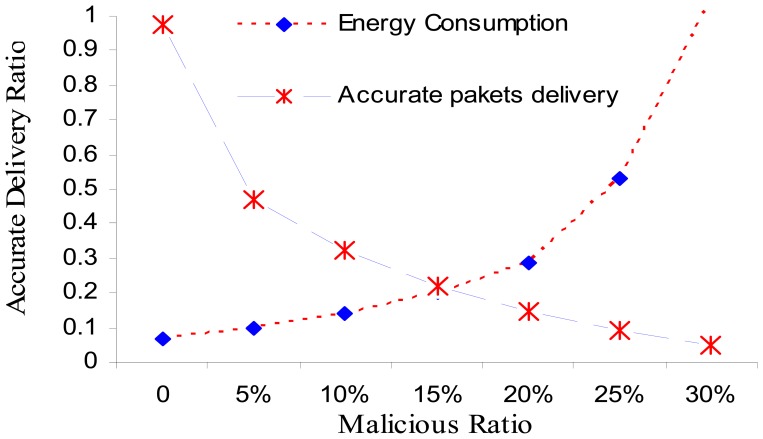
Figure 9.
Black Hole attack run with seven scenarios implemented according to the number of malicious nodes on the network, the energy consumption of each sensor node is as follows [17]: Ea =100 pJ/bit/m2, Ee = 50 nJ/bit and Ec = 5 nJ/bit where consumed for transmitting, receiving and listening respectively. Each sensor needs to send a packet of length R = 400 bits to the cluster head on random time. Cluster head period T is set as 2,000 s and the execution time of task is set as = 0.005 s. The data packet size is 2 KB and the sensing range to 64 meters.