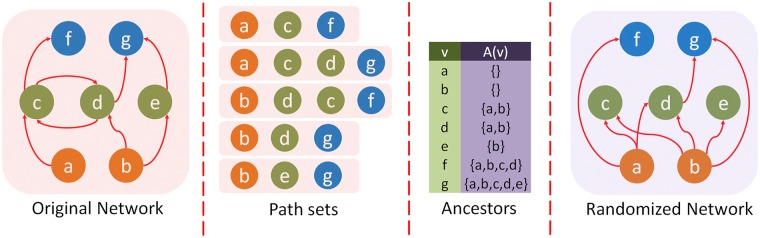
Fig 6. For the network and source-target paths given in the left two figures, we first compute the ancestors A(v) of each node v (shown in the third figure from left).
In the randomized network (shown at the right), we preserve the in-degree of each node v and randomly select incoming connections from the set A(v).