Abstract
User authentication is a crucial service in wireless sensor networks (WSNs) that is becoming increasingly common in WSNs because wireless sensor nodes are typically deployed in an unattended environment, leaving them open to possible hostile network attack. Because wireless sensor nodes are limited in computing power, data storage and communication capabilities, any user authentication protocol must be designed to operate efficiently in a resource constrained environment. In this paper, we review several proposed WSN user authentication protocols, with a detailed review of the M.L Das protocol and a cryptanalysis of Das’ protocol that shows several security weaknesses. Furthermore, this paper proposes an ECC-based user authentication protocol that resolves these weaknesses. According to our analysis of security of the ECC-based protocol, it is suitable for applications with higher security requirements. Finally, we present a comparison of security, computation, and communication costs and performances for the proposed protocols. The ECC-based protocol is shown to be suitable for higher security WSNs.
Keywords: authentication, security, ECC, wireless sensor network
1. Introduction
As wireless communication technology has matured, the deployment of Wireless Sensor Networks (WSNs) has become more common. Wireless communication is a natural fit for sensor networks for the following reasons: it reduces the cost of infrastructure, allowing sensor networks to be deployed in areas that were once cost prohibitive and it allows a greater range of applications than fixed location sensor networks [1]. WSNs are now providing economical solutions in a host of diverse industries: electric utilities use WSNs for remote voltage monitoring, museums use WSNs for humidity monitoring and control, health care providers use WSNs for patient monitoring and notification, and they are in use in the military. Other applications include environment tracking and habitat monitoring, etc. [2–5].
A key requirement for WSN is user authentication [6,7]. The client devices (remote wireless sensor nodes) need to be authenticated before being allowed to join the WSN and have access to the WSN’s resources. To date, most user authentication methods have focused on protocol implementations in the network and link layers. Accordingly, we propose an efficient protocol implementation in the WSN application layer. It should be noted that, in order to limit power consumption by sensor nodes and to overcome limitations in computation capacity, user authentication in a WSN is typically done in dedicated gateway node (GW-node) [8].
Sastry and Wagner [9] proposed a security enhancement using access control lists (ACL’s) in the GW node. In addition to verifying a client’s identity and arranging the nearest sensor node, an ACL would be maintained. The ACL would be limited to 255 entries. Watro et al. [10] proposed a complex mathematical method for user authentication employing RSA and Diffie-Hellman algorithms to calculate an encrypted public key (TinyPK authentication), but this protocol is open to hostile attack by a user masquerading as a sensor node (spoofing). Wong et al. [11] proposed a less complex, light-weight, dynamic user authentication method using a hash-based protocol. Their method recommended using the security features of the IEEE 802.15.4 MAC sublayer. Das [12] and Tseng et al. [13] pointed out that both Watro’s and Wong’s user authentication methods were vulnerable to stolen-verifier, replay, and forgery attacks (made possible by allowing multiple users with a single login ID). Das [12] proposed a two factor method of user authentication. This method is designed to protect against the aforementioned stolen-verifier, replay, and forgery attacks. Tseng et al. [13] further pointed out that Wong’s method was vulnerable to stolen passwords and that Wong’s method prevented users from freely changing their password. Tseng et al. proposed an enhanced user authentication method that is design to prevent the various attacks and to reduce the vulnerability to stolen passwords. Khan et al. [14,15] and Chen et al. [16] reviewed the Das two factor method and found additional security issues. Chen et al. [16] proposed a more secure and robust two-factor user authentication in WSNs. Unfortunately, we find that the Chen et al. proposal fails to provide a secure method for updating user passwords and is vulnerable to the insider attack problem.
To address all of the issues raised in the above studies, we propose a novel user authentication protocol for wireless sensor networks, using Elliptic Curves Cryptography (ECC) and smart cards. Our proposal addresses the key security issues, while at the same time reducing computational load requirements. The remainder of this paper is organized as follows: in Section 2, we review the Das method and perform a detailed cryptanalysis of that method; next we present the ECC-based authentication protocol (EAP) for WSNs in Section 3. In Section 4, we present a security and performance analysis of the related protocols. Then, in Section 5, we provide some concluding remarks.
2. Related Works
2.1. Review of Das’ Scheme
This section provides a brief review of the Das method and analyzes its protocol. Before this analysis we first summarize in Table 1 the notations used throughout this paper and their corresponding definitions.
Table 1.
Notations.
| Symbol | Definition |
|---|---|
| U | A user |
| ID | A user’s identity |
| PW | A user’s password |
| DID | A user’s dynamic login identity |
| GW-node | Gateway node of WSN |
| Sn | Nearest sensor node of WSN |
| h(.) | A secure one-way hash function |
| xa | A permanent secret parameter generated securely by the GW-node and stored in some defined sensor nodes before deploying the WSN |
| K | A symmetric key of GW-node which shared between the GW-node, users and the sensor nodes |
| || | A string concatenation operation |
| ⊕ | A string XOR operation |
| ⇒ | A secure channel |
| → | A public channel |
Das’ protocol involves the registration phase, login phase and verification phase, and can be briefly described as follows:
(1) Registration phase:
In this phase, a user Ui submits his/her IDi and PWi to the GW-node in a secured manner. Then, the GW-node issues a license to Ui. The steps are described as follows:
Step 1: Ui ⇒ GW-node:{IDi, PWi}. A Ui enters an identity IDi and a password PWi and then sends {IDi, PWi} to the GW-node using a secure channel.
Step 2: GW-node ⇒ smart card of Ui :{ h(.), IDi, Ni, h(PWi), xa}. The GW-node computes Ni = h(IDi || PWi) ⊕ h(K) after receiving the registration request. Then, the GW-node personalizes the smart card with parameters {h(.), IDi, Ni, h(PWi), xa}. Ui receives the smart card information using a secure channel.
(2) Login phase:
When user Ui enters an IDi and a PWi in order to carry out some inquiry or to access data from the WSN, the smart card must confirm the validity of Ui according to the following steps:
Step 1: Validate Ui. The entered IDi and PWi are validated against the ID and PW stored on the user’s smart card. If Ui’s identification validation fails, the smart card will terminate this request.
-
Step 2: Ui’s smart card calculates DIDi and Ci.
DIDi = h(IDi || PWi)⊕h(xa|| T), where T is the login system timestamp.
Ci = h(Ni || xa || T).
-
Step 3: Ui→GW-node:{DIDi, Ci, T}.
{DIDi, Ci, T} is transmitted to the GW-node via public channel.
(3a) Verification phase (gateway node):
When the GW-node receives a login request {DIDi, Ci, T} at time T*, the GW-node performs the following steps to verify the identity of Ui:
-
Step 1: Validates if T*–T < ΔT.
If (T* – T) ≤ ΔT then the validity of T can be certain, and the GW-node proceeds to the next step. Otherwise, the GW-node rejects the request. Here, ΔT denotes the expected time interval for transmission delay.
-
Step 2: Calculates .
h(IDi || PWi)* = DIDi⊕h(xa || T)
.
-
Step 3: Confirms whether the .
If the , then the GW-node accepts the login request and sends a request to Sn.
Step 4: GW-node→Sn:{DIDi, Ai, T'}.
The GW-node calculates Ai = h(DIDi || Sn || xa || T') and transmits a request {DIDi, Ai, T'} to Sn over a public channel. T' is the GW-node request timestamp. Ai is generated using the xa parameter, thus the value of Ai can be used by Sn to ensure that the message originates from a valid GW-node.
(3b) Verification phase (sensor node):
When Sn receives request {DIDi, Ai, T'} at time T, Sn performs the following steps to verify the validity of the request:
-
Step 1: Validates if T – T’ < ΔT.
If (T – T’) ≤ ΔT then the validity of T' can be certain, and Sn proceeds to the next step.
-
Step 2: Recalculates Ai.
Ai = h(DIDi || Sn || xa || T')
Step 3: Confirms whether the value of the locally calculated Ai is the same as the value of Ai in the GW-node request.
If the value of the locally calculated Ai is the same as the value of Ai in the GW-node request, then Sn responds to Ui’s original request. Otherwise, Sn rejects the request.
2.2. Cryptanalysis of Das’ Protocol
Recently, several studies have analyzed security flaws in Das’ scheme [14–16]. In this section, we also discuss the requirements of security in WSNs and describe the primary flaw of Das’ protocol (it omits mutual authentication) and several secondary security issues [14–16].
2.2.1. Security Requirements in Wireless Sensor Networks
Sastry and Wagner [9] noted several problems with regard to the security of user authentication provided by IEEE 802.15.4 [17]. They cited ACL management problems, loss of ACL state due to power interruptions, and key management problems. They concluded that IEEE 802.15.4 provides insufficient user authentication security and provided some solutions for the noted problems. However, above and beyond the security issues noted by Sastry and Wagner, there are two additional security issues that must be addressed:
Secure user authentication in WSNs should include, to the extent possible, methods for addressing application layer issues such as masquerade, replay, and forgery attacks.
Secure user authentication in WSNs should be based on mutual authentication.
2.2.2. No Mutual Authentication
Because Das’ protocol does not provide mutual authentication [14–16], a malicious user can attack a WSN that uses the Das protocol by means of eavesdropping and masquerading. The attack could be accomplished as follows:
Ui sends the message {DIDi, Ci, T} to the GW-node for accessing the WSN.
The GW-node sends the message {DIDi, Ai, T} to Sn for asking the service for Ui.
The attacker captures the message {DIDi, Ai, T} via eavesdropping.
The attacker provides an SM which masquerades as Sn to get the Ui’s request data or hold back the request.
Since SM co-works with Ui continuously, the Ui access requests will continue to fail.
With the Das method, after accepting the login request of Ui, the GW-node sends a message {DIDi, Ai, T’} to some nearest sensor node Sn. Here the value of Ai is computed by Ai = h(DIDi || Sn || xa || T’), where T' is the current timestamp of GW-node. The value of Ai is used to assure the sensor node that the message has come from the real GW-node. The GW-node message directs the sensor node to reply to the query with the data which Ui has requested. However, there is no mechanism for the GW-node to be assured that the reply message was initiated from the queried sensor node. Thus, the Das-scheme only provides unilateral authentication between the GW-node and sensor node. There is no mutual authentication between the two nodes.
2.2.3. No Protection against Insider Attacks
Nowadays users use a single common password for accessing different applications or servers. The situation is common practice and this is done for their convenience. It relieves the user from having to remember multiple passwords. Nevertheless, if the system manager or a privileged user of the GW-node obtains the common password of Ui, he/she may try to impersonate Ui by accessing other servers where Ui could be a registered user. In the Das scheme [14,15], Ui performs registration with the GW-node by presenting a password in plain format. Thus, the Das protocol does not provide sufficient protection against an insider attack on a GW-node by a privileged user.
2.2.4. No Provision for Changing/Updating Passwords
The fixed password is definitely suffered from threats than an updating password. It is a widely recommended security policy, for highly secure applications, that users should update or change their passwords frequently. In the scheme [14,15], there is no provision for a user to easily change his/her password.
2.2.5. No Protection against Forgery Attacks
A legal user of the system can launch a forgery attack against the WSN by eavesdropping and masquerading. A forgery attack can be launched as follows [16]:
A legal user of the system U* can login to the WSN at TA and TB accurately.
Suppose U* has embedded a synchronized Trojan virus into legal user Ui’s system.
- When Ui wants to login to the WSN at TA and TB, U* can eavesdrop on the messages {DIDi, Ci, TA } and {DIDi, Ci, TB } between the GW-node and Ui at TA and TB. To judge which message is DIDi or Ci as follows:
- Step 1.U* can obtain the following messages: DIDi(TA) = h(IDi || PWi)⊕h(xa || TA) and DIDi(TB) = h(IDi || PWi)⊕h(xa || TB).
-
Step 2. And then U* can forge the dynamic login identity DID*(TA) and DID*(TB).DID*(TA) = h(ID* || PW*)⊕h(xa || TA)DID*(TB) = h(ID* || PW*)⊕h(xa || TB).
U* can use the login phase formula to compute DIDi(TB), where DIDi(TB) is calculated as DIDi(TB) = DIDi(TA)⊕DID*(TA)⊕DID*(TB) = h(IDi‖PWi) ⊕
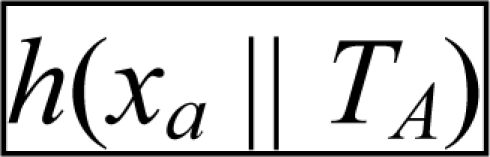 ⊕
⊕
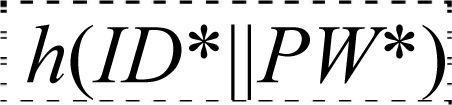 ⊕
⊕
 ⊕
⊕
 ⊕ h(xa‖TB)
⊕ h(xa‖TB)After U* obtains Ui’s DIDi(TB), U* sends a new session message {DIDi(TB), Ci, TS} within ΔT timestamp for a new login request. The timestamp TS, where TS = TB, is made by U* for attack on the WSN.
-
Thus, the GW-node will verify message {DIDi(TB), Ci, TS } from U* with following steps: U*→GW-node:{DIDi(TB), Ci, TS}
Step 1. The GW-node receives {DIDi(TB), Ci, TS} at T* and checks for T* – TS < ΔT. The GW-node passes the verification and proceeds to the next step.
(T* – TB < ΔT is known and TS = TB was made arbitrarily by U*)
Step 2. The GW-node calculates h(IDi || PWi)* = DIDi(TB) ⊕ h(xa || T) and obtains to pass the verification and proceed to the remaining steps.
Consequently, the Das protocol does not provide sufficient protection against a forgery attack by a legal user.
3. ECC-Based Authentication Protocol (EAP) for WSN
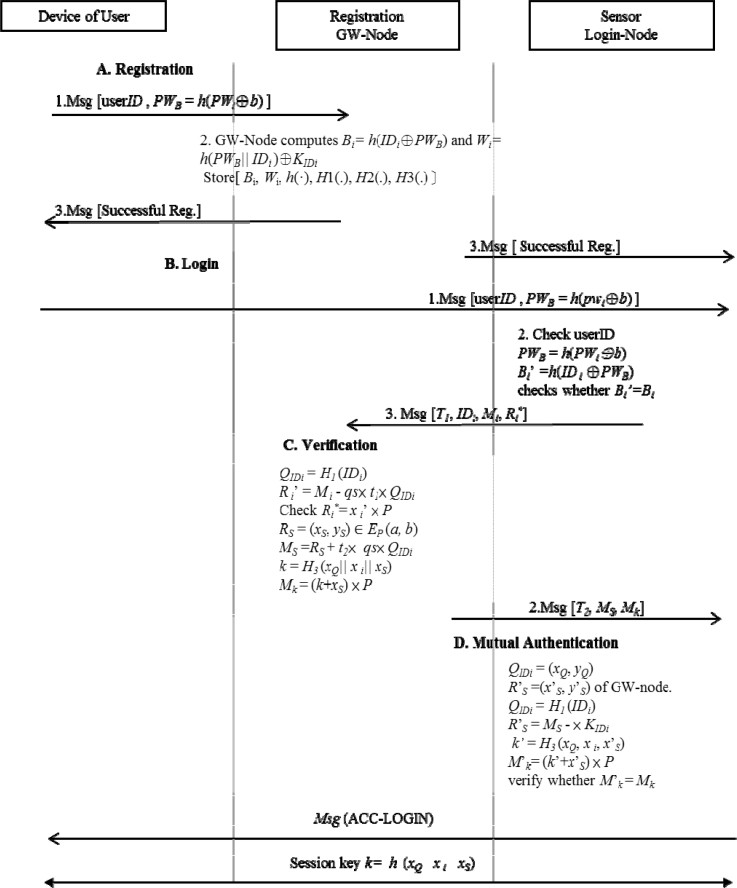
This section proposes a more efficient authentication mechanism using ECC. First, we review the fundamentals of Elliptic Curves and then survey the Elliptic Curves Cryptography (ECC) which is suitable for our construction of a secured authentication protocol for wireless sensor networks. The proposed five phases will be described later. The overall handshake of the proposed protocol is illustrated in Figure 1. The GW-node, Sn and user use the h(xQ||xi||xS) as a session key with communication handshakes.
Figure 1.
Communication handshakes of the proposed scheme.
3.1. ECC Based Authentication Protocol
In 1985 Miller and Kobiltz proposed a secure and efficient elliptic curve cryptosystem (ECC) [17,18]. Because ECC provides a smaller key size than any other cryptosystem, it is suitable for application in smart card and wireless systems.
An elliptic curve is a cubic equation of the form: E: y2 + axy + by = x3 + cx2 + dx + e, where a,b,c, d,e are real numbers. With regard to cryptography, we focus on the finite field of ECC and aim mainly at the prime p of elliptic curve group. The mathematical equation of ECC satisfies the form: E : y2 = (x3 + ax + b) mod p, where (4a3 + 27b2) ≠ 0. Let Fp denote the finite field of points, where p is a large prime number and containing x, y, a,b elements. The equation points and the point at infinity O compose the elliptic curve group over real numbers. We find a large prime number n such that n × P = O using the elliptic curve addition algorithm. Here, × denotes an elliptic curve multiplication. The arithmetic of elliptic curve discrete logarithm problem (ECDLP) is given points Q and P, where Q, P∈ Fp and are both publicly known, determine the random number K, 0 < K < n-1, and compute Q as : Q =K×P is satisfies. It is hard to determine K given Q and P, namely, ECDLP is a complex mathematical problem such that the security is achieved. The analog of Diffie-Hellman key exchange uses elliptic curve characteristics to complete key exchange. The key exchange between UA and UB can be done as follows [18–20]:
The user UA chooses a random integer rA as a private key, where rA < n and computes the public key QA as: QA = rA × P. Then, UA sends QA to the user UB.
The user UB selects a random integer rB as a private key, where rB < n and computes the public key QB as: QB = rB × P.UB sends QB to UA.
UA can compute shared key KA = rA × QB = rA × rB × P and UB can compute shared key KB = rB × QA = rB × rA × P. In this manner we find KA = KB.
3.2. Registration Phase
This phase is invoked whenever user Ui performs registration with the WSN. Then, Ui submits {IDi, PWB} to the GW-node by the secured channel. Then, the GW-node performs the license to Ui. The following steps are performed to complete this phase:
-
Step 1: Ui ⇒ GW-node:{IDi, PWB}.
Ui chooses his/her IDi and PWi password and randomly chooses a large number b for computing PWB = h(PWi ⊕ b).
Step 2: After receiving the registration request, the GW-node computes KIDi = qs × H1(IDi) ∈ Gp, where KIDi is Ui’s authentication key and Gp denotes a cyclic addition group of P.
Step 3: GW-node selects a base point P with the order n over Ep(a, b), where n is a large number for the security considerations. Then, the GW node derives its private/public key pair (qs, QS) by computing QS = qs × P. (Here × denotes an elliptic curve multiplication).
Step 4: GW node computes Bi = h(IDi⊕PWB) and Wi = h(PWB || IDi)⊕KIDi.
Step 5: GW-node ⇒ smart card of Ui :{Bi, Wi, h(·), b, H1(.), H2(.), H3(.)}.
GW-node stores {Bi, Wi, h(·), H1(.), H2(.), H3(.)} on a smart card and sends the smart card to Ui over a secure channel. Here H1(.), H2(.) and H3(.) are one-way hash functions, H1(.): {0, 1} →Gp, and .
Step 6: Upon Ui receiving the smart card, Ui stores the random number b in the smart card. Such that the smart card contains {Bi, Wi, h(·), b, H1(.), H2(.), H3(.)}.
3.3. Login Phase
Assume that Ui enters in order to ask a service from the network, the smart card must perform the following steps to validate the legality of Ui:
Step 1: Ui enters his/her IDi and PWi to login to obtain the message for GW-node request.
Step 2: Ui computes PWB = h(PWi⊕b) and Bi’ = h(IDi⊕PWB) and checks whether Bi’ = Bi. If it holds, U i computes Q = h(PWB||IDi) and KIDi = Wi⊕Q.
When the login request has been accepted, the user proceeds with the remaining steps:
Step 1: After Ui obtaining his/her authentication key KIDi, Ui chooses a random point Ri = (x i, yi) ∈ EP (a, b), where x i and y i are x and y coordinating point of Ri.
Step 2: Ui computes t1 = H2 (T1), Mi =Ri + t1 × KIDi and at the timestamp T1.
-
Step 3: Ui→GW-node: {T1, IDi, Mi, }.
Ui sends message Msg(T1, IDi, M i, ) to GW-node.
3.4. Verification Phase
After receiving the login request message Msg(T1, IDi, Mi, ) at T1 through the nearest sensor node (Sn), the GW-node executes the following steps to verify the user Ui:
-
Step 1: Compute QIDi and Ri’
GW-node performs the following computations to obtain QIDi = (xQ, yQ) and Ri’ = (xi’, yi’) of Ui.
QIDi = H1 (IDi)
t1 = H2 (T1)
Ri’ = Mi – qs× t1× QIDi
Step 2: The GW node verifies whether . If it holds, Ui is authenticated by GW-node.
-
Step 3: GW-node→ Ui: {T2, MS, Mk} through Sn.
The GW node chooses a random point RS = (xS, yS) ∈ EP (a, b) and computes t2 = H2 (T2), MS =RS + t2× qs× QIDi, session key k = H3 (xQ || xi || xS) and Mk = (k + xS) × P.
GW-node sends a message Msg(T2, MS, Mk) through the public channel in order to respond to the request of Sn at the timestamp T2.
3.5. Mutual Authentication Phase
The GW-node sends Msg(T2, MS, Mk) to the Sn and then Sn sends Msg(ACC-LOGIN) to the GW-node. The steps are described as follows:
-
Step 1: Compute QIDi and R’S
After receiving Msg(T2, MS, Mk), the Sn execution obtains the following computation
QIDi = (xQ, yQ) and R’S = (x’S, y’S) of the GW-node.
QIDi = H1 (IDi)
t2 = H2 (T2)
R’S = MS – t2 × KIDi
Step 2: Sn computes k’ = H3 (xQ|| xi || x’S) and M’k= (k’ + x’S) × P to verify whether M’k = Mk. If it holds, GW-node is successfully authenticated by Sn.
3.6. The Password-Changing Phase
When a user Ui enters an IDi and a PWi in order to request a password change, the smart card must compute a new value of to the GW-node. After receiving the password change request, the GW-node computes and .
Step 1: GW-node computes and .
Step 2: GW-node stores the new vale on smart card.
The smart card replaces the original values of Bi, Wi with the new value , and .
4. Security and Performance Analysis
4.1. Security Analysis
The studies we have referenced in this paper have discussed the security issues of remote user authentication. Below is a summary of those security issues, along with the reasons we believe our proposed ECC protocol can address those issues.
Resistance to insider attack: It is common practice for users to apply the same common password to access different applications. If a privileged insider has knowledge of another user Ui’s password, it hey may try to impersonate user Ui to access network applications. Our proposed protocol registers user Ui using cipher code PWB = h(PWi⊕b) over a secure channel. This provides protection against stolen passwords. Thus, our protocol resists insider attacks.
Resistance to masquerade attack: To successfully complete a masquerade attack, an attacker must know Ui’s password in order to pass verification in the login phase and to be able to interpret the verification message correctly for mutual authentication. An attacker, even a legitimate user U*, cannot masquerade as a different legitimate user Ui without Ui’s password for forging the messages sent to the GW-node.
Mutual authentication: Mutual authentication is an important feature for a verification service that is resistant to server spoofing attacks. Our protocol provides a mutual authentication between the user Ui and the GW-node by using ECC-based public and private keys exchange.
Securely change/update password: There is provision for users to update or change their password in our proposed scheme. Namely, a user can send a new password to the GW-node and then the GW-node computes new value of , and stores them on the smart card.
We recall that the protocol [12–16] of Wong et al. does not provide for mutual authentication, and can be vulnerable to forgery and replay attacks. Besides, the proposal of Watro et al. has security weaknesses against masquerade attacks, and Das’ protocol does not provide mutual authentication with an authenticated procedure using the hash function. Further, the weaknesses of Das’ scheme are that it may suffer from an insider attack and a forgery attack. Chen et al.’s scheme is similar in Das’ scheme, and also has the insider attack problem. Besides, the referenced proposals all fail to provide a secure method for updating user passwords. Table 2 compares our proposed protocol with the other referenced protocols in terms of protection against attacks. When compared against each other, our protocol provides a solution for user authentication that is more secure than the other referenced protocols.
Table 2.
Security comparison among the referenced protocols.
| Item | Proposed | Chen et al.’s | Das’ | Watro et al.’s | Wong et al.’s |
|---|---|---|---|---|---|
| Avoiding insider attack | Yes | No | No | Yes | Yes |
| Securely change/update password | Yes | No | No | No | No |
| Avoiding forgery attack | Yes | Yes | No | Yes | No |
| Mutual authentication | Yes | Yes | No | Yes | No |
| Avoiding masquerade attack | Yes | Yes | Yes | No | Yes |
| Avoiding replay attack | Yes | Yes | Yes | Yes | No |
| Avoiding guessing attack | Yes | Yes | Yes | Yes | Yes |
4.2. Performance Analysis
For comparing performance between our protocol and related protocols, we estimate the computation costs. In the definition of computation costs, we define the notation th as the hash computation time, tPA as the elliptic curve point addition computation time, tPM as the elliptic curve point multiplication computation time, tE as the elliptic curve polynomial computation time, tPR as the private key computation time, and tPU as the public key computation time. Note that the computation costs of tPU and tPR are considerably higher than th (tPU ≫ th and tPR ≫ th) because tPU and tPR usually need polynomial computation cost to obtain the public and private keys. Obviously, tE, tPA, tPM calculates a cubic equation at most and th calculates a linear equation or quadratic equation at most. The comparison of related protocols is illustrated in Table 3.
Table 3.
Performance comparison among related protocols.
| Proposed | Chen et al. | Das | Watro et al. | Wong et al. | |
|---|---|---|---|---|---|
| Authentication (Verification and Mutual Authentication) | 11 th + 4 tPA + 6 tPM + 2 tE | 7 th | 5th | 2th+2tPR+2tPU | 4th |
When considering the computation cost in the authentication phase (which includes the verification and mutual authentication phases), our protocol requires only 11 th + 4 tPA + 6 tPM + 2 tE. That is, our protocol needs one point addition operation, four point multiplication operations and one polynomial operation in ECC. However, Watro et al.’s protocol needs two hash functions and four polynomial computations for private key and public key computation. It uses complex RSA and Diffie-Hellman algorithms for user authentication. The polynomial computation time calculates a prime exponential function which is considerably higher than cubic equation [12,17]. In addition, Watro et al.’s protocol needs four polynomial computations, for tPR and tPU, are more than the other referenced protocols [12–16]. Besides, our proposed protocol is computed through combination of point addition and point multiplication, point multiplication is defined by repeated addition. Considering the computation costs, ECC can generate smaller key sizes but maintain equivalent levels of security with RSA [18–20]. This is the reason the ECC-based protocol is more practical than Watro et al.’s protocol.
Lastly, when considering the communication cost, the proposed protocol has higher computation cost than other protocols, except for Watro et al.’s protocol. However, the protocol of Das does not provide mutual authentication. The method we propose solves most of the Das method problems. Furthermore, although Das’s scheme needs five hash computation operations, Wong’s needs four hash computation operations and Chen et al.’s protocol performs wireless sensor networking using seven th, their protocols suffer from security issues. Our proposed protocol addresses these issues and provides better security than the other related protocols.
5. Conclusions
In this paper, we have analyzed Das’ scheme for user authentication in WSNs. The Das protocol, which does not provide mutual authentication, is susceptible to insider and forgery attacks. We have also reviewed the protocols of Wong et al., which is vulnerable to forgery and replay attacks, of Watro et al., which is vulnerable to masquerade attacks, and Chen et al.’s protocol, which is susceptible to insider attacks. Additionally, a user cannot change his/her password with the former schemes. Since WSNs needs more efficient methods to perform mutual authentication in an insecure network environment, we use an ECC-based mechanism to accomplish this. The proposed protocol can prevent all the problems of the former schemes and provide mutual authentication to protect inside security and outside security. Furthermore, it not only inherits the merits of ECC-based mechanism but also enhances the WSN authentication with higher security than other protocols. Therefore, the proposed protocol is more suited to WSNs environments.
Acknowledgments
This paper is supported by the National Science Council, Taiwan, R.O.C., Grant No. NSC 99-2219-E-007-007.
References
- 1.Callaway EH. Wireless Sensor Networks, Architectures and Protocols. Auerbach Publications; Taylor & Francis Group; Boca Raton, FL, USA: 2003. [Google Scholar]
- 2.Yick J, Mukherjee B, Ghosal D. Wireless Sensor Network Survey. Comput. Network. 2008;52:2292–2330. [Google Scholar]
- 3.Sundararaman B, Buy U, Kshemkalyani AD. Clock Synchronization for Wireless Sensor Network: A Survey. Ad-Hoc Networks. 2005;3:281–323. [Google Scholar]
- 4.Martinez K, Hart JK, Ong R. Environmental Sensor Networks. Computer. 2004;37:50–56. [Google Scholar]
- 5.Szewezyk R, Osterweil E, Polastre J, Hamilon M, Mainwaring A, Estrin D. Habitat Monitoring with Sensor Networks. Commun. ACM. 2004;47:34–40. [Google Scholar]
- 6.Das ML, Saxena A, Gulati VP. A Dynamic Id-Based Remote User Authentication Scheme. IEEE Trans. Consum. Electron. 2004;50:629–631. [Google Scholar]
- 7.Leung KC, Cheng LM, Fong AS, Chan CK. Cryptanalysis of a Modified Remote User Authentication Scheme Using Smart Cards. IEEE Trans. Consum. Electron. 2003;49:1243–1245. [Google Scholar]
- 8.Akyildiz IF, Weilian S, Sankarasubramaniam Y, Cayirci E. A Survey on Sensor Networks. IEEE Commun. Mag. 2002;40:102–114. [Google Scholar]
- 9.Sastry N, Wagner D. Proceedings of ACM Workshop on Wireless Security. Philadelphia, PA, USA: Oct 1, 2004. Security Considerations for IEEE 802.15.4 Networks; pp. 32–42. [Google Scholar]
- 10.Watro R, Kong D, Cuti S-F, Gardiner C, Lynn C, Kruus P, Tiny PK. Proceedings of the 2nd ACM Workshop on Security of Ad Hoc and Sensor Networks. Washington, DC, USA: Oct 25, 2004. Securing Sensor Networks with Public Key Technology; pp. 59–64. [Google Scholar]
- 11.Wong KHM, Zheng Y, Cao J, Wang S. A Dynamic User Authentication Scheme for Wireless Sensor Networks. Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing; Taichung, Taiwan. 5–7 June 2006; pp. 244–251. [Google Scholar]
- 12.Das ML. Two-Factor User Authentication in Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2009;8:1086–1090. [Google Scholar]
- 13.Tseng HR, Jan RH, Yang W. An Improved Dynamic User Authentication Scheme for Wireless Sensor Networks. Proceedings of IEEE Globecom; Washington, DC, USA. 26–30 November 2007; pp. 986–990. [Google Scholar]
- 14.Khan MK, Alghathbar K. Security Analysis of Two-Factor Authentication in Wireless Sensor Networks. Proceedings of Advances in Computer Science and Information Technology: AST/UCMA/ISA/ACN 2010 Conferences; Miyazaki, Japan. 23–25 June 2010; pp. 55–60. [Google Scholar]
- 15.Khan MK, Alghathbar K. Cryptanalysis and Security Improvements of ‘Two-Factor User Authentication in Wireless Sensor Networks’. Sensors J. 2010;10:2450–2459. doi: 10.3390/s100302450. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16.Chen TH, Shih WK. A Robust Mutual Authentication Protocol for Wireless Sensor Networks. ETRI J. 2010;32:704–712. [Google Scholar]
- 17.Wireless Medium Access Control and Physical Layer Specifications for Low-Rate Wireless Personal Area Networks. IEEE; Washington, DC, USA: 2003. IEEE Standards for 802.15.4, Part 15, Amendment 4. [Google Scholar]
- 18.Koblitz N. Elliptic Curve Cryptosystems. Math. Comput. 1987;48:203–209. [Google Scholar]
- 19.Miller VS. Advances in Cryptology—CRYPTO '85: Proceedings. Springer; Berlin/Heidelberg, Germany: 1986. Use of Elliptic Curves in Cryptography; p. 417. LNCS Cryptography Volume. [Google Scholar]
- 20.Menezes AJ, Oorschot PC, Vanstone SA. Handbook of Applied Cryptography. CRC Press Inc; Boca Raton, FL, USA: 1997. [Google Scholar]