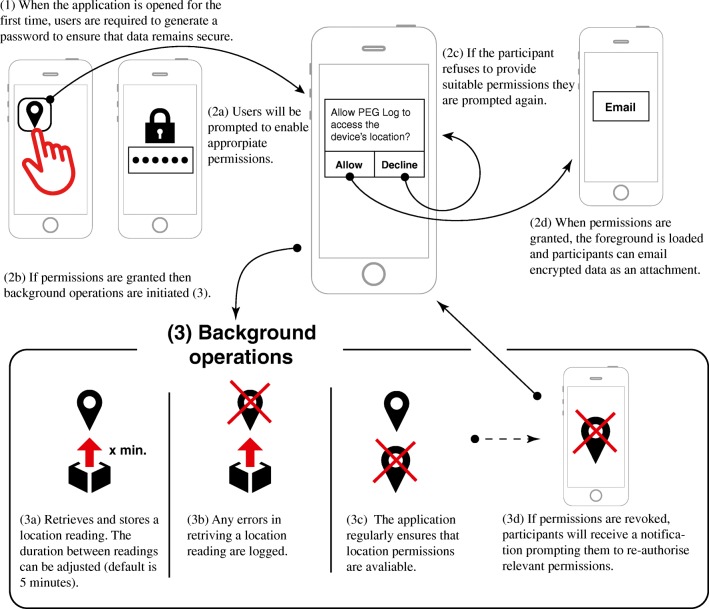
Fig. 1.
Infographic demonstrating the foreground (1, 2a–2d) and background (3a–3d) operations of the PEG LOG application. The only aspect of the application accessible by participants is the main activity page, which requests the relevant location permissions (2a) and allows participants to read the documentation, change their password, view their location data, and email files (2d).