Abstract
In recent years, with the increase in degenerative diseases and the aging population in advanced countries, demands for medical care of older or solitary people have increased continually in hospitals and healthcare institutions. Applying wireless sensor networks for the IoT-based telemedicine system enables doctors, caregivers or families to monitor patients’ physiological conditions at anytime and anyplace according to the acquired information. However, transmitting physiological data through the Internet concerns the personal privacy of patients. Therefore, before users can access medical care services in IoT-based medical care system, they must be authenticated. Typically, user authentication and data encryption are most critical for securing network communications over a public channel between two or more participants. In 2016, Liu and Chung proposed a bilinear pairing-based password authentication scheme for wireless healthcare sensor networks. They claimed their authentication scheme cannot only secure sensor data transmission, but also resist various well-known security attacks. In this paper, we demonstrate that Liu–Chung’s scheme has some security weaknesses, and we further present an improved secure authentication and data encryption scheme for the IoT-based medical care system, which can provide user anonymity and prevent the security threats of replay and password/sensed data disclosure attacks. Moreover, we modify the authentication process to reduce redundancy in protocol design, and the proposed scheme is more efficient in performance compared with previous related schemes. Finally, the proposed scheme is provably secure in the random oracle model under ECDHP.
Keywords: elliptic curve cryptography (ECC), Internet of Things (IoTs), medical care system, smart cards, user authentication, wireless sensor networks (WSNs)
1. Introduction
As more network technologies and smart devices have been developed, many IoT (Internet of Things) applications have been proposed, such as transportation and logistics services, healthcare services and a variety of smart environment (home, office, plant) domains. IoT is going to create a world where physical things can be seamlessly integrated into communication networks in order to provide autonomous and intelligent services for improving human beings’ life. In general, the IoT system involves three components: a sensing unit contains a large number of sensors, actuators and mobile terminals to sense physical environments; a network layer includes all network techniques with heterogeneous network configurations for data transmission; intelligent computing offers expected services or applications to IoT end users by mining and analyzing data processors.
IoT-based wireless sensor networks have been getting considerable attention from a variety of domains, such as environmental monitoring, intelligent appliances in daily living, medical care services, etc. Due to the ranking of the most common diseases in advanced countries having changed to chronic and cardiovascular diseases, the demands for medical care of such patients have increased substantially in hospitals and healthcare institutions. For the development of medical care services in hospitals and healthcare institutions, IoT-based WSNs technology is used to supplement physiological collection and measurement, enabling doctors, caregivers and families to examine the physiological conditions of patients remotely at anytime and anyplace through the Internet [1,2,3,4,5,6]. On the basis of IoT employed for medical care service in hospitals or healthcare institutions, WSNs enable sensing and collecting the physiological parameters of patients periodically, transmitting the acquired data to the authorized medical personnel, enabling professional doctors and medical personnel to monitor patients’ health conditions in real time and providing patients with appropriate medical care and medical treatment.
To apply IoT-based WSNs to medical care services successfully, ensuring the personal privacy of patients and preventing malicious network intrusion are paramount. Undoubtedly, the foundation of security is to authenticate the legitimacy of remote users and ensure the integrity of data transmissions [7,8,9,10,11,12]. In the last decade, a diversity of user authentication schemes in WSNs have been presented. In 2006, Wong et al. [13] introduced an efficient user authentication scheme for WSNs using lightweight hashing functions and XOR operations. In 2007, Tseng et al. [14] pointed out the vulnerability of Wong et al.’s scheme to replay, forgery and password guessing attacks. Furthermore, in 2008, Lee [15] showed that the computational overheads of Wong et al.’s scheme are not suitable for resource-constrained sensor nodes. In 2009, Das [16] suggested a two-factor (namely the password and smart card) authentication mechanism for WSNs, which not only prevents a series of security threats, but also achieves efficiency in terms of computational overheads. However, Huang et al. [17] and Li et al. [18] pointed out the vulnerability of Das’s scheme to off-line password guessing, user impersonation, node impersonation and unknown user attacks and that it does not provide the property of user anonymity. In 2012, Yoo et al. [19] pointed out the vulnerability of Huang et al.’s scheme to insider and parallel session attacks and that it does not provide mutual authentication between system participants. In 2013, Xue et al. [20] presented a temporal-credential-based authentication scheme for resource-constrained WSNs, and the authors claimed that their scheme provides relatively more security criteria without increasing system overheads too much in terms of communication, computation and storage. Parallel to Xue et al.’s work, in the same year, Li et al. [3] cryptanalyzed that Xue et al.’s scheme cannot withstand off-line password guessing, stolen-verifier, privileged insider, many logged-in users’ and stolen smart card attacks, and the above security threats make Xue et al.’s scheme inapplicable to practical WSN applications.
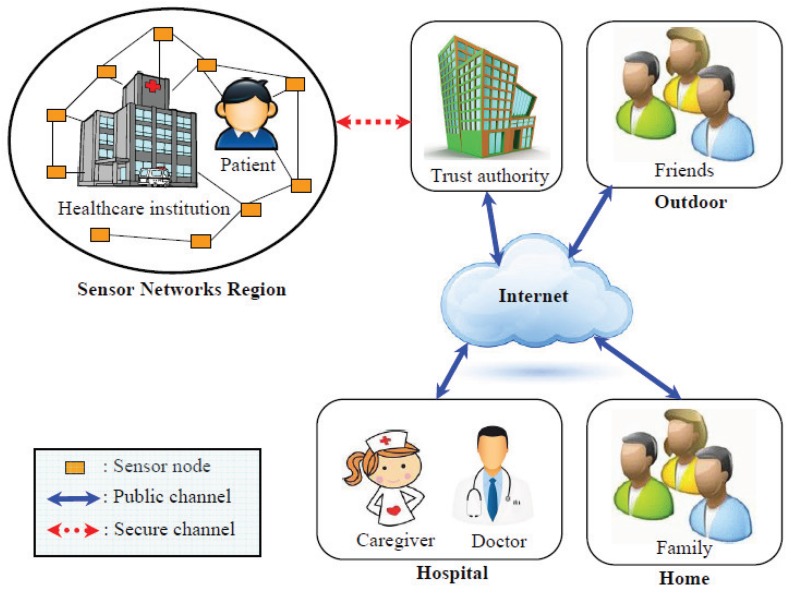
In order to design a secure and two-factor user authentication scheme for wireless healthcare sensor networks, Liu and Chung [21] in 2016 proposed a bilinear pairing-based [22] authentication scheme, and Figure 1 illustrates the comprehensive structure of the IoT-based medical care system, which could be applied in hospitals or healthcare institutions. When patients live in hospitals or healthcare institutions, they wear smart clothes in which body sensors are embedded in the piece of clothing and collect their physiological parameters (such as blood pressure, heartbeat, body pulse, electrocardiography and body temperature). Therefore, the users (such as doctors, caregivers, families and friends) in the medical care system can remotely inquire and monitor physiological information on patients with the help of trust authority. Before accessing the system, users must register with the trusted authority in person. After successful registration, the trusted authority issues a smart card to the user, and he/she can then use his/her smart card and mobile devices (such as smart phone, PDA, laptop and tablet computer) to log into the medical care system. After successful authentication, the user can access the sensed data of patients measured from sensor nodes within a limited time. Nevertheless, in this paper, we present a cryptanalysis of Liu–Chung’s authentication scheme and indicate that their scheme is susceptible to the password disclosure, replay, sensed data disclosure, sensed data forgery, off-line password guessing and stolen smart card attacks. To solve the above-mentioned security problems, we present an improved version of Liu–Chung’s authentication scheme using ECC, and we prove that the proposed scheme is secure under the elliptic curve discrete logarithm problem (ECDLP) and the elliptic curve Diffie–Hellman problem (ECDHP). In addition, by designing the mechanism of dynamic identity in the authentication process, we can build an extended scheme with user anonymity. User anonymity [23,24,25] means that a remote user’s real identity will be masked during the login session, and he/she cannot be linked or traced by any outsiders. Furthermore, the correctness of mutual authentication between participants has been proven in the random oracle model under ECDHP. Finally, the proposed scheme requires lower computational overheads compared with other ECC-based schemes, and this advantage makes our scheme more suitable and practical for IoT-based medical care systems.
Figure 1.
The IoT-based medical care system [21].
The rest of the paper is organized as follows. In Section 2, a brief review of Liu–Chung’s authentication scheme is provided. In Section 3, security weaknesses developed to attack Liu–Chung’s scheme are presented. In Section 4, the improved scheme is proposed. Security and performance analyses of our proposed scheme are presented in Section 5 and Section 6, respectively. Section 7 concludes this paper.
2. Review of Liu–Chung’s Authentication Scheme
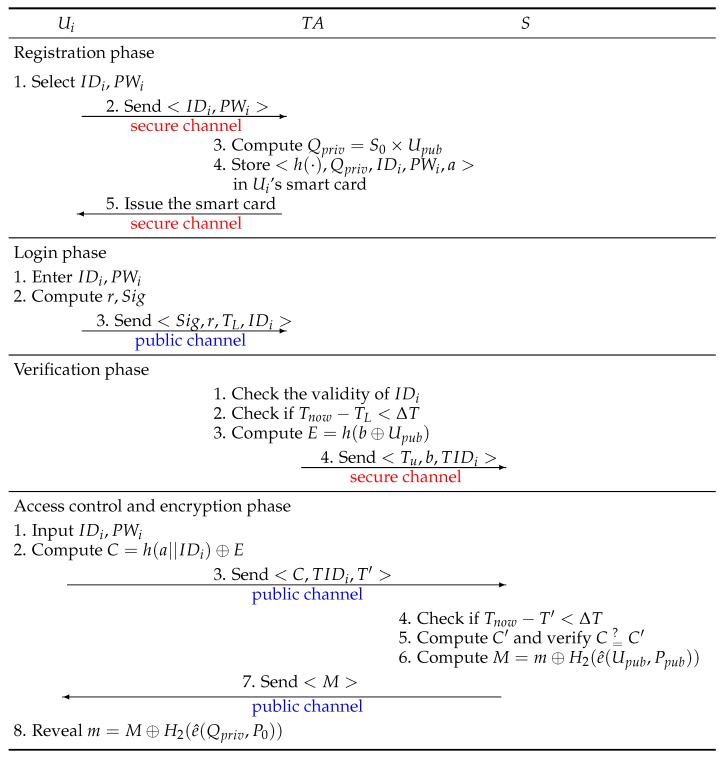
This section briefly reviews Liu–Chung’s authentication scheme [21], and their scheme consists of five phases, including: setup phase, registration phase, login phase, verification phase and access control and encryption phase. For convenience of description, the terminology and notations used in the paper are summarized as follows:
: The user.
: The trusted authority.
S: The sensor nodes deployed in hospitals and healthcare institutions.
: The identity of .
: The password of .
: A one-way hash function.
: The bilinear pairing function using parameter a and parameter b.
a: A private parameter generated by .
: The login time of .
: The current time.
: The time limit on the legal access to S by the user .
: The transmission delay.
m: The sensed data collected from S.
: The message concatenation.
⊕: The XOR operation.
2.1. Setup Phase
In this phase, the trusted authority selects a bilinear map and and generates two one-way hash functions and , where is an additive cyclic group of points on an elliptic curve E over , is a multiplicative cyclic group of a finite field and p is a large prime, such that for some great prime q. Then, selects the secret key and publishes the parameter .
2.2. Registration Phase
In this phase, the user registers with the trusted authority through a secure channel to be a legal user. The details of registration phase are as follows:
-
Step 1:
registers an authenticated identity with and sets password .
-
Step 2:
sends to .
-
Step 3:
computes , where and are ’s public parameter and secret key, respectively.
-
Step 4:
stores the parameters in ’s smart card, where a represents a private parameter generated by and all of the sensor nodes of include a.
-
Step 5:
issued the smart card to .
2.3. Login Phase
In this phase, the user inserts his/her smart card into the device and inputs and . Then, the smart card performs the following steps:
-
Step 1:
The smart card checks the and entered by matches those stored in the smart card. If yes, the smart card executes Step 2. Otherwise, the smart card terminates this phase.
-
Step 2:
The smart card computes and .
-
Step 3:
The smart card sends to through a public channel, where represents ’s login time to the .
2.4. Verification Phase
When receives the login request from , authenticates through the following steps:
-
Step 1:
checks the validity of and verifies if . If yes, approves the request of and executes Step 2. If no, rejects the request of .
-
Step 2:
checks if . If yes, executes Step 3. Otherwise, it means that the login time exceeds the transmission delay, and the login request is rejected by .
-
Step 3:
generates a random number b and computes . Then, sends E to through a public channel.
-
Step 4:
sends to all of the sensor nodes S through a secure channel and notifies S that is legal. Note that represents the time limit on the legal access to sensor node data by .
2.5. Access Control and Encryption Phase
When the user is authenticated as legal, can legally access sensed data m in S within a limited time, and and S perform the following steps:
-
Step 1:
inserts his/her smart card into the device and inputs and . Then, the smart card verifies whether and inputted matches the data stored in the card. If yes, the smart card executes Step 2.
-
Step 2:
The smart card computes .
-
Step 3:
The smart card sends to S through a public channel, where represents a timestamp.
-
Step 4:
Upon receiving from , S verifies if and . If yes, S executes Step 4.
-
Step 5:
S computes and checks whether . If yes, the sensed data m will be transmitted, and S executes Step 5. If no, S terminates this session.
-
Step 6:
S computes .
-
Step 7:
S sends M to through a public channel.
-
Step 8:uses the secret parameter and the public parameter to perform the following calculation to obtain m:
Figure 2 shows the schematic of Liu–Chung’s authentication scheme for the IoT-based medical care system.
Figure 2.
The schematic of Liu–Chung’s authentication scheme for IoT-based medical care system.
3. Weaknesses of Liu–Chung’s Authentication Scheme
In this section, we present the security weaknesses of Liu–Chung’s scheme. We show that their scheme has some security problems and that an attacker can mount different types of attacks on Liu–Chung’s scheme.
3.1. Password Disclosure Attacks
In real environments, the user may register with a number of remote services by using a common password and the identity for his/her convenience. Thus, the privileged-insider of may try to use the knowledge of user’s and to access another remote services. In the registration phase of Liu–Chung’s scheme, registers to by sending . Therefore, ’s sensitive password will be revealed by the privileged-insider of .
3.2. Replay Attacks
In the login phase of Liu–Chung’s scheme, although the transmitted login message includes timestamp , however, the other login parameters of are unchanged. Thus, an attacker could replay the eavesdropped messages, such as ’s login request with ’s current login time . Finally, can bypass the timestamp checking and replay attacks cannot prevented in Liu–Chung’s scheme.
3.3. Sense Data Disclosure Attacks
In the access control and encryption phase of Liu–Chung’s scheme, the sensor node S sends the encrypted sensed data M to through an insecure channel. Due to the public of and the public of , once an attacker eavesdrops the encrypted sensed data M from the public channel, can perform the following calculation to obtain m without knowing :
Finally, Liu–Chung’s scheme cannot prevent sensed data disclosure attacks.
3.4. Sense Data Forgery Attacks
In the access control and encryption phase, we found that Liu–Chung’s scheme allows the attacker to forge a fake sensed data for the user , and wrongly believes he/she has received the physiological conditions of the patients. The sensed data forgery attacks on Liu–Chung’s scheme are as follows:
-
(1)
When the sensor node S sends to the user , intercepts the message M.
-
(2)
maliciously forges a fake sensed data and computes , where and are public parameters of and , respectively. Then, sends to the user .
-
(3)
Upon receiving the message , uses the secret parameter and the public parameter to obtain .
Therefore, the attacker can control the sensed data that occur between the user and the sensor nodes S.
3.5. Stolen Smart Card Attacks
Usually, the smart card of the user is equipped with tamper-resistant hardware. However, if ’s smart card is lost or stolen, the attacker may obtain all of the sensitive parameters stored in its memory by monitoring the power consumption of the smart card [26]. Assume that obtains the smart card of and extracts the parameters stored inside it. then can make a valid login request with ease. For example, uses , , , a and and computes and . Finally, can make a valid login request to impersonate by sending to the trusted authority , where is the current login time of .
3.6. Off-Line Password Guessing Attacks
Since Liu–Chung’s authentication scheme is executed in the open network environment, then we assumed that an attacker can eavesdrop the communication channels between and in the login phase. Moreover, we assumed that was a legitimate user in the medical care system, and he/she can extract the parameter a by launching power analysis attack [26]. Thus, could guess ’s password through the following steps.
-
(1)
eavesdrops the message sent by a legal user , where .
-
(2)
guesses a password and computes in an off-line manner.
-
(3)
checks whether is equal to r or not. If it is equal, ’s sensitive password is successfully guessed. Otherwise, repeats Steps (1) and (2) until the correct password is found.
From the above descriptions, we conclude that could derive ’s password through an off-line manner, and Liu–Chung’s authentication scheme could not succeed against the off-line password guessing attacks.
4. The Proposed Scheme
This section proposes the new and improved lightweight user authentication scheme for medical care tailored for the Internet of Things environment. The proposed scheme is based on Liu–Chung’s scheme; thus, it tackles and eliminates all of the previously-mentioned security problems and vulnerabilities of their scheme. As Liu–Chung’s scheme, the proposed scheme also consists of five phases: setup, registration, login, verification and access control and encryption. Figure 3 shows the schematic of our proposed scheme for the IoT-based medical care system.
Figure 3.
The schematic of our proposed scheme for IoT-based medical care system.
4.1. Setup Phase
In this phase, the trusted authority selects an elliptic curve E over and a base point over the E and chooses a secure one-way hashing function , where p is a large prime such that for some great prime q and l means the length of the output. In addition, chooses the secret key and computes its public key . Finally, keeps securely and publishes as system parameters.
4.2. Registration Phase
In this phase, the user registers with the trusted authority through a secure channel to be a legal user, and the details of registration phase are as follows:
-
Step 1:
registers an authenticated identity and password with and chooses a random number r for computing .
-
Step 2:
sends the registration request to through a secure channel.
-
Step 3:
checks whether has been registered or not. If has not been registered, computes and . Then, stores the parameters in ’s smart card and issued the smart card to , where a represents a private parameter generated by and all the sensor nodes of include a.
-
Step 4:
computes , and and stores into the smart card. Finally, ’s smart card contains the parameters .
4.3. Login Phase
In this phase, the user inserts his/her smart card into the device and inputs and . Then, the smart card executes the following steps:
-
Step 1:
The smart card checks the and entered by matches those stored in the smart card. First, the smart card computes , and and verifies whether . If it holds, the smart card executes Step 2. Otherwise, the smart card terminates this phase.
-
Step 2:
The smart card generates a random number and computes , , and and sends to through a public channel, where represents ’s login time to the .
4.4. Verification Phase
When receives the login request from , authenticates through the following steps:
-
Step 1:
checks if . If yes, executes Step 2. Otherwise, it means that the login time exceeds the transmission delay, and the login request will be rejected by .
-
Step 2:
computes and and checks if user’s is recorded by . If yes, executes Step 3. Otherwise, the login request is denied by .
-
Step 3:
goes on to compute by using the identity and checks that the decrypted is the same as computed . If no, the session is aborted by . Otherwise, computes and sends the response message to through a public channel, where b represents a random number and represents a temporary identity for the user .
-
Step 4:
sends to all of the sensor nodes S via a secure channel and notifies S that the temporary identity is legal in the next access control and encryption phase.
-
Step 5:
When receives from , authenticates by computing and checks that the decrypted is involved in or not. If yes, confirms that is legal and the parameters , and E will be used in access control and encryption phase. Otherwise, ends this session. Note that and E must be kept secret by and temporarily stored into ’s smart card until the end of the access control and encryption phase.
4.5. Access Control and Encryption Phase
When the user is authenticated as legal, can legally access sensed data m in S within a permitted time , and and S perform the following steps:
-
Step 1:
In this step, the executed operations are the same as Step 1 of the login phase.
-
Step 2:
The smart card calculates and sends to S through a public channel, where represents a timestamp.
-
Step 3:
Upon receiving from , S verifies if and . If yes, S executes Step 4.
-
Step 4:
S computes by using the b transmitted by and the temporary identity of the user to examine whether . If yes, the validity of is authenticated by S, and the sensed data m will be transmitted by S. If no, S terminates this session.
-
Step 5:
S computes the session key and encrypts the sensed data by computing . Then, S sends to through a public channel. Note that the session key provides a secure channel for protecting data transmission between S and .
-
Step 6:
When receives from S, uses the parameters to calculate the session key and decrypts the sensed data m by computing .
Note that should be frequently updated when ’s is expired. If so, returns to the login and verification phases for requesting a new with . Finally, a new will be established and updated among and S in the access control and encryption phase.
5. Security Analysis of the Proposed Scheme
In this section, we analyze the security of our proposed scheme, and show that it is able to prevent the above-mentioned weaknesses in Liu–Chung’s scheme. The security of the proposed scheme is based on the collision-free one-way hash function and two hard problems: the elliptic curve discrete logarithm problem (ECDLP) and the elliptic curve Diffie–Hellman problem (ECDHP), defined as follows:
-
ECDLP:
Given a base point P over an elliptic curve E and a random variable , it is computationally infeasible to find out an integer solution a such that .
-
ECDLP:
Given three parameters , it is computationally infeasible to compute .
We analyze and summarize the main security advantages of our proposed scheme as follows.
5.1. Resistance to Password Disclosure and Password Guessing Attacks
In the registration phase, the user’s password is used in the message . Although the privileged-insider of can obtain the message and the identity of the user, it is unable to know the user’s sensitive password due to r being randomly selected by the user, and is protected by . Note that deriving from is equal to implementing the brute-force attack to crack the one-way hashing function. Moreover, during the login, verification and access control and encryption phases, neither the smart card nor the transmitted messages include user’s password . Hence, the proposed scheme eliminates the possibility of password disclosure and password guessing attacks.
5.2. Resistance to Replay Attacks
The timestamps and random numbers are common countermeasures to prevent replay attacks in the authentication process. Since the messages and contain freshly generated timestamps and and these timestamps are also embedded in the protected messages and , thus each participant first checks the freshness of timestamps received and verifies whether the same timestamps are present in the transmitted messages. Hence, this design discards the possibility of replay attacks in our proposed scheme.
5.3. Resistance to Sensed Data Disclosure Attacks
In the access control and encryption phase of the proposed scheme, the sensed data m is embedded in the encrypted message , and m is well-protected via high-entropy session key . Here, we assume that can obtain the parameter a from a legal smart card and can eavesdrop the transmitted messages and from the public channels between the user and the sensor nodes S. can use the collected parameters to compute and and derive . However, without having the knowledge of secrets E and , an attacker cannot derive from because of the irreversibility of the secure one-way hashing function.
On the other hand, during the login phase of the proposed scheme, we assume that the parameter and the public key of are disclosed. However, the secret parameter cannot be calculated by since the random number is unknown due to the infeasibility of deriving them from by solving ECDLP. Moreover, during the access control and encryption phase, a unique and fresh secret parameter is computed in each new session using the random parameter and the private key . Due to the difficulties of ECDHP, cannot derive from and , and thus, the protection of fresh secret parameter does not allow to gain E and from . Therefore, cannot successfully derive m from M by computing , and the confidentiality of the sensed data m is guaranteed in the proposed scheme.
5.4. Resistance to Sensed Data Forgery Attacks
In the access control and encryption phase of the proposed scheme, the sensor node S first authenticates the user by verifying whether . Due to the protection of using timestamp and the secret parameters a and , no one can forge a valid message to pass S’s verification. In addition, we assume that the attacker intercepts the response message M and tries to generate a legitimate message with fake sensed data . However, since does not know the secret parameters E and , it cannot generate the legitimate message . Thus, the proposed scheme could withstand the sensed data forgery attacks.
5.5. Resistance to Stolen Smart Card Attacks
Suppose that the smart card of is lost or stolen. The attacker could get the stored parameters and try to impersonate to successfully login to the trusted authority . can first guess a candidate identity and password and compute and . The way for to learn is to find out the correct pair such that . In the proposed scheme, we assume the probability of guessing composed of exact l characters and composed of exact m characters is approximately . This probability is negligible, and has no feasible way to derive and of the user in polynomial time.
5.6. Resistance to Off-Line Password Guessing Attacks
In the proposed scheme, we assume that an attacker could eavesdrop all of the transmission messages , , and between , and S. However, neither the smart card, nor the transmission messages include ’s password . Therefore, the proposed scheme could withstand the off-line password guessing attack.
5.7. Provision of the Efficient Login Phase
In order to illustrate the verification mechanism during the login phase, three cases are taken into consideration. Case 1 assumed inputs a correct identity and incorrect password . Case 2 assumed inputs an incorrect identity and correct password . Case 3 assumed inputs incorrect identity and incorrect password .
-
Case 1:
After the user inputs , the smart card computes , and and verifies . In fact, the verification cannot pass as , and the smart card immediately terminates the session.
-
Case 2:
After the user inputs , the smart card computes , and and verifies . Furthermore, the verification cannot pass as , and the smart card immediately terminates the session.
-
Case 3:
After the user inputs , the smart card computes , and and verifies . Similarly, the verification cannot pass as , and the smart card immediately terminates the session.
5.8. Provision of User Anonymity
Based on the design of our proposed scheme, the excellent property of user anonymity can be guaranteed at every phase. We cleverly mask the real identity of via a public channel, and no attacker can compromise ’s real identity by launching security attacks. First, in the login phase, ’s real identity is included in . Thus, cannot reveal without . Additionally, in the verification and access control and encryption phases, the temporary identity is generated and utilized to replace ’s identity transmitted among the user and the sensor nodes. That is to say, all of the identities are transmitted in cipher format instead of plaintext, and these temporary identities will be randomized at each new session. As a result, our proposed scheme can provide the property of user anonymity.
5.9. Provision of Mutual Authentication
In the login phase of the proposed scheme, only the legitimate user can know the secret parameter to generate a legal . Therefore, in Step 3 of the verification phase, can authenticate by checking if the decrypted is equal to the computed . Moreover, in Step 5 of the verification phase, only the legal can own the secret key to compute the common secret parameter . As a result, can authenticate by decrypting and checking if the revealed is involved in .
On the other hand, in the access control and encryption phase, only the legal user can obtain the secret parameter to generate a legal C. Thus, in Step 4 of the access control and encryption phase, S can authenticate by checking if the received C is equal to the computed . Additionally, in Step 5 of the access control and encryption phase, only the participated S can calculate the common session key to encrypt the sensed data by computing . Finally, can also authenticate S by establishing the common session key and checking if the sensed data m are involved in M by decrypting .
5.10. Provision of Session Key Security
Since the common session key is only shared and established among the user and the sensor nodes S, in order to establish a secure and authenticated channel for late successive transmission, the session key not only ensures confidentiality, but also achieves authenticity of participants and messages. Based on the design of session key , E is used for verifying the integrity of the transmitted messages, whereas is used for preventing possible replay and misuse service attacks. As a result, the session key security and data confidentiality can be provided in the proposed authentication scheme.
6. Security Proof of the Proposed Scheme
Here, we follow similar techniques to demonstrate the security of our scheme in the random oracle model [27,28,29,30] and under the elliptic curve Diffie–Hellman problem (ECDHP).
6.1. Adversarial Model
We assume an adversary is a probabilistic polynomial time algorithm and allowed to issue the following queries to some oracles. Note that an oracle has multiple instances , where denotes participants and . Here, we set and may use to simulate the proposed scheme via issuing queries.
query: Upon receiving this query with message m, instance follows the proposed scheme and then returns the result to .
query: Upon receiving this query with message m, instance returns a random value to .
query: may query user U’s password. Upon receiving this query, instance returns a password to . Note that this query models the forward secrecy of session key.
query: may query the previous established session keys. Upon receiving this query, instance returns a previous session key to , if it has accepted. Otherwise, returns a random string to . Note that this query models the knowing the session key attack of session key.
query: may only issue this query once. Upon receiving this query, instance flips an unbiased coin b. If , it returns a session key. Otherwise, it returns a random string. Note that this query models the semantic security of session key.
6.2. Mutual Authentication between and
Theorem 1.
In the random oracle model, assume that there exists an adversary with a non-negligible advantage that can impersonate to communicate with . Then, there is a challenger , which can solve the elliptic curve Diffie–Hellman problem (ECDHP) with advantage , where denotes the maximum number of send queries issued by , denotes the maximum number of hash queries issued by and k denotes the length of the hash value.
Proof.
Note that we say that successfully impersonates to communicate with . This means that accepts , but it has not been produced by . In this case, it could be that guessed . Then, this leads to:
(1) Given that and to for a, are unknown, then, can compute . Thus, given , can use as a subroutine to compute . In other words, can solve ECDLP with the advantage . ☐
Theorem 2.
In the random oracle model, assume that there exists an adversary with a non-negligible advantage that can impersonate to communicate with . Then, there is a challenger , which can solve the elliptic curve Diffie–Hellman problem (ECDHP) with advantage , where denotes the maximum number of send query issued by , denotes the maximum number of hash query issued by and k denotes the length of the hash value.
Proof.
Without of loss generality, we assume that the event that violates -to- authentication denoted by does not occur. Similarly, we use the symbol to define the event that violates -to- authentication. We say that successfully impersonates to communicate with . This means that at some point, accepts after sending . However, has not been produced by . In this case, it could be the following three cases:
guessed . The probability of this case is .
and were obtained in other session. The probability of this case is less than .
had issued the hash query for .
Thus, we have:
(2) Given and to for a, are unknown, then, can compute . Thus, given , can use as a subroutine to compute . In other words, can solve ECDLP with the advantage .
6.3. S Authenticates and Key Agreement
Theorem 3.
Under the elliptic curve computational Diffie–Hellman problem (ECDHP), no adversary can impersonate user to communicate with sensor node S after is authenticated as a legal user by .
Proof.
No one can forge except legal user because a is a secret value stored in ’s smart card, and E is obtained from the procedures of authenticating . By Theorem 2, we have proved that no one can impersonate to communicate with under the ECDHP. Even if the ’s smart card is broken, the adversary is still unable to forge E. ☐
Theorem 4.
Under the elliptic curve computational Diffie–Hellman problem (ECDHP), only user and sensor node S can establish a session key after is authenticated as a legal user by . In other words, no adversary can compute except and S.
Proof.
According to the proofs of Theorems 2 and 3, no one can compute except , an authenticated legal user. In another aspect, only S can compute because sends a and to S via a secure channel, and E is computed by . ☐
7. Performance Analyses and Comparisons
In this section, we provide a performance comparisons among our scheme and two existing ECC-based authentication schemes [5,21] for wireless healthcare sensor networks in terms of computation costs in the authentication process (which includes the login, verification, and access control and encryption phases). According to the experimental results of He [31], the execution times are given in Table 1, where the hardware platform is a Pentium IV 3-GHz processor with library MIRACL [32]. As shown in Table 1, it is clear that the elliptic curve scalar point multiplication and the bilinear pairing operation are more complicated than other operations, and the running time of the addition operation of points, the map-to-point hash function and the one-way hash function could be ignored. Therefore, we only need to count the execution time of the elliptic curve scalar point multiplication and the bilinear pairing operation.
Table 1.
Execution time (in milliseconds; ms) of various cryptographic operations.
| Notations | Descriptions |
|---|---|
| The time of executing an elliptic curve scalar point multiplication, 1 1.17 ms | |
| The time of executing a bilinear pairing operation, 1 3.16 ms | |
| The time of executing an addition operation of points, 1 ms, which is negligible | |
| The time of executing a map-to-point hash function, 1 ms, which is negligible | |
| The time of executing a one-way hash function, 1 ms, which is negligible |
In Table 2, we summarize the efficiency comparisons among our proposed scheme and other previous WSN-based authentication schemes in terms of computational complexity and the execution time, where the total execution times are measured using Table 1. From Table 2, we can see that the computation cost of our scheme is lower than that of Yeh et al.’s and Liu–Chung’s schemes on both the user, the trusted authority and the sensor node side. Therefore, our proposed scheme is the most efficient compared to the other two related schemes in terms of overall computation costs, and it can be claimed that the execution time of the proposed scheme is suitable for different real-life applications, including medical care systems.
Table 2.
Performance comparisons among the proposed scheme and other related schemes.
Lastly, the security criteria and functional properties of three ECC-based authentication schemes are summarized in Table 3. It is visible from Table 3 that Yeh et al.’s scheme [5] is vulnerable to password disclosure attack in the registration phase and also does not provide the user anonymity property, where Liu–Chung’s scheme [21] does not support this property. The proposed scheme can prevent all of the security weaknesses of the former scheme and provide mutual authentication and user anonymity to protect data integrity and user privacy. From Table 2 and Table 3, the proposed scheme not only keeps lower computational cost, but also possesses more security requirements along with strong security protection on the relevant security attacks for IoT-based medical care systems.
Table 3.
Functionality comparisons among the proposed scheme and other related schemes.
| Yeh et al. [5] (2011) | Liu–Chung [21] (2016) | The Proposed Scheme | |
|---|---|---|---|
| F1 | √ | ||
| F2 | √ | √ | |
| F3 | √ | √ | √ |
| F4 | √ | √ | |
| F5 | √ | ||
| F6 | √ | √ | |
| F7 | − | √ | |
| F8 | − | √ | |
| F9 | √ | √ | |
| F10 | √ | √ |
F1: Provision of user anonymity; F2: provision of efficient login phase; F3: provision of mutual authentication; F4: provision of session key security; F5: prevention of password disclosure attack; F6: prevention of replay attack; F7: prevention of sensed data disclosure attack; F8: prevention of sensed data forgery attack; F9: prevention of stolen smart card attack; F10: prevention of off-line password guessing attack; √: yes; : no; −: not mentioned.
8. Conclusions
In this paper, we first give a brief review of Liu–Chung’s authentication scheme combined with its basic security analysis and find that their scheme is vulnerable to password disclosure, off-line password guessing, sensed data disclosure, sensed data forgery, replay attacks and the stolen smart card problem. Furthermore, their scheme cannot achieve user anonymity and session key security, and it has unnecessary redundancy in protocol design. In order to repair their security flaws and improve the system performance, an improved efficient scheme is proposed. The security analysis indicates that the proposed authentication scheme is able to withstand those attacks mentioned and satisfies all desirable security attributes, such as user anonymity, mutual authentication, session key security and an efficient verification mechanism during the login phase. Comparing the efficiency with other ECC-based authentication schemes, the proposed scheme is comparable in terms of the computational overheads and practical as the secure authentication mechanism for the IoT-based medical care system.
Acknowledgments
The authors would like to thank the anonymous reviewers and the Editor for their constructive and generous feedback on this paper. In addition, this research was partially supported and funded by the Ministry of Science and Technology, Taiwan, R.O.C., under Contract No. MOST 105-2221-E-165-005.
Author Contributions
Chun-Ta Li proposed the ideas and wrote the paper; Tsu-Yang Wu and Chin-Ling Chen are corresponding authors who contributed to prove, analyze the data and supervise the paper; Cheng-Chi Lee and Chien-Ming Chen also supported the writing, and supervised parts of the scheme.
Conflicts of Interest
The authors declare no conflict of interest.
References
- 1.Chiou S.Y., Ying Z., Liu J. Improvement of a privacy authentication scheme Based on cloud for medical environment. J. Med. Syst. 2016;40:101. doi: 10.1007/s10916-016-0453-1. [DOI] [PubMed] [Google Scholar]
- 2.He D., Kumar N., Chen J. Robust anonymous authentication protocol for healthcare applications using wireless medical sensor networks. Multimed. Syst. 2015;21:49–60. doi: 10.1007/s00530-013-0346-9. [DOI] [Google Scholar]
- 3.Li C.T., Weng C.Y., Lee C.C. An advanced temporal credential-based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors. 2013;13:9589–9603. doi: 10.3390/s130809589. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Li C.T., Lee C.C., Weng C.Y. A secure cloud-assisted wireless body area network in mobile emergency medical care system. J. Med. Syst. 2016;40:117. doi: 10.1007/s10916-016-0474-9. [DOI] [PubMed] [Google Scholar]
- 5.Yeh H.L., Chen T.H., Liu P.C., Kim T.H., Wei H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors. 2011;11:4767–4779. doi: 10.3390/s110504767. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6.Zhou J., Cao Z., Dong X., Xiong N., Vasilakos A.V. 4S: A secure and privacy-preserving key management scheme for cloud-assisted wireless body area network in m-healthcare social networks. Inf. Sci. 2015;314:255–276. doi: 10.1016/j.ins.2014.09.003. [DOI] [Google Scholar]
- 7.Choi J., In Y., Park C., Seok S., Seo H., Kim H. Secure IoT framework and 2D architecture for end-to-end security. J. Supercomput. 2016 doi: 10.1007/s11227-016-1684-0. [DOI] [Google Scholar]
- 8.Kumari S., Khan M.K., Atiquzzaman M. User authentication schemes for wireless sensor networks: A review. Ad Hoc Netw. 2015;27:159–194. doi: 10.1016/j.adhoc.2014.11.018. [DOI] [Google Scholar]
- 9.Li C.T. A secure chaotic maps based privacy-protection scheme for multi-server environments. Secur. Commun. Netw. 2016;9:2276–2290. doi: 10.1002/sec.1487. [DOI] [Google Scholar]
- 10.Maitra T., Amin R., Giri D., Srivastava P.D. An efficient and robust user authentication scheme for hierarchical wireless sensor networks without tamper-proof smart card. Int. J. Netw. Secur. 2016;18:553–564. [Google Scholar]
- 11.Messai M.L., Seba H., Aliouat M. A lightweight key management scheme for wireless sensor networks. J. Supercomput. 2015;71:4400–4422. doi: 10.1007/s11227-015-1534-5. [DOI] [Google Scholar]
- 12.Rawat P., Singh K.D., Chaouchi H., Bonnin J.M. Wireless sensor networks: A survey on recent developments and potential synergies. J. Supercomput. 2014;68:1–48. doi: 10.1007/s11227-013-1021-9. [DOI] [Google Scholar]
- 13.Wong K., Zheng Y., Cao J., Wang S. A dynamic user authentication scheme for wireless sensor networks; Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC); Taichung, Taiwan. 5–7 June 2006; pp. 244–251. [Google Scholar]
- 14.Tseng H.R., Jan R.H., Yang W. An improved dynamic user authentication scheme for wireless sensor networks; Proceedings of the IEEE Globecom; Washington, DC, USA. 26–30 November 2007; pp. 986–990. [Google Scholar]
- 15.Lee T.H. Simple dynamic user authentication protocols for wireless sensor networks; Proceedings of the 2nd International Conference on Sensor Technologies and Applications; Cap Esterel, France. 25–31 August 2008; pp. 657–660. [Google Scholar]
- 16.Das M.L. Two-factor user authentication in wireless sensor Networks. IEEE Trans. Wirel. Commun. 2009;8:1086–1090. doi: 10.1109/TWC.2008.080128. [DOI] [Google Scholar]
- 17.Huang H.F., Chang Y.F., Liu C.H. Enhancement of two-factor user authentication in wireless sensor networks; Proceedings of the 2010 6th International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP); Darmstadt, Germany. 15–17 October 2010; pp. 27–30. [Google Scholar]
- 18.Li C.T., Lee C.C., Wang L.J., Liu C.J. A secure billing service with two-factor user authentication in wireless sensor networks. Int. J. Innov. Comput. Inf. Control. 2011;7:4821–4831. [Google Scholar]
- 19.Yoo S.G., Park K.Y., Kim J. A security-performance-balanced user authentication scheme for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2012;2012:382810. doi: 10.1155/2012/382810. [DOI] [Google Scholar]
- 20.Xue K., Ma C., Hong P., Ding R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013;36:316–323. doi: 10.1016/j.jnca.2012.05.010. [DOI] [Google Scholar]
- 21.Liu C.H., Chung Y.F. Secure user authentication scheme for wireless healthcare sensor networks. Comput. Electr. Eng. 2016;59:250–261. doi: 10.1016/j.compeleceng.2016.01.002. [DOI] [Google Scholar]
- 22.Joux A. The weil and tate pairings as building blocks for public key cryptosystems. Lect. Notes Comput. Sci. 2002;2369:20–32. [Google Scholar]
- 23.He D., Zhao W., Wu S. Security analysis of a dynamic ID-based authentication scheme for multi-server environment using smart cards. Int. J. Netw. Secur. 2013;15:350–356. [Google Scholar]
- 24.He D., Zeadally S., Kumar N., Lee J.H. Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. 2016 doi: 10.1109/JSYST.2016.2544805. [DOI] [Google Scholar]
- 25.Wang Y., Zhong H., Xu Y., Cui J. ECPB: Efficient conditional privacy-preserving authentication scheme supporting batch verification for VANETs. Int. J. Netw. Secur. 2016;18:374–382. [Google Scholar]
- 26.Messerges T.S., Dabbish E.A., Sloan R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002;51:541–552. doi: 10.1109/TC.2002.1004593. [DOI] [Google Scholar]
- 27.Bellare M., Rogaway P. Random oracles are practical: A paradigm designing efficient protocols; Proceedings of the 1st ACM Conference on Computer and Communications Security; Fairfax, VA, USA. 3–5 November 1993; pp. 62–73. [Google Scholar]
- 28.Canetti R., Goldreich O., Halevi S. The random oracle metholodology, revisited. J. ACM. 2004;51:557–594. doi: 10.1145/1008731.1008734. [DOI] [Google Scholar]
- 29.Chen C.M., Li C.T., Liu S., Wu T.Y., Pan J.S. A provable secure private data delegation scheme for mountaineering events in emergency system. IEEE Access. 2017;5:3410–3422. doi: 10.1109/ACCESS.2017.2675163. [DOI] [Google Scholar]
- 30.Wu T.Y., Tseng Y.M. An efficient user authentication and key exchange protocol for mobile client-server environments. Comput. Netw. 2010;54:1520–1530. doi: 10.1016/j.comnet.2009.12.008. [DOI] [Google Scholar]
- 31.He D. An efficient remote user authentication and key agreement protocol for mobile client-Vserver environment from pairings. Ad Hoc Netw. 2012;10:1009–1016. doi: 10.1016/j.adhoc.2012.01.002. [DOI] [Google Scholar]
- 32.Shamus Software. [(accessed on 22 June 2017)]; Available online: https://github.com/miracl/MIRACL.