. 2020 Nov 11;8:205071–205087. doi: 10.1109/ACCESS.2020.3037474
This work is licensed under a Creative Commons Attribution 4.0 License. For more information, see https://creativecommons.org/licenses/by/4.0/
This work is licensed under a Creative Commons Attribution 4.0 License. For more information, see https://creativecommons.org/licenses/by/4.0/
FIGURE 4.
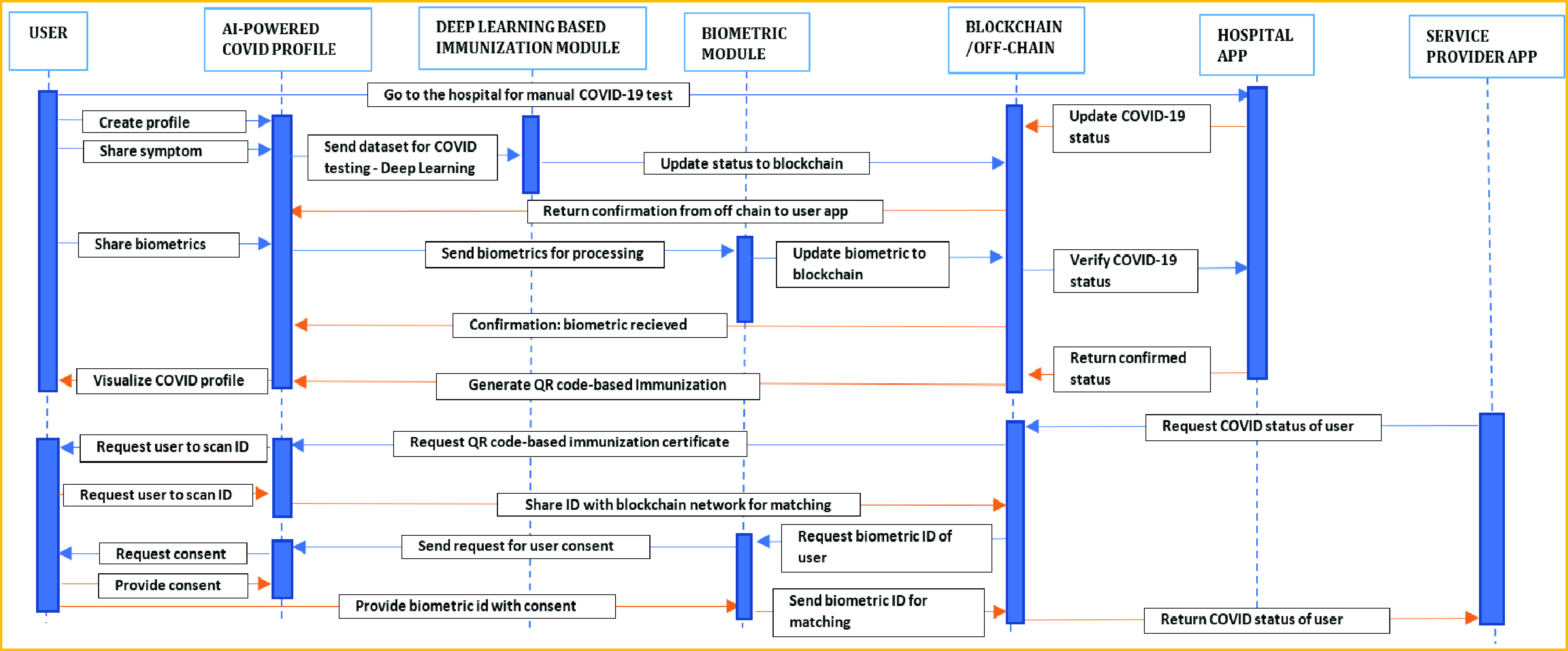
Sequence of secure user interaction and system output.
