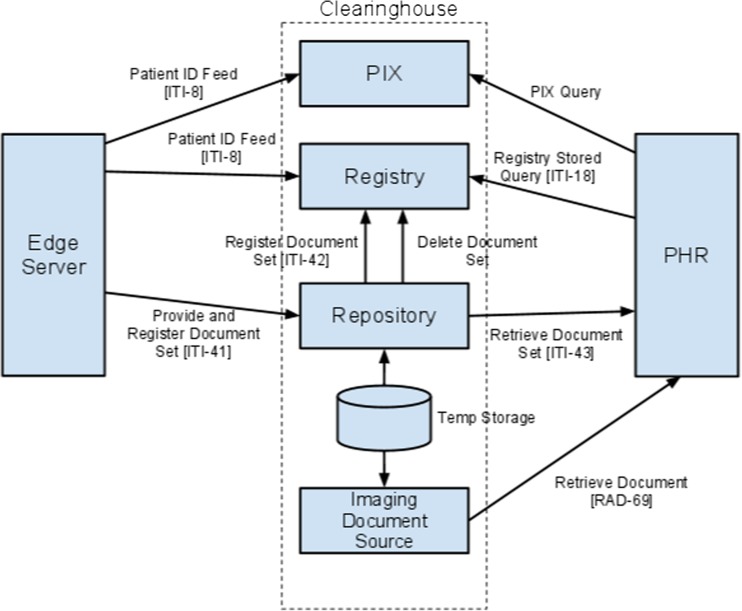
Fig. 5.
An exploded view of the Clearing House, detailing the XDS transactions alluded to in the previous figure. In place of real patient Identifiers that would typically be used in an XDS-b.i implementation, the ISN substitutes a three-factor hash consisting of data only the patient knows. All these transactions are over secure HTTP links, and the submitted document set is also encrypted via the aforementioned hash