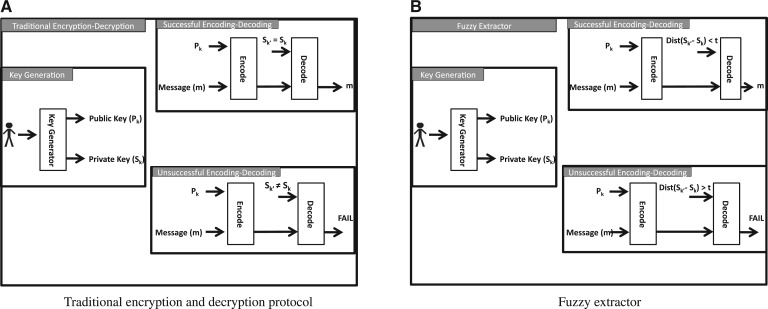
Fig. 1.
In traditional encryption and decryption protocol, each individual generates two codes using the key generation process. The public key (Pk) is accessible by every one, and the private key (Sk) should be kept secret. In order to send a secure message to a sender we will use the public key available by the sender to encode the message. Then, the receiver will use the secret key (private), which was generated for the sender with the public key in the key generation process, to decrypt the message as shown in panel (A). The Fuzzy extractor is similar to traditional encryption and decryption protocol with one major difference, that the private key to decrypt the encrypted message has to be close to the original private key, which was generated in key generation process, and not necessary the same key as shown in panel (B)