. 2006 Nov 21;8(4):e28. doi: 10.2196/jmir.8.4.e28
© Khaled El Emam, Sam Jabbouri, Scott Sams, Youenn Drouet, Michael Power. Originally published in the Journal of Medical Internet Research (http://www.jmir.org), 21.11.2006. Except where otherwise noted, articles published in the Journal of Medical Internet Research are distributed under the terms of the Creative Commons Attribution License (http://www.creativecommons.org/licenses/by/2.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited, including full bibliographic details and the URL (see "please cite as" above), and this statement is included.
Figure 3.
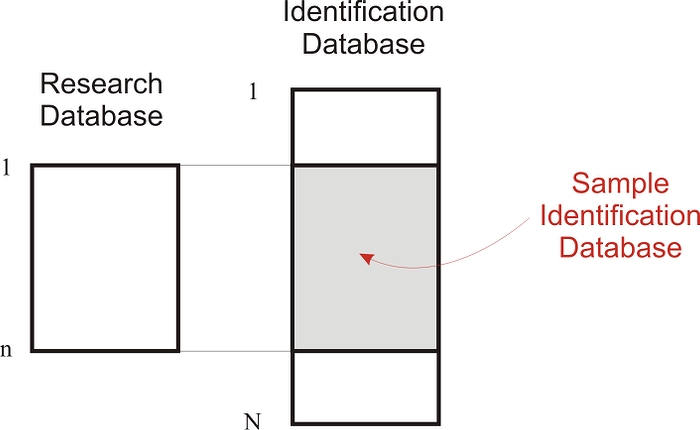
A sample identification database (shown shaded) for data intrusion simulation
