Table 7.
Energy Consumption results.
| Attack | Node 1: Hardware Crypto + Attack Aware Firmware | Node 2: Software Crypto + Insecure Firmware |
|---|---|---|
| Not Attacked | 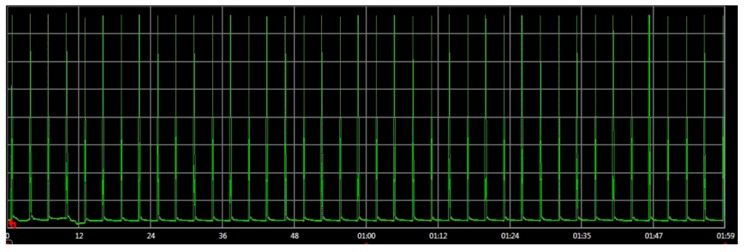 |
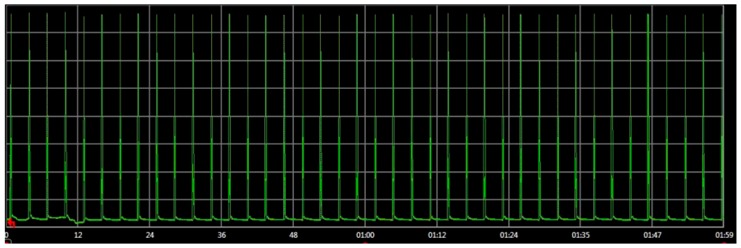 |
| 2.02 mWh | 2.02 mWh | |
| Replication Attack | 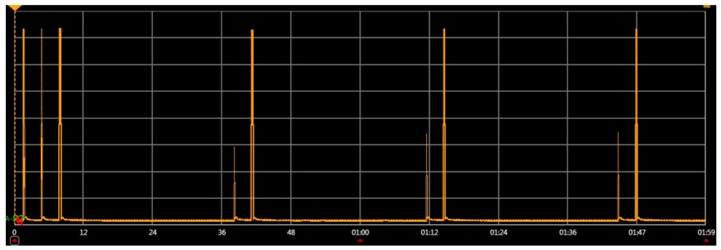 |
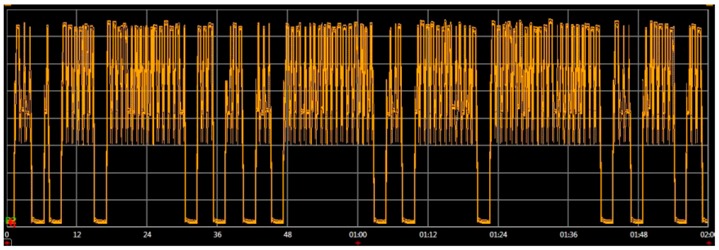 |
| 1.93 mWh | 4.48 mWh |
Energy Consumption results.
| Attack | Node 1: Hardware Crypto + Attack Aware Firmware | Node 2: Software Crypto + Insecure Firmware |
|---|---|---|
| Not Attacked |  |
 |
| 2.02 mWh | 2.02 mWh | |
| Replication Attack |  |
 |
| 1.93 mWh | 4.48 mWh |