Figure 2. Bob’s encoding and encrypting methods.
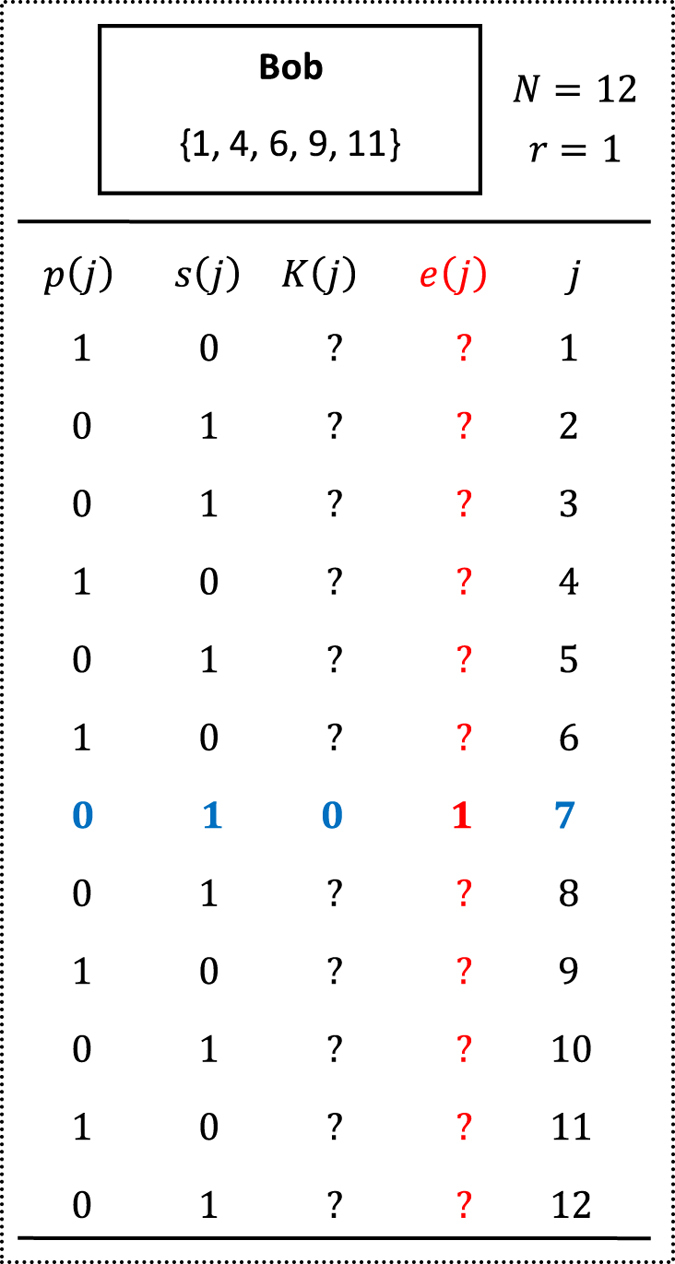
All 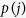 s,
s, 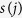 s and
s and 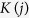 s are private, while all
s are private, while all 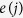 s are public. Alice can only decrypt
s are public. Alice can only decrypt 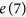 to further get
to further get 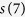 with the key
with the key 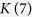 . Finally, Bob can rightly get
. Finally, Bob can rightly get 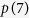 by computing
by computing 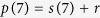 .
.

All 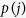 s,
s, 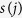 s and
s and 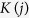 s are private, while all
s are private, while all 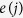 s are public. Alice can only decrypt
s are public. Alice can only decrypt 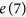 to further get
to further get 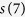 with the key
with the key 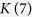 . Finally, Bob can rightly get
. Finally, Bob can rightly get 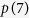 by computing
by computing 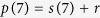 .
.