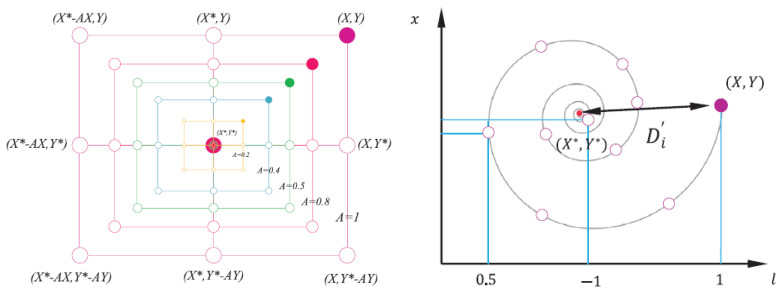
Figure 2.
Bubble-net hunting attack model consists of two stages: shrinking encircling mechanism (left) and spiral updating position (right), chosen in semi-random order [8]. Reproduced with permission from Elsevier publisher, licence no. 5198660218147.