Fig 11. Key sensitivity test I.
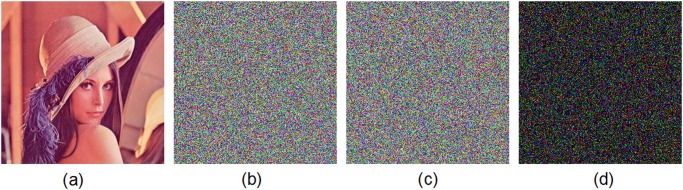
(a) Original image of Lena, (b) encrypted image of Lena with the secret key K1, (c) encrypted image of Lena with the secret key K2, (d) difference image.

(a) Original image of Lena, (b) encrypted image of Lena with the secret key K1, (c) encrypted image of Lena with the secret key K2, (d) difference image.