Abstract
Models of sequence evolution typically assume that all sequences are possible. However, restriction enzymes that cut DNA at specific recognition sites provide an example where carrying a recognition site can be lethal. Motivated by this observation, we studied the set of strings over a finite alphabet with taboos, that is, with prohibited substrings. The taboo-set is referred to as and any allowed string as a taboo-free string. We consider the so-called Hamming graph , whose vertices are taboo-free strings of length n and whose edges connect two taboo-free strings if their Hamming distance equals one. Any (random) walk on this graph describes the evolution of a DNA sequence that avoids taboos. We describe the construction of the vertex set of . Then we state conditions under which and its suffix subgraphs are connected. Moreover, we provide an algorithm that determines if all these graphs are connected for an arbitrary . As an application of the algorithm, we show that about of bacteria listed in REBASE have a taboo-set that induces connected taboo-free Hamming graphs, because they have less than four type II restriction enzymes. On the other hand, four properly chosen taboos are enough to disconnect one suffix subgraph, and consequently connectivity of taboo-free Hamming graphs could change depending on the composition of restriction sites.
Keywords: Bacteriophage DNA evolution, Endonuclease-dependent evolution, Restriction-enzyme dependent evolution, Restriction–modification system, Hamming graph with taboos, Connectivity of Hamming graphs
Introduction
In bacteria, restriction enzymes cleave foreign DNA to stop its propagation. To do so, a double-stranded cut is induced by a so-called recognition site, a DNA sequence of length 4–8 base pairs (Alberts et al. 2004). As part of their restriction–modification (R–M) system, bacteria can escape the lethal effect of their own restriction enzymes by modifying recognition sites in their own DNA (Kommireddy and Nagaraja 2013). Nevertheless, Gelfand and Koonin (1997) and Rocha et al. (2001) found a significant avoidance of recognition sites in bacterial DNA, and Rusinov et al. (2015) showed that this avoidance was characteristic of type II R–M systems. Also in bacteriophages, the avoidance of the recognition sites is evolutionary advantageous (Rocha et al. 2001), mainly for non-temperate bacteriophages affected by orthodox type II R–M systems (Rusinov et al. 2018a). Therefore in those instances the recognition site is, as we call it, a taboo for host and foreign DNA.
Although avoidance of recognition sites is well studied, e.g. by Rusinov et al. (2018b), taboo free DNA evolution has not yet been modelled. To initiate models of sequence evolution with taboos, we studied the Hamming graph , whose vertices are strings of length n over a finite alphabet not containing any taboos of the set as subsequence. Two vertices of the Hamming graph are adjacent if the corresponding taboo-free strings have Hamming distance equal to one. In biological terms, the sequences differ by a single substitution.
We note that, for a binary alphabet and taboo-set , the corresponding Hamming graphs are known as Fibonacci cubes. Some properties of the Fibonacci cubes like the Wiener Index or the degree distribution were surveyed by Klavžar (2013). Further results have been obtained for taboo-sets forbidding arbitrary numbers of consecutive “1”s, , by Hsu and Chung (1993), or when for an arbitrary binary string s by Ilić et al. (2012). Recently, the equivalent problem of lattice paths that avoid some patterns has been described using automata and generating functions by Asinowski et al. (2018, (2020).
We are not so much interested in enumerative properties of Hamming graphs. We want to define conditions under which the Hamming graphs stay connected for arbitrary finite alphabets and arbitrary finite taboo-sets. From an evolutionary point of view, connectivity guarantees that any taboo-free sequence can be generated by point mutations from any initial taboo-free sequence without containing a taboo-string during evolution. To include further biological realism, we will also study the connectivity of subgraphs of the Hamming graph, where s is a taboo-free suffix. Suffix s can be viewed as a conserved DNA fragment, that is, a sequence that remained invariable during evolution (Shoemaker and Fitch 1989; Fitch and Margoliash 1967).
The inclusion of Hamming graphs with a constant suffix provides more general results, because , where e is the empty string. Given a taboo-set , if for every taboo-free string s and integer n the Hamming graph is connected, then evolution can explore the space of taboo-free sequences by simple point mutation, no matter which DNA suffix fragments remain invariable, as long as the taboo-set does not change in the course of evolution.
Motivating examples and non-technical presentation of key results
Here, we give a non-technical description of the essential results to determine connectivity. The subsequent sections provide a more technical and precise description of the central results.
Consider an alphabet , for example . In a Hamming graph of length n, all possible words of length n are vertices, and two of these vertices are joined by an edge if they differ in exactly one position. A taboo-set is a set of forbidden subwords, such as . Then, to construct a taboo-free Hamming graph , we simply have to erase all words of the Hamming graph of length n containing those taboos. Figure 1 provides an example where is disconnected for .
Fig. 1.
Graph for for binary alphabet and . Set is constructed by adding every allowed letter at the beginning of each string in
Given some alphabet and some taboo-set, deciding whether graph is connected is not a trivial task. To see this, consider the four-nucleotide alphabet , which is our main object of interest. Figure 2 shows the connected graph for taboo-set . The word TTT is a cut vertex, meaning that taboo-set yields the disconnected graph
Fig. 2.
Graph , where and Vertex TTT is a cut vertex, because if we remove TTT and its incident edges (dashed lines, coloured red), then the resulting graph is disconnected. Consequently, graph induced by taboo-set is disconnected. Red, blue and yellow edges connect vertices with a different distribution of letter T (colour figure online)
Since the addition or deletion of one single taboo can have such an impact on connectivity, we need a tool to determine the structure of the taboo-free Hamming graphs. This tool is described in full generality at the end of Sect. 8. In the particular case when , our results can be simplified as follows.
-
If the number of taboos is smaller than the size of the alphabet, that is if , then all graphs are connected (Corollary 25.b). For example, given , all taboo-free Hamming graphs are connected.
Similarly, if the size of the set of all starting letters of taboos is smaller than the size of the alphabet, then all taboo-free Hamming graphs are connected (Corollary 25.a). This applies for taboo-set , because the set of initial letters is and .
-
Proposition 24 describes a slightly more complex sufficient condition to determine connectivity. Given , delete the first letter of each taboo to construct the set . For example, if , then .
In set , consider every pair of strings with Hamming distances 1 or 0. For example, the pair (AA, AA) has distance 0; the pair (AA, CA) has distance 1; and the pair (AA, TT) has distance 2. If every pair with Hamming distance 1 or 0 can be taboo-free extended to the left by the same letter, then all graphs are connected.
For example, the pair (AA, AA) can be extended by C, because CAA is taboo-free, and the pair (AA, CA) can be extended by T, because TAA and TCA are taboo-free. After checking all possible pairs with Hamming distance 0 or 1, we see that all such pairs in are extendable to the left, and thus taboo-set generates connected taboo-free Hamming graphs.
-
If Proposition 24 cannot be applied, then we apply the characterization of Theorem 22. Assume for example that . Since the pair with Hamming distance one is not taboo-free extendable to the left by any letter, we proceed as follows. First we construct , the set of all proper suffixes of . In our example, , where e is the string with no letters. Now we consider, for every suffix the graph , where |r| is the length of r and M is the length of the longest taboo(s) in . If all graphs are connected, then every graph is connected. In our example, graphs , , and are connected, implying that all taboo-free Hamming graphs are connected.
When graph is disconnected for some , then suffix r induces disconnected taboo-free Hamming graphs of the form for . Therefore evolution cannot explore the whole space of taboo-free sequences. This is the case for taboo-set of Fig. 2, where yields the disconnected graph .
Outline
We will characterize taboo-sets such that every Hamming graph of the form is connected. To this end, we describe in Sect. 5 basic properties of taboo-sets. In Sect. 6, we introduce a very general type of taboo-sets, called left proper (Definition 4), which are our main object of study. In Proposition 11.b we show that, to construct graph , we only need the longest prefix of s which is a suffix of a taboo, which we call . In Sect. 7 we state the graph isomorphism (Theorem 16). In Sect. 8 we explain how the edges of a quotient graph are related to the structure of graph (Proposition 17).
Combining all these results, in Sect. 8 we characterize the connectivity of Hamming graphs . We prove by induction that the connectivity of a small number of quotient graphs implies the connectivity of all Hamming graphs with long suffixes (Proposition 20). This result can be used to prove connectivity of Hamming graphs with short suffixes (Proposition 21). These two results yield the characterization of the connectivity of every suffix Hamming graph in Theorem 22. Section 9 provides examples of bacterial taboo-sets and their connectivity.
Basic notations
We will introduce some standard notations concerning strings as well as some relevant terms from graph theory.
Strings
We will use the term string to refer to a sequence of symbols over an arbitrary finite alphabet , where , while (DNA) sequence is reserved for biological contexts, where the alphabet consists of the four nucleotides .
We denote the set of strings of length n over the alphabet by . The length of a string s is denoted by |s|. The empty string will be denoted by e, and satisfies and .
Given a string , the expression
denotes the substring of s starting at the ith position and ending at the jth position, and e when this substring is not well-defined (for example if ). In particular s[1, j] is a prefix of s that ends at position j and s[i, n] is a suffix of s that starts at position i. A substring, prefix or suffix is called proper if it is not the entire string s. For a set of strings S, we define the substrings from the i th to the j th position of S as
We also need the set of proper suffixes of S, defined as
where refers to all integers i within the interval [2, |s|]. It should not be confused with substring s[2, |s|] of s.
Example 1
If then
If string is substring of string , we write , while denotes that is not a substring of . By convention, for any string s. For strings and , we define as the concatenation of and . Note that for any s. For a string s and a set of strings , the concatenation of s with all elements in S is denoted by . If and are disjoint sets, then the disjoint union of and will be denoted by .
Finally, given two strings of equal length, denotes their Hamming distance, that is, the number of positions at which the corresponding symbols differ.
Graph theory
We will use common graph theory terminology following Wilson (1986). Let denote a simple, undirected graph with vertex set V and edge set E. We say that graph is subgraph of if and , and we denote this as .
Given a graph and a subset , then the subgraph induced by in , , has vertex set and, for any , iff .
Two graphs and are isomorphic, denoted by , if there exists a bijection such that, for every , iff . That is, and are isomorphic if there exists an edge-preserving bijection between their vertex sets.
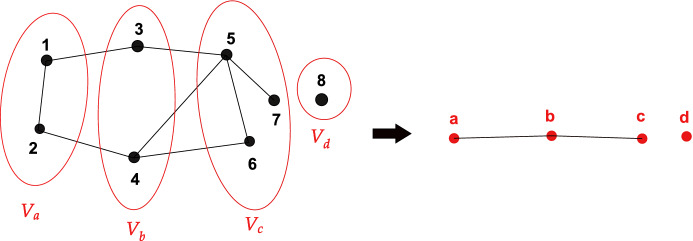
We will also need the quotient graph, as defined by Sanders and Schulz (2013), to study the connectivity of Hamming graphs. To define it, consider a graph and a partition of its vertex set V, namely for some index set J. The quotient graph of , denoted as , is the graph whose vertices are J and such that iff an edge connects a vertex in with a vertex in . Figure 3 gives an example of a quotient graph.
Fig. 3.
Example of a quotient graph. For on the left hand side, with and partition , we obtain the quotient graph on the right hand side
Our strategy to prove connectivity of taboo-free Hamming graphs will use the following propositions, whose proof is simple enough to be omitted.
Proposition 1
Consider graph and partition .
If every induced subgraph for is connected and the quotient graph is connected, then is connected.
Proposition 2
For graph , the following statements are equivalent:
is connected.
For every partition of V, the quotient graph is connected.
Properties of taboo-sets
We will repetadly use of the following terminology.
Definition 1
A finite set of strings such that every satisfies is called a taboo-set.
Strings in are called taboos.
The length of the longest taboo(s) in will be denoted by .
A string is taboo-free if it does not contain any taboo of as substring.
denotes the set of taboo-free strings of length n .
denotes the set of strings in with suffix s.
Similarly, denotes all strings in with prefix s.
With Definition 1 in mind, we can prove some simple properties of taboo-sets.
Proposition 3
Given taboo-sets and , it holds that:
Set is a taboo-set
For ,
If for every there exists such that , then for any , .
Proof
Every has length at least 2, and thus is a taboo-set.
All strings satisfy for all and for all this is equivalent to s satisfying for all .
Consider . Assume that ; then there exists such that . But there also exists a such that , and thus , a contradiction. Hence .
For a given n and , we can find a taboo-set such that In this sense, taboo-sets are not unique, as we illustrate in the following proposition.
Proposition 4
For a string t and , it holds that
Proof
: Any taboo in has as substring, and thus Proposition 3.c implies .
: Assume that there exists an with . Since and , the substring t is either preceded or followed by some symbol This contradicts
Proposition 4 implies that, for any , we can construct many taboo-sets such that as long as , where M and denote the length of the longest taboo in and respectively.
Example 2
If with , Proposition 3.a and 4 imply that satisfies for any . Repeating this process, we can construct a taboo-set such that for any string t and satisfying for any .
Example 2 and Proposition 4 motivate the following definition.
Definition 2
A taboo-set is minimal if the following conditions hold:
For every different , it holds that .
For every and , set is not a subset of
Condition (a) is easy to justify: If string AA is a taboo, it is redundant that AAA be a taboo. Condition (b) avoids unnecessarily complicated taboo-sets. For example, using the four-nucleotide alphabet, taboo-set can be minimized as . In general, one can minimize a taboo-set according to Example 2.
Since we want to study taboo-free strings of arbitrary lengths, we need conditions to concatenate taboo-free strings such that the concatenated sequence is taboo-free. The following result gives such a condition.
Proposition 5
Given taboo-set , consider three strings such that and are taboo-free and . Then is taboo-free.
Proof
If and , then is taboo-free, as desired. Now assume either or , yielding . For each , the fact that implies that either or , hence each is taboo-free and the result follows.
Prefixes and suffixes of a taboo-free string
Given a taboo-free string s, the construction of set for depends on which string w can be concatenated to the left side of s, such that . This motivates the following definition.
Definition 3
Given a taboo-set , consider a taboo-free string s and . The k-prefixes of s are the elements of the set , defined as
If , then we will say that s is k-prefixable.
Similarly, the k-suffixes of s, denoted , are the strings such that , that is, . When , we say that s is k-suffixable.
Example 3
If and , then and . Hence string AA is 1-prefixable and 2-prefixable. Moreover, , hence string AA is 1-suffixable.
By construction, given , for any it holds that
| 1 |
That is, is with s concatenated. Moreover, the following proposition shows that the k-prefixes of a string s induce a disjoint partition of the set .
Proposition 6
Given a taboo-set and a taboo-free string s, consider integers and . It holds that
That is, the set can be partitioned into the disjoint sets of taboo-free strings of length n with suffix ws, where .
Proof
If s is not k-prefixable, then and , hence the equation holds. Otherwise, the inclusion is clear, while the follows from the fact that, for any string preceding the suffix s, this w must necessarily belong to .
Clearly, if a taboo-free string s is -prefixable, then it is also k-prefixable for any integer , while nothing can be said a priori about the case . Consequently, we need to find conditions under which one can concatenate at least one symbol to the left of a taboo-free string. We will first introduce such taboo-sets in Definition 4 and then characterize prefixability in Proposition 7.
Definition 4
A taboo-set is called left proper if every is 1-prefixable. Analogously, is right proper if every is 1-suffixable.
Example 4
If and , then and AC is not 1-suffixable. Thus, is not left proper.
Proposition 7
Consider a left proper taboo-set and a taboo-free string s such that one of the following conditions holds:
and s is -prefixable
Then s is k-prefixable for every .
Proof
If condition (a) applies, then the prefix is 1-prefixable, because is left proper. That is, there exists with . Proceeding analogously with (as)[1, M] , we infer that s is 2-prefixable. Continuing with this process, we deduce that s is k-prefixable for any .
If condition (b) holds, then we can take any string in and proceed as we did assuming (a).
We mainly study left proper taboo-sets due to Proposition 7, because the existence of arbitrary k-prefixes is necessary in many of our proofs. Analogous results for right proper taboo-sets are obtained by reversing the order of the symbols composing the string.
According to Proposition 7, if the length of a taboo-free string is at least M, then the taboo-free string can prefixed for arbitrary lengths. Otherwise, one needs to check the -prefixability of this string. To that end, the following result comes in handy.
Proposition 8
Consider a left proper taboo-set and a taboo-free string s.
If and , then for .
If either or , then for .
Proof
- If and , since , it holds that . This implies that for every , because otherwise
which contradicts . If , since is left proper, Proposition 7.a implies that s is k-prefixable for every . Thus, . Similarly, if , then s is -prefixable, and thus Proposition 7.b implies that s is k-prefixable for every .
Note that, since the assumptions of Proposition 8.a are the negation of the assumptions of Proposition 8.b, in Proposition 8 we have proved that for iff string s satisfies and .
To study the connectivity of Hamming graphs , we need to know whether two different strings have a k-prefix in common. Thus, we introduce the following.
Definition 5
Given a taboo-set , we say that two taboo-free strings and (maybe of different length) are left k-synchronized if . If , then we say that and are right k-synchronized.
In words, two taboo-free strings are left k-synchronized if they are k-prefixable by at least one string w. Clearly, two taboo-free strings that are left -synchronized are also left k-synchronized for any (one simply has to “cut” the k symbols on the left of ). The following proposition states when we can also guarantee k-synchronization for :
Proposition 9
Consider a left proper taboo-set and two taboo-free strings , with length greater than zero, such that and are left -synchronized. Then and are left k-synchronized for any .
Proof
If , then the assertion is true since and are -synchronized.
For , consider a string . We know that and are taboo-free strings with length at least M. Since is left proper, Proposition 7.a applied to and implies that and are -prefixable for any . Therefore w is -prefixable for any . For any , take and consider strings xws and xwr. The fact that , together with the fact that xw and the pair are taboo-free, allows applying Proposition 5, hence and are also taboo-free.
It follows that . With , the result follows for any .
The following proposition provides a Hamming-distance based criterion to quickly decide whether two taboo-free strings of length M are left k-synchronized.
Proposition 10
Consider a left proper taboo-set . If all pairs with are left 1-synchronized, then all pairs with are left k-synchronized for all .
Proof
Given any left 1-synchronized pair with , there exists an such that and are taboo-free. Since for and the Hamming distance between these two strings is at most 1, are 1-synchronized, hence there exists a symbol such that and are taboo-free, i.e. and are left 2-synchronized. Continuing with this process, it follows that and are k-synchronized.
We will now discuss conditions that allow increasing the string length of an entire set of taboo-free strings. To this end, consider two taboo-free strings and the set . It is generally not true that , because the concatenation of s to a taboo-free string from can create a taboo string around the junction of both strings. For the remainder of this section we will discuss when the equality holds.
Definition 6
For a taboo-set and a taboo-free string s, we define the length of the longest taboo suffix-prefix match as
i.e. denotes the length of the longest prefix of s being a proper suffix of a taboo.
Note that the length is well defined, because , hence Using this length , in Proposition 11 we give conditions implying that equality holds.
Proposition 11
For a taboo-set and a taboo-free string s, the following holds:
- Take such that . Then for any ,
- For any it holds that
Proof
The inclusion is clear. The inclusion follows from the fact that, if we are given such that , since , Proposition 5 yields that the concatenated string rws is taboo-free.
-
The result is obvious if or , hence assume and .
Clearly . For , consider . We need to prove that the string
is taboo-free. But otherwise, since and s are taboo-free, there would exist integers c, d such that and . Take , which yields , contradicting the maximality of . Hence rs is taboo-free, as desired. Note that the same argument applies if .
From Proposition 11.b we obtain two corollaries.
Corollary 12
Given a taboo-set and a taboo-free string s, for any it holds that
Proof
By construction, Proposition 11.b yields
Corollary 13
For a taboo-set and for any pair of taboo-free strings and , the following statements are equivalent for all :
and are left k-synchronized
and are left k-synchronized.
Proof
Strings and are left k-synchronized iff We just have to apply Corollary 12.
Thus, the string , which is the longest prefix of s that matches a proper suffix of the taboos, provides all the information we need to construct or .
Isomorphisms between taboo-free Hamming graphs
Here we will discuss isomorphism between Hamming graphs. Let us first introduce the formal definition of a taboo-free Hamming graph.
Definition 7
The taboo-free Hamming graph of length n, , is the graph with vertex set such that two vertices are adjacent if their Hamming distance equals 1, that is, iff Analogously, is the Hamming graph with vertex set .
Examples of disconnected Hamming graphs are given in Figs. 1 and 2. When dealing with taboo-free Hamming graphs, the following proposition is a simple way to establish graph isomorphisms.
Proposition 14
Consider a taboo-set , a taboo-free string s and a taboo-free string w satisfying . If for some , then and are isomorphic.
Proof
By assumption, the vertex set of is . Thus, the map
is well defined and bijective. Moreover, f is an edge-preserving bijection: Given any pair of strings and any string , then iff .
Propositions 14 and 11.a imply that, for a taboo-free string s with , the graphs and are isomorphic. Furthermore Proposition 11.b implies that which can be stated as follows.
Proposition 15
Consider a taboo-set and a taboo-free string s. There exists a unique such that . Moreover, for any ,
Proposition 15 does not describe in which cases . However, if is left proper, Proposition 8 implies that this happens iff and . This suggests that we can state a version of Proposition 15 for left proper . But first, due to our interest in taboo-free strings of length M, we introduce the following.
Definition 8
Given a left proper taboo-set , the long suffix classification is defined as
that is, is the set of all suffixes of taboos that are the longest prefix of at least one taboo-free string of length M.
Example 5
If and , then
For any , we see , hence . Moreover,
yielding . If we consider , where could represent a 5-methylcytosine, and , then string satisfies , hence .
The following theorem classifies graphs for left proper .
Theorem 16
Consider a left proper taboo-set and a taboo-free string s such that either or . Then a unique exists such that , which satisfies for . Moreover, if , then .
Proof
Proposition 8.b yields for , while for follows from Proposition 15. Hence we can set , which by definition belongs to . Since by assumption either or , it follows from Proposition 7 that s is k-prefixable for any k, and thus also is k-prefixable. We consider , which satisfies . Therefore . All in all, . This w is trivially unique since is uniquely determined given s.
As for the case , the fact that and the definition of implies that .
In formal terms, Theorem 16 states that the equivalence relation “being isomorphic” divides all graphs into equivalence classes. The representative of each class is a graph , where . When , string w belongs to . This is why is called the long suffix classification.
To efficiently compute , we recommend that be minimal. Theorem 16 implies that
| 2 |
and thus we define the short suffix classification as
| 3 |
The set is called short suffix classification because only when it can happen that a graph is represented by a graph with . Note that, if a string w satisfies the condition and for some , then any satisfies , hence . This property is used in the following example.
Example 6
If and , then it is clear that , because the empty string e belongs to both sets. Moreover, due to . Therefore
Connectivity of taboo-free Hamming graphs
We will make extensive use of the quotient graph to study the connectivity of taboo-free Hamming graphs. Before we start with the technicalities, we briefly describe our initial strategy.
For a Hamming graph , let us consider two different subsets of its vertex set, namely and , where . These two subsets are disjoint, so we can use the quotient graph to make each of them collapse in a single vertex, represented respectively by and . We will prove in Proposition 17 that and are adjacent in iff strings and have Hamming distance 1 and are left n-synchronized. This is specially interesting, because we know from Proposition 9 that two left -synchronized strings are left n-synchronized for any . Thus, it is enough to know that are adjacent in to claim that are adjacent in all partition graphs for (that is the essential content of Lemma 18). More formally, we have the following results.
Proposition 17
Given taboo-set , and , consider graph and a subset partitioned as , where are taboo-free strings of length j. Consider moreover the quotient graph , where denotes the graph induced by S in .
In these conditions, a pair of vertices is connected by an edge iff the pair , is left n-synchronized and .
Proof
By definition, b and c are adjacent in iff in graph an edge connects a vertex in with a vertex in . Since , this edge exists iff and there exists such that . The last condition is the definition of and being left n-synchronized.
The combination of Propositions 17 and 9 gives the following lemma.
Lemma 18
Given a left proper taboo-set , a taboo-free string s and , consider, for any , partition and quotient graph . Then it holds that
If is connected, then is connected for .
Proof
For some , consider an edge of graph , where . We set and . Proposition 17 implies that and are adjacent in iff and are are left -synchronized and . Since and are left -synchronized, they are also left -synchronized for any , and thus and are adjacent in for . Hence the decreasing chain of quotient graphs is proven.
Now we will prove that this chain stabilizes after . If , then, according to Proposition 9, and are left k-synchronized for arbitrary k, and thus Proposition 17 implies that and are adjacent in for arbitrary . All in all, and have the same edges, as desired.
Regarding connectivity, given graphs and with the same vertex set such that , if subgraph is connected, then is connected.
Figure 4 visualizes Lemma 18 for alphabet , taboo-set (which is left proper), suffix and .
Fig. 4.
Visualization of Lemma 18 for , , and . It holds that
We are finally ready to study the connectivity of graphs for . Let us begin with the following lemma.
Lemma 19
Given a left proper , for any consider the set and partition
inducing the quotient graph Then the following statements are equivalent:
For every , is connected.
For every and integer , is connected.
Proof
Proposition 2 states that, in a connected graph, every quotient graph is connected, and thus (b) implies (a) by considering .
Now we prove by induction that (a) implies (b). For and , we have that
hence is connected. For the inductive step, assume that is connected for every and up to an integer . We will prove that also every is connected. Consider
Let us write w separating the first symbols from the last one, that is for and Then for any , . Since , Proposition 11.a implies , while the isomorphism established in Proposition 14 yields
Thus, every is connected, because the induction hypothesis implies that is connected since . To prove that graph is connected, it remains to apply Proposition 1, so we need to prove that the quotient graph induced by partition , namely , is connected.
We know that, given partition , the quotient graph is connected. Applying Lemma 18 with and , we get the following chain of inclusions:
Since is connected, every quotient graph of the chain of inclusions is connected, as shown in Lemma 18. In particular, graph is an element of the chain of inclusions because , so it is connected, as desired.
Lemma 19 is very interesting: We wanted to characterize the connectivity of graphs for and . We have proved that it is enough to study a finite number of graphs, namely for , that is, graphs. Let us summarize the connectivity results that follow from Lemma 19 and Theorem 16.
Proposition 20
Given a left proper , the following statements are equivalent:
For any taboo-free string s with and any integer , is connected.
For any and any integer , is connected.
For any , is connected.
For any , the partition induces a connected partition graph
Proof
Implication (a) (b) is obvious, while (b) (a) is proven as follows: Given , where s is a taboo-free string with , Proposition 11.a implies that Since , applying Proposition 11.a again we have . Proposition 14 yields the isomorphism , and is connected due to and the assumption of (b). Thus, statements (a) and (b) are equivalent.
Implication (b) (c) is consequence of Theorem 16. Moreover, (c) (d) follows from Proposition 2. It remains to prove (d) (b), which we do as follows. Corollary 12 implies . Moreover, for any and , we claim that the following statements are equivalent:
-
(i)
Strings aw and bw are left k-synchronized.
-
(ii)
Strings and are left k-synchronized.
Indeed, the implication (i) (ii) is obvious, so let us prove (ii) (i). Given a taboo-free string such that and are taboo-free, we want to prove that also saw and sbw are taboo-free. But if that were not the case, it would be the consequence of either or for some integers . However, that contradicts the maximality of , yielding .
Our previous claim and Proposition 17 imply that, if for some , given partition , it holds that
Theorem 16 implies that, for every , there exists . Applying Lemma 19, finally (d) (b) follows.
It is worth noticing how simpler the connectivity problem has become. Initially, we were studying whether every with is connected, obtaining in Lemma 19 that this is equivalent to the connectivity of graphs for , which are graphs. Now we see, using Proposition 20 and the fact that , that we only need to prove the connectivity of graphs, namely either or for . We give an example.
Example 7
Take and , which is left proper. Using Proposition 20, since and the connectivity of graphs
implies that any with is connected. Proposition 15 implies that, for any taboo-free string s and , is connected.
Proposition 20 characterizes the connectivity of every for . We know from Theorem 16 that there exists such that . Since , to complete our characterization of the connectivity of every taboo-free Hamming graph, some cases (such as Example 6) require considering the connectivity of graphs for . We have the following.
Proposition 21
Given a left proper and , assume that, for every , graph is connected. Given , if partition
satisfies that for each , and moreover is connected, then is connected for .
Proof
For , given partition
subgraphs are connected due to . Moreover, since is connected, Lemma 18 with implies that is connected for . Thus, the quotient graph and all induced subgraphs are connected. The connectivity of follows applying Proposition 1.
In Proposition 21, one can always take and just check if or is connected for . Otherwise one can try and increase it progressively.
Example 8
If and , then it holds that and . For , it can be proven that is connected. Thus, Proposition 20 implies that every is connected for and .
We can combine Propositions 20 and 21 to obtain our aimed characterization of the connectivity of every suffix Hamming graph. We do so in the following theorem.
Theorem 22
Given a left proper taboo-set , the following are equivalent.
-
Consider, for every , partition , and for every , partition .
For , every partition graph is connected; for , every partition graph is connected; for , every graph with is connected.
For , graph is connected; for , graph is connected; for and , every graph is connected.
For every taboo-free string s and , graph is connected.
Proof
Proposition 2 states that the connectivity of a graph is equivalent to the connectivity of each of its quotient graphs. Hence (b) (a) follows, because if graphs and are connected, then also partition graphs and are connected. Since the implication (c) (b) is obvious, it only remains to prove (a) (c).
Theorem 16 states that, when is left proper, every nonempty graph of the form is isomorphic to graph , where . By construction, strings in either belong to or . Therefore, statement (c) is equivalent to the connectivity, for every , of every , where , and of every , where .
Assuming statement (a), since every partition graph is connected for , Proposition 20 implies that every graph is connected, where and . For any , there exists by construction a such that . Since due to Proposition 15, it follows that (a) implies that every is connected, where and .
It remains to prove that (a) implies that every is connected, where and . Since every partition graph is connected, Proposition 21 with implies that is connected for . The connectivity of graphs is part of the assumptions of (a), and graphs and are trivially connected, finishing the proof.
In general, if has just a few taboos, proving connectivity becomes easier since most of strings are left k-synchronized. In Proposition 23 only previous results are used, while in Proposition 24 we study this case more exhaustively in a self-contained manner. Note that, when taboo-set is minimal, the assumptions of Proposition 24 are much easier to check.
Proposition 23
Given a left proper such that every pair of strings with is left 1-synchronized, it holds that:
For any and , is connected.
For any with connected , is connected for .
Proof
Proposition 10 implies that every pair is left k-synchronized for any . We know from Lemma 17 that left k-synchronization of two strings with Hamming distance 1 indexing a partition as suffixes is equivalent to those two strings being adjacent in the partition graph. Therefore any quotient graph induced by partition is fully connected (that is, every two vertices are adjacent). In particular, every is connected, and thus Proposition 20 implies (a). Similarly with partition since for , Proposition 21 implies (b).
Example 9
For and , the strings and are taboo-free for , hence they are left 1-synchronized. Since , for any taboo-free string s and , is connected.
Proposition 24
Given taboo-set and set , if every pair of taboo-free strings with and is left 1-synchronized, then it holds that:
Every taboo-free string is 1-prefixable. In particular, is left proper.
Every two taboo-free strings with are left 1-synchronized.
Graph is connected for every taboo-free string s and .
Proof
Consider any taboo-free string s. Assume that, for each , as is not taboo-free, that is, that for some integer , . WLOG assume and consider , which satisfies since . By construction, for any , string is not taboo-free. On the other hand, the Hamming distance between and itself is 0, and thus the assumption of the statement implies that is left 1-synchronized with . In other words, a symbol exists such that is taboo-free, which is a contradiction. All in all, s must be 1-prefixable. Taking we see that is left proper.
Given taboo-free strings such that , assume that they are not 1-synchronized. Then for every , either or for some . Denote by those such that , and analogously with . If were empty, then would not be 1-prefixable, contradicting (a). Thus, both and must be nonempty. Consider and . It holds that and . Moreover, we have that the pair , is not left 1-synchronized. Since , that contradicts the assumptions of the statement, hence and must be left 1-synchronized, as desired.
-
Clearly is connected, so let us proceed by induction. Assume is connected for a fixed and consider . Since , if , then is connected. Otherwise we take different ; we will prove that they are connected. We know that , hence let us write and for and . If , the result is obvious, so assume .
By hypothesis, is connected, and thus there exists a path of vertices of , namely , such that , and . For every , the pair , is left 1-synchronized, and thus there exists such that and are taboo-free. Since , and are adjacent in . Moreover every pair of taboo-free strings contained in is adjacent for . Since the relation “being connected” is transitive, vertices and are connected, as desired.
Example 10
If and , then . Every pair of strings in is left 1-synchronized, hence for every taboo-free s and , is connected.
Now we aim to find an upper bound for the number of taboos needed to guarantee connectivity of the graphs . The following Corollary of Proposition 24 holds.
Corollary 25
Consider an alphabet and a taboo-set . The following holds:
If , then for any taboo-free string s and , is connected.
If , then for any taboo-free string s and , is connected.
Proof
Assume that taboo-free strings , satisfy . That is, for each , either or has a taboo as prefix, contradicting . Therefore every two taboo-free strings are left 1-synchronized, so we can apply Proposition 24.c, implying (a).
If , then . Thus, statement (a) yields the result.
Corollary 25.b implies that, if , then every is connected. In Examples 11 and 12, we give examples of taboo-sets over an alphabet with and symbols respectively, such that and at least one suffix graph is disconnected. In this sense, the upper bound that guarantees connectivity for every suffix graph cannot be improved.
Example 11
If and , then is left proper and . For , , which makes disconnected. The trivial graphs and are both connected.
Example 12
For , and the left proper taboo-set
we claim that is disconnected for . Indeed,
so take and . It holds that , hence we found two disconnected components in graph . This is coherent with .
To generalize this example, for , denote by the concatenation of i ’s. The taboo-set
satisfies that graph is disconnected for .
In this section, we have stated various results regarding the connectivity of every suffix Hamming graph given a left proper taboo-set . Up to Theorem 16, our aim was to characterize the connectivity of every suffix Hamming graph. Then we found sufficient conditions in Proposition 24 and Corollary 25 that are easier to apply. When studying this connectivity problem, the practitioner should firstly try to apply the results requiring easy-to-check assumptions, and increasingly use the more complicated ones. Given a taboo-set , a possible workflow would be the following:
We check if . If it holds, we can apply Corollary 25.a. Otherwise go to step 2)
In order to apply Proposition 24, we check if every pair of taboo-free strings with and is left 1-synchronized. If it does not hold, go to step 3)
We check whether is left proper (this holds in all the biological examples that we considered so far). Otherwise redefine an equivalent left proper taboo-set and apply the characterization of Theorem 22. Two possibilities can arise: Either every suffix Hamming graph is connected, and thus evolution can explore all the space of taboo-free strings; or some taboo-free strings belonging to or induce disconnected suffix graphs for some , implying that stays disconnected for .
Examples of plausible bacterial taboo-sets
Taboo-sets as generated by the avoidance of restriction sites can assume various levels of complexities. In this section, we discuss some examples from REBASE (Roberts et al. 2014) using the theory developed in this work. Note that many restriction enzymes of REBASE database have an unknown recognition site, hence our taboo-sets may underestimate the actual amount of taboos. Before describing the examples, we will briefly review essential nomenclature for DNA sequences.
DNA is double-stranded, where A pairs with T and G pairs with C, hence it suffices to discuss only one of the strands. We adopt the convention that, given any of the strands, the DNA sequence is always represented from the 5’ end to the 3’ end (which is chemically determined). As a consequence, given a DNA sequence, its complementary DNA sequence, the one lying on the opposite strand, is obtained by inverting the order of the symbols and carrying through substitutions and . If a DNA sequence s is identical to its complementary DNA sequence, we say that s is an inverted repeat (Ussery et al. 2008). For example, sequence CCGG is an inverted repeat.
The fact that DNA is double-stranded implies that each recognition site induces taboos in pairs, namely itself and its complementary DNA sequence. For example, if AGGGC is a recognition site, then also the complementary strand GCCCT is a taboo. If, however, the recognition site is an inverted repeat such as TGCA, then this pair is actually one single recognition site. Recognition sites of type II R–M systems are nearly always an inverted repeat (Rusinov et al. 2015; Gelfand and Koonin 1997), and therefore one recognition site induces one single taboo. This is specially interesting because, according to Rusinov et al. (2015, (2018a), only type II R–M systems induce taboos.
A permutation of the symbols of alphabet does not alter any of the results that we proved along this work. Moreover, by reversing the order of the symbols, any statement regarding e.g. left-properness and suffixes has an analogous one in which right-properness and suffixes are involved. On the other hand, taboo-sets induced by restriction enzymes remain invariant when we interchange every recognition site by its complementary sequence. Therefore, note that, for a bacterial taboo-set , if we prove that every graph is connected, then also every graph is connected.
A frequent case: Turneriella parva
The Turneriella parva (REBASE organism number 8970) strain produces a restriction enzyme with recognition site GATC, an inverted repeat. Similarly, another of its enzymes has recognition sites GGACC and GGTCC. Thus, these restriction enzymes generate the taboo-set
| 4 |
Since , Corollary 25.a implies that every graph is connected. Therefore the evolution of the DNA sequences can potentially reach any other taboo-free DNA sequence, no matter which suffix was conserved along this process.
Among the 3623 bacteria in REBASE (2020a), only 465 have more than three type II restriction enzymes. Assuming that only type II restriction enzymes induce taboos, as stated by Rusinov et al. (2015, (2018a), Corollary 25.b implies that at least of bacterial taboo-sets in REBASE (2020a) yield connected taboo-free Hamming graphs. Similarly, at least of archea in REBASE (2020b) induce connected taboo-free Hamming graphs, because they have less than four type II restriction enzymes. The following example describes a more complex collection of restriction enzymes.
Helicobacter pylori
In H. pylori 21-A-EK1, studied by Ailloud et al. (2019), many restriction enzymes have been identified. For the sake of clarity, let us write , where denotes those taboos in whose first symbol is . Then we have
| 5 |
where represents taboos of the type GTabAC with , and so on for analogous notations.
We want to apply Proposition 24. Take any and assume that they are not left 1-synchronized. In particular WLOG we can assume that , implying . If , then , which contradicts . Therefore it must be , yielding . In any case, . Thus, for any with , it holds that and are left 1-synchronized, so Proposition 24 can be applied: Every graph is connected and, in particular, is connected.
An imaginary bacterium
The taboo-set can significantly influence evolution in the cases where some is disconnected. To explain this, we will create a plausible, nonexistent example. Suppose that a strain of Bacterium imaginara has taboo-set
where the second set contains the complementary DNA sequences of the first set, except that of GGCC, which is an inverted repeat. Thus, taboo-set is induced by 4 restriction enzymes. At first glance, taboo-set seems less restrictive than , which has 6 taboos of length four and 22 taboos of length five or more.
Proposition 24 cannot be applied because CCC and GCC are not left 1-synchronized, and actually we can find a disconnected suffix graph. Let us take , which satisfies
implying that, for any strings and , it holds that . Thus, we found two disconnected components in , namely and . All in all, the graph is disconnected for .
This produces the following evolutionary implications: Assume that we have two correctly aligned DNA fragments and of the genome of Bacterium imaginara. Assume moreover that we can write and for some strings and , as also that the suffix CCC is invariable due to functional constrains. Then cannot have evolved from by simple point mutations, because at some point in evolution a taboo string is produced that is lethal for the carrier. Thus, the standard models of sequence evolution (Strimmer and von Haeseler 2009) do not apply.
Concluding remarks
Using the results proven in this work, it is possible to decide whether every Hamming graph is connected. The connectivity of the taboo-free Hamming graphs induced by the restriction enzymes of the bacteria listed in REBASE could be quickly analysed with our tools. Unfortunately, for many organisms listed in REBASE, the recognition sites of restriction enzymes are not available.
Based on the current version of REBASE (2020a), we conclude using Corollary 25 that taboo-sets of at least of bacteria in REBASE induce connected taboo-free Hamming graphs, because they have less than four type II restriction enzymes. For larger taboo-sets, Proposition 24 can be used, as we did in Sect. 9.2, or one can directly use the characterization of Theorem 22. Thus, restriction enzymes in bacteria generally do not lead to any disconnected taboo-free Hamming graph, and our models of sequence evolution are by and large applicable. However, the influence of some missing sequences in the Hamming graph on the estimation of evolutionary parameters deserves further investigations. We also would like to emphasize that still many recognition sites have to be identified, and thus it may be well possible that we find disconnected taboo-free Hamming graphs in the next future.
We consider the formal framework developed in this paper as a first and necessary step to understand the effect of restriction enzymes (and possibly other taboo sequences) on the DNA composition of bacteria and viruses, or more generally on the sequence space modelled as a Hamming graph. Consider, for example, the phylogenetic studies by Ailloud et al. (2019), where the H. pylori taboo-set of Sect. 9.2 was taken from. The following natural questions arise: How are inferred evolutionary times between the two H. pylori populations affected by ? Has their GC content varied due to the taboos of restriction enzymes?
To answer such questions, we need to develop models of sequence evolution that take taboos into account. Taboo avoidance induces complex dependencies along a DNA sequence, which can be measured using Markov Chain Monte Carlo (MCMC) simulations. If all taboo-free Hamming graphs are connected, then MCMC methods are easy to apply (Manuel et al. unpublished). A disconnected taboo-free Hamming graph, however, leads to a reducible Markov chain, which complicates simulation of taboo-free evolution.
Another application of our framework is the construction of combinations of restriction enzymes that lead to a disconnected Hamming graph, and thus limit evolutionary freedom. This may help to efficiently treat viral infections. Some progress has been made in the usage of restriction enzymes for the treatment of viral infections (Weber et al. 2014). Since one or just a few SNPs can significantly alter the symptoms or even the mortality associated to a pathogen (Collery et al. 2017; Yuan et al. 2017), our characterization of the connectivity of taboo-free Hamming graphs could help to delete SNPs from the viral genome that are detrimental to humans. Although the treatment of an infection using restriction enzymes is mostly unexplored, this work could be a first theoretical guide to a successful treatment.
Acknowledgements
We would like to thank Michael Charleston (University of Tasmania) for his constructive criticism. In fact the idea of studying taboo-free sequences originated from discussions with Mike while Arndt received a visiting fellowship at the University of Tasmania. This work was supported by the Austrian Science Fund (FWF, Grant Number I-1824-B22) to Arndt von Haeseler.
Author Contributions
C.M. wrote this manuscript with the guidance of A.vonH. All authors read and approved the manuscript.
Funding
Open access funding provided by Austrian Science Fund (FWF).
Compliance with ethical standards
Conflict of interest
The authors declare that they have no conflict of interests.
Footnotes
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Cassius Manuel, Email: cassius.perez@univie.ac.at.
Arndt von Haeseler, Email: arndt.von.haeseler@univie.ac.at.
References
- Ailloud F, Didelot X, Woltemate S, Pfaffinger G, Overmann J, Bader RC, Schulz C, Malfertheiner P, Suerbaum S. Within-host evolution of Helicobacter pylori shaped by niche-specific adaptation, intragastric migrations and selective sweeps. Nat Commun. 2019;10(1):2273. doi: 10.1038/s41467-019-10050-1. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Alberts B, Bray D, Lewis J, Raff M, Roberts K, Watson J. Molecular biology of the cell (chapter 8) 5. London: Garland; 2004. pp. 532–534. [Google Scholar]
- Asinowski A, Bacher A, Banderier C, Gittenberger B (2018) Analytic combinatorics of lattice paths with forbidden patterns: enumerative aspects. In: Language and automata theory and applications. Springer, pp 195–206
- Asinowski A, Bacher A, Banderier C, Gittenberger B (2020) Analytic combinatorics of lattice paths with forbidden patterns, the vectorial kernel method, and generating functions for pushdown automata. Algorithmica 82:386–428. 10.1007/s00453-019-00623-3
- Collery MM, Kuehne SA, McBride SM, Kelly ML, Monot M, Cockayne A, Dupuy B, Minton NP. What’s a SNP between friends: the influence of single nucleotide polymorphisms on virulence and phenotypes of Clostridium difficile strain 630 and derivatives. Virulence. 2017;8(6):767–781. doi: 10.1080/21505594.2016.1237333. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Fitch WM, Margoliash E. A method for estimating the number of invariant amino acid coding positions in a gene using cytochrome c as a model case. Biochem Genet. 1967;1(1):65–71. doi: 10.1007/BF00487738. [DOI] [PubMed] [Google Scholar]
- Gelfand M, Koonin E. Avoidance of palindromic words in bacterial and archaeal genomes: a close connection with restriction enzymes. Nucleic Acids Res. 1997;25:2430–9. doi: 10.1093/nar/25.12.2430. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Hsu WJ, Chung MJ (1993) Generalized Fibonacci cubes. In: 1993 International conference on parallel processing—ICPP’93, vol 1, pp 299–302
- Ilić A, Klavžar S, Rho Y. Generalized Fibonacci cubes. Discrete Math. 2012;312:2–11. doi: 10.1016/j.disc.2011.02.015. [DOI] [Google Scholar]
- Klavžar S. Structure of Fibonacci cubes: a survey. J Comb Optim. 2013;25:505–522. doi: 10.1007/s10878-011-9433-z. [DOI] [Google Scholar]
- Kommireddy V, Nagaraja V. Diverse functions of restriction–modification systems in addition to cellular defense. Microbiol Mol Biol Rev MMBR. 2013;77:53–72. doi: 10.1128/MMBR.00044-12. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Manuel C, Pfannerer S, von Haeseler A (unpublished) Etaboo: modelling and measuring taboo-free evolution. Unpublished
- REBASE (2020a) The restriction enzyme database. http://rebase.neb.com/rebase/arcbaclistB.html. Accessed 17 June 2020
- REBASE (2020b) The restriction enzyme database. http://rebase.neb.com/rebase/arcbaclistA.html. Accessed 17 June 2020
- Roberts RJ, Vincze T, Posfai J, Macelis D. REBASEa database for DNA restriction and modification: enzymes, genes and genomes. Nucleic Acids Res. 2014;43(D1):D298–D299. doi: 10.1093/nar/gku1046. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Rocha E, Danchin A, Viari A. Evolutionary role of restriction/modification systems as revealed by comparative genome analysis. Genome Res. 2001;11:946–958. doi: 10.1101/gr.GR-1531RR. [DOI] [PubMed] [Google Scholar]
- Rusinov I, Ershova A, Karyagina A, Spirin S, Alexeevski A. Lifespan of restriction–modification systems critically affects avoidance of their recognition sites in host genomes. BMC Genomics. 2015;16(1):1084. doi: 10.1186/s12864-015-2288-4. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Rusinov IS, Ershova AS, Karyagina AS, Spirin SA, Alexeevski AV. Avoidance of recognition sites of restriction–modification systems is a widespread but not universal anti-restriction strategy of prokaryotic viruses. BMC Genomics. 2018;19(1):885. doi: 10.1186/s12864-018-5324-3. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Rusinov IS, Ershova AS, Karyagina AS, Spirin SA, Alexeevski AV. Comparison of methods of detection of exceptional sequences in prokaryotic genomes. Biochemistry (Moscow) 2018;83(2):129–139. doi: 10.1134/S0006297918020050. [DOI] [PubMed] [Google Scholar]
- Sanders P, Schulz C (2013) High quality graph partitioning. In: Proceedings of the 10th DIMACS implementation challenge workshop
- Shoemaker JS, Fitch WM. Evidence from nuclear sequences that invariable sites should be considered when sequence divergence is calculated. Mol Biol Evol. 1989;6(3):270–289. doi: 10.1093/oxfordjournals.molbev.a040550. [DOI] [PubMed] [Google Scholar]
- Strimmer K, von Haeseler A. Genetic distances and nucleotide substitution models. In: Lemey P, Salemi M, Anne-Mieke V, editors. The phylogenetic handbook: a practical approach to phylogenetic analysis and hypothesis testing. 2. Cambridge: Cambridge University Press; 2009. pp. 111–141. [Google Scholar]
- Ussery DW, Wassenaar TM, Borini S. Computing for Comparative Microbial Genome: Bioinformatics for Microbiologists. 1. Berlin: Springer; 2008. [Google Scholar]
- Weber ND, Aubert M, Dang CH, Stone D, Jerome KR. DNA cleavage enzymes for treatment of persistent viral infections: recent advances and the pathway forward. Virology. 2014;454–455:353–361. doi: 10.1016/j.virol.2013.12.037. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Wilson RJ. Introduction to graph theory. New York: Wiley; 1986. [Google Scholar]
- Yuan L, Huang X-Y, Liu Z-Y, Zhang F, Zhu XL, Yu J-Y, Ji X, Xu Y, Li G, Li C, Wang H-J, Deng Y-Q, Wu M, Cheng M-L, Ye Q, Xie D-Y, Li X-F, Wang X, Shi W, Qin C-F. A single mutation in the prM protein of Zika virus contributes to fetal microcephaly. Science. 2017;358:933–936. doi: 10.1126/science.aam7120. [DOI] [PubMed] [Google Scholar]