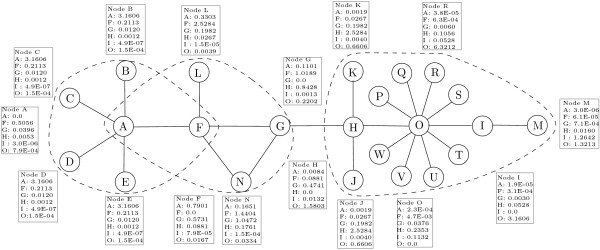
Figure 1.
A simple network. Each box contains the numerical values obtained from Equation 2 from nodes A, F, G, H, I and O to other target nodes. The values for nodes P, Q, S, T, U, V and W are the same as node R's. Results for other nodes are not shown. Final identified clusters are delimited when the merging threshold 2.0 is used.