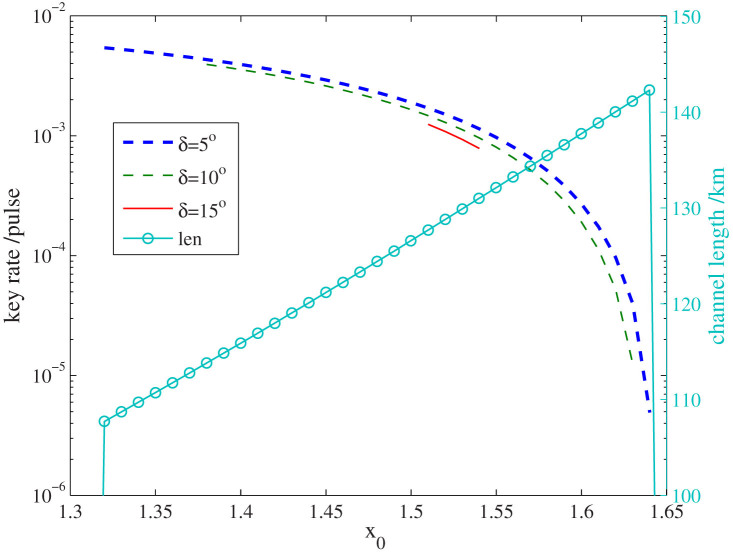
Figure 3. The estimated key rate of Alice and Bob under our attack.
But in fact, the key are insecure, since our attack corresponds to an entanglement-breaking channel and no secret key can be generated under this channel. Here we also show the equivalent channel length of Qμ, defined as len = −(10/a) log10{min(1, Qμ/(μηBob)} (a = 0.21 is the loss of standard fiber), which represents the minimal channel length of Alice and Bob that Eve can successfully load our attack. In the simulations, we assume that the SPD and homodyne detection of Eve are perfect, and set f(Eμ) = 1.22, Y0 = 1.7 × 10−6, ηBob = 0.045, μ = 0.48, and ν = 0.1 according to the experimental results of Ref. 6.