Abstract
Background
Genetic data are widely considered inherently identifiable. However, genetic data sets come in many shapes and sizes, and the feasibility of privacy attacks depends on their specific content. Assessing the reidentification risk of genetic data is complex, yet there is a lack of guidelines or recommendations that support data processors in performing such an evaluation.
Objective
This study aims to gain a comprehensive understanding of the privacy vulnerabilities of genetic data and create a summary that can guide data processors in assessing the privacy risk of genetic data sets.
Methods
We conducted a 2-step search, in which we first identified 21 reviews published between 2017 and 2023 on the topic of genomic privacy and then analyzed all references cited in the reviews (n=1645) to identify 42 unique original research studies that demonstrate a privacy attack on genetic data. We then evaluated the type and components of genetic data exploited for these attacks as well as the effort and resources needed for their implementation and their probability of success.
Results
From our literature review, we derived 9 nonmutually exclusive features of genetic data that are both inherent to any genetic data set and informative about privacy risk: biological modality, experimental assay, data format or level of processing, germline versus somatic variation content, content of single nucleotide polymorphisms, short tandem repeats, aggregated sample measures, structural variants, and rare single nucleotide variants.
Conclusions
On the basis of our literature review, the evaluation of these 9 features covers the great majority of privacy-critical aspects of genetic data and thus provides a foundation and guidance for assessing genetic data risk.
Keywords: genetic privacy, privacy, data anonymization, reidentification
Introduction
Privacy Risks of Genetic Data
Genomics is a rapidly developing field with exabytes of genetic data being generated, stored, and analyzed by public and private institutions per year. These data drive scientific progress, especially when they are shared with the scientific community or among institutions. However, genetic data can provide information about an individual’s identity together with sensitive details, such as their ethnic background [1]; physical traits such as eye color [2], hair and skin color [3], height [4]; and diseases or susceptibility to diseases [5]. Therefore, even if personal identifiers (eg, name, date of birth, or others) are removed, sharing genetic data may violate the individual’s right to privacy. In 2018, a seminal study demonstrated that it is possible to reidentify individuals by name from genetic data alone [6]. The authors matched genetic data of an anonymous female study participant to the genetic genealogy database GEDmatch and identified her surname from matches with relatives who had uploaded their data on GEDmatch. Such reidentification of genetic data records using publicly available databases is highly problematic and a growing threat to privacy as publicly available genetic genealogy databases continue to grow. It is estimated that a genetic database needs to cover “only 2% of the target population to provide a third-cousin match to nearly any person” in a matching attack, similar to the one demonstrated by Erlich et al [6]. As of 2018, the probability for such a match was estimated to be 60% for the platform GEDmatch. Through similar methods of familial DNA searches, multiple individuals have been identified in criminal cases, despite never having shared their genetic data themselves [7,8]. Other attacks aim to reveal sensitive information from genetic data. In 2009, researchers discovered a genetic predisposition for Alzheimer disease in the public genome of the famous molecular biologist and Nobel laureate James Watson, although he had attempted to prevent such an attack by withholding certain parts of the data [9]. The high identifiability potential of genetic data together with its sensitive content with regard to health (eg, susceptibility to diseases such as Alzheimer disease or cancer) and physical traits (refer to the studies by Erlich and Narayanan [10], El Emam et al [11], and Mohammed Yakubu and Chen [12] for a review) has raised public concern that genetic data that are shared or published in the context of research or health care could be misused [13]. For example, attackers could exploit genetic data to obtain personal and sensitive information about individuals, and this information could be misused by insurance companies, mortgage providers, or employers to discriminate on the basis of genetic information (eg, about disease susceptibility) [14]. As an additional complication, DNA sequence is heritable; therefore, leakage of an individual’s genetic data can violate the privacy of whole families [15,16].
The Challenge of Anonymizing Genetic Data
Genetic data can be used to identify individuals because each person’s DNA sequence differs uniquely from the standard human reference genome. Although more than 99% of the DNA sequence is identical across all humans, the remaining <1% consists of distinct combinations of insertions, deletions, duplications, translocations, and inversions of short or long DNA fragments (refer to the study by Trost et al [17] for a review). These genetic variations are not randomly distributed across the genome but occur more frequently in specific variable regions. Some variations are rare, while others (ie, polymorphisms) are shared by a significant proportion of the population. While some variations have no observable effect, others influence gene transcription, expression, or the amino acid sequence of a protein and have an effect on the phenotype, for example, physical traits, metabolism, and disease susceptibility. These variable regions with an effect on the phenotype are of great interest to research; however, these can also be effectively used for individual identification and the inference of sensitive attributes. Even a small genetic data set of only 30 highly variable genetic loci is likely to contain unique records, and these could not only be linked to genetic records in other data sets but also provide insights into health and physical traits (refer to the studies by Erlich and Narayanan [10], El Emam et al [11], and Mohammed Yakubu and Chen [12] for a review). Furthermore, genetic variation is highly intercorrelated (variation in one genomic region correlates with variation in another) and correlated to other modalities (genetic variation is associated with transcription, expression, epigenetic regulation, etc), making it possible to link data records of the same individual even across databases that do not contain the same type of data (eg, match a genetic data sequence to a gene expression record). Anonymizing genetic data while maintaining its full utility remains an unsolved challenge, and there is no consensus on whether it is even possible [18]. Many privacy-enhancing technologies aim to reduce the information content of genetic data or restrict access to it, such that only a minimal amount of information is shared. An example is genomic beacons, which allow only simple yes or no queries to determine whether a specific variant is present in a study cohort [19]. However, it has become evident that even this limited amount of information can be exploited for privacy attacks, and few queries to genomic beacons can suffice to determine whether individuals (whose genome is known) are present in a study cohort [20-23]. Similarly, proposals for encryption and differential privacy approaches [24,25] have often been countered by demonstrations of attacks [26-28], and even synthetic genetic data may not fully protect the study participants from privacy attacks [29] (refer to the study by Mittos et al [30] for a review of privacy-enhancing technologies). Thus, even a substantial reduction in information content can often not completely eliminate all privacy risks of genetic data [31].
The Risk Minimization Approach for Genetic Data Privacy
Most legislations do not require to reduce the risk of individual identification to zero, and several jurisdictions have decided to take a risk-based approach and consider genetic data anonymous if the risk of successful reidentification is below a predefined acceptable threshold [32]. Therefore, genetic data processors must find the balance between reducing information such that reidentification is no longer reasonably likely, while maintaining as much utility of the data as possible [33]. The challenge in adopting this approach lies in the correct assessment of the reidentification probability. Genetic data are complex and come in various shapes or forms, making it difficult to standardize reidentification assessments. Established methods such as assessing k-anonymity are difficult to apply to genetic data because of their high uniqueness, and many other methods fall short because of the high intercorrelation of genetic data. Simple measures such as assessing the number of single nucleotide polymorphisms (SNPs) in genetic data ignore the importance of the location of the SNPs in the genome, their frequencies in the population, and the actual feasibility of cross-linking the specific SNPs to identifiable information. For example, the reidentification risk is much higher for SNPs that are commonly included in the SNP assays used by direct-to-consumer genetic testing (DTC-GT) providers than for less frequently studied SNPs, as these are more difficult to link to publicly available identifying information. In addition, genetic data may contain SNP information even if this is not immediately evident, for example, in the raw data of sequencing-based gene expression studies. Data processors who are not familiar with the intricacies of genetic data find little guidance on performing an assessment on genetic data that considers these factors. While several genomic privacy metrics have been proposed, the great majority focus on evaluating SNPs only [34] and neglect other known privacy-critical aspects of genetic data as well as aspects of feasibility (eg, the expertise, time, effort, availability of external resources, and other requirements required for an attack). However, the risk of severe privacy attacks on genetic data (ie, where the identity of the data subject is revealed) greatly depends on the specific content of the data as well as “soft factors,” such as the availability of publicly accessible resources to cross-link and infer quasi-identifying information and the time, cost, and knowledge required to perform such an attack. Given the foundational potential of genetic data to advance research and health care, a risk-based approach that carefully evaluates the true risk of reidentification on a case-by-case basis for each data set in question is warranted, or else any type of genetic data must be considered identifiable.
Methods
To get a comprehensive overview of the types and aspects of genetic data sets that are vulnerable to reidentification attacks, as well as the methods, databases, and know-how used for these attacks, we searched for studies that demonstrate a privacy attack on genetic data. We did not aim to establish an exhaustive overview of all published privacy attacks but aimed to get a comprehensive understanding of the most vulnerable features of genetic data. Therefore, we first searched for recent reviews published on the topic of genomic privacy using ProQuest. Using the search terms (ti(*genom* OR *genetic*) AND ti(privacy OR re-identification OR reidentification OR “data security”)) and (pd(>20170101)) and (at.exact(“Review”)), we identified 23 reviews, of which 3 (13%) were discarded because they were off topic. One additional review was identified during the literature research and added to the selection (refer to Multimedia Appendix 1 [35-55] for an overview of the included and excluded reviews), resulting in a final sample of 21 reviews. In a second step, we extracted all references cited in the reviews (n=1645) and identified all original research studies that demonstrate a privacy attack on genetic data. After the removal of 514 duplicates and 876 reference studies that did not contain any description of information inference from human genetic data, we first excluded 89 studies whose main contribution was the presentation of privacy-preserving measures to exclude privacy attacks that were performed only for the purpose of proving the efficiency of the proposed counter methods. Next, we excluded 120 studies that did not present original research and were purely associative (ie, did not demonstrate how an adversary gains knowledge that was not intended to be shared from genetic data) as well as 4 studies that did not demonstrate the attack on real data. This process resulted in the selection of 42 unique studies (refer to Figure 1 for an overview of the process and Table S1 in Multimedia Appendix 1 for an overview of the eligible attack studies). Extending on the framework by Mohammed Yakubu and Chen [12] and Lu et al [56], we categorized attacks into (1) identity tracing (attacker triangulates the identity of an individual), (2) inference (attacker uses an individual’s genetic data to infer sensitive attributes such as disease or drug abuse or to infer additional data or cross-link records across databases), and (3) membership attacks (attacker uncovers membership of an individual in a data set). We evaluated the type and components of genetic data exploited for this attack as well as the effort and resources used for it (time, expertise, databases, and computation power) and its success rate if sufficient information was reported in the study. The initial evaluation was conducted by one reviewer and independently verified by another. Table S1 in Multimedia Appendix 1 presents a detailed overview of the attack studies.
Figure 1.
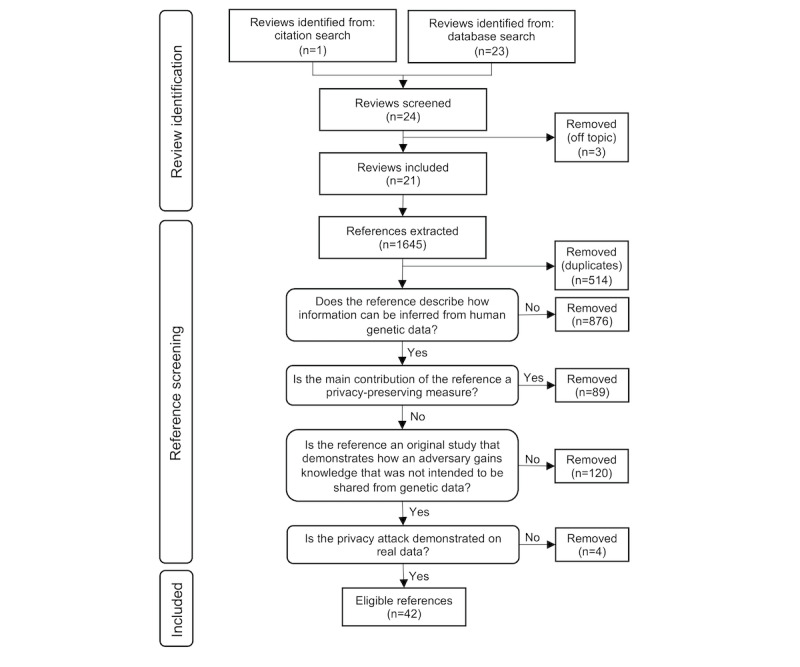
Flowchart overview of the 2-step literature review process: identification of relevant reviews, followed by extraction and screening of references.
Results
A Comprehensive Overview of Privacy Risks in Genetic Data Sets
On the basis of our literature review, we created an overview of the parts and aspects of genetic data that are commonly exploited in privacy attacks and that should therefore be taken into consideration when performing a risk assessment on genetic data. The goal of this overview is to provide data processors, who may not be experts in genomic data privacy, with essential background knowledge about the privacy vulnerabilities associated with genetic data. This understanding will help them identify privacy-critical aspects and serve as a starting point for conducting risk assessments on genetic data sets. Notably, the reidentification risks associated with data that complement genetic data (eg, clinical data and demographic data) as well as aspects of the data environment (access and governance) are crucial for a comprehensive risk assessment [57], but these aspects are not in the scope of this research. From our literature review, we synthesized 9 features that are both inherent to any genetic data and informative about privacy risk (Figure 2). The features are not mutually exclusive. Instead, they represent different “views” on genetic data and highlight various aspects that should be considered in a privacy risk assessment. For each feature, we lay out why this feature is associated with privacy risk by summarizing the relevant evidence in the scientific literature, and we assess the criticality of these attacks. In addition, we provide guiding questions that help to assess the risk of a given data set. The features can be divided into three groups:
Figure 2.
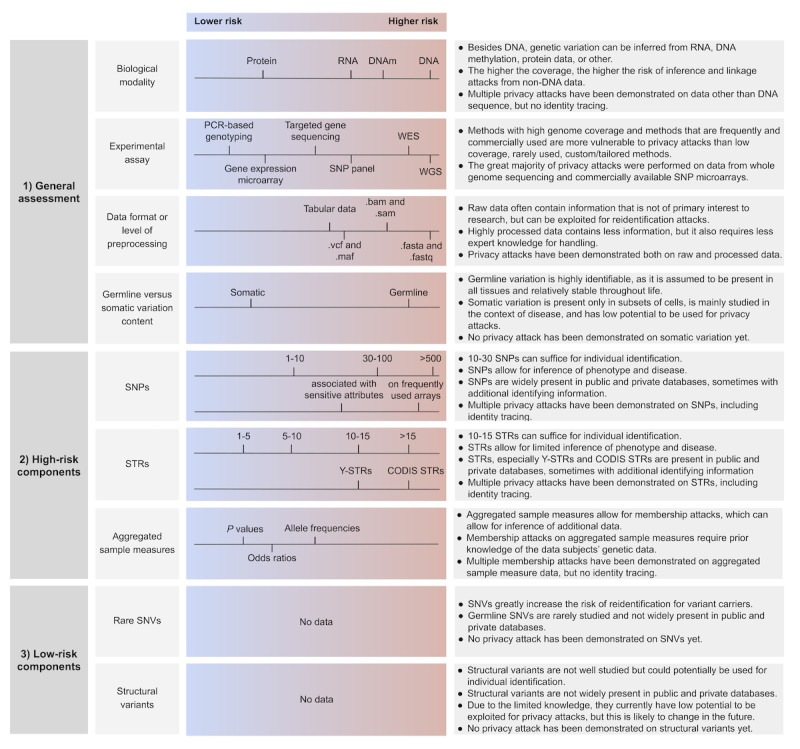
Overview of the privacy-critical features of genetic data sets, with exemplary values and key points to consider for risk assessment. CODIS: Combined DNA Index System; SNP: single nucleotide polymorphism; SNV: single nucleotide variant; STR: short tandem repeat; WES: whole exome sequencing; WGS: whole genome sequencing; Y-STR: short tandem repeat on the Y chromosome.
The first 4 features are general categorizations of the genomic data set and serve as a very rough estimate of the amount of privacy-critical information in the data.
The next 3 features are specific genomic features that are known to be a high risk for privacy. Their assessment is critical for estimating the reidentification risk.
The last 2 features are genomic features that have not been exploited for privacy attacks yet but should still be considered and could present a risk if they are present to a high degree in the data.
We summarize our findings in an overview figure, which lists the 9 features and their relevance for privacy. While it is challenging to define clear risk thresholds, there is a recognized need for practical guidance and orientation. To address this, we provide a scale that ranges from lower to higher risk and offer illustrative examples derived from the overview of privacy attack studies. These scales and examples serve as the initial guidance for risk assessment, emphasizing their purpose as guiding principles rather than exact measurements. The assessment of each individual feature is intricate and thoroughly explained in the corresponding sections. In addition, while the scales offer a framework to compare and assess different features, it is crucial to consider all features comprehensively to arrive at a conclusive assessment. Furthermore, the text sections highlight important interactions that arise from the comprehensive evaluation of these features.
Table S1 in Multimedia Appendix 1 presents a detailed description of the original attack studies.
Evidence of Privacy Risks in Genetic Data
Part 1. General Assessment
Biological Modality
While most privacy attacks have been demonstrated on DNA sequence data, other types of molecular data (eg, DNA methylation data or data derived from RNA) are also considered genetic data under General Data Protection Regulation, can also be identifiable, and have also been exploited for attacks [58-67]. Attacks on these types of data are performed mainly by 3 mechanisms. The first mechanism is direct extraction of DNA sequence from raw or low-processed data. This is possible, because even if not of primary interest, DNA sequence information is often a by-product of gene expression or DNA methylation studies [68-70]. For example, Gürsoy et al [70] demonstrated how genetic variants can be called from raw RNA sequencing data. The second mechanism is inference of DNA sequence, for example, through known associations of genetic sequence and gene expression or other modalities. For example, Schadt et al [65] used gene expression data of individuals (40,000 transcript counts) to infer genetic variants (1000 SNPs), which allowed them to determine with high certainty whether individuals with known SNPs were members of a gene expression study cohort (N=378). They also assessed the success rate of matching gene expression records to SNP records in a simulated cohort of 300 million individuals and correctly matched 97.1% of the records, demonstrating the feasibility of cross-linking these data types, which since then has been confirmed in additional studies [60,62,63]. Less literature has been published on other types of data, such as protein or epigenetic data (eg, DNA methylation), but similar proof of concept of cross-linkage to SNP data has been demonstrated in prior studies [58-60,63,64,66,67,71]. In the third mechanism, sensitive information such as disease phenotypes, demographic information, and behavioral traits is inferred from gene expression, protein levels, or other modalities (eg, age [72], cigarette smoking, and alcohol consumption [59] from DNA methylation).
However, such inference and linkage are not error free. For example, in the study by Schadt et al [65], the accuracy of the imputed SNPs from gene expression data was low (average Pearson correlation coefficient was 0.35 between true and inferred genotype). It is not clear whether such imputed data could be used for privacy attacks in the real world, such as in an identity tracing attack (eg, via upload of the imputed genetic data to GEDmatch or other). Considering that previous successful identity tracing attacks have used >500,000 SNPs [6], the inference of 1000 SNPs (with errors) may not be sufficient for such an attack. If the reconstruction of a larger set of SNPs were attempted, it is likely that the initial imputation error would propagate and thereby reduce the probability of a successful identity tracing attack. Furthermore, Schadt et al [65] reported much lower matching performance if training and test data stem from different array manufacturers, a scenario that is likely to occur in real-world data. Finally, although biological associations between genomic variants and gene expression are publicly accessible, substantial expert knowledge is still required for accessing this information and implementing the attack. Similar limitations apply to all the aforementioned studies. Altogether, data sets of RNA, protein, or epigenetic data, especially if they are large (eg, genome-wide), do allow for linkage and inference attacks. However, true reidentification would require matching the inferred genetic or phenotypic information to databases with identifying or quasi-identifying information in a next step, and no such full identity tracing attack starting with data other than DNA sequence has been demonstrated yet.
The guiding questions in this context are as follows:
Do the data contain DNA sequence information directly (eg, DNA sequencing reads)? If yes, could the data be processed such that sequence information is no longer available (eg, report DNA methylation levels in percentage instead of providing raw sequencing read files)?
Could DNA sequence information be inferred from the data (eg, via biological correlations such as expression or methylation quantitative trait loci)?
What sensitive information could be inferred from the data (eg, age, sex, diseases, or physical traits)?
Experimental Assay
Knowing the experimental assay that was used to generate the data can already provide a first estimate of its information content and linkability. For example, sequencing-based assays generally produce very rich data (eg, high genome coverage and high precision, such as whole genome DNA sequencing), whereas polymerase chain reaction–based genotyping assays provide more sparse data (eg, information on only 1 nucleotide of the DNA sequence). However, genome coverage alone (ie, the percentage of all base pairs or loci of the genome covered by the method) is not a reliable proxy for privacy risk. In some circumstances, a data set with only 10 sequenced positions of the DNA could in fact be more critical than a data set containing hundreds of positions, if those 10 positions are in highly identifiable loci. However, as a very rough indicator of information content, we believe it is still valuable to consider the genome coverage of the data as one of many factors in the risk assessment. In many cases, the rule of thumb that more sequence information equals higher information content and hence risk of cross-linking, inference, and reidentification is true. Nevertheless, these aspects need to be carefully evaluated together with the biological modality of the data, the level of processing, and the specific content of the data.
It is also important to consider that data produced with frequently used methods, such as commercially available kits (eg, SNP microarrays), often target the same genetic variants that are also interrogated by DTC-GT companies and genome-wide disease association studies and can thus more easily be linked to public data and exploited for privacy attacks than data generated with tailor-made, targeted analysis methods (refer to the study by Lu et al [73] for an overview of genotyping arrays commonly used by direct-to-consumer companies). Finally, as nearby variants are more likely to be correlated, it is also important to consider how the genetic information in the data is spread across the genome. A targeted assay that reads all SNPs within a specific gene likely carries less information than an assay that interrogates the same number of SNPs distributed across the full genome, as nearby SNPs are more likely to be correlated [74]. In line with these arguments, the great majority of published privacy attacks were performed on data obtained from whole genome sequencing and commercially available SNP microarrays (ie, rich, genome-wide data in the order of hundreds of thousands of SNP loci from a commercial assay).
The guiding questions in this context are as follows:
Which method was used to generate the data? Does this method produce rich or sparse data? (What percentage of all base pairs or loci of the genome are covered by the method?)
How do the data produced with this method cover the genome (ie, genome-wide vs targeted approach)?
How likely is it that data generated with the same method are present in publicly available databases (ie, commercial assay vs custom)?
Data Format or Level of Processing
The format of the data gives some indication on its processing level and can thus help to estimate its information content. Genetic data processing consists of cleaning, filtering, normalizing, and reducing raw data to a version that contains only the information that is relevant for its intended use. Important standard formats in genomic sequencing experiments sorted from raw to processed are .fasta and .fastq (raw nucleobase reads); .bed, .bam, and .sam (reads aligned to reference genome); .vcf and .maf files (deviations from the reference genome only), whereas highly processed data are often represented in tabular (.csv and .tsv) or otherwise structured form (.json, .xml, or other) containing only variants or regions of interest. Raw or low-processed data (.fasta, .fastq, .bed, .bam, or .sam) often contain information that is not of primary interest to research but can be exploited for reidentification attacks (eg, raw read files from gene expression studies can contain genomic variant information [63]). While the possibilities for privacy attacks are greater in raw data, it is important to note that the required effort and expert knowledge for handling these data are usually higher than those for processed data, where genetic variants such as SNPs do not need to be extracted.
The guiding question in this context is as follows:
If the data are in a raw or semiprocessed format, do the data contain any information that is not directly relevant for their intended use?
Germline Versus Somatic Variation Content
Genetic variants found in an individual’s genome can be categorized into germline and somatic variants. This categorization is specific to individuals and depends on the heritability of the variant (ergo, its presence in the individual’s reproductive tissues). Heritable variants are categorized as germline (ie, present in germ and usually also in somatic cells) and nonheritable variants are categorized as somatic (ie, present in somatic cells only). In the context of genetic privacy, it is important to understand that germline variation comprises all variants that can be assumed to be present in every cell of the body, are not expected to change much throughout the lifetime of an individual, are inherited from parental DNA, and are expected to be passed to the offspring. Such variation can inform about identity, ancestry, and kinship and is, therefore, used by DTC-GT providers, forensics, and genetic genealogy services. The most prominent example for germline variation are SNPs, as variation found at known SNP loci is generally assumed to be germline. (However, the terms germline variants and SNPs cannot be used interchangeably, as they refer to different concepts: germline describes the heritability, and SNP describes the type of variant and its frequency in the population.) Overall, germline variants are not only highly relevant for individual identification because of their stability and omnipresence across tissues but are also of great interest for scientific research. Associations of germline variants to disease, physical traits, or other biomedical modalities are well studied, with results being publicly accessible. As such, germline variants are vulnerable to identity, inference, and linkage attacks, and indeed, all the reviewed privacy attacks targeted germline variants.
In contrast, somatic variants are acquired during life (after fertilization) and are usually present only in specific, nonreproductive tissues or even only in single cells or cell populations. They are intensively studied in the context of diseases (eg, cancer), and as they are often found to be associated with diseases, data on somatic variants could be used to infer sensitive attributes about data subjects. However, their low association with identity and use limited to clinical diagnostics and scientific research makes it very difficult to cross-link them to databases with identifying or quasi-identifying information. DTC-GT companies, forensics services, or genetic genealogy services do not use somatic variants to determine identity, familial relations, or ancestry, as somatic variation is neither stable nor present in all tissues and cells (usually found only in a fraction of cells analyzed in a sample). A linkage attack based on somatic variation would require a matching data record of the same tissue, ideally taken at a similar time in life, which is unlikely to exist for most cases (as somatic variant patterns can change rapidly, eg, in cancer tissue). No identity tracing, inference, or membership attack based on somatic variation data has been published yet, and considering its low potential for identifiability, somatic variation data can currently be considered a low risk for reidentification attacks.
To determine whether a variant is germline or somatic, one would ideally analyze multiple samples from one individual to determine whether the variant is present in germ cells or only in specific somatic cells. In practice, experts can assess the status of a variant from its sequencing read signal (determining whether it is present in all cells of the sample or only in a few), genomic location, and type alone by comparing it to public knowledge of known loci of germline and somatic variation or through computational approaches [75]. In processed genetic data, variants which are with high certainty germline have often already been identified and are indicated as such (eg, SNPs are identified by a specific reference SNP cluster ID, such as “rs343543”), whereas somatic variants are described by standard mutation nomenclature (eg, single nucleotide variants [SNVs] are described by the Human Genome Variation Society nomenclature, containing the reference genome used; the genomic location of the variant; the nucleotide in the reference sequence; and the detected nucleotide, such as “NC_000023.9:g.32317682G>A”). Furthermore, the type of tissue that was used to generate genetic data, most importantly whether samples were taken from healthy or tumor tissue, can also give some indication on the amount of germline variation included in the data. When analyzing tumor tissue data, germline variations such as SNPs are typically removed during processing, as the focus is on studying somatic variation. However, especially if the data are raw and unfiltered, they often contain germline variants irrespective of whether they were taken from healthy or tumor tissue and must hence be considered a higher risk for reidentification. Therefore, while data that are both derived from tumor tissues and highly processed are often a low privacy risk, the amount of information on germline variation that is contained in the data needs to be assessed case by case. Public databases (eg, dbSNP, hosted by the National Institutes of Health’s National Center for Biotechnology Information) store information about the genomic locations and population frequencies of SNPs and can be used to search data for this important type of germline variation.
The guiding questions in this context are as follows:
Was germline or somatic variation of primary interest when generating or processing the data?
If somatic variation was of primary interest, was germline variation removed from the data?
Part 2. High-Risk Components
SNPs
SNPs are germline SNVs that are present in >1% of the population. They are highly relevant features for individual reidentification and the most privacy-critical component of genetic data sets. Because SNPs usually have 2 different states (ie, a common or reference and a rare nucleotide) and human somatic cells have 2 DNA copies (ie, are diploid), an individual usually has 1 of 3 different states at a SNP locus, often represented as 0,1, and 2 (0 represents 2 copies of the common variant [ie, homozygous for major allele], 1 represents 1 copy of the common variant and 1 copy of the rare variant [heterozygous], and 2 represents 2 copies of the rare variant [homozygous for minor allele]). Knowing an individual’s state at 30 to 80 statistically independent SNPs (or a random set of approximately 300 SNPs) can suffice for individual identification [76-79], yet commonly used SNP or genome sequencing assays often read hundreds of thousands of SNPs at once. As germline variation, SNPs are assumed to be stable and present in every cell of the body, signifying that they can identify individuals across samples taken at different times or from different tissues. As they are heritable, DTC-GT providers and forensic institutes compare SNP patterns of individuals to determine familial relations and ancestry [80]. Furthermore, SNPs are associated with physiological traits (eg, skin, hair and eye color [2,3], facial features [81], BMI [82], and height [4]), ethnicity [1], and susceptibility to diseases [5], making them central to research and genetic testing (refer to the study by Dabas et al [83] for a review of association of SNPs with externally visible characteristics).
SNP data can be directly used for reidentification by matching it to publicly accessible databases, as demonstrated in the reidentification attack by Erlich et al [6], who uploaded SNP data (700,000 SNPs) from an anonymous study participant to the genetic genealogy website GEDmatch and identified the participant’s surname through matches with relatives. Such identity tracing attacks are possible because millions of people send their DNA to DTC-GT companies such as AncestryDNA, 23andMe, FamilyTreeDNA, or MyHeritage [84], and many also decide to share their genetic data on publicly accessible websites, such as GEDmatch, the Personal Genome Project [85], or OpenSNP [86]. Enabling individuals to identify and contact relatives, learn about their ancestry, disease predispositions, and contribute their data to research, these platforms often contain genetic data accompanied by information about an individual’s diseases and traits or even personal data such as place of residence, age, sex, surname, or phone number. In addition, there is a wealth of publicly accessible knowledge on associations of SNPs with physical features, diseases, other genetic variants or genetic modalities (eg, gene expression and DNA methylation; eg, dbSNP database [87], the GWAS catalog [5], the International Genome Sample Resource from the 1000 Genomes Project [88], and data from the HapMap project [89]), which can and have been exploited for completion and inference attacks (eg, inference of additional genetic variation in genomic regions that were not studied originally, other biomedical modalities such as gene expression and DNA methylation, or physical attributes [9,90-96]). For example, Humbert et al [92] predicted phenotypic traits (eye, hair and skin color, blood type, and more) of individuals from their SNP data (20 SNPs) using publicly available knowledge on SNP-phenotype associations from the public database SNPedia and used this information to cross-link individuals between genetic and phenotypic data sets. In addition, Humbert et al [92] inferred additional and sensitive information (eg, susceptibility to Alzheimer disease) from the SNP data. However, this linkage attack had a success rate of only 5% (ie, proportion of correctly matched individuals) in a data set of 80 individuals and is likely to perform worse in more realistic scenarios with larger data sets. Nyholt et al [9] imputed the status of multiple risk variants for Alzheimer disease in the published genome of Dr James Watson [94] from SNPs in nearby genomic regions, although the respective gene had been masked. Edge et al [90] cross-linked individuals in SNP and short tandem repeat (STR) data sets, a highly identifiable type of genetic variation that is used in forensics, by imputing STR from SNP data (642,563 loci). In a highly debated study, Lippert et al [93] developed a model to predict phenotypic traits (facial structure, voice, eye color, skin color, age, sex, height, and BMI) from whole genome sequencing (WGS) data containing >6 million SNPs and used it to cross-link high-resolution face photographs of individuals to their genetic data in a cohort of 1061 study participants. In a real-life scenario, photos and personal data from social media could be exploited for such an attack and matched to the inferred phenotype. However, it has been argued that the predictive power in this study stems mainly from the estimation of the participant’s ancestry and sex [97] and that the attack is unlikely to be successful in the real world and with more realistic, lower-quality images [98]. Furthermore, large, genome-wide association studies indicate that the currently known associations between SNPs and facial structure, voice, height, and BMI are too small to be useful for accurate phenotype prediction on an individual level; however, this will likely improve in the future. Nevertheless, other characteristics, such as ancestry, eye, hair color, and skin color, can be inferred from specific SNPs with high accuracy, and corresponding DNA phenotyping kits are already commercially available and used in forensics today [99]. As a small number of SNPs can already uniquely identify an individual and SNPs are widely available in public databases together with identifying and quasi-identifying information, SNPs must be considered a high risk for privacy and data sanitization efforts (eg, as proposed by Emani et al [100]) should be used in any genetic data set containing >20 SNPs.
The guiding questions in this context are as follows:
How many SNPs do the data contain (directly or indirectly)?
Are the SNPs in close proximity or spread across the genome (nearby SNPs are more likely to be correlated and thus often contain less information than statistically independent SNPs)?
Are the interrogated SNPs frequently assessed in research or by DTC-GT providers (ie, how likely is it that they can be linked to publicly available, identifying data sets)? The study by Lu et al [73] presents an overview of genotyping arrays commonly used by direct-to-consumer companies.
Are all SNPs relevant to the intended use of the data or could some be removed from the data?
What sensitive information could be inferred from the data (eg, diseases and physical traits)?
Could additional DNA sequence information be inferred from the data (eg, association with STRs or other)?
STRs
The human genome contains more than half a million regions of repetitive units of 2 to 6 bases, the so-called STRs or microsatellites [101]. The number of repeats in these regions is highly variable across individuals and can affect protein function or expression or be linked to medical conditions or physical traits [102]. Knowing the repeat numbers of as little as 10 to 30 STRs can suffice for individual identification. Because of their high identifiability, STRs are used to determine identity and kinship in forensics, law enforcement, paternity testing, and genetic genealogy. For example, the Combined DNA Index System (CODIS; a set of 20 STRs) is used to connect suspects to crime scenes or establish identity of missing persons. While CODIS STRs are usually not of interest in research studies or genetic genealogy, STRs on the Y chromosome (ie, Y-STRs, only present in male individuals) are included in several DTC-GT kits, where they are used to identify relatives along the paternal ancestry line (eg, “Y-STR Testing” by FamilyTreeDNA). Consequently, several large databases of STR loci with accompanying identifying and quasi-identifying information exist (eg, mitoYDNA from mitoYDNA Ltd). In addition, the CODIS forensic database and analysis software contains genetic data and identifying information from >14 million individuals in the United States alone [103].
Several studies demonstrate reidentification attacks on Y-STRs. Gitschier et al [104] provided first evidence for surname inference from Y-STRs by matching genetic STR profiles of anonymous study participants from the international HapMap project [89] to 2 genetic genealogy databases (Ysearch and Sorenson Molecular Genealogy Foundation [SGMF]). Later, Gymrek et al [105] demonstrated that it is not only possible to infer surnames from STR data (eg, 34 Y-STR loci extracted from WGS data) but also to triangulate the actual identity of data subjects with high probability using publicly accessible genealogy databases, record search engines, obituaries, and genealogical websites. The authors attempted this for 10 study participants of the 1000 Genomes Project and correctly identified 5 out of 10 individuals. It is important to note that STR data can also be fortuitously included in genetic data derived from targeted gene or WGS, even if they are not of primary interest for the study. Moreover, STR markers can be imputed from genetic data sets that do not even cover STR regions by exploiting known associations between SNPs and STRs [90]. While the authors of this study report a low imputation accuracy for STRs from SNPs (likely too low to reliably impute full STR profiles even from large SNP data), they did demonstrate the ability to cross-link records across SNP and STR databases. In detail, they correctly matched 90% to 98% of paired SNP (642,563 loci) and STR data records (13 STRs) to each other, and such successful linkage has also been demonstrated elsewhere [106].
Due to the high association of STRs with identity, any genetic data that directly (eg, repeat numbers for specific STR regions) or indirectly (eg, WGS data covering STR regions) contain >10 STR regions could be considered identifiable. However, the actual risk of reidentification depends on the availability of STR databases with identifying and quasi-identifying information and the ability to cross-link records. It is important to note that the databases used in the seminal study by Gymrek et al [105] (ie, Ysearch and SGMF) are no longer available (Ysearch, belonging to FamilyTreeDNA, closed in 2018, and SGMF, belonging to Ancestry, was shut down in 2015), and access to the CODIS database is restricted to criminal justice agencies for law enforcement identification purposes. However, databases from DTC-GT providers (eg, FamilyTreeDNA) and public platforms (eg, mitoYDNA) are still available and allow uploading results from third-party providers; therefore, an attacker could fabricate a genetic testing result from STR data [107,108] and reproduce the demonstrated surname inference attacks. From information about possible surnames, sex, and residence inferred from matches on the platform, the triangulation of identity could be possible with the help of additional publicly available resources [105,109]. However, such an attack would only be possible on male data records (ie, Y chromosome based) and is not guaranteed to find matches that allow surname inference; the success rate in the demonstrated attack was 11.9% (109/911 cases), and the 2 previous studies used >30 STR loci (all located in close vicinity of each other and on the Y chromosome). Furthermore, the know-how and effort necessary for such an attack is high. Finally, even if genetic matches or surnames are identified, the reconstruction of identity from surname is not trivial and can take months to complete, as others have pointed out [110]. Still, because of their high identifiability potential and their use in DTC-GT, paternity testing, and forensics, STRs should be removed from genetic data if they are not of primary interest and otherwise considered a high risk for privacy.
The guiding questions in this context are as follows:
Do the data directly or indirectly (eg, STRs in raw data and STRs imputable from SNPs) contain >10 STR loci?
Are these STR loci either (1) part of the CODIS system or (2) on the Y chromosome (ie, high linkability)?
Could additional DNA sequence information be inferred from the data (eg, association with SNPs or other)?
Aggregated Sample Measures
Aggregated sample measures, that is, variables that are the result of aggregating genetic data across multiple samples can also be exploited for privacy attacks (reviewed by Craig et al [111]). The most prominent examples are summary statistics from association studies such as SNP frequencies, odds ratios, or correlation coefficients. However, the limited information content in these summary statistics usually only allows for membership attacks, that is, assessing whether an individual of known genetic background is part of a study group or database or not [112-114]. Multiple studies demonstrate such an attack [113,115-119], although Homer et al [114] were the first to explain how membership of an individual in a mixture can be predicted from the reported SNP allele frequencies (ie, if SNPs of that individual are known, in this case >10,000 SNPs). The authors accomplished this by comparing the reported study allele frequencies to allele frequencies in a reference cohort of similar ancestry (obtained from public resources) and detecting the bias introduced by the sample of interest. Their method performed well even if the individual’s contribution to the mixture was <1%, and this method can easily be extended to predicting membership from aggregated data from a study cohort. In response to that, the US National Institutes of Health has restricted the publication of aggregate GWAS results in their databases [120]; however, the feasibility of the attack has been critically discussed. Its power depends on the size and quality of the actual and reference cohorts, the number of reported SNP allele frequencies, prior knowledge of the attacker, and the fulfillment of several underlying assumptions, many of which are likely not fulfilled in practice [115,116,121,122]. Aside from membership attacks, it was also shown that aggregate results, such as linear models that have been fitted to study data or polygenic risk scores, can be exploited to predict sensitive attributes and genotypes via model inversion [28,123]. However, this attack required background information on the data subject and on the distribution of variables in the study data. Furthermore, its performance is limited by the predictive power and complexity of the fitted model. Membership and attribute inference attacks on aggregate data can reveal demographic, genetic, and phenotypic information (such as country or place of residence due to participation in a local study, ethnicity, disease, age group, or presence of specific genetic variants due to descriptions of inclusion or exclusion criteria in the cohort) and can thus facilitate linkage and identity tracing attacks, which is why they can be a risk for privacy. However, no identity tracing attack based on aggregate data has been demonstrated yet.
The guiding question in this context is as follows:
What sensitive information could an attacker gain from ascertaining the membership of an individual to the data set (eg, geographic information, sex, disease, and age)?
Part 3. Low-Risk Components
No privacy attack has been demonstrated on these components, but due to their high association with identifying and sensitive attributes, we recommend including them in the risk assessment.
Rare SNVs
Rare SNVs are single nucleotide substitutions that are present in <1% of the population. They may be somatic or germline and can be associated with pathological conditions and thus reveal sensitive information. Furthermore, while less informative than common SNVs (ie, SNPs) from an information theoretical standpoint, rare variants greatly increase the risk of reidentification for the small subpopulation of variant carriers. However, because of their low frequency in the population, germline SNVs are rarely the target of large scientific studies (eg, for phenotype or disease association) and have very limited use for ancestry and disease susceptibility analysis. Therefore, most DTC-GT providers and research studies specifically target regions of common genetic variation (eg, SNPs) and either use assays that do not detect SNVs or remove them during preprocessing, making it very unlikely that a set of SNVs could be linked to any database with quasi-identifying information. No identity tracing, completion, or inference attack has been published on SNVs yet; therefore, they can currently be viewed as a low risk for reidentification, despite their high theoretical potential for identifiability.
The guiding questions in this context are as follows:
What sensitive information could be inferred from the data (eg, diseases and physical traits)?
Could additional DNA sequence information be inferred from the data (eg, association with SNPs or other)?
Are there any databases that could be used to cross-link the data to identifiable data, and how accessible are the databases?
Structural Variants
The study of structural variants (SVs) in the human genome is in its early stages, but it is already clear that it accounts for even more individual variation than SNPs [124,125]. The best-studied type of SVs is copy number variation (CNV), that is, deletions and duplications of regions larger than 50 base pairs. CNVs can be used as measures of relatedness and identifiers of population origin [126], have a strong impact on gene expression [127], and could allow for the inference of physical features [128] and pathological conditions [129], thereby revealing sensitive information of data subjects. However, CNVs are still not well studied, and sequencing technologies have only recently progressed to a level that allows to capture their full scope in the human genome (reviewed by Mahmoud et al [124]). Most importantly, human CNV databases are very scarce in comparison to databases of SNVs (refer to the study by Ho et al [130] for an overview of the available human SV reference sets), and they are currently not used for genetic genealogy analyses, making it difficult to link CNVs across databases to obtain identifying information. A privacy attack based on CNVs or any other type of SV yet remains to be demonstrated. Finally, it is important to note that many SVs that are assessed in medical and research studies are somatic, that is, nonhereditary, not present in all cells of the body, not stable, and thus not strongly associated with identity. For example, tumor tissue is characterized by frequent and dynamic changes in SVs (eg, CNVs in tumor tissue, also referred to as CNAs), which are likely neither directly nor indirectly identifiable. Therefore, the risk of reidentification from SVs can currently be considered low, but the growth of public databases and their use in genealogical or clinical research should be monitored. The same holds true for common SVs, such as CNVs that occur in >1% of the population and are hence classified as polymorphisms (ie, CNPs). Little is known about the population frequencies of CNVs, and while public databases are growing, no privacy attack based on CNPs has been demonstrated yet. Due to the limited knowledge about CNPs or other common SVs in the population, their presence in genetic data is difficult to assess, and they can be considered a low risk for reidentification at the current time.
The guiding questions in this context are as follows:
What sensitive information could be inferred from the data (eg, diseases and physical traits)?
Could additional DNA sequence information be inferred from the data (eg, association with SNPs or other)?
Are there any databases that could be used to cross-link the data to identifiable data, and how accessible are the databases?
Discussion
Limitations
It is important to acknowledge some key limitations of our review. First, it is possible that we may have missed relevant studies. This is particularly true for recent research, as our search was confined to original studies referenced in existing reviews. While the search strategy was designed to retrieve the most pertinent studies, it carries the risk of overlooking lesser-known or very recent studies. Therefore, we recommend conducting periodic reviews to stay updated with scientific advancements and changes in the availability of public genetic data that may contain (indirectly) identifying information susceptible to identity tracing attacks. Second, even under the assumption that all relevant literature was considered, it is still possible that we may have overlooked certain vulnerabilities. This is known as the “proof of nonexistence fallacy”—the absence of evidence for risk does not imply the absence of those risks. Finally, it was necessary to balance our aim of providing a comprehensive and evidence-based overview of genetic privacy vulnerabilities with our aim of providing practical and useful guidance. Therefore, we provide both a detailed assessment (refer to the Results section and Table S1 in Multimedia Appendix 1) as well as a simplified overview (Figure 2). However, this trade-off necessitated compromises in practical utility on one hand and scientific exhaustiveness on the other hand.
Conclusions
On the basis of the findings of this review, it can be argued that the privacy risks of genetic data vary greatly between data sets. Considering all genetic data at all times as information relating to an identifiable natural person is not correct, and it is becoming apparent that reidentification risk in genetic data must be assessed on a case-by-case basis and under the consideration of all the means reasonably likely to be used [131]. However, while efforts are underway [132], no practical guidelines or recommendations for performing such a reidentification risk assessment on genetic data have been proposed yet. On the basis of a review of the scientific literature on privacy attacks on genetic data, we provide an overview of genetic data privacy risks that can guide data processors in risk assessment by providing the necessary background knowledge and an overview of the existing evidence. We believe that a careful examination of the 9 described features in the data set at hand (biological modality or type of data, experimental assay, data format or level of processing, germline vs somatic variation content, content of SNPs, STRs, aggregated sample measures, rare SNVs, and SVs) provides a strong foundation for a data risk assessment. While completely eliminating the possibility of reidentification is rarely achievable, a more practical approach of risk minimization is warranted [133,134], accompanied by organizational and technical measures to safeguard genetic data from reidentification attack attempts and a transparent communication of the remaining risks to data subjects.
Acknowledgments
The authors would like to thank Florian Schneider for reviewing the manuscript.
Abbreviations
- CNV
copy number variation
- CODIS
Combined DNA Index System
- DTC-GT
direct-to-consumer genetic testing
- SGMF
Sorenson Molecular Genealogy Foundation
- SNP
single nucleotide polymorphism
- SNV
single nucleotide variant
- STR
short tandem repeat
- SV
structural variant
- Y-STR
short tandem repeat on the Y chromosome
List of identified reviews and a table with the description and evaluation of original privacy attack studies.
PRISMA checklist.
Footnotes
Conflicts of Interest: NM was contracted by Roche Diagnostics GmbH, Penzberg, Germany, while contributing to this work. All other authors declare no other conflicts of interest.
References
- 1.Huang T, Shu Y, Cai YD. Genetic differences among ethnic groups. BMC Genomics. 2015 Dec 21;16:1093. doi: 10.1186/s12864-015-2328-0. https://bmcgenomics.biomedcentral.com/articles/10.1186/s12864-015-2328-0 .10.1186/s12864-015-2328-0 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Simcoe M, Valdes A, Liu F, Furlotte NA, Evans DM, Hemani G, Ring SM, Smith GD, Duffy DL, Zhu G, Gordon SD, Medland SE, Vuckovic D, Girotto G, Sala C, Catamo E, Concas MP, Brumat M, Gasparini P, Toniolo D, Cocca M, Robino A, Yazar S, Hewitt A, Wu W, Kraft P, Hammond CJ, Shi Y, Chen Y, Zeng C, Klaver CC, Uitterlinden AG, Ikram MA, Hamer MA, van Duijn CM, Nijsten T, Han J, Mackey DA, Martin NG. Genome-wide association study in almost 195,000 individuals identifies 50 previously unidentified genetic loci for eye color. Sci Adv. 2021 Mar;7(11):eabd1239. doi: 10.1126/sciadv.abd1239. https://www.science.org/doi/abs/10.1126/sciadv.abd1239?url_ver=Z39.88-2003&rfr_id=ori:rid:crossref.org&rfr_dat=cr_pub0pubmed .7/11/eabd1239 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 3.Pavan WJ, Sturm RA. The genetics of human skin and hair pigmentation. Annu Rev Genomics Hum Genet. 2019 Aug 31;20:41–72. doi: 10.1146/annurev-genom-083118-015230. [DOI] [PubMed] [Google Scholar]
- 4.Yengo L, Vedantam S, Marouli E, Sidorenko J, Bartell E, Sakaue S, Graff M. A saturated map of common genetic variants associated with human height. Nature. 2022 Oct;610(7933):704–712. doi: 10.1038/s41586-022-05275-y. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Buniello A, MacArthur JA, Cerezo M, Harris LW, Hayhurst J, Malangone C, McMahon A, Morales J, Mountjoy E, Sollis E, Suveges D, Vrousgou O, Whetzel PL, Amode R, Guillen JA, Riat HS, Trevanion SJ, Hall P, Junkins H, Flicek P, Burdett T, Hindorff LA, Cunningham F, Parkinson H. The NHGRI-EBI GWAS catalog of published genome-wide association studies, targeted arrays and summary statistics 2019. Nucleic Acids Res. 2019 Jan 08;47(D1):D1005–12. doi: 10.1093/nar/gky1120. https://europepmc.org/abstract/MED/30445434 .5184712 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6.Erlich Y, Shor T, Pe'er I, Carmi S. Identity inference of genomic data using long-range familial searches. Science. 2018 Nov 09;362(6415):690–4. doi: 10.1126/science.aau4832. https://europepmc.org/abstract/MED/30309907 .science.aau4832 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.Greytak EM, Moore C, Armentrout SL. Genetic genealogy for cold case and active investigations. Forensic Sci Int. 2019 Jun;299:103–13. doi: 10.1016/j.forsciint.2019.03.039.S0379-0738(19)30126-4 [DOI] [PubMed] [Google Scholar]
- 8.Kennett D. Using genetic genealogy databases in missing persons cases and to develop suspect leads in violent crimes. Forensic Sci Int. 2019 Aug;301:107–17. doi: 10.1016/j.forsciint.2019.05.016.S0379-0738(19)30201-4 [DOI] [PubMed] [Google Scholar]
- 9.Nyholt DR, Yu CE, Visscher PM. On Jim Watson's APOE status: genetic information is hard to hide. Eur J Hum Genet. 2009 Feb;17(2):147–9. doi: 10.1038/ejhg.2008.198. https://europepmc.org/abstract/MED/18941475 .ejhg2008198 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 10.Erlich Y, Narayanan A. Routes for breaching and protecting genetic privacy. Nat Rev Genet. 2014 Jun;15(6):409–21. doi: 10.1038/nrg3723. https://europepmc.org/abstract/MED/24805122 .nrg3723 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 11.El Emam K, Jonker E, Arbuckle L, Malin B. A systematic review of re-identification attacks on health data. PLoS One. 2011;6(12):e28071. doi: 10.1371/journal.pone.0028071. https://dx.plos.org/10.1371/journal.pone.0028071 .PONE-D-11-14348 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 12.Mohammed Yakubu A, Chen YP. Ensuring privacy and security of genomic data and functionalities. Brief Bioinform. 2020 Mar 23;21(2):511–26. doi: 10.1093/bib/bbz013.5309007 [DOI] [PubMed] [Google Scholar]
- 13.Joly Y, Dalpe G. Genetic discrimination still casts a large shadow in 2022. Eur J Hum Genet. 2022 Dec;30(12):1320–2. doi: 10.1038/s41431-022-01194-8. https://europepmc.org/abstract/MED/36163420 .10.1038/s41431-022-01194-8 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 14.Tiller J, Lacaze P. Australians can be denied life insurance based on genetic test results, and there is little protection. The Conversation. 2017. Aug 24, [2024-04-05]. https://theconversation.com/australians-can-be-denied-life-insurance-based-on-genetic- test-results-and-there-is-little-protection-81335 .
- 15.Humbert M, Ayday E, Hubaux JP, Telenti A. Addressing the concerns of the lacks family: quantification of kin genomic privacy. Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security; CCS '13; November 4-8, 2013; Berlin, Germany. 2013. pp. 1141–52. https://dl.acm.org/doi/10.1145/2508859.2516707 . [DOI] [Google Scholar]
- 16.Deznabi I, Mobayen M, Jafari N, Tastan O, Ayday E. An inference attack on genomic data using kinship, complex correlations, and phenotype information. IEEE/ACM Trans Comput Biol Bioinform. 2018;15(4):1333–43. doi: 10.1109/TCBB.2017.2709740. [DOI] [PubMed] [Google Scholar]
- 17.Trost B, Loureiro LO, Scherer SW. Discovery of genomic variation across a generation. Hum Mol Genet. 2021 Oct 01;30(R2):R174–86. doi: 10.1093/hmg/ddab209. https://europepmc.org/abstract/MED/34296264 .6325570 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 18.EDPB documenton response to the request from the European commission for clarifications on the consistent application of the GDPR, focusing on health research. European Data Protection Board. 2021. [2024-04-05]. https://edpb.europa.eu/sites/default/files/files/file1/edpb_replyec_questionnaireresearch_final.pdf .
- 19.Global Alliance for Genomics and Health GENOMICS. A federated ecosystem for sharing genomic, clinical data. Science. 2016 Jun 10;352(6291):1278–80. doi: 10.1126/science.aaf6162.352/6291/1278 [DOI] [PubMed] [Google Scholar]
- 20.Shringarpure SS, Bustamante CD. Privacy risks from genomic data-sharing beacons. Am J Hum Genet. 2015 Nov 05;97(5):631–46. doi: 10.1016/j.ajhg.2015.09.010. https://linkinghub.elsevier.com/retrieve/pii/S0002-9297(15)00374-2 .S0002-9297(15)00374-2 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 21.von Thenen N, Ayday E, Cicek AE. Re-identification of individuals in genomic data-sharing beacons via allele inference. Bioinformatics. 2019 Feb 01;35(3):365–71. doi: 10.1093/bioinformatics/bty643.5056754 [DOI] [PubMed] [Google Scholar]
- 22.Raisaro JL, Tramèr F, Ji Z, Bu D, Zhao Y, Carey K, Lloyd D, Sofia H, Baker D, Flicek P, Shringarpure S, Bustamante C, Wang S, Jiang X, Ohno-Machado L, Tang H, Wang X, Hubaux J. Addressing Beacon re-identification attacks: quantification and mitigation of privacy risks. J Am Med Inform Assoc. 2017 Jul 01;24(4):799–805. doi: 10.1093/jamia/ocw167. https://europepmc.org/abstract/MED/28339683 .3038412 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 23.Ayoz K, Ayday E, Cicek AE. Genome reconstruction attacks against genomic data-sharing beacons. Proc Priv Enhanc Technol. 2021;2021(3):28–48. doi: 10.2478/popets-2021-0036. https://europepmc.org/abstract/MED/34746296 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 24.Fienberg SE, Slavkovic A, Uhler C. Privacy preserving GWAS data sharing. Proceedings of the 2011 IEEE 11th International Conference on Data Mining Workshops; ICDMW '11; December 11, 2011; Washington, DC. 2011. pp. 628–35. https://dl.acm.org/doi/10.1109/ICDMW.2011.140 . [DOI] [Google Scholar]
- 25.Huang Z, Ayday E, Fellay J, Hubaux JP, Juels A. GenoGuard: protecting genomic data against brute-force attacks. Proceedings of the 2015 IEEE Symposium on Security and Privacy; SP '15; May 17-21, 2015; San Jose, CA. 2015. pp. 447–62. https://ieeexplore.ieee.org/document/7163041 . [DOI] [Google Scholar]
- 26.Wang Y, Wen J, Wu X, Shi X. Infringement of individual privacy via mining differentially private GWAS statistics. Proceedings of the 2nd International Conference on Big Data Computing and Communications; BigCom '16; July 29-31, 2016; Shenyang, China. 2016. pp. 29–31. https://link.springer.com/chapter/10.1007/978-3-319-42553-5_30 . [DOI] [Google Scholar]
- 27.Cavallaro L, Kinder J, Domingo-Ferrer J, Oprisanu B, Dessimoz C, Cristofaro ED. How much does Genoguard really "guard"?: an empirical analysis of long-term security for genomic data. Proceedings of the 18th ACM Workshop on Privacy in the Electronic Society; WPES '19; November 11, 2019; London, UK. 2019. pp. 93–105. https://tinyurl.com/4w8sxk6f . [DOI] [Google Scholar]
- 28.Fredrikson M, Lantz E, Jha S, Lin S, Page D, Ristenpart T. Privacy in pharmacogenetics: an end-to-end case study of personalized warfarin dosing. Proc USENIX Secur Symp. 2014 Aug;2014:17–32. https://europepmc.org/abstract/MED/27077138 . [PMC free article] [PubMed] [Google Scholar]
- 29.Oprisanu B, Ganev G, Cristofaro ED. On utility and privacy in synthetic genomic data. Proceedings of the 2022 Network and Distributed Systems Security; NDSS '22; April 24-28, 2022; San Diego, CA. 2022. pp. 1–18. https://www.ndss-symposium.org/wp-content/uploads/2022-92-paper.pdf . [DOI] [Google Scholar]
- 30.Mittos A, Malin B, Cristofaro ED. Systematizing genome privacy research: a privacy-enhancing technologies perspective. Proc Priv Enhancing Technol. 2019;(1):87–107. doi: 10.2478/popets-2019-0006. https://petsymposium.org/2019/files/papers/issue1/popets-2019-0006.pdf . [DOI] [Google Scholar]
- 31.Martinez C, Jonker E. A practical path towards genetic privacy in the United States. Future of Privacy Forum. 2020. [2022-10-31]. https://fpf.org/wp-content/uploads/2020/04/APracticalPathTowardGeneticPrivacy_April2020.pdf .
- 32.Bernier A, Liu H, Knoppers BM. Computational tools for genomic data de-identification: facilitating data protection law compliance. Nat Commun. 2021 Nov 29;12(1):6949. doi: 10.1038/s41467-021-27219-2. doi: 10.1038/s41467-021-27219-2.10.1038/s41467-021-27219-2 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 33.The GDPR and genomic data - the impact of the GDPR and DPA 2018 on genomic healthcare and research. PHG Foundation. 2020. [2024-04-05]. https://tinyurl.com/dfk7e3xs .
- 34.Wagner I. Evaluating the strength of genomic privacy metrics. ACM Trans Priv Secur. 2017 Jan 09;20(1):1–34. doi: 10.1145/3020003. [DOI] [Google Scholar]
- 35.Abinaya B, Santhi S. A survey on genomic data by privacy-preserving techniques perspective. Comput Biol Chem. 2021 Aug;93:107538. doi: 10.1016/j.compbiolchem.2021.107538. [DOI] [PubMed] [Google Scholar]
- 36.Azencott CA. Machine learning and genomics: precision medicine versus patient privacy. Philos Trans A Math Phys Eng Sci. 2018 Sep 13;376(2128):20170350. doi: 10.1098/rsta.2017.0350.rsta.2017.0350 [DOI] [PubMed] [Google Scholar]
- 37.Ayday E, Humbert M. Inference attacks against kin genomic privacy. IEEE Secur Privacy. 2017;15(5):29–37. doi: 10.1109/msp.2017.3681052. [DOI] [Google Scholar]
- 38.Aziz MM, Sadat MN, Alhadidi D, Wang S, Jiang X, Brown CL, Mohammed N. Privacy-preserving techniques of genomic data-a survey. Brief Bioinform. 2019 May 21;20(3):887–95. doi: 10.1093/bib/bbx139. https://europepmc.org/abstract/MED/29121240 .4600334 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 39.Berger B, Cho H. Emerging technologies towards enhancing privacy in genomic data sharing. Genome Biol. 2019 Jul 02;20(1):128. doi: 10.1186/s13059-019-1741-0. https://genomebiology.biomedcentral.com/articles/10.1186/s13059-019-1741-0 .10.1186/s13059-019-1741-0 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 40.Bonomi L, Huang Y, Ohno-Machado L. Privacy challenges and research opportunities for genomic data sharing. Nat Genet. 2020 Jul 29;52(7):646–54. doi: 10.1038/s41588-020-0651-0. https://europepmc.org/abstract/MED/32601475 .10.1038/s41588-020-0651-0 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 41.Carter AB. Considerations for genomic data privacy and security when working in the cloud. J Mol Diagn. 2019 Jul;21(4):542–52. doi: 10.1016/j.jmoldx.2018.07.009. https://linkinghub.elsevier.com/retrieve/pii/S1525-1578(17)30596-2 .S1525-1578(17)30596-2 [DOI] [PubMed] [Google Scholar]
- 42.Clayton EW, Halverson CM, Sathe NA, Malin BA. A systematic literature review of individuals' perspectives on privacy and genetic information in the United States. PLoS One. 2018 Oct 31;13(10):e0204417. doi: 10.1371/journal.pone.0204417. https://dx.plos.org/10.1371/journal.pone.0204417 .PONE-D-18-09954 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 43.Gürsoy G. Genome privacy and trust. Annu Rev Biomed Data Sci. 2022 Aug 10;5(1):163–81. doi: 10.1146/annurev-biodatasci-122120-021311. [DOI] [PubMed] [Google Scholar]
- 44.Knoppers BM, Beauvais MJ. Three decades of genetic privacy: a metaphoric journey. Hum Mol Genet. 2021 Oct 01;30(R2):R156–60. doi: 10.1093/hmg/ddab164. https://europepmc.org/abstract/MED/34155499 .6307333 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 45.May T. Sociogenetic risks — ancestry DNA testing, third-party identity, and protection of privacy. N Engl J Med. 2018 Aug 02;379(5):410–2. doi: 10.1056/nejmp1805870. [DOI] [PubMed] [Google Scholar]
- 46.Oestreich M, Chen D, Schultze JL, Fritz M, Becker M. Privacy considerations for sharing genomics data. EXCLI J. 2021;20:1243–60. doi: 10.17179/excli2021-4002. https://europepmc.org/abstract/MED/34345236 .2021-4002 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 47.Schwab AP, Luu HS, Wang J, Park JY. Genomic privacy. Clin Chem. 2018 Dec;64(12):1696–703. doi: 10.1373/clinchem.2018.289512.clinchem.2018.289512 [DOI] [PubMed] [Google Scholar]
- 48.Shen H, Ma J. Privacy challenges of genomic big data. Adv Exp Med Biol. 2017;1028:139–48. doi: 10.1007/978-981-10-6041-0_8. [DOI] [PubMed] [Google Scholar]
- 49.Shi X, Wu X. An overview of human genetic privacy. Ann N Y Acad Sci. 2017 Jan 14;1387(1):61–72. doi: 10.1111/nyas.13211. https://europepmc.org/abstract/MED/27626905 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 50.Stiles D, Appelbaum PS. Cases in precision medicine: concerns about privacy and discrimination after genomic sequencing. Ann Intern Med. 2019 May 07;170(10):717. doi: 10.7326/m18-2666. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 51.Wan Z, Hazel JW, Clayton EW, Vorobeychik Y, Kantarcioglu M, Malin BA. Sociotechnical safeguards for genomic data privacy. Nat Rev Genet. 2022 Jul 04;23(7):429–45. doi: 10.1038/s41576-022-00455-y. https://europepmc.org/abstract/MED/35246669 .10.1038/s41576-022-00455-y [DOI] [PMC free article] [PubMed] [Google Scholar]
- 52.Wang S, Jiang X, Singh S, Marmor R, Bonomi L, Fox D, Dow M, Ohno-Machado L. Genome privacy: challenges, technical approaches to mitigate risk, and ethical considerations in the United States. Ann N Y Acad Sci. 2017 Jan 28;1387(1):73–83. doi: 10.1111/nyas.13259. https://europepmc.org/abstract/MED/27681358 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 53.Belani S, Tiarks GC, Mookerjee N, Rajput V. "I agree to disagree": comparative ethical and legal analysis of big data and genomics for privacy, consent, and ownership. Cureus. 2021 Oct;13(10):e18736. doi: 10.7759/cureus.18736. https://europepmc.org/abstract/MED/34796049 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 54.Du L, Wang M. Genetic privacy and data protection: a review of Chinese direct-to-consumer genetic test services. Front Genet. 2020 Apr 28;11:416. doi: 10.3389/fgene.2020.00416. https://europepmc.org/abstract/MED/32425986 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 55.Dugan T, Zou X. Privacy-preserving evaluation techniques and their application in genetic tests. Smart Health. 2017 Jun;1-2:2–17. doi: 10.1016/j.smhl.2017.03.003. [DOI] [Google Scholar]
- 56.Lu D, Zhang Y, Zhang L, Wang H, Weng W, Li L, Cai H. Methods of privacy-preserving genomic sequencing data alignments. Brief Bioinform. 2021 Nov 05;22(6):bbab151. doi: 10.1093/bib/bbab151.6279828 [DOI] [PubMed] [Google Scholar]
- 57.Heeney C, Hawkins N, de Vries J, Boddington P, Kaye J. Assessing the privacy risks of data sharing in genomics. Public Health Genomics. 2011;14(1):17–25. doi: 10.1159/000294150. doi: 10.1159/000294150.000294150 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 58.Backes M, Berrang P, Bieg M, Eils R, Herrrnann C, Humbert M, Lehmann I. Identifying personal DNA methylation profiles by genotype inference. Proceedings of the 2017 IEEE Symposium on Security and Privacy; SP '17; May 22-26, 2017; San Jose, CA. 2017. pp. 957–76. https://ieeexplore.ieee.org/document/7958619 . [DOI] [Google Scholar]
- 59.Philibert RA, Terry N, Erwin C, Philibert WJ, Beach SR, Brody GH. Methylation array data can simultaneously identify individuals and convey protected health information: an unrecognized ethical concern. Clin Epigenetics. 2014;6(1):28. doi: 10.1186/1868-7083-6-28. https://clinicalepigeneticsjournal.biomedcentral.com/articles/10.1186/1868-7083-6-28 .91 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 60.Gürsoy G, Lu N, Wagner S, Gerstein M. Recovering genotypes and phenotypes using allele-specific genes. Genome Biol. 2021 Sep 07;22(1):263. doi: 10.1186/s13059-021-02477-x. https://genomebiology.biomedcentral.com/articles/10.1186/s13059-021-02477-x .10.1186/s13059-021-02477-x [DOI] [PMC free article] [PubMed] [Google Scholar]
- 61.Hagestedt I, Zhang Y, Humbert M, Berrang P, Tang H, Wang X, Backes M. MBeacon: privacy-preserving beacons for DNA methylation data. Proceedings of the 2019 Network and Distributed Systems Security Symposium; NDSS '19; February 24-27, 2019; San Diego, CA. 2019. pp. 1–15. https://www.ndss-symposium.org/wp-content/uploads/2019/02/ndss2019_03A-2_Hagestedt_paper.pdf . [DOI] [Google Scholar]
- 62.Harmanci A, Gerstein M. Quantification of private information leakage from phenotype-genotype data: linking attacks. Nat Methods. 2016 Mar;13(3):251–6. doi: 10.1038/nmeth.3746. https://europepmc.org/abstract/MED/26828419 .nmeth.3746 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 63.Harmanci A, Gerstein M. Analysis of sensitive information leakage in functional genomics signal profiles through genomic deletions. Nat Commun. 2018 Jun 22;9(1):2453. doi: 10.1038/s41467-018-04875-5. doi: 10.1038/s41467-018-04875-5.10.1038/s41467-018-04875-5 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 64.Boonen K, Hens K, Menschaert G, Baggerman G, Valkenborg D, Ertaylan G. Beyond genes: re-identifiability of proteomic data and its implications for personalized medicine. Genes (Basel) 2019 Sep 05;10(9):682. doi: 10.3390/genes10090682. https://www.mdpi.com/resolver?pii=genes10090682 .genes10090682 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 65.Schadt EE, Woo S, Hao K. Bayesian method to predict individual SNP genotypes from gene expression data. Nat Genet. 2012 May;44(5):603–8. doi: 10.1038/ng.2248.ng.2248 [DOI] [PubMed] [Google Scholar]
- 66.Dyke SO, Cheung WA, Joly Y, Ammerpohl O, Lutsik P, Rothstein MA, Caron M, Busche S, Bourque G, Rönnblom L, Flicek P, Beck S, Hirst M, Stunnenberg H, Siebert R, Walter J, Pastinen T. Epigenome data release: a participant-centered approach to privacy protection. Genome Biol. 2015 Jul 17;16(1):142. doi: 10.1186/s13059-015-0723-0. https://genomebiology.biomedcentral.com/articles/10.1186/s13059-015-0723-0 .10.1186/s13059-015-0723-0 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 67.Berrang P, Humbert M, Zhang Y, Lehmann I, Eils R, Backes M. Dissecting privacy risks in biomedical data. Proceedings of the 2018 IEEE European Symposium on Security and Privacy; EuroS&P'18; April 24-26, 2018; London, UK. 2018. pp. 62–76. https://ieeexplore.ieee.org/document/8406591/similar#similar . [DOI] [Google Scholar]
- 68.Zhao Y, Wang K, Wang W, Yin T, Dong W, Xu C. A high-throughput SNP discovery strategy for RNA-seq data. BMC Genomics. 2019 Feb 27;20(1):160. doi: 10.1186/s12864-019-5533-4. https://bmcgenomics.biomedcentral.com/articles/10.1186/s12864-019-5533-4 .10.1186/s12864-019-5533-4 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 69.Gürsoy G, Li T, Liu S, Ni E, Brannon CM, Gerstein MB. Functional genomics data: privacy risk assessment and technological mitigation. Nat Rev Genet. 2022 Apr;23(4):245–58. doi: 10.1038/s41576-021-00428-7.10.1038/s41576-021-00428-7 [DOI] [PubMed] [Google Scholar]
- 70.Gürsoy G, Emani P, Brannon CM, Jolanki OA, Harmanci A, Strattan JS, Cherry JM, Miranker AD, Gerstein M. Data sanitization to reduce private information leakage from functional genomics. Cell. 2020 Nov 12;183(4):905–17. doi: 10.1016/j.cell.2020.09.036. https://linkinghub.elsevier.com/retrieve/pii/S0092-8674(20)31233-2 .S0092-8674(20)31233-2 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 71.Li S, Bandeira N, Wang X, Tang H. On the privacy risks of sharing clinical proteomics data. AMIA Jt Summits Transl Sci Proc. 2016;2016:122–31. https://europepmc.org/abstract/MED/27595046 . [PMC free article] [PubMed] [Google Scholar]
- 72.Dupras C, Beck S, Rothstein MA, Berner A, Saulnier KM, Pinkesz M, Prince AE, Liosi S, Song L, Joly Y. Potential (mis) use of epigenetic age estimators by private companies and public agencies: human rights law should provide ethical guidance. Environ Epigenet. 2019;5(3):dvz018. doi: 10.1093/eep/dvz018. [DOI] [Google Scholar]
- 73.Lu C, Greshake Tzovaras B, Gough J. A survey of direct-to-consumer genotype data, and quality control tool (GenomePrep) for research. Comput Struct Biotechnol J. 2021 Jun 27;19:3747–54. doi: 10.1016/j.csbj.2021.06.040. https://linkinghub.elsevier.com/retrieve/pii/S2001-0370(21)00278-6 .S2001-0370(21)00278-6 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 74.Collins A, Lonjou C, Morton NE. Genetic epidemiology of single-nucleotide polymorphisms. Proc Natl Acad Sci U S A. 1999 Dec 21;96(26):15173–7. doi: 10.1073/pnas.96.26.15173. https://europepmc.org/abstract/MED/10611357 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 75.Sun JX, He Y, Sanford E, Montesion M, Frampton GM, Vignot S, Soria JC, Ross JS, Miller VA, Stephens PJ, Lipson D, Yelensky R. A computational approach to distinguish somatic vs. germline origin of genomic alterations from deep sequencing of cancer specimens without a matched normal. PLoS Comput Biol. 2018 Feb;14(2):e1005965. doi: 10.1371/journal.pcbi.1005965. https://dx.plos.org/10.1371/journal.pcbi.1005965 .PCOMPBIOL-D-15-01621 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 76.Yousefi S, Abbassi-Daloii T, Kraaijenbrink T, Vermaat M, Mei H, van 't Hof P, van Iterson M, Zhernakova DV, Claringbould A, Franke L, 't Hart LM, Slieker RC, van der Heijden A, de Knijff P. A SNP panel for identification of DNA and RNA specimens. BMC Genomics. 2018 Jan 25;19(1):90. doi: 10.1186/s12864-018-4482-7. https://bmcgenomics.biomedcentral.com/articles/10.1186/s12864-018-4482-7 .10.1186/s12864-018-4482-7 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 77.Lin Z, Owen AB, Altman RB. Genetics. Genomic research and human subject privacy. Science. 2004 Jul 09;305(5681):183. doi: 10.1126/science.1095019.305/5681/183 [DOI] [PubMed] [Google Scholar]
- 78.Sanchez JJ, Phillips C, Børsting C, Balogh K, Bogus M, Fondevila M, Harrison CD, Musgrave-Brown E, Salas A, Syndercombe-Court D, Schneider PM, Carracedo A, Morling N. A multiplex assay with 52 single nucleotide polymorphisms for human identification. Electrophoresis. 2006 May;27(9):1713–24. doi: 10.1002/elps.200500671. [DOI] [PubMed] [Google Scholar]
- 79.Pakstis AJ, Speed WC, Fang R, Hyland FC, Furtado MR, Kidd JR, Kidd KK. SNPs for a universal individual identification panel. Hum Genet. 2010 Mar;127(3):315–24. doi: 10.1007/s00439-009-0771-1. [DOI] [PubMed] [Google Scholar]
- 80.Kling D, Phillips C, Kennett D, Tillmar A. Investigative genetic genealogy: current methods, knowledge and practice. Forensic Sci Int Genet. 2021 May;52:102474. doi: 10.1016/j.fsigen.2021.102474. https://linkinghub.elsevier.com/retrieve/pii/S1872-4973(21)00013-2 .S1872-4973(21)00013-2 [DOI] [PubMed] [Google Scholar]
- 81.White JD, Indencleef K, Naqvi S, Eller RJ, Hoskens H, Roosenboom J, Lee MK, Li J, Mohammed J, Richmond S, Quillen EE, Norton HL, Feingold E, Swigut T, Marazita ML, Peeters H, Hens G, Shaffer JR, Wysocka J, Walsh S, Weinberg SM, Shriver MD, Claes P. Insights into the genetic architecture of the human face. Nat Genet. 2021 Jan;53(1):45–53. doi: 10.1038/s41588-020-00741-7. https://europepmc.org/abstract/MED/33288918 .10.1038/s41588-020-00741-7 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 82.Locke AE, Kahali B, Berndt SI, Justice AE, Pers TH, Day FR, Powell C, Vedantam S, Buchkovich M, Yang J, Croteau-Chonka DC, Esko T, Fall T, Ferreira T, Gustafsson S, Kutalik Z, Luan J, Mägi R, Randall JC, Winkler TW, Wood AR, Workalemahu T, Faul JD, Smith JA, Zhao JH, Zhao W, Chen J, Fehrmann R, Hedman ÅK, Karjalainen J, Schmidt EM, Absher D, Amin N, Anderson D, Beekman M, Bolton JL, Bragg-Gresham JL, Buyske S, Demirkan A, Deng G, Ehret GB, Feenstra B, Feitosa MF, Fischer K, Goel A, Gong J, Jackson AU, Kanoni S, Kleber ME, Kristiansson K, Lim U, Lotay V, Mangino M, Leach IM, Medina-Gomez C, Medland SE, Nalls MA, Palmer CD, Pasko D, Pechlivanis S, Peters MJ, Prokopenko I, Shungin D, Stančáková A, Strawbridge RJ, Sung YJ, Tanaka T, Teumer A, Trompet S, van der Laan SW, van Setten J, Van Vliet-Ostaptchouk JV, Wang Z, Yengo L, Zhang W, Isaacs A, Albrecht E, Ärnlöv J, Arscott GM, Attwood AP, Bandinelli S, Barrett A, Bas IN, Bellis C, Bennett AJ, Berne C, Blagieva R, Blüher M, Böhringer S, Bonnycastle LL, Böttcher Y, Boyd HA, Bruinenberg M, Caspersen IH, Chen YD, Clarke R, Daw EW, de Craen AJ, Delgado G, Dimitriou M, Doney AS, Eklund N, Estrada K, Eury E, Folkersen L, Fraser RM, Garcia ME, Geller F, Giedraitis V, Gigante B, Go AS, Golay A, Goodall AH, Gordon SD, Gorski M, Grabe HJ, Grallert H, Grammer TB, Gräßler J, Grönberg H, Groves CJ, Gusto G, Haessler J, Hall P, Haller T, Hallmans G, Hartman CA, Hassinen M, Hayward C, Heard-Costa NL, Helmer Q, Hengstenberg C, Holmen O, Hottenga JJ, James AL, Jeff JM, Johansson Å, Jolley J, Juliusdottir T, Kinnunen L, Koenig W, Koskenvuo M, Kratzer W, Laitinen J, Lamina C, Leander K, Lee NR, Lichtner P, Lind L, Lindström J, Lo KS, Lobbens S, Lorbeer R, Lu Y, Mach F, Magnusson PK, Mahajan A, McArdle WL, McLachlan S, Menni C, Merger S, Mihailov E, Milani L, Moayyeri A, Monda KL, Morken MA, Mulas A, Müller G, Müller-Nurasyid M, Musk AW, Nagaraja R, Nöthen MM, Nolte IM, Pilz S, Rayner NW, Renstrom F, Rettig R, Ried JS, Ripke S, Robertson NR, Rose LM, Sanna S, Scharnagl H, Scholtens S, Schumacher FR, Scott WR, Seufferlein T, Shi J, Smith AV, Smolonska J, Stanton AV, Steinthorsdottir V, Stirrups K, Stringham HM, Sundström J, Swertz MA, Swift AJ, Syvänen AC, Tan ST, Tayo BO, Thorand B, Heath AC, Arveiler D, Bakker SJ, Beilby J, Bergman RD, Barroso I, North KE, Ingelsson E, Hirschhorn JN, Loos RJ, Speliotes EK. Genetic studies of body mass index yield new insights for obesity biology. Nature. 2015 Feb 12;518(7538):197–206. doi: 10.1038/nature14177. http://hdl.handle.net/2318/1562225 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 83.Dabas P, Jain S, Khajuria H, Nayak BP. Forensic DNA phenotyping: inferring phenotypic traits from crime scene DNA. J Forensic Leg Med. 2022 May;88:102351. doi: 10.1016/j.jflm.2022.102351.S1752-928X(22)00049-X [DOI] [PubMed] [Google Scholar]
- 84.Regalado A. More than 26 million people have taken an at-home ancestry test. MIT Technology Review. 2019. Feb 11, [2024-04-05]. https://www.technologyreview.com/2019/02/11/103446/more-than-26-million-people-have-taken-an-at-home-ances try-test/
- 85.Church GM. The personal genome project. Mol Syst Biol. 2005;1:2005.0030. doi: 10.1038/msb4100040. https://europepmc.org/abstract/MED/16729065 .msb4100040 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 86.Greshake B, Bayer PE, Rausch H, Reda J. openSNP--a crowdsourced web resource for personal genomics. PLoS One. 2014;9(3):e89204. doi: 10.1371/journal.pone.0089204. https://dx.plos.org/10.1371/journal.pone.0089204 .PONE-D-13-09504 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 87.Smigielski EM, Sirotkin K, Ward M, Sherry ST. dbSNP: a database of single nucleotide polymorphisms. Nucleic Acids Res. 2000 Jan 01;28(1):352–5. doi: 10.1093/nar/28.1.352. https://air.unimi.it/handle/2434/235313 .gkd114 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 88.Fairley S, Lowy-Gallego E, Perry E, Flicek P. The International Genome Sample Resource (IGSR) collection of open human genomic variation resources. Nucleic Acids Res. 2020 Jan 08;48(D1):D941–7. doi: 10.1093/nar/gkz836. https://europepmc.org/abstract/MED/31584097 .5580898 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 89.International HapMap Consortium A haplotype map of the human genome. Nature. 2005 Oct 27;437(7063):1299–320. doi: 10.1038/nature04226. https://europepmc.org/abstract/MED/16255080 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 90.Edge MD, Algee-Hewitt BF, Pemberton TJ, Li JZ, Rosenberg NA. Linkage disequilibrium matches forensic genetic records to disjoint genomic marker sets. Proc Natl Acad Sci U S A. 2017 May 30;114(22):5671–6. doi: 10.1073/pnas.1619944114. https://www.pnas.org/doi/abs/10.1073/pnas.1619944114?url_ver=Z39.88-2003&rfr_id=ori:rid:crossref.org&rfr_dat=cr_pub0pubmed .1619944114 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 91.He Z, Yu J, Li J, Han Q, Luo G, Li Y. Inference attacks and controls on genotypes and phenotypes for individual genomic data. IEEE/ACM Trans Comput Biol Bioinform. 2020;17(3):930–7. doi: 10.1109/TCBB.2018.2810180. [DOI] [PubMed] [Google Scholar]
- 92.Humbert M, Huguenin K, Hugonot J, Ayday E, Hubaux JP. De-anonymizing genomic databases using phenotypic traits. Proc Priv Enhanc Technol. 2015;2015:99–114. doi: 10.1515/popets-2015-0020. https://petsymposium.org/popets/2015/popets-2015-0020.pdf . [DOI] [Google Scholar]
- 93.Lippert C, Sabatini R, Maher MC, Kang EY, Lee S, Arikan O, Harley A, Bernal A, Garst P, Lavrenko V, Yocum K, Wong T, Zhu M, Yang WY, Chang C, Lu T, Lee CW, Hicks B, Ramakrishnan S, Tang H, Xie C, Piper J, Brewerton S, Turpaz Y, Telenti A, Roby RK, Och FJ, Venter JC. Identification of individuals by trait prediction using whole-genome sequencing data. Proc Natl Acad Sci U S A. 2017 Sep 19;114(38):10166–71. doi: 10.1073/pnas.1711125114. https://www.pnas.org/doi/abs/10.1073/pnas.1711125114?url_ver=Z39.88-2003&rfr_id=ori:rid:crossref.org&rfr_dat=cr_pub0pubmed .1711125114 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 94.Wheeler DA, Srinivasan M, Egholm M, Shen Y, Chen L, McGuire A, He W, Chen YJ, Makhijani V, Roth GT, Gomes X, Tartaro K, Niazi F, Turcotte CL, Irzyk GP, Lupski JR, Chinault C, Song X, Liu Y, Yuan Y, Nazareth L, Qin X, Muzny DM, Margulies M, Weinstock GM, Gibbs RA, Rothberg JM. The complete genome of an individual by massively parallel DNA sequencing. Nature. 2008 Apr 17;452(7189):872–6. doi: 10.1038/nature06884.nature06884 [DOI] [PubMed] [Google Scholar]
- 95.Sero D, Zaidi A, Li J, White JD, Zarzar TB, Marazita ML, Weinberg SM, Suetens P, Vandermeulen D, Wagner JK, Shriver MD, Claes P. Facial recognition from DNA using face-to-DNA classifiers. Nat Commun. 2019 Jun 11;10(1):2557. doi: 10.1038/s41467-019-10617-y. doi: 10.1038/s41467-019-10617-y.10.1038/s41467-019-10617-y [DOI] [PMC free article] [PubMed] [Google Scholar]
- 96.Wang Y, Wu X, Shi X. Using aggregate human genome data for individual identification. Proceedings of the 2013 IEEE International Conference on Bioinformatics and Biomedicine; BIBM '13; December 18-21, 2013; Shanghai, China. 2013. pp. 410–5. https://ieeexplore.ieee.org/abstract/document/6732527 . [Google Scholar]
- 97.Erlich Y. Major flaws in “identification of individuals by trait prediction using whole-genome sequencing data”. bioRxiv. doi: 10.1101/185330. Preprint posted online September 7, 2017. https://www.biorxiv.org/content/10.1101/185330v3 . [DOI] [Google Scholar]
- 98.Venkatesaramani R, Malin BA, Vorobeychik Y. Re-identification of individuals in genomic datasets using public face images. Sci Adv. 2021 Nov 19;7(47):eabg3296. doi: 10.1126/sciadv.abg3296. https://www.science.org/doi/abs/10.1126/sciadv.abg3296?url_ver=Z39.88-2003&rfr_id=ori:rid:crossref.org&rfr_dat=cr_pub0pubmed . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 99.Schneider PM, Prainsack B, Kayser M. The use of forensic DNA phenotyping in predicting appearance and biogeographic ancestry. Dtsch Arztebl Int. 2019 Dec 23;51-52(51-52):873–80. doi: 10.3238/arztebl.2019.0873. https://europepmc.org/abstract/MED/31941575 .arztebl.2019.0873 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 100.Emani PS, Gürsoy G, Miranker A, Gerstein MB. Assessing and mitigating privacy risk of sparse, noisy genotypes by local alignment to haplotype databases. bioRxiv. doi: 10.1101/2021.07.18.452853. Preprint posted online August 30, 2022. https://www.biorxiv.org/content/10.1101/2021.07.18.452853v2 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 101.Lander ES, Linton LM, Birren B, Nusbaum C, Zody MC, Baldwin J, Devon K, Dewar K, Doyle M, FitzHugh W, Funke R, Gage D, Harris K, Heaford A, Howland J, Kann L, Lehoczky J, LeVine R, McEwan P, McKernan K, Meldrim J, Mesirov JP, Miranda C, Morris W, Naylor J, Raymond C, Rosetti M, Santos R, Sheridan A, Sougnez C, Stange-Thomann Y, Stojanovic N, Subramanian A, Wyman D, Rogers J, Sulston J, Ainscough R, Beck S, Bentley D, Burton J, Clee C, Carter N, Coulson A, Deadman R, Deloukas P, Dunham A, Dunham I, Durbin R, French L, Grafham D, Gregory S, Hubbard T, Humphray S, Hunt A, Jones M, Lloyd C, McMurray A, Matthews L, Mercer S, Milne S, Mullikin JC, Mungall A, Plumb R, Ross M, Shownkeen R, Sims S, Waterston RH, Wilson RK, Hillier LW, McPherson JD, Marra MA, Mardis ER, Fulton LA, Chinwalla AT, Pepin KH, Gish WR, Chissoe SL, Wendl MC, Delehaunty KD, Miner TL, Delehaunty A, Kramer JB, Cook LL, Fulton RS, Johnson DL, Minx PJ, Clifton SW, Hawkins T, Branscomb E, Predki P, Richardson P, Wenning S, Slezak T, Doggett N, Cheng JF, Olsen A, Lucas S, Elkin C, Uberbacher E, Frazier M, Gibbs RA, Muzny DM, Scherer SE, Bouck JB, Sodergren EJ, Worley KC, Rives CM, Gorrell JH, Metzker ML, Naylor SL, Kucherlapati RS, Nelson DL, Weinstock GM, Sakaki Y, Fujiyama A, Hattori M, Yada T, Toyoda A, Itoh T, Kawagoe C, Watanabe H, Totoki Y, Taylor T, Weissenbach J, Heilig R, Saurin W, Artiguenave F, Brottier P, Bruls T, Pelletier E, Robert C, Wincker P, Smith DR, Doucette-Stamm L, Rubenfield M, Weinstock K, Lee HM, Dubois J, Rosenthal A, Platzer M, Nyakatura G, Taudien S, Rump A, Yang H, Yu J, Wang J, Huang G, Gu J, Hood L, Rowen L, Madan A, Qin S, Davis RW, Federspiel NA, Abola AP, Proctor MJ, Myers RM, Schmutz J, Dickson M, Grimwood J, Cox DR, Olson MV, Kaul R, Raymond C, Shimizu N, Kawasaki K, Minoshima S, Evans GA, Athanasiou M, Schultz R, Roe BA, Chen F, Pan H, Ramser J, Lehrach H, Reinhardt R, McCombie WR, de la Bastide M, Dedhia N, Blöcker H, Hornischer K, Nordsiek G, Agarwala R, Aravind L, Bailey JA, Bateman A, Batzoglou S, Birney E, Bork P, Brown DG, Burge CB, Cerutti L, Chen HC, Church D, Clamp M, Copley RR, Doerks T, Eddy SR, Eichler EE, Furey TS, Galagan J, Gilbert JG, Harmon C, Hayashizaki Y, Haussler D, Hermjakob H, Hokamp K, Jang W, Johnson LS, Jones TA, Kasif S, Kaspryzk A, Kennedy S, Kent WJ, Kitts P, Koonin EV, Korf I, Kulp D, Lancet D, Lowe TM, McLysaght A, Mikkelsen T, Moran JV, Mulder N, Pollara VJ, Ponting CP, Schuler G, Schultz J, Slater G, Smit AF, Stupka E, Szustakowki J, Thierry-Mieg D, Thierry-Mieg J, Wagner L, Wallis J, Wheeler R, Williams A, Wolf YI, Wolfe KH, Yang SP, Yeh RF, Collins F, Guyer MS, Peterson J, Felsenfeld A, Wetterstrand KA, Patrinos A, Morgan MJ, de JP, Catanese JJ, Osoegawa K, Shizuya H, Choi S, Chen YJ, Szustakowki J. Initial sequencing and analysis of the human genome. Nature. 2001 Feb 15;409(6822):860–921. doi: 10.1038/35057062. [DOI] [PubMed] [Google Scholar]
- 102.Wyner N, Barash M, McNevin D. Forensic autosomal short tandem repeats and their potential association with phenotype. Front Genet. 2020;11:884. doi: 10.3389/fgene.2020.00884. https://europepmc.org/abstract/MED/32849844 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 103.FBI US Law Enforcement Resources: Biometrics and Fingerprints. Combined DNA Index System (CODIS) [2023-03-29]. https://tinyurl.com/3by74dhj .
- 104.Gitschier J. Inferential genotyping of Y chromosomes in latter-day saints founders and comparison to Utah samples in the HapMap project. Am J Hum Genet. 2009 Feb;84(2):251–8. doi: 10.1016/j.ajhg.2009.01.018. https://linkinghub.elsevier.com/retrieve/pii/S0002-9297(09)00025-1 .S0002-9297(09)00025-1 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 105.Gymrek M, McGuire AL, Golan D, Halperin E, Erlich Y. Identifying personal genomes by surname inference. Science. 2013 Jan 18;339(6117):321–4. doi: 10.1126/science.1229566.339/6117/321 [DOI] [PubMed] [Google Scholar]
- 106.Kim J, Edge MD, Algee-Hewitt BF, Li JZ, Rosenberg NA. Statistical detection of relatives typed with disjoint forensic and biomedical loci. Cell. 2018 Oct 18;175(3):848–58.e6. doi: 10.1016/j.cell.2018.09.008. https://linkinghub.elsevier.com/retrieve/pii/S0092-8674(18)31180-2 .S0092-8674(18)31180-2 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 107.Edge MD, Coop G. Attacks on genetic privacy via uploads to genealogical databases. Elife. 2020 Jan 07;9:e51810. doi: 10.7554/eLife.51810. https://europepmc.org/abstract/MED/31908268 .51810 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 108.Ney P, Ceze L, Kohno T. Genotype extraction and false relative attacks: security risks to third-party genetic genealogy services beyond identity inference. Proceedings of the 2020 Network and Distributed Systems Security (NDSS) Symposium; NDSS '20; February 23-26, 2020; San Diego, CA. 2020. pp. 1–15. https://www.ndss-symposium .org/wp-content/uploads/2020/02/23049.pdf/> . [DOI] [Google Scholar]
- 109.Sweeney L, Abu A, Winn J. Identifying participants in the personal genome project by name. SSRN Journal. doi: 10.2139/ssrn.2257732. Preprint posted online April 29, 2013. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2257732 . [DOI] [Google Scholar]
- 110.Guerrini CJ, Wickenheiser RA, Bettinger B, McGuire AL, Fullerton SM. Four misconceptions about investigative genetic genealogy. J Law Biosci. 2021;8(1):lsab001. doi: 10.1093/jlb/lsab001. https://europepmc.org/abstract/MED/33880184 .lsab001 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 111.Craig DW, Goor RM, Wang Z, Paschall J, Ostell J, Feolo M, Sherry ST, Manolio TA. Assessing and managing risk when sharing aggregate genetic variant data. Nat Rev Genet. 2011 Sep 16;12(10):730–6. doi: 10.1038/nrg3067. https://europepmc.org/abstract/MED/21921928 .nrg3067 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 112.Im HK, Gamazon ER, Nicolae DL, Cox NJ. On sharing quantitative trait GWAS results in an era of multiple-omics data and the limits of genomic privacy. Am J Hum Genet. 2012 Apr 06;90(4):591–8. doi: 10.1016/j.ajhg.2012.02.008. https://linkinghub.elsevier.com/retrieve/pii/S0002-9297(12)00093-6 .S0002-9297(12)00093-6 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 113.Wang R, Li YF, Wang X, Tang H, Zhou X. Learning your identity and disease from research papers: information leaks in genome wide association study. Proceedings of the 16th ACM conference on Computer and communications security; CCS '09; November 9-13, 2009; Chicago, IL. 2009. pp. 534–44. https://dl.acm.org/doi/10.1145/1653662.1653726 . [DOI] [Google Scholar]
- 114.Homer N, Szelinger S, Redman M, Duggan D, Tembe W, Muehling J, Pearson JV, Stephan DA, Nelson SF, Craig DW. Resolving individuals contributing trace amounts of DNA to highly complex mixtures using high-density SNP genotyping microarrays. PLoS Genet. 2008 Aug 29;4(8):e1000167. doi: 10.1371/journal.pgen.1000167. https://dx.plos.org/10.1371/journal.pgen.1000167 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 115.Sankararaman S, Obozinski G, Jordan MI, Halperin E. Genomic privacy and limits of individual detection in a pool. Nat Genet. 2009 Sep;41(9):965–7. doi: 10.1038/ng.436.ng.436 [DOI] [PubMed] [Google Scholar]
- 116.Braun R, Rowe W, Schaefer C, Zhang J, Buetow K. Needles in the haystack: identifying individuals present in pooled genomic data. PLoS Genet. 2009 Oct;5(10):e1000668. doi: 10.1371/journal.pgen.1000668. https://dx.plos.org/10.1371/journal.pgen.1000668 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 117.Cai R, Hao Z, Winslett M, Xiao X, Yang Y, Zhang Z, Zhou S. Deterministic identification of specific individuals from GWAS results. Bioinformatics. 2015 Jun 01;31(11):1701–7. doi: 10.1093/bioinformatics/btv018. https://europepmc.org/abstract/MED/25630377 .btv018 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 118.Bu D, Wang X, Tang H. Haplotype-based membership inference from summary genomic data. Bioinformatics. 2021 Jul 12;37(Suppl_1):i161–8. doi: 10.1093/bioinformatics/btab305. https://europepmc.org/abstract/MED/34252973 .6319711 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 119.Almadhoun N, Ayday E, Ulusoy Ö. Inference attacks against differentially private query results from genomic datasets including dependent tuples. Bioinformatics. 2020 Jul 01;36(Suppl_1):i136–45. doi: 10.1093/bioinformatics/btaa475. https://europepmc.org/abstract/MED/32657411 .5870519 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 120.Zerhouni EA, Nabel EG. Protecting aggregate genomic data. Science. 2008 Oct 03;322(5898):44. doi: 10.1126/science.322.5898.44b.1165490 [DOI] [PubMed] [Google Scholar]
- 121.Visscher PM, Hill WG. The limits of individual identification from sample allele frequencies: theory and statistical analysis. PLoS Genet. 2009 Oct;5(10):e1000628. doi: 10.1371/journal.pgen.1000628. https://dx.plos.org/10.1371/journal.pgen.1000628 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 122.Masca N, Burton PR, Sheehan NA. Participant identification in genetic association studies: improved methods and practical implications. Int J Epidemiol. 2011 Dec;40(6):1629–42. doi: 10.1093/ije/dyr149. https://europepmc.org/abstract/MED/22158671 .dyr149 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 123.Pardo R, Rafnsson W, Steinhorn G, Lavrov D, Lumley T, Probst C, Ziedins I, Wąsowski A. Privacy with good taste: a case study in quantifying privacy risks in genetic scores. arXiv. doi: 10.1007/978-3-031-25734-6_7. Preprint posted online August 26, 2022. https://arxiv.org/abs/2208.12497 . [DOI] [Google Scholar]
- 124.Mahmoud M, Gobet N, Cruz-Dávalos DI, Mounier N, Dessimoz C, Sedlazeck FJ. Structural variant calling: the long and the short of it. Genome Biol. 2019 Nov 20;20(1):246. doi: 10.1186/s13059-019-1828-7. https://genomebiology.biomedcentral.com/articles/10.1186/s13059-019-1828-7 .10.1186/s13059-019-1828-7 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 125.Pang AW, MacDonald JR, Pinto D, Wei J, Rafiq MA, Conrad DF, Park H, Hurles ME, Lee C, Venter JC, Kirkness EF, Levy S, Feuk L, Scherer SW. Towards a comprehensive structural variation map of an individual human genome. Genome Biol. 2010;11(5):R52. doi: 10.1186/gb-2010-11-5-r52. https://genomebiology.biomedcentral.com/articles/10.1186/gb-2010-11-5-r52 .gb-2010-11-5-r52 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 126.Chen W, Hayward C, Wright AF, Hicks AA, Vitart V, Knott S, Wild SH, Pramstaller PP, Wilson JF, Rudan I, Porteous DJ. Copy number variation across European populations. PLoS One. 2011;6(8):e23087. doi: 10.1371/journal.pone.0023087. https://dx.plos.org/10.1371/journal.pone.0023087 .PONE-D-11-03380 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 127.Chiang C, Scott AJ, Davis JR, Tsang EK, Li X, Kim Y, Hadzic T, Damani FN, Ganel L. The impact of structural variation on human gene expression. Nat Genet. 2017 May 3;49(5):692–9. doi: 10.1038/ng.3834. https://europepmc.org/abstract/MED/28369037 .ng.3834 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 128.Ueki M, Takeshita H, Fujihara J, Kimura-Kataoka K, Iida R, Yasuda T. Simple screening method for copy number variations associated with physical features. Leg Med (Tokyo) 2017 Mar;25:71–4. doi: 10.1016/j.legalmed.2017.01.006.S1344-6223(17)30030-5 [DOI] [PubMed] [Google Scholar]
- 129.Weischenfeldt J, Symmons O, Spitz F, Korbel JO. Phenotypic impact of genomic structural variation: insights from and for human disease. Nat Rev Genet. 2013 Feb;14(2):125–38. doi: 10.1038/nrg3373.nrg3373 [DOI] [PubMed] [Google Scholar]
- 130.Ho SS, Urban AE, Mills RE. Structural variation in the sequencing era. Nat Rev Genet. 2020 Mar;21(3):171–89. doi: 10.1038/s41576-019-0180-9. https://europepmc.org/abstract/MED/31729472 .10.1038/s41576-019-0180-9 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 131.Shabani M, Marelli L. Re-identifiability of genomic data and the GDPR: assessing the re-identifiability of genomic data in light of the EU General Data Protection Regulation. EMBO Rep. 2019 Jun;20(6):e48316. doi: 10.15252/embr.201948316. https://europepmc.org/abstract/MED/31126909 .embr.201948316 [DOI] [PMC free article] [PubMed] [Google Scholar]
- 132.Molnár-Gábor F, Korbel JO. Genomic data sharing in Europe is stumbling-Could a code of conduct prevent its fall? EMBO Mol Med. 2020 Mar 06;12(3):e11421. doi: 10.15252/emmm.201911421. https://europepmc.org/abstract/MED/32072760 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 133.Martinez-Martin N, Magnus D. Privacy and ethical challenges in next-generation sequencing. Expert Rev Precis Med Drug Dev. 2019;4(2):95–104. doi: 10.1080/23808993.2019.1599685. https://europepmc.org/abstract/MED/32775691 . [DOI] [PMC free article] [PubMed] [Google Scholar]
- 134.Clayton EW, Evans BJ, Hazel J, Rothstein MA. The law of genetic privacy: applications, implications, and limitations. J Law Biosci. 2019:1–36. doi: 10.2139/ssrn.3384321. [DOI] [PMC free article] [PubMed] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Supplementary Materials
List of identified reviews and a table with the description and evaluation of original privacy attack studies.
PRISMA checklist.


