. 2013 Apr;14(2):91–110. doi: 10.2174/1389202911314020003
©2013 Bentham Science Publishers
This is an open access article distributed under the terms of the Creative Commons Attribution License (http://creativecommons.org/licenses/by/2.5/), which permits unrestrictive use, distribution, and reproduction in any medium, provided the original work is properly cited.
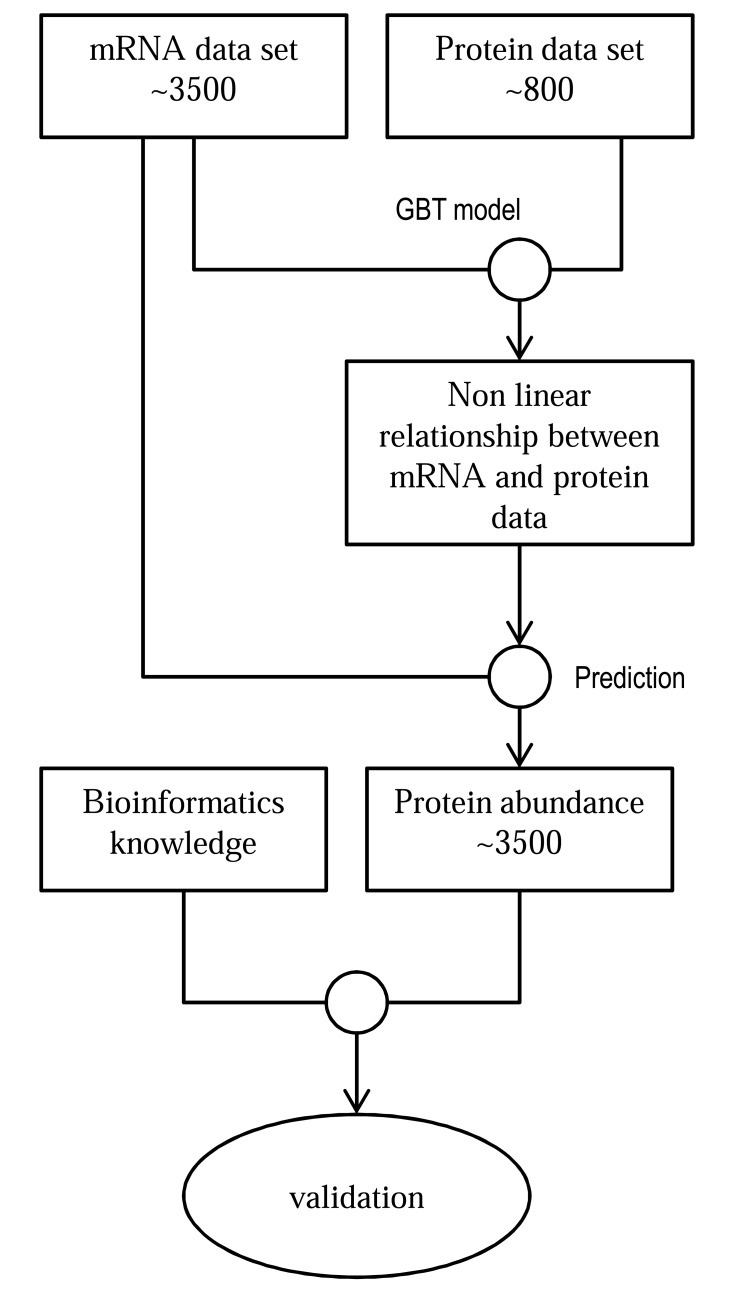
Fig. (3).
Flowchart of the method used by Garcia et al. [77].