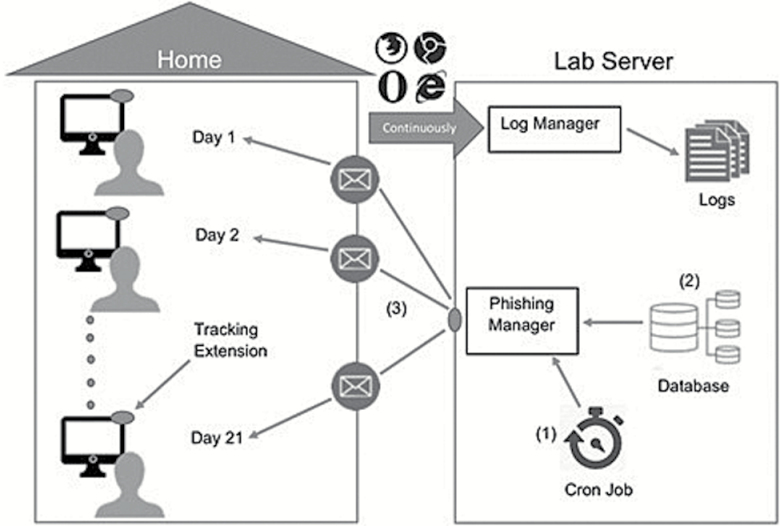
Figure 1.
PHIT study framework. Special software (cron-jobs) invoked our spear-phishing manager software module daily to (1) fetch user, schedule information, and spear-phishing email from database (2) and sent spear-phishing email to user; (3) a browser extension and a full-system behavioral extractor sent all computer events generated by the user (web links visited, timestamps, and information about software executed, files opened and network connections established) over the study course to the log manager software module, which recorded this data in log files (see “continuously” in figure).