Abstract
We formulate and analyze a generic coverage optimization problem arising in wireless sensor networks with sensors of limited mobility. Given a set of targets to be covered and a set of mobile sensors, we seek a sensor dispatch algorithm maximizing the covered targets under the constraint that the maximal moving distance for each sensor is upper-bounded by a given threshold. We prove that the problem is NP-hard. Given its hardness, we devise four algorithms to solve it heuristically or approximately. Among the approximate algorithms, we first develop randomized -optimal algorithm. We then employ a derandomization technique to devise a deterministic -approximation algorithm. We also design a deterministic approximation algorithm with nearly approximation ratio by using a colouring technique, where denotes the maximal number of subsets covering the same target. Experiments are also conducted to validate the effectiveness of the algorithms in a variety of parameter settings.
Keywords: approximation algorithm, integer programming, mobile sensors, target coverage, wireless sensor network
1. Introduction
Wireless Sensor Networks (WSNs) are widely valued and have received significant attention in the last two decades. They are low cost and flexible thus they are widely applied in many applications scenarios ranging from health-care [1,2], industrial inspection [3], environmental monitoring [4,5], military defense [6,7], agriculture monitoring [8,9]. Coverage, as a fundamental issue in WSNs, has a direct impact on the networks’ efficiency. Based on the range of interesting, coverage problem was divided into area coverage [10,11], target coverage and barrier coverage [12,13]. In area coverage, each point in the entire 2D/3D range of interest (ROI) needs to be observed by at least one sensor. In target coverage, the objective is to ensure that a set of finite points located in the ROI are covered. Barrier coverage mainly focuses on detecting the intrusion across the borders of ROI. Most of the research on deployment problem focused on the area coverage. However, target coverage is also of primary importance as it is common in applications. For example, in information collection, only the information on certain points needs to be collected. As sensors may be randomly deployed in a large area, relocating a subset of mobile sensors is often required to ensure effective coverage over the monitored area. For battery-powered sensors, the energy consumption in movement is much higher than that in sensing and communication. Therefore, efficient sensor movement and scheduling strategies are called for to save energy while still meeting the coverage requirement or improve coverage quality with limited mobility [14,15,16].
In this paper, we study a target coverage problem with sensors of limited mobility in Mobile Wireless Sensor Network (MWSM). The network model was first presented in Reference [17]. In this network model, targets would be covered in a disk centred the sensor, that is, the sensor covers a target if it locates in the disk of the target. Each mobile sensor can cover more than one target if it locates in the overlapped region. The surveillance region is divided into several subareas, where a different subset of targets is detected/covered. Liao et al. [17] aim to minimize the sum of movement distances subject to covering all the targets. Considering there are not always enough sensors to cover all the targets and the energy of each sensor is limited, we want to study how to cover maximized number of targets with sensors of limited mobility. We call it Maximum Target Coverage with Limited Mobility (MTCLM) Problem. As far as we know, the problem is first presented in this paper. We prove that the MTCLM problem is NP-hard, and propose four algorithms, including one heuristic algorithm and three approximation algorithms. The heuristic algorithm is to choose an available subset at present that has the most increased profit. The approximation algorithms include a randomized approximation algorithm, where e denotes the base of the natural logarithm; a deterministic approximation algorithm by applying derandomiziation technique, and a deterministic approximation algorithm based on graph colouring technique, where is the maximal number of subsets covering the same target. Approximation algorithms are usually related to NP-hard problems. Since it is impossible to solve NP-hard in polynomial time, a polynomial-time suboptimal solution is acceptable. Different from heuristic algorithms, approximation algorithms can get a quality-guarantee solution, thus it requires provable solution quality and provable running time range.
To sum up, our contributions in this paper are the following:
We formulate the MTCLM problem and prove it NP-hard.
We propose four algorithms for the MTCLM problem, including one heuristic algorithm and three approximation algorithms.
We conduct experiments to validate the effectiveness of each algorithm in different conditions.
The rest of this paper is organized as follows—Section 2 reviews related works. The network model, the problem description and hardness are given in Section 3. Section 4 describes the four algorithms we present for the MTCLM problem. Section 5 presents the simulation results and investigates the performance of the algorithms proposed. Section 6 concludes the paper.
2. Related Works
Coverage Problem is so crucial that much research has done in the literature. Several survey papers related to the coverage issue in WSNs have been published [18,19,20,21,22], conclude the existing studies in different view. Reference [20] is the latest one published in 2019. It concluded the papers into three catalogues of coverage protocols: coverageaware deployment protocols, sleep scheduling protocols and cluster-based sleep scheduling protocols. It proposed that the more realistic model in WSNs is the future direction. Reference [22] described the deployment techniques in WSNs in detail, including Genetic Algorithms, Computational Geometry, Artificial Potential Fields, and Particle Swarm Optimization, and classifies the recent studies to the techniques. Reference [18] mainly concluded the studies on mobile wireless sensor networks (M-WSNs). It concluded that there were mainly four techniques to solve these problem proposed in M-WSNs, including optimization technique, computational geometry based technique, the virtual force-based technique, and geometry pattern based technique. Connectivity was usually considered in coverage problems [21]. Different from the above papers focusing on the deterministic model, Reference [19] concluded the coverage problem with uncertain properties and summarized the relevant models. Although the coverage problem had gotten so much attention, when a new technique was introduced to WSN, there were still considerable new researches. For example, with energy harvest technique getting mature, References [23,24,25,26,27,28] were proposed to study the coverage problem on the rechargeable WSN.
Most of the research on deployment problem focused on the area coverage. Target coverage is also an important topic. Most target coverage problems were NP-hard problem, optimization algorithms were applied to them including evolutionary algorithms [11,29,30,31,32] and combinatiorial algorithms [17,33,34,35,36].
A constrained Pareto-based multi-objective evolutionary approach (CPMEA) was proposed to find Pareto optimal layouts that maximized the coverage and minimized the sensors energy consumption while maintaining full connectivity between sensors [11]. A centralized genetic approach was provided to minimize the number of sensors and ensure targets K-coverage and M-connectivity simultaneously in Reference [29]. The fitness function was defined as a weighted sum of three factors: minimizing the number of sensors, maximizing the coverage performance and maximizing the communication connectivity. Dahiya et al. [30] proposed an algorithm to maximize the coverage of moving targets. They sampled the points on the trajectories of the mobile sensors uniformly to build a stationary probability distribution so that the uncertainty in the position of targets was fixed. A particle swarm intelligence (PSI)-based deployment algorithm was proposed to find the minimum number of static sensors to cover given targets in Reference [32]. Roselin et al. [31] proposed a sleep scheduling protocol to find disjoint covered set to extend the network lifetime while fulfilling the coverage and connectivity. Considering there were some crucial targets not be covered well, they classified sensors into four kinds and set their heuristic value, handled carefully the sensors which monitored the crucial targets.
The network model in our paper was first presented by Liao et al. [17]. In this paper, the Minimum Movement Target Coverage (MMTC) Problem was proved to be NP-hard. An extended Hungarian method was proposed to solve a particular case of the MMTC problem in which the distance between each pair of targets was longer than two times of sensing radius of sensors and a target based Voronoi greedy algorithm to solve the general case of MMTC. Another heuristic solution by minimizing the number of sensors needed was proposed in Reference [33]. Besides that, network connectivity was also considered in this paper. Another special case of MMTC, k-sink MMTC problem was proposed by Chen et al. [34], in which the sensors were located at k base stations and each station had infinite sensors, and a PTAS was proposed to obtain a approximation solution. Reference [35] studied the MMTC problem with restricted mobility that sensors could move only in two mutually perpendicular directions. A heuristic algorithm was proposed to ensure coverage and connectivity. Nguyen et al. [36] proposed a more general problem for the target coverage and network connectivity than the MMTC problem, termed the Maximum Weighted Target Coverage and Sensor Connectivity with Limited Mobile Sensors (TAR-CC) problem. In this paper, a maximum-coverage-based algorithm and a Steiner-treebased algorithm were proposed. In Reference [37], they also showed the hardness of some related topic on target coverage problem and rectified the incorrectness of the proof in Reference [17] by reducing MMTC problem to the minimum geometric disk cover problem. No approximation algorithm for the MMTC problem has been presented until now.
In our paper, we study the MTCLM problem to cover maximum number of targets with sensors with limited mobility, which is different from the Maximum Weighted Target Coverage problem in Reference [36] because the mobility is limited. And the maximumcoverage-based algorithm is not suitable anymore.
3. Preliminary and Problem Statement
3.1. Network Model and Problem Definition
We study the MTCLM problem in the following model. All the networking nodes are located in an obstacle-free surveillance region, including sensors and targets. The network is represented as . is the set of N targets distributed uniformly and randomly, each of which has its known position. is a set of M homogeneous mobile sensors with the same sensing radius r, which are supposed to schedule to cover all the targets. The disk model is adopted. That means a target t is said to be covered if and only if at least one mobile sensor’s final position is in the disk centred target t with radius r. The mobile sensors have known initial position, and they can move in any direction and stop anywhere. In Figure 1, the mobile sensor s can cover target a, b, c because s is in the disk , , at the same time, where is a disk centred a target t with radius r. As a result, the surveillance region can be divided into several subareas. In some subarea, a subset of targets is covered. Let denote a subset of targets, be the corresponding subarea where the sensors cover the subset of targets. Let denote the set of subsets corresponding to the subareas in surveillance region. Let K denote the number of the subareas/subsets, that is, .
Figure 1.
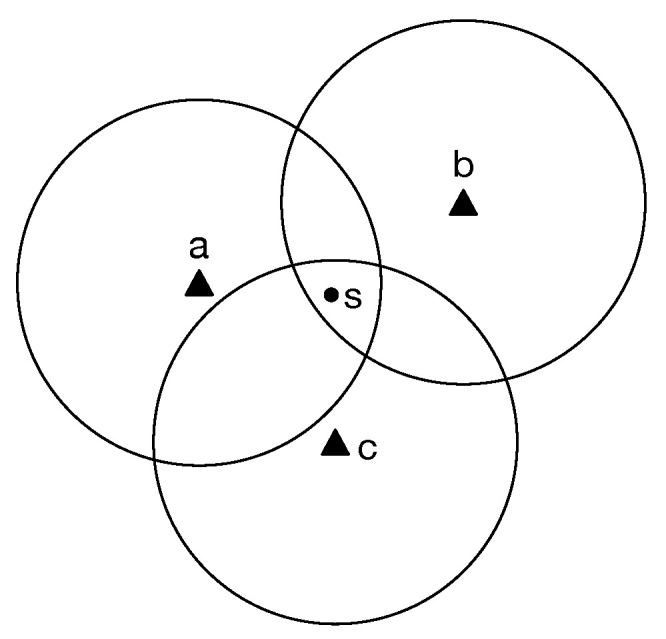
Subareas divided by targets.
Considering the limited energy of each mobile sensor, we present a maximum target coverage problem with sensors of limited distance. Let be the mobile sensors’ corresponding moving distance constraint. The maximum target coverage problem with sensors of limited mobility is defined below:
Definition 1.
Maximum Target Coverage with Limit Mobility (MTCLM) Problem: Given M mobile sensors and N targets located at surveillance domain with known positions, the mobile sensor are homogeneous with the same sensing radius. With the maximal moving distance of sensors constrained, to find how to schedule the sensors to cover as many targets as possible.
Table 1 summarizes the notations used in this paper.
Table 1.
Notations.
| Symbol | Definition |
|---|---|
| the set of targets: | |
| S | the set of sensors: |
| the distance constraint of sensors: | |
| a subset of sensors: | |
| the set of subsets: | |
| M | the number of sensors: |
| N | the number of targets: |
| K | the number of subareas: |
| r | the sensing radius of sensors |
| the sensing region of target t | |
| the intersection of for all |
3.2. Hardness of The Problem
We prove the MTCLM problem is NP-hard by reducing the minimum geometric disk cover (MGDC) problem to it as in Reference [37]. The MGDC problem is NP-hard and its definition is showed as following:
Definition 2.
The minimum geometric disk cover problem (MGDC) [38]: Given a set of m points , a disk radius r, and a constant , does there exist a set of centers such that every point in is covered by a disk centred at one of the centers in C and the cardinality of C, that is, n is not greater than k?
Then we prove the MTCLM problem is NP-hard.
Theorem 1.
The MTCLM problem is NP-hard.
Proof.
We consider a special case of the MTCLM problem when the maximal distance of each mobile sensors is not constrained, that is, for , each mobile sensor alway be able to reach any subarea to cover targets. By reducing the MGDC problem to the special case of the MTCLM problem, we prove the MTCLM problem is NP-hard.
Given an MGDC instance like Definition 2, we construct an MTCLM instance. In this instance, there are mobile sensors and targets; the sensing radius of mobile sensors is r. The set of centers is the set of final positions of the mobile sensors. If the MGDC instance is satisfied, that is, there exist disks covering all the points , there must be less than M sensors located in centers and the maximum number of covered targets in the MTCLM problem is N. Conversely, if the maximum number of targets covered in the MTCLM instance is m, there exist centers to cover all the points in . The MGDC instance is satisfied. Else if the maximum number of targets covered in the MTCLM instance is less than m, there does not exist centers all the points in . The MGDC instance is not satisfied.
Thus, the MTCLM problem is NP-hard. □
4. Algorithms
In this section, we propose four algorithms for the MTCLM problem, a heuristic algorithm, a randomized approximation algorithm, a derandomized approximation algorithm, and a deterministic approximation algorithm, respectively. Given an MTCLM instance, we should first find the subareas and its corresponding subsets, then find the minimal distances between each mobile sensor i and each subarea j. We will use the distance algorithm proposed in Reference [34] to solve the above two problems. That will take time. After pretreatment, we focus on the core issue on how to schedule the mobile sensors to cover the targets.
With the moving distance constraint, sensors can reach only some subareas. We construct a bipartite graph . Each vertex denotes a sensor in . Each vertex denotes a subarea covering a set of targets . When the distance between sensor i and subarea is smaller than the constrained moving distance of sensor i, that is, , there is an edge between vertex i and j, where is the minimum distance between sensor i and subarea j obtained in the pretreatment. The MTCLM problem is turning to be a matching problem except the weight is submodular. We formulate the MTCLM problem by an integer linear program (ILP) as following:
| (1) |
| (2) |
| (3) |
| (4) |
| (5) |
where denotes if target covered or not. denotes if sensor is scheduled to subarea , . The first constraint is the feasibility constraint, the second is the coverage constraint.
4.1. Greedy Algorithm
In this subsection, we propose a heuristic algorithm by choosing the available subset which contains the most uncovered targets for each sensor.
In Algorithm 1, let denote the solution. Let denote the uncovered targets in current iteration, . Let denote the covered targets. For each sensor , to find the accessbile subset with the most uncovered targets. The time complexity of this algorithm is .
| Algorithm 1: MTCLM_GREEDY(G, ). |
|
4.2. Randomized Algorithm
The Greedy algorithm presented above can not guarantee algorithm’s performance. Thus, we present three approximation algorithms which can make sure that the deviation of approximate solutions from the optimal value would not exceed a certain range. In this subsection, we propose a randomized approximation algorithm to obtain the expected value of the solution relative to the optimal value.
In this algorithm, we first obtain the optimal solution, and {}, of the Linear Program Relaxation (LPR) of formulas ILP, by replacing the constraints (4), (5) with and . Then for each vertex , we choose edge with prob. . Without changing the approximation ratio, we shift the covered targets by avoiding to cover the same subset. We run the algorithm for several times until we obtain the acceptable approximation solution.
Theorem 2.
Algorithm 2 is a randomized -approximation algorithm for the MTCLM problem.
Proof.
In this algorithm, the prob. for sensor covering target is and each sensor sends to cover subsets independently. Therefore, the overall prob. of not covering target t sums up to . According to Arithmeticgeometric mean inequality and the coverage constraint of ILP, we can show that
where m denotes the maximal degree of any vertex in in graph G. Again, it holds algebraically that . It then follows that the prob. of covering target t in the algorithm is
Remind that is the optimal value of LPR, bigger than the optimal value of ILP. Let denote the optimal value of ILP. Then the expected number of covered targets is
It holds that the randomized rounding algorithm gives a randomized -optimal solution.
Linear programs can be solved in polynomial time and so is Algorithm 2. The theorem is proved. □
In Algorithm 2, we use the recycle variable to avoid the sensors covering the same subset that would improve results and reduce instability in experiments.
| Algorithm 2: MTCLM_RANDOM (G, ). |
|
The method of conditional expectation can be used to derandomize the solution, but the computing complexity depends on the maximal degree n of any vertex in graph G, that is, the maximal number of subareas a sensor can reach. We show the derandomized algorithm as below: Let denote the set of vertices for sensor i. . In each iteration k, is fixed. Set to let the current conditional expectation maximized, that is, , where denotes the value of the LPR. After M iterations, we can obtain deterministic -optimal solution. In this algorithm, linear programs need to be solved. At the worst cast, is the number of vertices in . The number of subareas was proved in Reference [34]. Thus, at the worst case. That would make the time complexity of the derandomized algorithm too high. Even though, there are still lots of situations in which n is constant in practical. With the moving distance constraint, each sensor is only allowed to reach a constant subarea, that is the derandomized algorithm suitable for.
Theorem 3.
Algorithm 3 is a deterministic -approximation algorithm when n is constant.
Proof.
As the explanation above, we prove the theorem by induction.
When , with no is fixed, is the expectation of the total number of covered targets. is proved in Theorem 2, where is the optimal solution of the ILP.
In each iteration k, where is fixed. And . We choose , thus .
After M iterations, the number of covered targets is .
To sum up, there are M iterations, and in each iteration, we need to solve at most n linear programs. Thus the time complexity is , assuming the time complexity of a linear program is . When each sensor is only allowed to reach a constant subarea, that is, n is a constant, Algorithm 3 is linearly solvable. Now, we prove that Algorithm 3 is a deterministic -approximation algorithm. □
| Algorithm 3: MTCLM_DERANDOMIZED(G, ). |
|
4.3. Deterministic Algorithm
The randomized algorithm needs to run several times to reduce instability. The derandomized algorithm can obtain an approximation solution determinately but costs too much time complexity at most time. In this subsection, we propose a deterministic algorithm to obtain a nearly approximation value with less time complexity, where is the maximal number of subsets covering the same target. Let and denote the optimal solution of the LPR. We round up each of them to the closest fraction of the form , H is a large integer and a is an integer between 0 and H. Mathematically, let and is defined similarly. (The rounding would incur a quantization error which we analysis later). For the graph , we duplicate each node to identical nodes covering the same set of targets and connect each duplicated node to the neighbor of j. We call the new graph the auxiliary graph . We then find an edge-colouring of such that any pair of edge sharing the same vertex in is coloured differently. We can prove that H colours are sufficient. We can show by pigeon-hole principle that we can always find a colour that the vertices in covered by the edges in the colour cover at least targets, that is, . To prove this by contradiction, assuming that this is not true. Then the
It is leading to contradiction with the constraint (3) of the ILP.
The above analysis immediately implies that selecting the edges covered by the best coloured induced a -optimal solution. More applications of the method can be seen in Reference [39].
Each increases by at most by the rounding, hence increases the objective function by at most . Taking quantization error into consideration, the approximation ratio is . The auxiliary graph has at most nodes, edges, to find a proper coloration by greedy will take time . If we set , the approximation ratio is and the time complexity is . Thus we get the Theorem 4.
Theorem 4.
Algorithm 4 is a nearly approximation algorithm
| Algorithm 4: MTCLM_COLOUR (G, ). |
|
5. Simulation Experiments
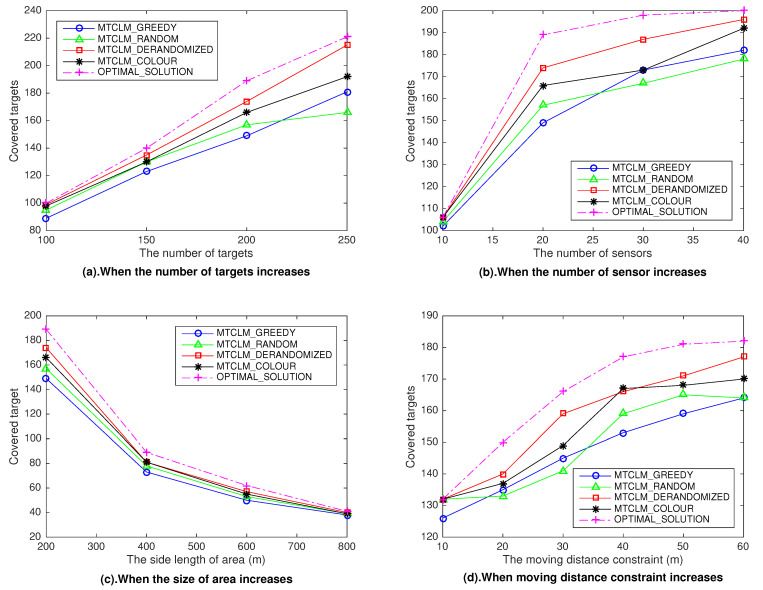
Even though the performance of some algorithms we proposed have been proved in theory, we still conduct a set of simulation experiments by using Matlab to compare them, validate their effectiveness, and show the impression of some parameters. We consider four network parameters that may impact on the number of covered targets: the number of targets M, the number of sensors N, the size of the surveillance region, the moving distance constraint . In the experiments, there are 200 targets and 20 mobile sensors uniformly, randomly generated in a square region of size 200 m × 200 m. The sensors’ coverage radius is m, and their moving distance constraint is 40 m. Even though the moving distance constraint of each sensor can be different, in our experiments, we assume they are the same. To test the impression of each parameter, we vary it in experiments and keep the other parameters keep the same. For each combination of network parameters, we randomly generate ten instances of the network and report the mean performance result. We show the results in Figure 2 below. In Figure 2, we compute the results of the algorithms we present and compare them to the optimal solutions. The optimal solutions can be obtained by using Matlab’s toolbox ’Yalmip’, which is a free optimization solution tool developed by Lofberg.
Figure 2.
To show the impression of four parameters on the four algorithms and the optimal solution. (a) shows the impression of the number of targets; (b) shows the impression of the number of sensors; (c) shows the impression of size of area; (d) shows the impression of the moving distance constraint of sensors.
In Figure 2a, the number of targets varied from 100 to 250. In Figure 2b, four different numbers of sensors are considered, namely . We can observe that, when the number of targets increases or the number of sensors increases, the number of targets covered increases.
In Figure 2c, four different sizes of area are considered, namely 200 m × 200 m, 400 m × 400 m, 600 m × 600 m, 800 m × 800 m. We observe that when the size of the surveillance regionincreases, the number of targets covered decreases. It is easy to understand that when the size of the surveillance region increases whereas the number of targets remain unchange, the average density of targets gets low. The average number of targets in a subset decrease hence the total number of covered targets decreases.
In Figure 2d, the moving distance constraint varied from 10 to 60. It is observed that when the moving distance constraint increases, the number of targets covered increase, but the growth rate would become slower.
In the simulation experiments, we obtain the numbers of maximum covered tagets through four algorithms, which are smaller than the optimal solutions. We calculate the lower bound of the performance of each algorithm, which is the minimum ratio of the algorithm solution to the optimal solution in the experimental data. Table 2 lists the lower performance bound of each algorithm:
Table 2.
The experimental lower bounds of the performance of the algorithms.
| Name of the Algorithm | Lower Bound of the Performance |
|---|---|
| MTCLM_GREEDY | 0.78 |
| MTCLM_RANDOM | 0.75 |
| MTCLM_DERANCOMIZED | 0.91 |
| MTCLM_COLOUR | 0.86 |
The approximation ratio is a performance lower bound, for example, in a maximization problem, approximation ratio of the algorithm indicates the approximate solution obtained by the algorithm would at least times greater than the optimal solution. Remind that the approximation ratio of algorithm MTCLM_RANDOM and MTCLM_DERANDOMIZED is , the approximation ratio of algorithm MTCLM_COLOUR is which depends on the parameter , where denotes the maximal number of subsets covering the same target. As shown in Table 2, the experimental lower bounds of the performance of the algorithms meet the theoretical analysis. Also, we can see that MTCLM_GREEDY algorithm achieves relatively worse results especially when the size of area is small and the number of targets and sensors remains unchange. That is because when the density of the target and the sensor becomes higher, it cannot just greedily select the target area, it needs to rely on global information. The performance of algorithm MTCLM_RANDOM is with a certain degree of randomness. The algorithm MTCLM_DERANDOMIZED has the best performance but it has higher time complexity than others. The algorithm MTCLM_COLOUR performs better than the theoretical analysis. There are two possibilities, one is that the example with the worst performance is not found, and the other is that there is a more accurate approximation analysis method for algorithm MTCLM_COLOUR, which can be studied further.
Combined with theoretical analysis, we know how to choose a suitable algorithm among these four algorithms according to the actual situation. When the accuracy requirements are not very high and the time requirements are very strict, the MTCLM_GREEDY algorithm and the MTCLM_RANDOM algorithm are good choices. Because these two algorithms only need linear time complexity, but the MTCLM_GREEDY algorithm cannot get a provable performance and the MTCLM_RANDOM has a randomly biased performance. When the target density is not large, that is, the parameter is small, the MTCLM_COLOUR algorithm will achieve good performance. When a sensor can only reach a constant number of target areas, that is, the parameter n denoting the number of target areas a sensor can reach is a constant, the time complexity of the MTCLM_DERANDOM algorithm is not high, and a good approximation ratio can be obtained.
6. Discussion
In this paper, we are the first to present the MTCLM problem to maximize the number of covered targets with sensors under limited mobility constraints. It applies to improving the utilization efficiency of insufficient sensors. Considering that the MTCLM problem is NP-hard and the requirements for time and performance are different in actual situations, we have proposed four algorithms and provided proof of algorithm performance for three of them. Through theoretical and experimental analysis, we also provide the direction of the algorithm selection in actual situations. Moreover, the proposed solutions are applicable to solving relevant resource allocation problems with the same model. In the future, it is interesting to find a more efficient algorithm with a better approximation ratio.
Author Contributions
Conceptualization, D.L. and H.S.; Methodology, D.L., L.C.; Software, D.L.; Validation, D.L., H.S.; Investigation, D.L.; Resources, H.S.; Writing—original draft preparation, D.L.; Writing—review, H.S., L.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research is supported by National Key R&D Program of China Project #2017YFB0203201, Key-Area Research and Development Plan of Guangdong Province #2020B010164003. The corresponding author is Hong Shen.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, of in the decision to publish the results.
Footnotes
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Hackmann G., Guo W., Yan G., Sun Z., Lu C., Dyke S. Cyber-physical codesign of distributed structural health monitoring with wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2013;25:63–72. doi: 10.1109/TPDS.2013.30. [DOI] [Google Scholar]
- 2.Shahin M.K., Tharwat A., Gaber T., Hassanien A.E. A wheelchair control system using human-machine interaction: Singlemodal and multimodal approaches. J. Intell. Syst. 2019;28:115–132. doi: 10.1515/jisys-2017-0085. [DOI] [Google Scholar]
- 3.Li X., Li D., Wan J., Vasilakos A.V., Lai C.F., Wang S. A review of industrial wireless networks in the context of industry 4.0. Wirel. Netw. 2017;23:23–41. doi: 10.1007/s11276-015-1133-7. [DOI] [Google Scholar]
- 4.Lombardo L., Corbellini S., Parvis M., Elsayed A., Angelini E., Grassini S. Wireless sensor network for distributed environmental monitoring. IEEE Trans. Instrum. Meas. 2017;67:1214–1222. doi: 10.1109/TIM.2017.2771979. [DOI] [Google Scholar]
- 5.Roy A., Sarma N. A synchronous duty-cycled reservation based MAC protocol for underwater wireless sensor networks. Digit. Commun. Netw. 2020 doi: 10.1016/j.dcan.2020.09.002. [DOI] [Google Scholar]
- 6.Pawgasame W. A survey in adaptive hybrid wireless sensor network for military operations; Proceedings of the 2016 Second Asian Conference on Defence Technology (ACDT); Chiang Mai, Thailand. 21–23 January 2016; pp. 78–83. [Google Scholar]
- 7.Shakila R., Paramasivan B. Performance Analysis of Submarine Detection in Underwater Wireless Sensor Networks for Naval Application. Microprocess. Microsyst. 2020 doi: 10.1016/j.micpro.2020.103293. [DOI] [Google Scholar]
- 8.Mois G., Folea S., Sanislav T. Analysis of three IoT-based wireless sensors for environmental monitoring. IEEE Trans. Instrum. Meas. 2017;66:2056–2064. doi: 10.1109/TIM.2017.2677619. [DOI] [Google Scholar]
- 9.Srbinovska M., Gavrovski C., Dimcev V., Krkoleva A., Borozan V. Environmental parameters monitoring in precision agriculture using wireless sensor networks. J. Clean. Prod. 2015;88:297–307. doi: 10.1016/j.jclepro.2014.04.036. [DOI] [Google Scholar]
- 10.Gupta H.P., Tyagi P.K., Singh M.P. Regular Node Deployment for k-Coverage in m-Connected Wireless Networks. IEEE Sens. J. 2015;15:7126–7134. doi: 10.1109/JSEN.2015.2471837. [DOI] [Google Scholar]
- 11.Khalesian M., Delavar M.R. Wireless sensors deployment optimization using a constrained Pareto-based multi-objective evolutionary approach. Eng. Appl. Artif. Intell. 2016;53:126–139. doi: 10.1016/j.engappai.2016.03.004. [DOI] [Google Scholar]
- 12.Zhang Y., Sun X., Wang B. Efficient algorithm for k-barrier coverage based on integer linear programming. China Commun. 2016;13:16–23. doi: 10.1109/CC.2016.7489970. [DOI] [Google Scholar]
- 13.Kim D., Wang W., Son J., Wu W., Lee W., Tokuta A.O. Maximum lifetime combined barrier-coverage of weak static sensors and strong mobile sensors. IEEE Trans. Mob. Comput. 2016;16:1956–1966. doi: 10.1109/TMC.2016.2606403. [DOI] [Google Scholar]
- 14.Gao X., Chen Z., Wu F., Chen G. Energy Efficient Algorithms for k -Sink Minimum Movement Target Coverage Problem in Mobile Sensor Network. IEEE/ACM Trans. Netw. 2017;25:3616–3627. doi: 10.1109/TNET.2017.2756925. [DOI] [Google Scholar]
- 15.Guo J., Jafarkhani H. Movement-Efficient Sensor Deployment in Wireless Sensor Networks With Limited Communication Range. IEEE Trans. Wirel. Commun. 2019;18:3469–3484. doi: 10.1109/TWC.2019.2914199. [DOI] [Google Scholar]
- 16.Elhoseny M., Tharwat A., Yuan X., Hassanien A.E. Optimizing K-coverage of mobile WSNs. Expert Syst. Appl. 2018;92:142–153. doi: 10.1016/j.eswa.2017.09.008. [DOI] [Google Scholar]
- 17.Liao Z., Zhang S., Cao J., Wang W., Wang J. Minimizing movement for target coverage in mobile sensor networks; Proceedings of the 2012 32nd International Conference on Distributed Computing Systems Workshops; Macau, China. 18–21 June 2012; pp. 194–200. [Google Scholar]
- 18.Mohamed S.M., Hamza H.S., Saroit I.A. Coverage in mobile wireless sensor networks (M-WSN) Comput. Commun. 2017;110:133–150. doi: 10.1016/j.comcom.2017.06.010. [DOI] [Google Scholar]
- 19.Wang Y., Wu S., Chen Z., Gao X., Chen G. Coverage problem with uncertain properties in wireless sensor networks: A survey. Comput. Netw. 2017;123:200–232. doi: 10.1016/j.comnet.2017.05.008. [DOI] [Google Scholar]
- 20.Elhabyan R., Shi W., St-Hilaire M. Coverage protocols for wireless sensor networks: Review and future directions. J. Commun. Netw. 2019;21:45–60. doi: 10.1109/JCN.2019.000005. [DOI] [Google Scholar]
- 21.Khoufi I., Minet P., Laouiti A., Mahfoudh S. Survey of deployment algorithms in wireless sensor networks: Coverage and connectivity issues and challenges. Int. J. Auton. Adapt. Commun. Syst. 2017;10:341–390. doi: 10.1504/IJAACS.2017.088774. [DOI] [Google Scholar]
- 22.Deif D.S., Gadallah Y. Classification of wireless sensor networks deployment techniques. IEEE Commun. Surv. Tutor. 2013;16:834–855. doi: 10.1109/SURV.2013.091213.00018. [DOI] [Google Scholar]
- 23.Shi T., Li J.Z., Gao H., Cai Z.P. Coverage in Battery-Free Wireless Sensor Networks; Proceedings of the IEEE Conference on Computer Communications (IEEE Infocom 2018); Honolulu, HI, USA. 16–19 April 2018; pp. 108–116. [Google Scholar]
- 24.Lin C., Zhou Y., Ma F., Deng J., Wang L., Wu G. Minimizing charging delay for directional charging in wireless rechargeable sensor networks; Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications; Paris, France. 29 April–2 May 2019; pp. 1819–1827. [Google Scholar]
- 25.Shi T., Cheng S., Li J., Cai Z. Constructing connected dominating sets in battery-free networks; Proceedings of the IEEE INFOCOM 2017-IEEE Conference on Computer Communications; Atlanta, GA, USA. 1–4 May 2017; pp. 1–9. [Google Scholar]
- 26.Wang C., Li J., Yang Y., Ye F. A hybrid framework combining solar energy harvesting and wireless charging for wireless sensor networks; Proceedings of the IEEE INFOCOM 2016-The 35th Annual IEEE International Conference on Computer Communications; San Francisco, CA, USA. 10–14 April 2016; pp. 1–9. [Google Scholar]
- 27.Wu T., Yang P., Dai H., Xu W., Xu M. Charging oriented sensor placement and flexible scheduling in rechargeable WSNs; Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications; Paris, France. 29 April–2 May 2019; pp. 73–81. [Google Scholar]
- 28.Shi T., Cheng S., Cai Z., Li J. Adaptive connected dominating set discovering algorithm in energy-harvest sensor networks; Proceedings of the IEEE INFOCOM 2016-The 35th Annual IEEE International Conference on Computer Communications; San Francisco, CA, USA. 10–14 April 2016; pp. 1–9. [Google Scholar]
- 29.Gupta S.K., Kuila P., Jana P.K. Genetic algorithm approach for k -coverage and m -connected node placement in target based wireless sensor networks. Comput. Electr. Eng. 2016;56:544–556. doi: 10.1016/j.compeleceng.2015.11.009. [DOI] [Google Scholar]
- 30.Dahiya S., Singh P.K. Optimized mobile sink based grid coverage-aware sensor deployment and link quality based routing in wireless sensor networks. AEU-Int. J. Electron. Commun. 2018;89:191–196. doi: 10.1016/j.aeue.2018.03.031. [DOI] [Google Scholar]
- 31.Roselin J., Latha P., Benitta S. Maximizing the wireless sensor networks lifetime through energy efficient connected coverage. Ad Hoc Netw. 2017;62:1–10. doi: 10.1016/j.adhoc.2017.04.001. [DOI] [Google Scholar]
- 32.Senouci M.R., Bouguettouche D., Souilah F., Mellouk A. Static wireless sensor networks deployment using an improved binary PSO. Int. J. Commun. Syst. 2016;29:1026–1041. doi: 10.1002/dac.3040. [DOI] [Google Scholar]
- 33.Liao Z., Wang J., Zhang S., Cao J., Min G. Minimizing movement for target coverage and network connectivity in mobile sensor networks. IEEE Trans. Parallel Distrib. Syst. 2015;26:1971–1983. doi: 10.1109/TPDS.2014.2333011. [DOI] [Google Scholar]
- 34.Chen Z., Gao X., Wu F., Chen G. A PTAS to minimize mobile sensor movement for target coverage problem; Proceedings of the INFOCOM 2016-The 35th Annual IEEE International Conference on Computer Communications; San Francisco, CA, USA. 10–14 April 2016; pp. 1–9. [Google Scholar]
- 35.Choudhuri R., Das R.K. Coverage of targets in mobile sensor networks with restricted mobility. IEEE Access. 2018;6:10803–10813. doi: 10.1109/ACCESS.2018.2801941. [DOI] [Google Scholar]
- 36.Nguyen N., Liu B., Wang S. On New Approaches of Maximum Weighted Target Coverage and Sensor Connectivity: Hardness and Approximation. arXiv. 2018 doi: 10.1109/TNSE.2019.2952369.1811.00487 [DOI] [Google Scholar]
- 37.Nguyen N., Liu B. The Mobile Sensor Deployment Problem and the Target Coverage Problem in Mobile Wireless Sensor Networks are NP-Hard. IEEE Syst. J. 2019;13:1312–1315. doi: 10.1109/JSYST.2018.2828879. [DOI] [Google Scholar]
- 38.Hochbaum D.S., Maass W. Approximation schemes for covering and packing problems in image processing and VLSI. J. ACM. 1985;32:130–136. doi: 10.1145/2455.214106. [DOI] [Google Scholar]
- 39.Barnoy A., Guha S. Approximating the Throughput of Multiple Machines in Real-Time Scheduling. SIAM J. Comput. 2002;31:331–352. doi: 10.1137/S0097539799354138. [DOI] [Google Scholar]