. 2017 Apr 27;19(4):e131. doi: 10.2196/jmir.7065
©Hsiao-Hsien Rau, Yi-Syuan Wu, Chi-Ming Chu, Fu-Chung Wang, Min-Huei Hsu, Chi-Wen Chang, Kang-Hua Chen, Yen-Liang Lee, Senyeong Kao, Yu-Lung Chiu, Hsyien-Chia Wen, Anis Fuad, Chien-Yeh Hsu, Hung-Wen Chiu. Originally published in the Journal of Medical Internet Research (http://www.jmir.org), 27.04.2017.
This is an open-access article distributed under the terms of the Creative Commons Attribution License (https://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work, first published in the Journal of Medical Internet Research, is properly cited. The complete bibliographic information, a link to the original publication on http://www.jmir.org/, as well as this copyright and license information must be included.
Figure 3.
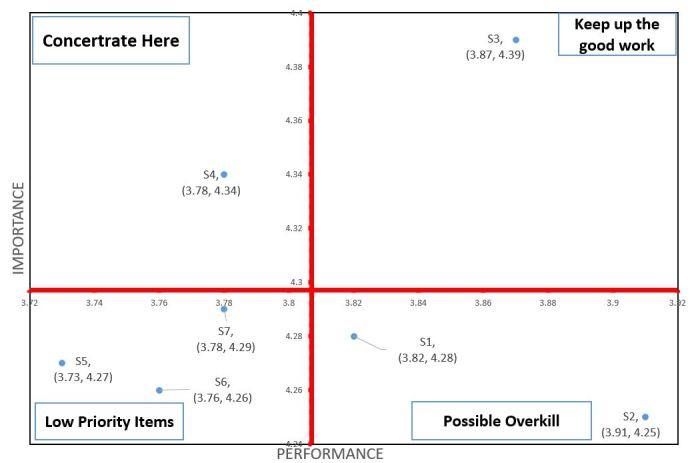
Quadrant diagram of the importance and performance of the security of the system.
