FIGURE 1.
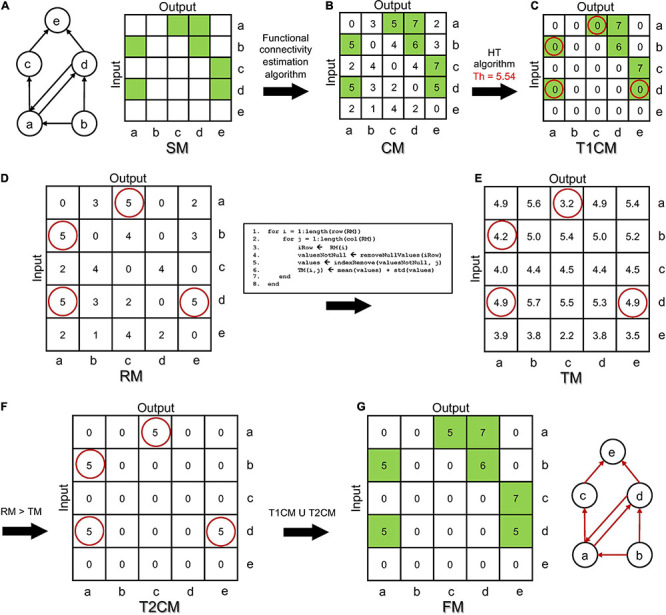
Double Threshold (DDT) algorithm operating principle applied to a simple network. (A) Structural graph made up of n = 5 nodes and the k = 7 structural directed links (left). Structural connectivity matrix (SM) where each green square identifies a structural connection in the graph (right). (B) Functional connectivity matrix (CM) obtained by applying the correlation algorithm to each pair of spike train. In the CM, the green squares show the functional connectivity values that correspond to the actually existing structural links in the network. (C) Applying the first hard threshold (n = 1), the T1CM matrix was computed. In T1CM, the red circles point to those connections incorrectly deleted from the CM (false negatives). (D) The rejected connectivity matrix (RM) is made of all the values that have been previously deleted by applying the hard threshold to the CM. By applying the stripping process summarized in the pseudo-code, (E) the thresholding matrix (TM) resulting from the application of the second step of DDT to the RM is achieved. It contains the threshold for each corresponding value of T1CM. (F) The T2CM shows every RM value that satisfies the condition RM > TM. (G) Final functional thresholded connectivity matrix (FM) and its relative functional graph.
