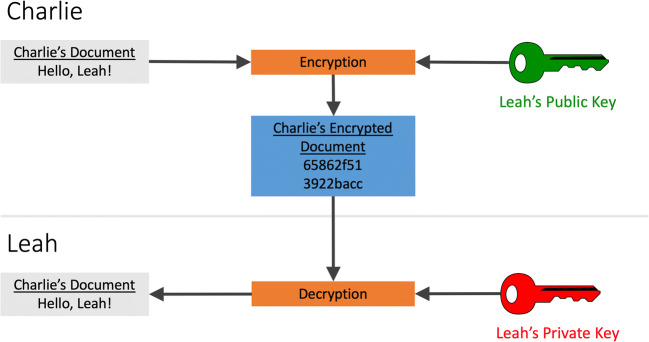
Fig. 3.
Public key cryptography. Blockchain relies on public key cryptography which uses key pairs (public keys are publicly available, and private keys are kept secret like passwords). Using Leah’s public key, Charlie can encrypt a message which can only be decrypted by Leah with the use of Leah’s private key. The data are encrypted as the message is unreadable without the private key