. 2021 Feb 9;9(2):e25245. doi: 10.2196/25245
©Sheikh Mohammad Idrees, Mariusz Nowostawski, Roshan Jameel. Originally published in JMIR Medical Informatics (http://medinform.jmir.org), 09.02.2021.
This is an open-access article distributed under the terms of the Creative Commons Attribution License (https://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work, first published in JMIR Medical Informatics, is properly cited. The complete bibliographic information, a link to the original publication on http://medinform.jmir.org/, as well as this copyright and license information must be included.
Figure 3.
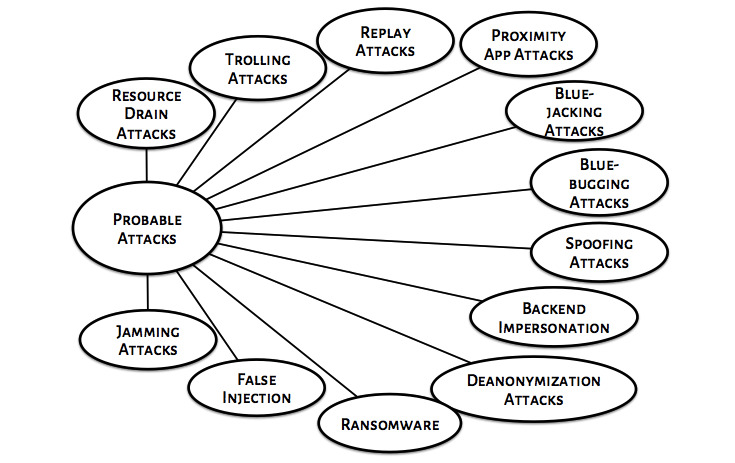
Probable attacks on contact tracing apps.
