364 | 99.6765 |
| 5.2.08.tiff | Couple | 512 | gray | 99.6162 | 99.6281 | 99.5870 | 99.6037 |
| 5.2.09.tiff | Aerial | 512 | gray | 99.6040 | 99.6197 | 99.6260 | 99.6029 |
| 5.2.10.tiff | Stream and bridge | 512 | gray | 99.6078 | 99.6281 | 99.6124 | 99.6124 |
| 5.3.01.tiff | Male | 1024 | gray | 99.6044 | 99.6098 | 99.5931 | 99.6072 |
| 5.3.02.tiff | Airport | 1024 | gray | 99.6034 | 99.6119 | 99.6128 | 99.6116 |
| 7.1.01.tiff | Truck | 512 | gray | 99.6098 | 99.6273 | 99.5992 | 99.6082 |
| 7.1.02.tiff | Airplane | 512 | gray | 99.6189 | 99.5892 | 99.6075 | 99.6174 |
| 7.1.03.tiff | Tank | 512 | gray | 99.6140 | 99.6201 | 99.6079 | 99.6120 |
| 7.1.04.tiff | Car and APCs | 512 | gray | 99.6124 | 99.5894 | 99.5988 | 99.5911 |
| 7.1.05.tiff | Truck and APCs | 512 | gray | 99.6197 | 99.6185 | 99.6170 | 99.6178 |
| 7.1.06.tiff | Truck and APCs | 512 | gray | 99.6231 | 99.6117 | 99.6272 | 99.6174 |
| 7.1.07.tiff | Tank | 512 | gray | 99.5953 | 99.6223 | 99.5931 | 99.5922 |
| 7.1.08.tiff | APC | 512 | gray | 99.6239 | 99.6151 | 99.6094 | 99.6056 |
| 7.1.09.tiff | Tank | 512 | gray | 99.5815 | 99.6044 | 99.6162 | 99.6086 |
| 7.1.10.tiff | Car and APCs | 512 | gray | 99.5945 | 99.6101 | 99.6045 | 99.5941 |
| 7.2.01.tiff | Airplane(U-2) | 1024 | gray | 99.6114 | 99.6156 | 99.6156 | 99.6204 |
| boat.512.tiff | Fishing boat | 512 | gray | 99.6090 | 99.6006 | 99.6154 | 99.6101 |
| ruler.512.tiff | Pixel ruler | 512 | gray | 99.6002 | 99.6265 | 99.6120 | 99.6212 |
Table 3.
UACI values of the matching cipher images by distinct algorithms
| Images | Description | Size | Type | Proposed | CMT-IEA63 | LAS-IES64 | LICM-IEA65 |
|---|---|---|---|---|---|---|---|
| 5.1.09.tiff | Moon surface | 256 | gray | 33.4527 | 33.5980 | 33.4456 | 33.4032 |
| 5.1.10.tiff | Aerial | 256 | gray | 33.4411 | 33.5366 | 33.4946 | 33.3557 |
| 5.1.11.tiff | Airplane | 256 | gray | 33.4654 | 33.4398 | 33.5541 | 33.4696 |
| 5.1.12.tiff | Clock | 256 | gray | 33.5273 | 33.4228 | 33.4302 | 33.4634 |
| 5.1.13.tiff | Resolution chart | 256 | gray | 33.5126 | 33.4205 | 33.4438 | 33.3046 |
| 5.1.14.tiff | Chemical plant | 256 | gray | 33.3366 | 33.4696 | 33.4655 | 33.4796 |
| 5.2.08.tiff | Couple | 512 | gray | 33.5251 | 33.4720 | 33.4008 | 33.4493 |
| 5.2.09.tiff | Aerial | 512 | gray | 33.4637 | 33.4921 | 33.4804 | 33.5077 |
| 5.2.10.tiff | Stream and bridge | 512 | gray | 33.4888 | 33.4914 | 33.4563 | 33.4457 |
| 5.3.01.tiff | Male | 1024 | gray | 33.4312 | 33.4532 | 33.4585 | 33.4886 |
| 5.3.02.tiff | Airport | 1024 | gray | 33.4598 | 33.4853 | 33.4605 | 33.4384 |
| 7.1.01.tiff | Truck | 512 | gray | 33.5776 | 33.5212 | 33.5037 | 33.4890 |
| 7.1.02.tiff | Airplane | 512 | gray | 33.4078 | 33.4846 | 33.4237 | 33.4190 |
| 7.1.03.tiff | Tank | 512 | gray | 33.4673 | 33.4647 | 33.4291 | 33.4689 |
| 7.1.04.tiff | Car and APCs | 512 | gray | 33.4806 | 33.5202 | 33.4739 | 33.4997 |
| 7.1.05.tiff | Truck and APCs | 512 | gray | 33.4669 | 33.5400 | 33.4362 | 33.4313 |
| 7.1.06.tiff | Truck and APCs | 512 | gray | 33.5479 | 33.5254 | 33.3954 | 33.4760 |
| 7.1.07.tiff | Tank | 512 | gray | 33.4788 | 33.5205 | 33.4073 | 33.4470 |
| 7.1.08.tiff | APC | 512 | gray | 33.3658 | 33.5678 | 33.4332 | 33.5203 |
| 7.1.09.tiff | Tank | 512 | gray | 33.4426 | 33.5223 | 33.4177 | 33.4704 |
| 7.1.10.tiff | Car and APCs | 512 | gray | 33.3967 | 33.4325 | 33.4344 | 33.4892 |
| 7.2.01.tiff | Airplane(U-2) | 1024 | gray | 33.4812 | 33.4965 | 33.4556 | 33.4192 |
| boat.512.tiff | Fishing boat | 512 | gray | 33.3652 | 33.5097 | 33.4654 | 33.5414 |
| ruler.512.tiff | Pixel ruler | 512 | gray | 33.4813 | 33.5129 | 33.4262 | 33.4363 |
Figure 12.
Results of NPCR visualization across different algorithms for comparison
Figure 13.
Comparison results of UACI visualization with different algorithms
Information entropy analysis
The degree of randomness in a system is typically assessed by using the entropy of the information as a standard metric. For an information source m, the information entropy is given by
| (Equation 24) |
where L represents the total number of pixels. The probability of is denoted by .
Suppose the source sends 256 symbols and we can get the theoretical value using Equation 24. The closer it is to 8, the less likely it is that an attacker will be able to successfully decode the encrypted image. The Lena image is used as the experimental image of information entropy (size: 256 256, type: color). Table 4 compares the entropy values and shows that the experimental results are close to 8. This indicates that the proposed algorithm has good entropy properties.
Table 4.
The results of information entropy analysis for distinct algorithms
| Encryption algorithm | Channel |
Average value | ||
|---|---|---|---|---|
| Red | Green | Blue | ||
| Proposed | 7.9993 | 7.9994 | 7.9993 | 7.99933 |
| Ref. Hua et al.62 | 7.9993 | 7.9993 | 7.9993 | 7.99930 |
| Ref. Kumar et al.66 | 7.9912 | 7.9914 | 7.9915 | 7.99137 |
| Ref. Kadir et al.67 | 7.9278 | 7.9744 | 7.9705 | 7.95757 |
| Ref. Wu et al.68 | 7.9895 | 7.9894 | 7.9894 | 7.98943 |
| Ref. Zhou et al.69 | 7.9992 | 7.9994 | 7.9993 | 7.99930 |
Image quality analysis
In the realm of image processing, peak signal to noise ratio (PSNR) and structural similarity (SSIM) are served as standard metrics for assessing the quality of encryption. The mean square error (MSE) is part of the PSNR, defined as
| (Equation 25) |
where MSE represents the mean square error between the plaintext image X and the cipher image Y. The vertical extent of the image is represented by H, and the horizontal dimension of the image is denoted by W. The pixel level of the image is denoted by Q. SSIM is a measure of the similarity between two images, explained as
| (Equation 26) |
where the mean values of image X is denoted by and the mean values of image Y is denoted by . The standard deviation of image X is denoted by , the standard deviation of image Y is represented by , and L indicates the dynamic amplitude of pixel values.
As shown in the Table 5, the values of MSE, PSNR, and SSIM can be determined using mathematical Equations 25 and 26. Ideally, the PSNR of an encrypted image should be around 10 dB, while the SSIM should be between −1 and 1. An absolute SSIM value close to 1 indicates excellent similarity between the images being compared. Therefore, after encryption, variations in SSIM should fluctuate around 0.
Table 5.
PSNR, MSE, and SSIM values
| Images | Description | Size | Type | PSNR(dB) | Ref.70 | MSE | Ref.70 | SSIM | Ref.70 |
|---|---|---|---|---|---|---|---|---|---|
| 5.1.09.tiff | Moon surface | 256 | gray | 10.1586 | 10.1588 | 6269.29 | 6269.10 | 0.0103 | 0.0098 |
| 5.1.10.tiff | Aerial | 256 | gray | 9.2692 | 9.2858 | 7694.17 | 7664.70 | 0.0099 | 0.0098 |
| 5.1.11.tiff | Airplane | 256 | gray | 7.7554 | 7.7187 | 10902.98 | 10995.00 | 0.0103 | 0.0098 |
| 5.1.12.tiff | Clock | 256 | gray | 7.2710 | 7.2913 | 12189.26 | 12133.00 | 0.0081 | 0.0107 |
| 5.1.13.tiff | Resolution chart | 256 | gray | 4.9404 | 4.9343 | 20846.78 | 20876.00 | 0.0092 | 0.0064 |
| 5.1.14.tiff | Chemical plant | 256 | gray | 9.2195 | 9.2311 | 7782.77 | 7762.00 | 0.0115 | 0.0091 |
| 5.2.08.tiff | Couple | 512 | gray | 9.6047 | 9.6319 | 7122.20 | 7077.70 | 0.0095 | 0.0097 |
| 5.2.09.tiff | Aerial | 512 | gray | 8.2012 | 8.2019 | 9839.26 | 9837.60 | 0.0089 | 0.0091 |
| 5.2.10.tiff | Stream and bridge | 512 | gray | 8.7573 | 8.7508 | 8656.67 | 8669.70 | 0.0100 | 0.0085 |
| 5.3.01.tiff | Male | 1024 | gray | 8.0013 | 8.0033 | 10310.87 | 10298.00 | 0.0080 | 0.0086 |
| 5.3.02.tiff | Airport | 1024 | gray | 8.7334 | 8.7449 | 8704.47 | 8681.50 | 0.0091 | 0.0091 |
| 7.1.01.tiff | Truck | 512 | gray | 9.9018 | 9.9244 | 6651.21 | 6616.70 | 0.0104 | 0.0106 |
| 7.1.02.tiff | Airplane | 512 | gray | 8.9647 | 8.9790 | 8253.05 | 8225.90 | 0.0104 | 0.0110 |
| 7.1.03.tiff | Tank | 512 | gray | 10.1862 | 10.1819 | 6229.64 | 6237.20 | 0.0104 | 0.0108 |
| 7.1.04.tiff | Car and APCs | 512 | gray | 9.8068 | 9.8081 | 6798.26 | 6796.20 | 0.0101 | 0.0109 |
| 7.1.05.tiff | Truck and APCs | 512 | gray | 9.6001 | 9.6067 | 7129.70 | 7118.80 | 0.0103 | 0.0106 |
| 7.1.06.tiff | Truck and APCs | 512 | gray | 9.1130 | 9.1258 | 7975.85 | 7952.50 | 0.0103 | 0.0095 |
| 7.1.07.tiff | Tank | 512 | gray | 10.0470 | 10.0528 | 6432.49 | 6424.00 | 0.0106 | 0.0103 |
| 7.1.08.tiff | APC | 512 | gray | 10.3267 | 10.3206 | 6031.23 | 6039.80 | 0.0113 | 0.0109 |
| 7.1.09.tiff | Tank | 512 | gray | 9.8454 | 9.8368 | 6738.12 | 6751.60 | 0.0107 | 0.0107 |
| 7.1.10.tiff | Car and APCs | 512 | gray | 10.1809 | 10.1702 | 6237.23 | 6252.60 | 0.0104 | 0.0108 |
| 7.2.01.tiff | Airplane(U-2) | 1024 | gray | 6.3261 | 6.3214 | 15152.17 | 15168.00 | 0.0048 | 0.0046 |
| boat.512.tiff | Fishing boat | 512 | gray | 9.3058 | 9.3009 | 7629.54 | 7638.20 | 0.0097 | 0.0086 |
| gray21.512.tiff | 21 level step wedge | 512 | gray | 7.5706 | 7.5703 | 11376.67 | 11378.00 | 0.0088 | 0.0090 |
| ruler.512.tiff | Pixel ruler | 512 | gray | 4.7649 | 4.7657 | 21706.57 | 21702.00 | 0.0087 | 0.0075 |
Key space
The key space denotes the encompassing set of all conceivable keys that can be utilized for key generation. The magnitude of the key space is contingent upon the length of secure keys and serves as a critical determinant of the strength of a cryptosystem. It is one of the most important parameters in the overall assessment of the robustness and reliability of a cryptographic system. The image encryption algorithm proposed in this paper utilizes a 2D discrete chaotic system, and the expression of its key space can be given as , where are the key parameters with precision and MD5 are the hash value introduced to enhance the key space, which can generate a 128-bit hash. The approximate estimation of the key space size for this encryption scheme is . By analyzing Table 6, it becomes evident that our proposed encryption scheme not only demonstrates a notable advantage in terms of the key space over existing schemes but also contributes to the enhanced resilience of our encryption algorithm against various types of attacks.
Table 6.
Table of key space comparisons
Sensitivity analysis
This section analyses the performance sensitivity of the algorithm separately for both key and plaintext. It is essential that security algorithms have a high level of sensitivity. This implies that even minute alterations in the encryption or decryption process, such as modifications to the key or variations in the plaintext information, will result in incorrect outcomes.
Key sensitivity analysis
Key sensitivity analysis is performed by comparing the resulting ciphertexts when the identical image is encrypted using two comparable keys. Our study examines the difference in the resulting ciphertext obtained from encrypting with the actual key and encryption using an additional key that contains slight perturbations. The difference between these two results is then evaluated using NPCR and UACI, as calculated via Equation 22, with the consequences presented in Table 7. Interestingly, the consequences express that, even when the key is subjected to slight perturbations, the resulting NPCR and UACI values of the commensurating ciphertext are close to the ideal values of 99.6094% and 33.4635%, respectively. Figure 14 shows the statistical results of NPCR and UACI under different disturbance parameters. In addition, it can be clearly seen from Figure 14 that NPCR and UACI are very close to the ideal values, indicating that the proposed algorithm has good key sensitivity, so it can effectively resist differential attacks and chosen-plaintext attacks.
Table 7.
Comparison of average encryption times
Figure 14.
Comparison conclusions of NPCR and UACI presentation with various levels of disturbance
Plaintext sensitivity analysis
Plaintext sensitivity refers to the degree of change in the resulting ciphertext when the plaintext pixels are changed. If an algorithm ignores plaintext sensitivity, it becomes vulnerable to attacks that exploit the comparison between plaintext and ciphertext pairs. Consequently, the measure of plaintext sensitivity is a crucial element in determining the robustness of the algorithm against plaintext attacks. In this section, we analyze the sensitivity of the proposed algorithm to ordinary images by adding 1 to the pixel values of ordinary images at , , , and to calculate the NPCR and UACI. The results are presented in Table 8, and the comparison images are shown in Figure 15; the dotted line in the figure is the average value of NPCR and UACI for the corresponding color. As indicated in Table 8, when the pixel values at the selected locations are varied by 1, the corresponding encrypted images exhibit a remarkable average NPCR score of 99.6101% compared to the original ciphertext, which is close to the ideal value of 99.6094%. Additionally, an average UACI score of 33.4743% is observed, which is also close to the desirable UACI value of 33.4635%. Based on the results, we can observe that the proposed algorithm makes the cryptographic images susceptible to significant modification, making it insurmountable for attackers to compromise the system by comparing the ciphertexts. Consequently, the proposed algorithm is sufficiently equipped to withstand various types of plaintext attacks.
Table 8.
Key sensitivity test results
| Images | Description | Size | Type | 0 |
|
|
|
|
|||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| NPCR | UACI | NPCR | UACI | NPCR | UACI | NPCR | UACI | NPCR | UACI | ||||
| 5.1.09.tiff | Moon surface | 256 | gray | 99.6429 | 33.4527 | 99.6262 | 33.5135 | 99.5789 | 33.4181 | 99.6109 | 33.5142 | 99.6231 | 33.3606 |
| 5.1.10.tiff | Aerial | 256 | gray | 99.6643 | 33.4411 | 99.6368 | 33.3855 | 99.5987 | 33.4934 | 99.5987 | 33.5587 | 99.6338 | 33.4519 |
| 5.1.11.tiff | Airplane | 256 | gray | 99.5865 | 33.4654 | 99.6368 | 33.3868 | 99.6063 | 33.4430 | 99.6414 | 33.4939 | 99.6124 | 33.3773 |
| 5.2.08.tiff | Couple | 512 | gray | 99.6162 | 33.5251 | 99.6071 | 33.4395 | 99.6033 | 33.5052 | 99.5979 | 33.4903 | 99.6063 | 33.4551 |
| 5.2.09.tiff | Aerial | 512 | gray | 99.6040 | 33.4637 | 99.6086 | 33.4904 | 99.6078 | 33.4370 | 99.5708 | 33.4582 | 99.6189 | 33.4731 |
| 5.2.10.tiff | Stream and bridge | 512 | gray | 99.6078 | 33.4888 | 99.5945 | 33.5082 | 99.6155 | 33.4839 | 99.6155 | 33.4767 | 99.6098 | 33.5189 |
| 5.3.01.tiff | Male | 1024 | gray | 99.6044 | 33.4312 | 99.6146 | 33.4459 | 99.6081 | 33.4501 | 99.6126 | 33.4708 | 99.6132 | 33.4830 |
| 5.3.02.tiff | Airport | 1024 | gray | 99.6034 | 33.4598 | 99.6270 | 33.4504 | 99.6043 | 33.4988 | 99.6037 | 33.4530 | 99.6097 | 33.4479 |
| 7.2.01.tiff | Airplane(U-2) | 1024 | gray | 99.6114 | 33.4812 | 99.6086 | 33.4596 | 99.6030 | 33.4348 | 99.6092 | 33.4762 | 99.6191 | 33.4776 |
Figure 15.
Comparison conclusions of NPCR and UACI presentation with different locations
The complexity and execution time analysis
We gauge the complexity of the proposed algorithm by measuring the computational time required for encryption and assess its suitability for real-time applications. In this encryption scheme, the most critical four steps are chaotic sequence generation, image scrambling, replacement, and bit-level chain diffusion. Their complexity is , , , and , respectively. Thus, the total complexity is . Table 9 provides a comparison of encryption times between our proposed algorithm and corresponding algorithms in the literature. It is noteworthy that the encryption time data in Table 9 were obtained using computers with varying processing capabilities and memory configurations to comprehensively evaluate algorithm performance. Such comparisons aid in determining which encryption algorithm is best suited to meet security and performance requirements under specific hardware and environmental conditions.
Table 9.
Plaintext sensitivity test results
| Images | Description | Size | Type | (H/3,W/3) |
(H/3,2 W/3) |
(2 H/3,W/3) |
(2 H/3,2 W/3) |
||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| NPCR | UACI | NPCR | UACI | NPCR | UACI | NPCR | UACI | ||||
| 2.1.09.tiff | San Diego(Point Loma) | 512 | color | 99.5911 | 33.4904 | 99.5834 | 33.3552 | 99.5728 | 33.4221 | 99.6155 | 33.4213 |
| 2.2.13.tiff | Stockton | 1024 | color | 99.6262 | 33.7220 | 99.5773 | 33.4769 | 99.6155 | 33.4456 | 99.6124 | 33.3336 |
| 4.2.03.tiff | Mandrill | 512 | color | 99.6197 | 33.4086 | 99.6170 | 33.4828 | 99.5792 | 33.4577 | 99.6017 | 33.4272 |
| 4.2.07.tiff | Peppers | 512 | color | 99.614 | 33.4424 | 99.6284 | 33.4607 | 99.6243 | 33.4108 | 99.6265 | 33.4115 |
| 5.1.09.tiff | Moon surface | 256 | gray | 99.6078 | 33.6272 | 99.5987 | 33.5365 | 99.5956 | 33.4835 | 99.6262 | 33.3571 |
| 5.1.10.tiff | Aerial | 256 | gray | 99.6109 | 33.4922 | 99.6353 | 33.5588 | 99.6353 | 33.3817 | 99.5865 | 33.3876 |
| 5.1.11.tiff | Airplane | 256 | gray | 99.6338 | 33.5427 | 99.6292 | 33.4084 | 99.5956 | 33.3985 | 99.5773 | 33.5661 |
| 5.2.08.tiff | Couple | 512 | gray | 99.6159 | 33.5467 | 99.6006 | 33.4131 | 99.638 | 33.4967 | 99.6109 | 33.5117 |
| 5.2.09.tiff | Aerial | 512 | gray | 99.6101 | 33.4628 | 99.6243 | 33.4903 | 99.6143 | 33.4327 | 99.6204 | 33.5087 |
| 5.2.10.tiff | Stream and bridge | 512 | gray | 99.6231 | 33.4788 | 99.6078 | 33.5042 | 99.6319 | 33.4991 | 99.6105 | 33.4073 |
| 5.3.01.tiff | Male | 1024 | gray | 99.5978 | 33.4303 | 99.6098 | 33.4721 | 99.6089 | 33.4410 | 99.6080 | 33.4276 |
| 5.3.02.tiff | Airport | 1024 | gray | 99.6045 | 33.4976 | 99.6061 | 33.4617 | 99.6060 | 33.4332 | 99.6067 | 33.4688 |
| 7.2.01.tiff | Airplane(U-2) | 1024 | gray | 99.6016 | 33.4537 | 99.6068 | 33.4851 | 99.6057 | 33.4522 | 99.6070 | 33.4456 |
| house.tiff | House | 512 | color | 99.6136 | 33.4647 | 99.6059 | 33.4378 | 99.6212 | 33.4957 | 99.6117 | 33.4957 |
Robustness analysis
Robustness is an important index in the evaluation of image encryption algorithm. It measures whether the encryption algorithm can effectively protect the content of the image from damage or leakage in the face of various interference noises. In the real world, images may be affected by a variety of disturbances. Therefore, it is very important to analyze and evaluate the anti-interference ability of image encryption algorithm. In this section, salt and pepper noise and occlusion attack are selected for analysis.
Salt and pepper noise analysis
Separately add 5%, 10%, and 20% salt and pepper noise into the plaintext image. We can see from Figure 16 that the image adding noise can still have effective recognizable image information after decryption.
Figure 16.
The cipher and decryption image after adding salt and pepper noise
(A) Add 5% salt and pepper noise.
(B) Add 10% salt and pepper noise.
(C) Add 20% salt and pepper noise.
Occlusion attack analysis
Respectively add occlusion noise, whose sizes are , , and , into cipher image, and we can see from Figure 17 that the image adding noise can still have effective recognizable image information after decryption.
Figure 17.
The cipher and decryption image after adding occlusion noise
(A) Add occlusion noise.
(B) Add occlusion noise.
(C) Add occlusion noise.
Conclusion
This paper presents a comprehensive encryption algorithm for enhancing image security by combining chaos-based block permutation and bit planes chain diffusion. Our approach aims to improve the security of image encryption, enhance its ability to withstand cryptographic attacks in existing computing environments, and ensure secure communication of digital images in networked environments. To begin, we propose a novel block permutation encryption algorithm that employs chaotic sequences to perform various operations on the plaintext image, such as block scrambling, rotation, inversion, positive/negative transformation, and color component transformation. These operations generate an intermediate cipher image, effectively safeguarding the confidentiality of the image. We introduce the random order substitution method, which further increases the difficulty for the attacker to crack the ciphertext. Last but not least, we utilize the hierarchical structure of the bit plane and chain diffusion to generate the final ciphertext. By incorporating these mechanisms, the avalanche effect is enhanced, thus increasing the security of the encryption. Experimental results demonstrate that our proposed algorithm has high security and robustness, making it highly resistant to various cryptographic attacks. Therefore, the image encryption algorithm reported in this paper is a preferred secure communication technology solution, which has a broad application prospect in the secure transmission of multimedia information in big data environments, etc.
Limitations of the study
There may be some possible limitations in this study. In robustness analysis, there is a very small probability of damaging the original hidden key, resulting in the ciphertext not being able to be restored.
STAR★Methods
Key resources table
| REAGENT or RESOURCE | SOURCE | IDENTIFIER |
|---|---|---|
| Software and algorithms | ||
| Matlab R2023a | MathWorks.Inc | https://ww2.mathworks.cn/products/matlab.html |
| The USC-SIPI Image Database | University of Southern California | https://sipi.usc.edu/database/database.php |
Resource availability
Lead contact
Further information for resources and materials should be directed to and will be fulfilled by the lead contact, Dr. Heping Wen (wenheping@uestc.edu.cn).
Materials availability
This study did not generate new unique reagents.
Data and code availability
-
•
All experimental data is clearly explained in this paper.
-
•
This paper does not report original code.
-
•
Any additional information required to reanalyze the data reported in this paper is available from the lead contact upon request.
Method details
In this study, a PC equipped with MATLAB R2023a software was used as the experimental platform. The system is driven by AMD Ryzen 9 5950 X CPU with a clock frequency of 3.88 GHz. The device has 32GB memory and 4TB hard disk and runs on Windows 10 operating system. The experimental data were selected from the USC-SIPI image database. All the software and data involved can be publicly available in the key resources table.
Quantification and statistical analysis
Adjacent pixel correlation analysis
The correlation coefficients are calculated as follows:
where and form the first pair of horizontal/vertical/diagonal/anti-diagonal adjacent pixels and M is the total number of horizontal/vertical/diagonal/anti-diagonal adjacent pixels.
Differential statistical analysis
Two standards are typically used to measure the dissimilarity between the source image and its encrypted version: the number of pixel change rate (NPCR) and the uniform average change intensity (UACI). In standard disparate attacks, attackers tend to make subtle modifications to the source image and then encrypt the original image using the proposed algorithm. This approach allows them to reveal the underlying relationship between the original and encrypted images. NPCR and UACI criteria are commonly used to evaluate the resistance of an encryption scheme to disparate attacks. The equations for calculating NPCR and UACI are as follows:
where represents the size of the image, is the cipher image before and after changing one pixel of the plaintext image. D can be defined:
Information entropy analysis
The degree of randomness in a system is typically assessed by using the entropy of the information as a standard metric. For an information source m, the information entropy is given by:
where L represents the total number of pixels. The probability of is denoted by .
Image quality analysis
In the realm of image processing, Peak Signal to Noise Ratio (PSNR) and Structural Similarity (SSIM) are served as standard metrics for assessing the quality of encryption. The Mean Square Error (MSE) is part of the PSNR, defined as:
where MSE represents the mean square error between the plaintext image X and the ciphertext image Y. The vertical extent of the image is represented by H, the horizontal dimension of the image is denoted by W. The pixel level of the image is denoted by Q. SSIM is a measure of the similarity between two images, explained as:
where the mean values of image X is denoted by , the mean values of image Y is denoted by . The standard deviation of image X is denoted by , the standard deviation of image Y is represented by and L indicates the dynamic amplitude of pixel values.
Acknowledgments
This work was supported in part by Guangdong Basic and Applied Basic Research Foundation under grant 2023A1515011717, in part by Project for Zhongshan Science and Technology under grant 2021B2062, and in part by Special Projects for Key Fields of the Education Department of Guangdong Province under grant 2023ZDZX1041.
Author contributions
Conceptualization, Y.L.; methodology, Y.L.; software, Y.L. and S.K.; validation, S.K. and X.Z.; formal analysis, S.K. and X.Z.; investigation, S.K. and X.Z.; resources, H.W. and K.Z.; data curation, S.K. and X.Z.; writing – original draft, Y.L. and H.W.; writing – review & editing, Y.L. and H.W.; visualization, Y.L.; supervision, H.W.; project administration, H.W.; funding acquisition, H.W. All authors have read and agreed to the published version of the manuscript.
Declaration of interests
The authors declare no competing interests.
Published: December 2, 2023
References
- 1.Liang X., Zhang C., Luo Y., Wang X., Qiu K. Secure encryption and key management for ofdm-pon based on chaotic hilbert motion. J. Lightwave Technol. 2023;41:1619–1625. [Google Scholar]
- 2.Luo Y., Zhang C., Wang X., Liang X., Qiu K. Robust key update with controllable accuracy using support vector machine for secure ofdma-pon. J. Lightwave Technol. 2023;41:4663–4671. [Google Scholar]
- 3.Wu T., Zeng W., Liu Y., Song S., Zhao L., Chen C., Zhang C., Guo L. Secure turbulence-resistant coherent free-space optical communications via chaotic region-optimized probabilistic constellation shaping. Opt. Lett. 2023;48:684–687. doi: 10.1364/OL.480981. [DOI] [PubMed] [Google Scholar]
- 4.Li C., Lin D., Lü J., Hao F. Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography. IEEE MultiMedia. 2018;25:46–56. [Google Scholar]
- 5.Li X., Zhou L., Tan F. An image encryption scheme based on finite-time cluster synchronization of two-layer complex dynamic networks. Soft Comput. 2021;26:511–525. [Google Scholar]
- 6.Tiwari D., Mondal B., Singh S.K., Koundal D. Lightweight encryption for privacy protection of data transmission in cyber physical systems. Cluster Comput. 2022;26:2351–2365. [Google Scholar]
- 7.Kumari P., Mondal B. An encryption scheme based on grain stream cipher and chaos for privacy protection of image data on iot network. Wirel. Pers. Commun. 2023;130:2261–2280. [Google Scholar]
- 8.Kumari P., Mondal B. Lightweight image encryption algorithm using nlfsr and cbc mode. J. Supercomput. 2023;79:19452–19472. [Google Scholar]
- 9.Liu L., Wang J. A cluster of 1d quadratic chaotic map and its applications in image encryption. Math. Comput. Simulat. 2023;204:89–114. [Google Scholar]
- 10.Chai X., Wang Y., Chen X., Gan Z., Zhang Y. Tpe-gan: Thumbnail preserving encryption based on gan with key. IEEE Signal Process. Lett. 2022;29:972–976. [Google Scholar]
- 11.Liu W., Sun K., He S., Wang H. The parallel chaotification map and its application. IEEE Trans. Circuits Syst. I. 2023;70:3689–3698. [Google Scholar]
- 12.Lu X., Xie E.Y., Li C. Periodicity analysis of the logistic map over ring z3n. Int. J. Bifurcation Chaos. 2023;33 [Google Scholar]
- 13.Wen H., Huang Y., Lin Y. High-quality color image compression-encryption using chaos and block permutation. J. King Saud Univ. Comput. Inf. Sci. 2023;35 [Google Scholar]
- 14.Ding Y., Liu W., Wang H., Sun K. A new class of discrete modular memristors and application in chaotic systems. Eur. Phys. J. Plus. 2023;138 [Google Scholar]
- 15.Liu X., Sun K., Wang H., He S. A class of novel discrete memristive chaotic map. Chaos, Solit. Fractals. 2023;174 [Google Scholar]
- 16.Man Z., Li J., Di X., Sheng Y., Liu Z. Double image encryption algorithm based on neural network and chaos. Chaos, Solit. Fractals. 2021;152 [Google Scholar]
- 17.Wen H., Wu J., Ma L., Liu Z., Lin Y., Zhou L., Jian H., Lin W., Liu L., Zheng T., Zhang C. Secure optical image communication using double random transformation and memristive chaos. IEEE Photonics J. 2023;15:1–11. [Google Scholar]
- 18.Chen L., Li C., Li C. Security measurement of a medical communication scheme based on chaos and dna coding. J. Vis. Commun. Image Represent. 2022;83 [Google Scholar]
- 19.Hu M., Li J., Di X. Quantum image encryption scheme based on 2d Sine2- logistic chaotic map. Nonlinear Dyn. 2022;111:2815–2839. [Google Scholar]
- 20.Man Z., Li J., Di X., Zhang R., Li X., Sun X. Research on cloud data encryption algorithm based on bidirectional activation neural network. Inf. Sci. 2023;622:629–651. [Google Scholar]
- 21.Wen H., Chen Z., Zheng J., Huang Y., Li S., Ma L., Lin Y., Liu Z., Li R., Liu L., et al. Design and embedded implementation of secure image encryption scheme using dwt and 2d-lasm. Entropy. 2022;24:1332. doi: 10.3390/e24101332. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 22.Chai X., Fu J., Gan Z., Lu Y., Zhang Y., Han D. Exploiting semi-tensor product compressed sensing and hybrid cloud for secure medical image transmission. IEEE Internet Things J. 2023;10:7380–7392. [Google Scholar]
- 23.Chen X., Mou J., Cao Y., Yan H., Jahanshahi H. A Chaotic Color Image Encryption Scheme Based on Improved Arnold Scrambling and Dynamic Dna Encoding. Multimed. Tool. Appl. 2023 [Google Scholar]
- 24.Hua Z., Liu X., Zheng Y., Yi S., Zhang Y. Reversible data hiding over encrypted images via preprocessing-free matrix secret sharing. IEEE Trans. Circuits Syst. Video Technol. 2023:1. [Google Scholar]
- 25.Wen H., Lin Y. Cryptanalyzing an image cipher using multiple chaos and dna operations. J. King Saud Univ. Comput. Inf. Sci. 2023;35 [Google Scholar]
- 26.Liu S., Li C., Hu Q. Cryptanalyzing two image encryption algorithms based on a first-order time-delay system. IEEE MultiMedia. 2022;29:74–84. [Google Scholar]
- 27.Wen H., Chen R., Yang J., Zheng T., Wu J., Lin W., Jian H., Lin Y., Ma L., Liu Z., Zhang C. Security Analysis of a Color Image Encryption Based on Bit-Level and Chaotic Map. Multimed. Tool. Appl. 2023 [Google Scholar]
- 28.Zhou S., Qiu Y., Wang X., Zhang Y. Novel image cryptosystem based on new 2d hyperchaotic map and dynamical chaotic s-box. Nonlinear Dyn. 2023;111:9571–9589. [Google Scholar]
- 29.Zhou S., Wang X., Zhang Y. Novel image encryption scheme based on chaotic signals with finite-precision error. Inf. Sci. 2023;621:782–798. [Google Scholar]
- 30.Fridrich J. Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurcation Chaos. 1998;08:1259–1284. [Google Scholar]
- 31.Chen J., Chen L., Zhou Y. Cryptanalysis of a dna-based image encryption scheme. Inf. Sci. 2020;520:130–141. [Google Scholar]
- 32.Wen H., Lin Y. Cryptanalysis of an image encryption algorithm using quantum chaotic map and dna coding. Expert Syst. Appl. 2024;237 [Google Scholar]
- 33.Zou C., Wang X., Zhou C., Xu S., Huang C. A novel image encryption algorithm based on dna strand exchange and diffusion. Appl. Math. Comput. 2022;430 [Google Scholar]
- 34.Zheng J., Lv T. Image encryption algorithm based on cascaded chaotic map and improved zigzag transform. IET Image Process. 2022;16:3863–3875. [Google Scholar]
- 35.Jiang X., Jiang G., Wang Q., Shu D. Image Encryption Algorithm Based on 2d-Clicm Chaotic System. IET Image Process. 2023 [Google Scholar]
- 36.Gao Z., Wu Q., Liao L., Su B., Gao X., Fu S., Li Z., Wang Y., Qin Y. Experimental demonstration of synchronous privacy enhanced chaotic temporal phase en/decryption for high speed secure optical communication. Opt Express. 2022;30:31209–31219. doi: 10.1364/OE.467578. [DOI] [PubMed] [Google Scholar]
- 37.Jiang Z., Ding Q. Second-order side-channel analysis based on orthogonal transform nonlinear regression. Entropy. 2023;25:505. doi: 10.3390/e25030505. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 38.Su Y., Wang X., Xu M., Zou C., Liu H. A three-dimensional (3d) space permutation and diffusion technique for chaotic image encryption using merkel tree and dna code. Sens. Imaging. 2023;24 [Google Scholar]
- 39.Zhang Y., Zhou W., Zhao R., Zhang X., Cao X. F-tpe: Flexible thumbnail-preserving encryption based on multi-pixel sum-preserving encryption. IEEE Trans. Multimedia. 2023;25:5877–5891. [Google Scholar]
- 40.Feng W., Qin Z., Zhang J., Ahmad M. Cryptanalysis and improvement of the image encryption scheme based on feistel network and dynamic dna encoding. IEEE Access. 2021;9:145459–145470. [Google Scholar]
- 41.Lai Q., Zhang H., Kuate P.D.K., Xu G., Zhao X.-W. Analysis and implementation of no-equilibrium chaotic system with application in image encryption. Appl. Intell. 2022;52:11448–11471. [Google Scholar]
- 42.Tang Z., Chai X., Lu Y., Wang B., Tan Y. An end-to-end screen shooting resilient blind watermarking scheme for medical images. J. Inf. Secur. Appl. 2023;76 [Google Scholar]
- 43.Ye G., Liu M., Yap W.-S., Goi B.-M. Reversible image hiding algorithm based on compressive sensing and deep learning. Nonlinear Dyn. 2023;111:13535–13560. [Google Scholar]
- 44.Lu D., Li M., Liao Y., Tao G., Cai H. Verifiable privacy-preserving queries on multi-source dynamic dna datasets. IEEE Trans. Cloud Comput. 2023;11:1927–1939. [Google Scholar]
- 45.Wang X., Zhao M. An image encryption algorithm based on hyperchaotic system and dna coding. Opt. Laser Technol. 2021;143 [Google Scholar]
- 46.Wen H., Kang S., Wu Z., Lin Y., Huang Y. Dynamic rna coding color image cipher based on chain feedback structure. Mathematics. 2023;11:3133. [Google Scholar]
- 47.Wen H., Liu Z., Lai H., Zhang C., Liu L., Yang J., Lin Y., Li Y., Liao Y., Ma L., et al. Secure dna-coding image optical communication using non-degenerate hyperchaos and dynamic secret-key. Mathematics. 2022;10:3180. [Google Scholar]
- 48.Bao B., Wang Z., Hua Z., Chen M., Bao H. Regime transition and multi-scroll hyperchaos in a discrete neuron model. Nonlinear Dyn. 2023;111:13499–13512. [Google Scholar]
- 49.Cao C., Cen Z., Feng X., Wang Z., Zhu Y. Straightforward guess and determine analysis based on genetic algorithm. J. Syst. Sci. Complex. 2022;35:1988–2003. [Google Scholar]
- 50.Jiang N., Zhao A., Liu S., Zhang Y., Peng J., Qiu K. Injection-locking chaos synchronization and communication in closed-loop semiconductor lasers subject to phase-conjugate feedback. Opt Express. 2020;28:9477–9486. doi: 10.1364/OE.389028. [DOI] [PubMed] [Google Scholar]
- 51.Zhang Y.-Q., Huang H.-F., Wang X.-Y., Huang X.-H. A secure image encryption scheme based on genetic mutation and mlncml chaotic system. Multimed. Tool. Appl. 2021;80:19291–19305. [Google Scholar]
- 52.Lai Q., Hu G., Erkan U., Toktas A. A novel pixel-split image encryption scheme based on 2d salomon map. Expert Syst. Appl. 2023;213 [Google Scholar]
- 53.Li H., Yu S., Feng W., Chen Y., Zhang J., Qin Z., Zhu Z., Wozniak M. Exploiting dynamic vector-level operations and a 2d-enhanced logistic modular map for efficient chaotic image encryption. Entropy. 2023;25:1147. doi: 10.3390/e25081147. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 54.Luo Y., Wang F., Xu S., Zhang S., Li L., Su M., Liu J. Conceal: A robust dual-color image watermarking scheme. Expert Syst. Appl. 2022;208 [Google Scholar]
- 55.Teng L., Wang X., Yang F., Xian Y. Color image encryption based on cross 2d hyperchaotic map using combined cycle shift scrambling and selecting diffusion. Nonlinear Dyn. 2021;105:1859–1876. [Google Scholar]
- 56.Li M., Wang P., Yue Y., Liu Y. Cryptanalysis of a secure image encryption scheme based on a novel 2d sine–cosine cross-chaotic map. J. Real. Time. Image Process. 2021;18:2135–2149. [Google Scholar]
- 57.Lu X., Xie E.Y., Li C. Periodicity analysis of Logistic map over ring Z3n. Int. J. Bifurcation Chaos. 2023;33 [Google Scholar]
- 58.Ma Y., Li C., Ou B. Cryptanalysis of an image block encryption algorithm based on chaotic maps. J. Inf. Secur. Appl. 2020;54 [Google Scholar]
- 59.Shafique A., Shahid J. Novel image encryption cryptosystem based on binary bit planes extraction and multiple chaotic maps. Eur. Phys. J. Plus. 2018;133 [Google Scholar]
- 60.Wen H., Yu S. Cryptanalysis of an image encryption cryptosystem based on binary bit planes extraction and multiple chaotic maps. Eur. Phys. J. Plus. 2019;134 [Google Scholar]
- 61.Song C., Qiao Y. A novel image encryption algorithm based on dna encoding and spatiotemporal chaos. Entropy. 2015;17:6954–6968. doi: 10.3390/e21030246. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 62.Hua Z., Jin F., Xu B., Huang H. 2d logistic-sine-coupling map for image encryption. Signal Process. 2018;149:148–161. [Google Scholar]
- 63.Hua Z., Zhou Y., Pun C.-M., Chen C.P. 2d sine logistic modulation map for image encryption. Inf. Sci. 2015;297:80–94. [Google Scholar]
- 64.Hua Z., Zhou Y. Image encryption using 2d logistic-adjusted-sine map. Inf. Sci. 2016;339:237–253. [Google Scholar]
- 65.Cao C., Sun K., Liu W. A novel bit-level image encryption algorithm based on 2d-licm hyperchaotic map. Signal Process. 2018;143:122–133. [Google Scholar]
- 66.Kumar M., Sathish G., Alphonse M., Lahcen R.A.M. A new rgb image encryption using generalized heat equation associated with generalized vigene‘ re-type table over symmetric group. Multimed. Tool. Appl. 2019;78:28025–28061. [Google Scholar]
- 67.Kadir A., Hamdulla A., Guo W.-Q. Color image encryption using skew tent map and hyper chaotic system of 6th-order cnn. Optik. 2014;125:1671–1675. [Google Scholar]
- 68.Wu X., Kurths J., Kan H. A robust and lossless dna encryption scheme for color images. Multimed. Tool. Appl. 2018;77:12349–12376. [Google Scholar]
- 69.Zhou Y., Bao L., Chen C.P. A new 1d chaotic system for image encryption. Signal Process. 2014;97:172–182. [Google Scholar]
- 70.Wen H., Lin Y., Xie Z., Liu T. Chaos-based block permutation and dynamic sequence multiplexing for video encryption. Sci. Rep. 2023;13 doi: 10.1038/s41598-023-41082-9. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 71.Murillo-Escobar M., Cruz-Hernández C., Abundiz-Pérez F., López-Gutiérrez R., Acosta Del Campo O. A rgb image encryption algorithm based on total plain image characteristics and chaos. Signal Process. 2015;109:119–131. [Google Scholar]
- 72.Liu L., Zhang Q., Wei X. A rgb image encryption algorithm based on dna encoding and chaos map. Comput. Electr. Eng. 2012;38:1240–1248. Special issue on Recent Advances in Security and Privacy in Distributed Communications and Image processing. [Google Scholar]
- 73.Mansouri A., Wang X. A novel block-based image encryption scheme using a new sine powered chaotic map generator. Multimed. Tool. Appl. 2021;80:21955–21978. [Google Scholar]
- 74.Shafique A., Ahmed F. Image encryption using dynamic s-box substitution in the wavelet domain. Wirel. Pers. Commun. 2020;115:2243–2268. [Google Scholar]
- 75.Alexan W., Elkandoz M., Mashaly M., Azab E., Aboshousha A. Color image encryption through chaos and kaa map. IEEE Access. 2023;11:11541–11554. [Google Scholar]
- 76.Alexan W., ElBeltagy M., Aboshousha A. Rgb image encryption through cellular automata, s-box and the lorenz system. Symmetry. 2022;14:443. [Google Scholar]
- 77.Xu L., Li Z., Li J., Hua W. A novel bit-level image encryption algorithm based on chaotic maps. Opt Laser. Eng. 2016;78:17–25. [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
-
•
All experimental data is clearly explained in this paper.
-
•
This paper does not report original code.
-
•
Any additional information required to reanalyze the data reported in this paper is available from the lead contact upon request.