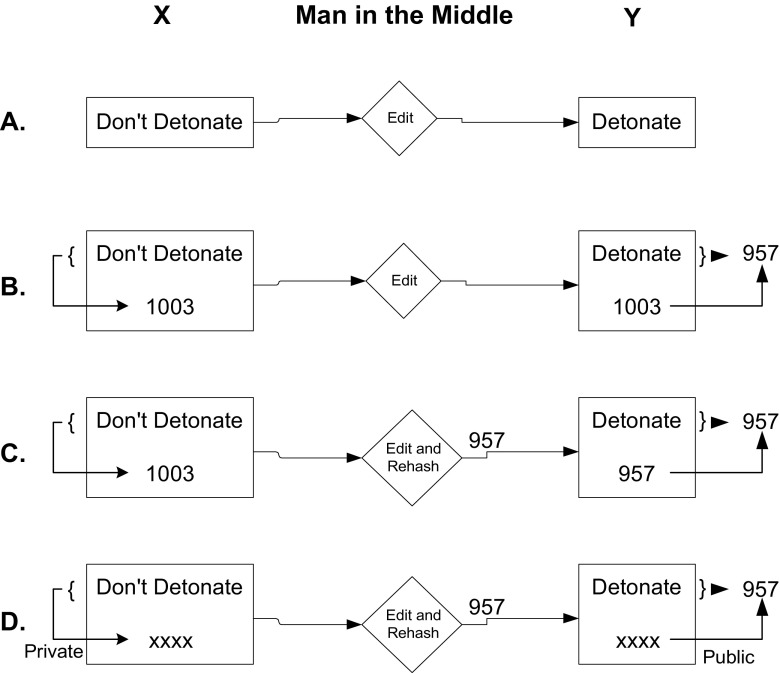
Fig. 1.
(A) X sends a message, and it is altered by M. Y cannot discern the alteration. (B) X computes the document’s message digest (MD) and sends its value (1003) with the document. M alters the message. Y recomputes the MD of the message and detects an alteration, because the MDs do not match (957 ≠ 1003). (C) This time, M recomputes the MD and sends it with the altered message. Now when Y recomputes the MD and checks against the sent MD, the two match, and Y is fooled. (D) X digitally signs the MD, and M cannot reproduce X’s signature without X’s private key. Nevertheless, M alters the message. When Y decodes the MD signed by X and compares it with the recomputed MD of the altered message, Y detects the substitution (957 ≠ 1003)