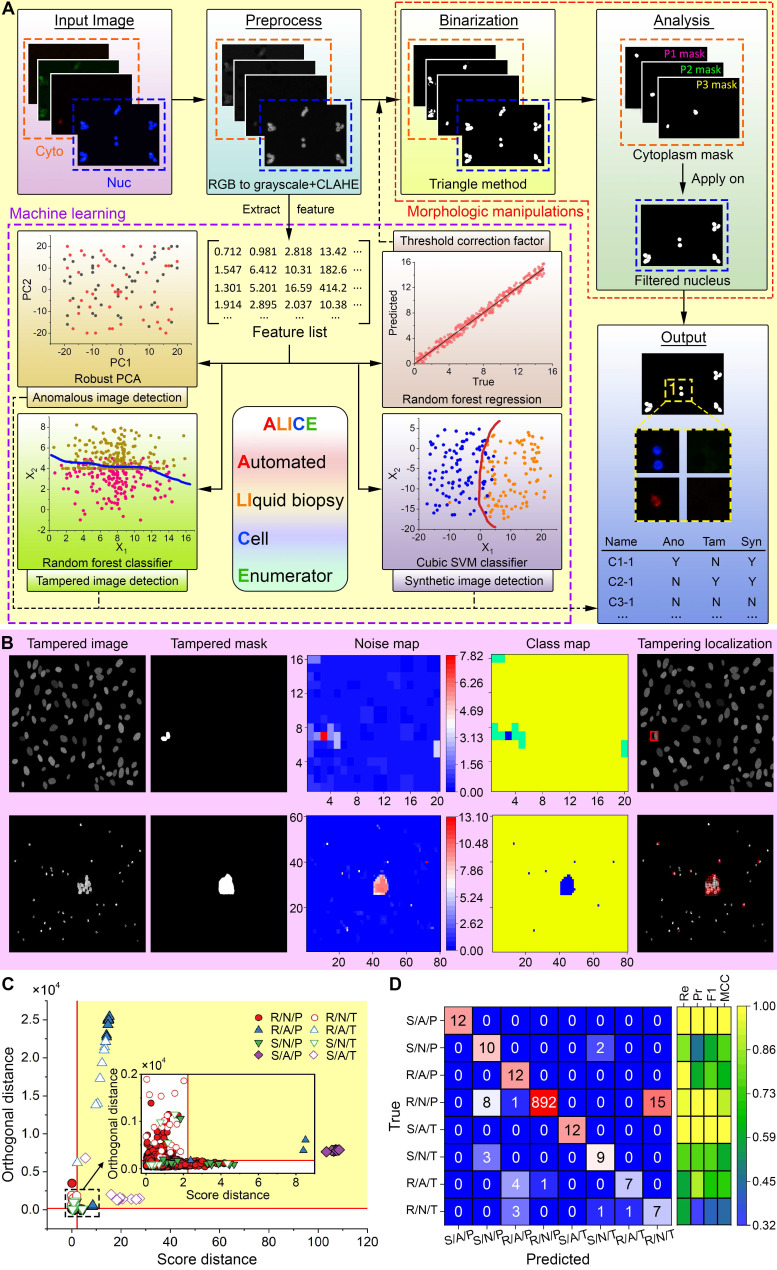
Figure 2.
Overview of ALICE with enhanced connectivity and cybersecurity. (A) ALICE contains a hybrid AI engine that combines traditional rule-based morphological manipulations with modern statistical machine learning for an automated and accurate identification, localization and enumeration of cell phenotypes. The built-in cybersecurity detects enigmatic and fake input data. (B) Localization of the tampered region via a multi-class hierarchical clustering based on PCA-derived noise levels of the input image. Different colors in the class map represent different predicted classes. The class with the least number of pixels is considered a tampered region and visualized by a bounded red box. (C) From an image set of 1000 images, individually detected image types are marked using different symbols. The yellow shaded area represents the region of anomaly determined by the robust PCA. Inset shows a magnified plot of the region around the origin. Anomalous, tampered and synthetic images are detected by the robust PCA algorithm, random forest classifier and cubic SVM classifier, respectively. Note: 'R' denotes real, 'S' denotes synthetic, 'N' denotes normal, 'P' denotes pristine, 'A' denotes anomalous, 'T' denotes tampered. (D) The corresponding confusion matrix and performance indices for the detection results in (C). 'Re' denotes the recall, 'Pr' denotes the precision, 'F1' denotes the F1 score and 'MCC' denotes the Matthews correlation coefficient.