Table 3.
Comparison of different adversarial attack methods.
| Attack Method | Attack Settings | Similarity Metric | Scope | Domain | Attack Objectives |
|---|---|---|---|---|---|
| FGSM17 | White-Box |
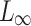 , , 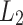
|
Universal | Classification | Obfuscation |
| Face Recognition19 | White-Box | Physical | Image-specific | Recognition | Impersonation |
| PGD23 | White-Box |  |
Universal | Classification | Obfuscation |
| A3GN84 | White-Box | Cosine | Image-specific | Recognition | Impersonation |
| Evolutionary Optimization20 | Black-Box | – | Image-specific | Recognition | Impersonation |
| GFLM85 | White-Box | – | Image-specific | Recognition | Obfuscation |
| AdvFaces21 | Semi-White-Box | 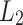 |
Image-specific | Recognition | Both |
| GAP++88 | White-Box |
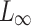 , , 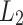 , , 
|
Universal | – | Obfuscation |
