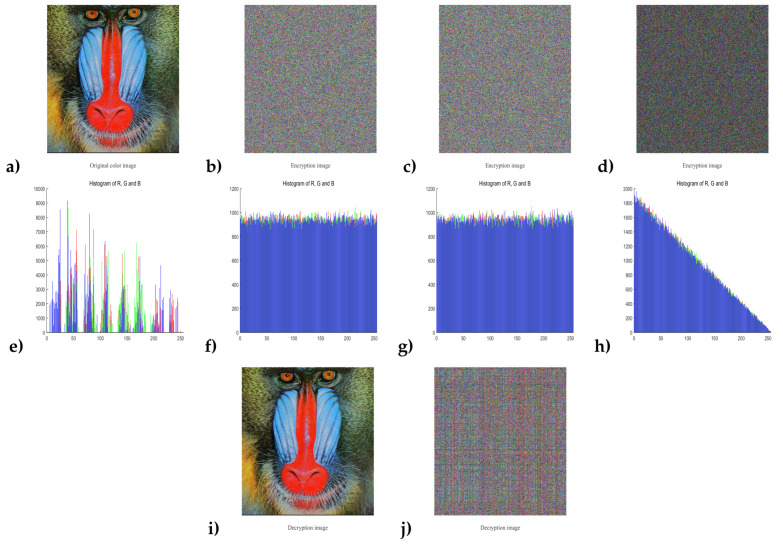
Figure 8.
The key sensitivity test: (a,e): the original image and corresponding histogram; (b,f): the encrypted image with the security key set and corresponding histogram; (c,g): the encrypted image with the security key set and corresponding histogram; (d,h): the pixel-by-pixel difference and corresponding histogram; (i): the decrypted image from using the correct security key set ; (j): the decrypted image from using an incorrect security key set .