Figure 7.
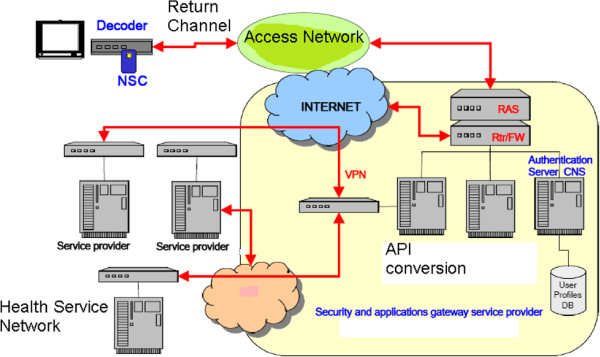
NSC-based authentication process. Architecture of the network infrastructure required for NSC-based security implementation.

NSC-based authentication process. Architecture of the network infrastructure required for NSC-based security implementation.