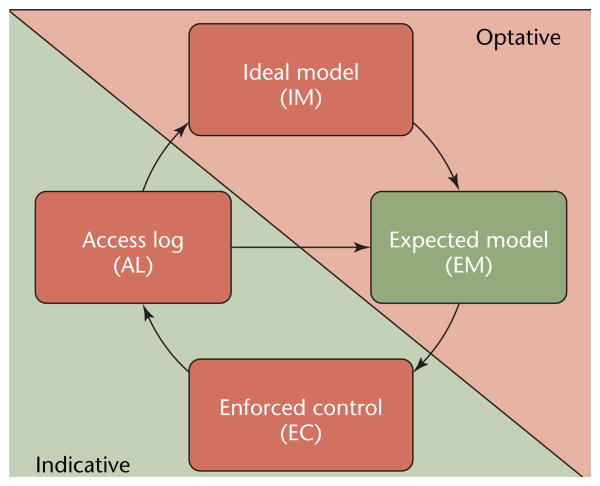
Figure 1.
The experience-based access management (EBAM) life cycle. Access logs (ALs) are used to measure differences between existing enforced controls (EC) and the ideal model (IM) for access rights. This measurement is collected in the expected model (EM), which aids the improvement over time of enforced controls.