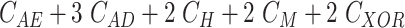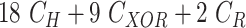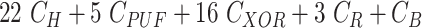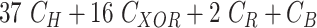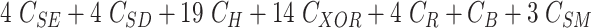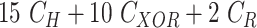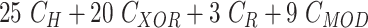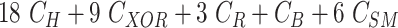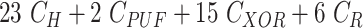TABLE V. Computation Cost Comparison of MASK Protocol Versus Conventional Protocols.
Acronyms:
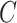 - Computation,
- Computation,
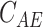 - Computation of asymmetric encryption,
- Computation of asymmetric encryption,
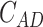 - Computation of asymmetric decryption,
- Computation of asymmetric decryption,
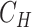 - Computation of Hash,
- Computation of Hash,
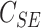 - Computation of symmetric encryption,
- Computation of symmetric encryption,
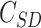 - Computation of symmetric decryption,
- Computation of symmetric decryption,
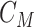 - Computation of hash based MAC,
- Computation of hash based MAC,
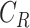 - Computation of random number,
- Computation of random number,
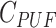 - Computation of Physically Unclonable Function,
- Computation of Physically Unclonable Function,
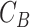 - Computation of bio-metric,
- Computation of bio-metric,
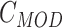 - Computation of modulus,
- Computation of modulus,
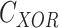 - Computation of Bit-wise XOR,
- Computation of Bit-wise XOR,
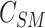 - Computation of Scalar Multiplication, Integers - defines the frequency of operation.
- Computation of Scalar Multiplication, Integers - defines the frequency of operation.