Fig. 3. Leakage detection and mitigation during repeated ZZ checks using HMMs.
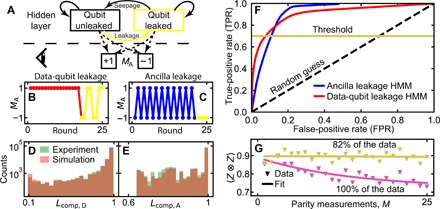
(A) Simplified HMM. In each round, a hidden state (leaked or unleaked) (top) is updated probabilistically (full arrows) and produces an observable MA (bottom) with state-dependent probabilities (dashed arrows). After training, the HMM can be used to assess the likelihood of states given a produced string of MA. (B) Example for a data-qubit leakage event (yellow markers), showing the characteristic pattern of repeated errors. (C) Example for QA leakage signaled by constant MA = −1. (D) Histograms of with M = 25, both obtained experimentally, and simulated by the HMM optimized to detect data-qubit leakage, binned according to the likelihood (Eqs. 9 and 10) of the data qubits being unleaked (as assessed from the trained HMM). HMM training suggests 5.6% total data-qubit leakage at M = 25 [calculated from Table 1 as the steady-state fraction pleak/(pleak + pseep)]. (E) Corresponding histograms using the HMM optimized for QA leakage. This HMM suggests 3.8% total QA leakage. (F) Receiver operating characteristics (ROCs) for the trained HMMs. (G) 〈Z ⊗ Z〉 after M ZZ checks and correction based on the final outcomes, without (same data as in Fig. 2D) and with leakage mitigation by postselection (TPR = 0.7).
