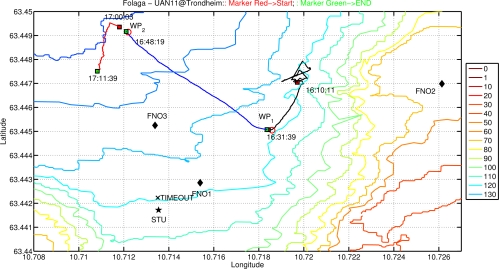
Figure 13.
Folaga path during the experimental activity on May 27. In the first part of the day the vehicle was acoustically controlled by the UAN command and control center to proceed to deeper investigation in an area where an intruder was detected. However, the C2 moved the vehicle too far from the network where it lost the connectivity. According to the behavior described in Section 3 the vehicle autonomously planned a new mission to move towards the high value asset (the base station) to protect where it could re-enter the network.