Fig. 1.
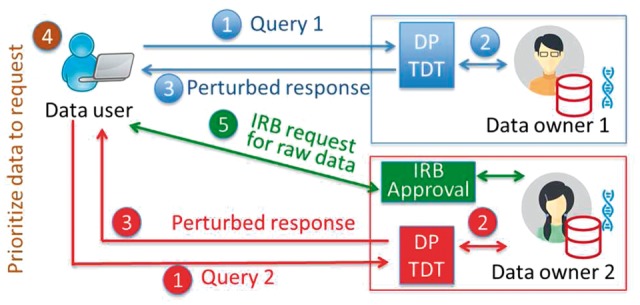
A workflow for privacy-protecting data access from DP TDT. (1) A data user sends queries to different datasets. (2) Data owners compute the true results based on the query. (3) Instead of returning the true results, data owners return perturbed, DP TDT results. (4) The data user compares the utility among different datasets to prioritize requests for data. (5) The data user files a data access application to obtain participant-level data
