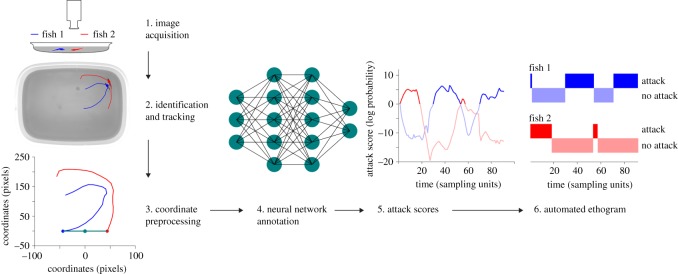
Figure 1.
Computer vision pipeline. 1: Raw video. 2: Unmarked animals after identification with idtracker.ai and a short span of the trajectory of each animal overlaid. 3: Preprocessing of a local portion of trajectory for neural network analysis. 4: Schematic of the neural network classifier which was trained to mimic human annotations. 5: Time series of attack scores for two animals as produced by the neural network classifier. High attack score values indicate a high internal confidence of the network that an attack is taking place. 6: Automatic ethogram calculated by thresholding the attack score.