Fig. 4. High-dimensional QKD without and with quantum hacking.
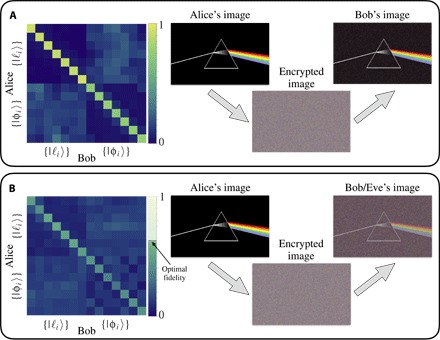
(A) Experimental probability matrices obtained from projective measurements are shown on the left side. The bases selected by Alice and Bob are indicated on the vertical and horizontal axes, respectively. On the right, we show Alice’s initial message and Bob’s decrypted message. (B) Experimental probability matrices with the presence of an eavesdropper having access to a symmetric optimal UQCM. Similarly, Alice’s initial message is shown along with the decrypted message obtained by both Bob and Eve. One may note that for the BB84 protocol, the symmetric UQCM does not lead to the optimal individual attack. Rather, our UQCM results in the optimal individual attack for the QKD protocol exploiting all d + 1 available MUBs. In the simpler case of the BB84 protocol, the optimal attack consists of the asymmetric Fourier-covariant cloner (1, 26), which cannot be straightforwardly implemented in our experimental setup.
