Table 2.
Basic notation.
| Symbol | Description |
|---|---|
| UR | User |
| SR | Sensor |
| GW | Gateway |
| IDUR,IDSR,IDGW | Identities of UR, SR and GW |
| pwUR | Password of U |
| sk | Session key |
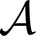
|
Probabilistic polynomial-time adversary |
| L(·),H(·),F(·) | Cryptographic hash functions |
| Enck(·)/Deck(·) | Symmetric encryption/decryption under key k |
| MAC | Message authentication code |
| Mack(·)/Verk(·) | MAC generation/verification under key k |
| ⊕ | Bitwise exclusive-or (XOR) operation |
| ‖ | String concatenation operation |
| {0,1}n | Bit strings of length n |
