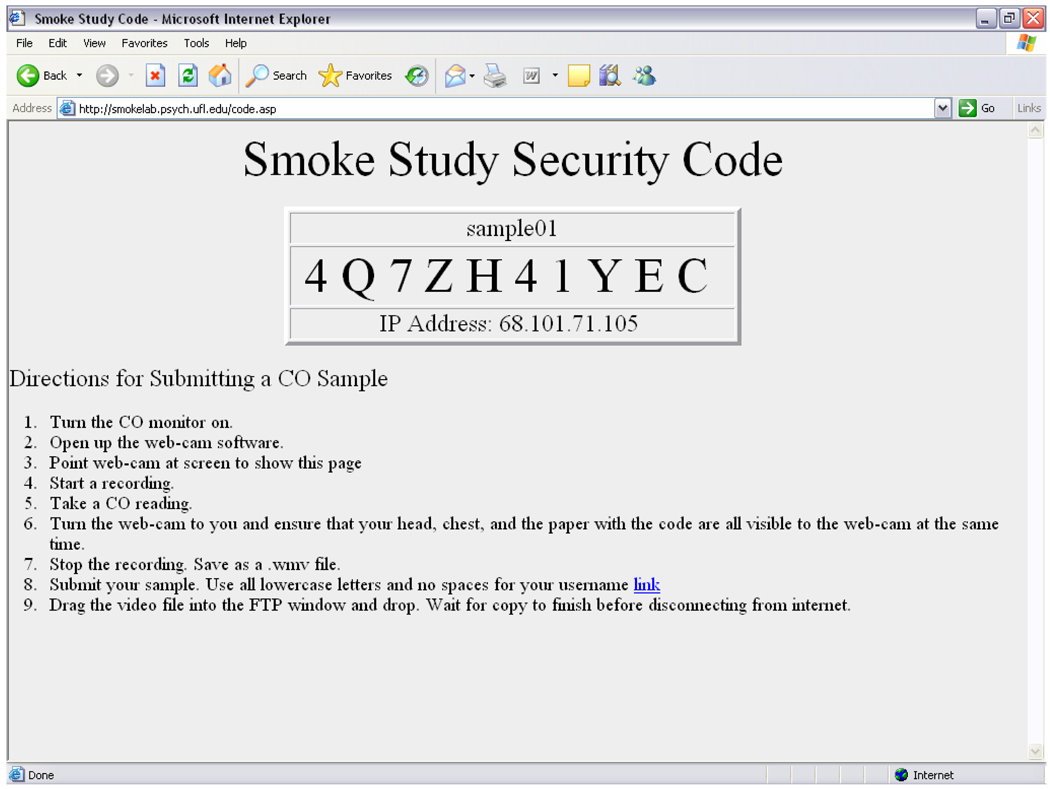
Figure 2.
Screenshot of what appeared when a participant logged onto the server. Each time a participant logged in a randomly determined, unique alphanumeric code was displayed on the screen. As verification, the server stored the time of the log in and the randomly generated code to match that shown by the participant in the video.