. 2024 Jan 15;10:e1772. doi: 10.7717/peerj-cs.1772
©2024 Iftikhar
This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
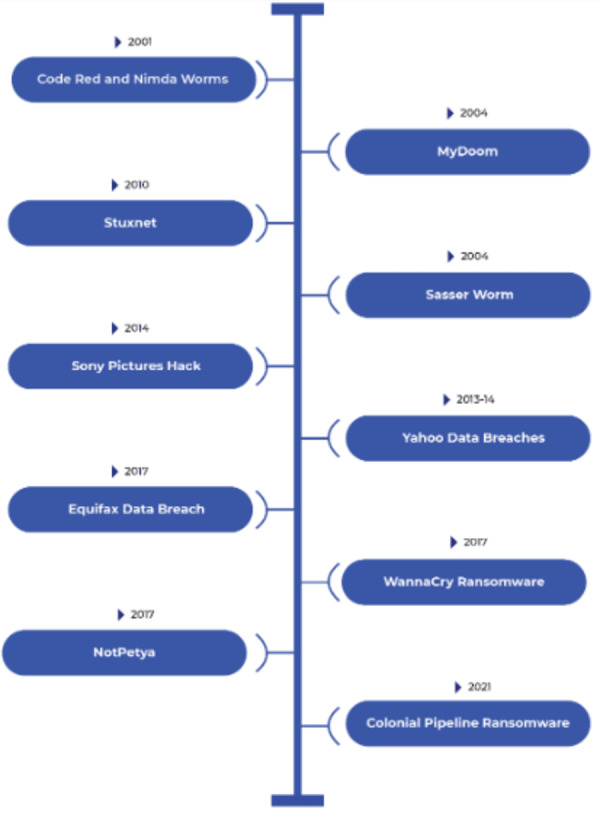
Figure 2. Overview of some of the recent cyberattacks.