TABLE 3. Comparison of Protocols for Security and Privacy Properties With Key Symbols and Terms.
| Name | Threat Model | Security Threats | Encryption Mechanism | Privacy Threats | Privacy Mechanism | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| T1 | T2 | T3 | T4 | T5 | T6 | T7 | T8 | T9 | T10 | T11 | T12 (Linkage) | |||||
| By Authority | By Contact | |||||||||||||||
| Epione | Semi-honest | • | ○ | ○ | • | ○ | • | • | Public key | • | • | ○ | • | ◑ | • | MPC (PSI-CA), pseudo-identifier |
| TCN | Semi-honest | ○ | • | ○ | ○ | ○ | • | ○ |
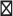 |
• | • | ○ | • | • | • | Pseudo-identifier |
| Reichert et al. | Semi-honest | ○ | ○ | ○ | ○ | ○ | ○ | • |
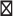 |
○ | ○ | ○ | • | ○ | • | MPC |
| DP3T | Semi-honest | ○ | ○ | ○ | ○ | ○ | ◑ | • | Symmetric | • | • | ○ | • | • | • | Pseudo-identifier |
| PACT | Semi-honest | ○ | ○ | ○ | • | ○ | ○ | ○ |
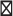 |
• | ◑ | ○ | • | • | ◑ | Pseudo-identifier |
| QUEST | Honest | • | ○ | ○ | • | ○ | ◑ | ○ | Symmetric | • | • | ○ | ○ | ○ | ○ | Homomorphic encryption |
| CAUDHT | Semi-honest | ○ | ○ | ○ | • | ○ | ◑ | • | Public key | • | • | ○ | • | • | ○ | Blind signature |
| PEPP-PT | Honest | ○ | ○ | ○ | • | ○ | ○ | • | Public key (assumed) | • | ○ | • | ○ | ○ | ○ | Pseudo-identifier |
| BlueTrace | Honest | • | • | • | • | ○ | ◑ | • | Symmetric | • | • | • | ○ | ○ | • | Pseudo-identifier |
| Whisper | Semi-honest | ○ | • | • | ○ | ○ | • | ○ |
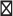 |
• | • | ○ | • | • | • | Pseudo-identifier |
| EPIC | Semi-honest | ○ | ○ | ○ | ◑ | ○ | ○ | ○ | Public key | • | ◑ | ○ | • | • | • | Homomorphic encryption |
| Recover | Honest | • | ○ | ○ | ○ | ○ | • | • |
 |
○ | ○ | ○ | ○ | ○ | • | Pseudo-identifier |
T1: Spoofing identity T2: Tampering with data T3: Repudiation T4: Information disclosure
T5: Denial of service T6: Replay attack T7: False-positive claim T8: Explicit consent
T9: Lack of control T10: Data longevity T11: Identification T12: Linkage
•: Property satisfied ○: Property unsatisfied ◑:Property partially satisfied
 : Not applicable
: Not applicable
