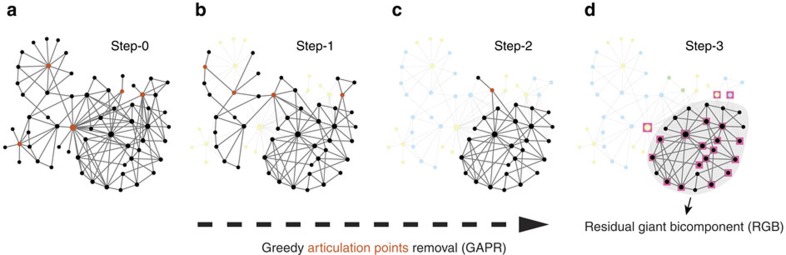
Figure 1. Articulation points and the greedy articulation points removal process.
(a) Articulation points in the terrorist communication network from the attacks on the United States on September 11, 2001 are highlighted in red. This network contains in total 62 nodes and 153 links13. (b,c) At each time step, all the articulation points and the links attached to them are removed from the network. This greedy articulation points removal procedure can be considered as a network decomposition process: at each step, all the removed nodes (because of the removal of articulation points in the current network) form a layer in the network. We peel the network off one layer after another, until there is no articulation point left. We find that this terrorist communication network consists of 3 layers, shown in light yellow, blue, and green, respectively. (d) After 3 steps, a well-defined residual giant bicomponent is left, which contains 26 of the 62 nodes. Interestingly, 16 of the 19 hijackers (highlighted with squares) are in the residual giant bicomponent, which is statistically significant (Fisher's exact test yields a two-tailed test P value 1.13 × 10−5).