Fig. 6.
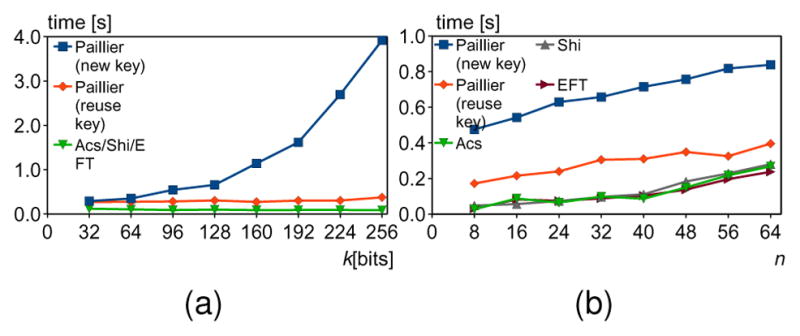
The average runtimes of a protocol for different encryption key sizes k (n = 32) and different number of participants n (k = 128).

The average runtimes of a protocol for different encryption key sizes k (n = 32) and different number of participants n (k = 128).