. 2022 Apr 25;2022:5061059. doi: 10.1155/2022/5061059
Copyright © 2022 Nabeel Albishry et al.
This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Figure 4.
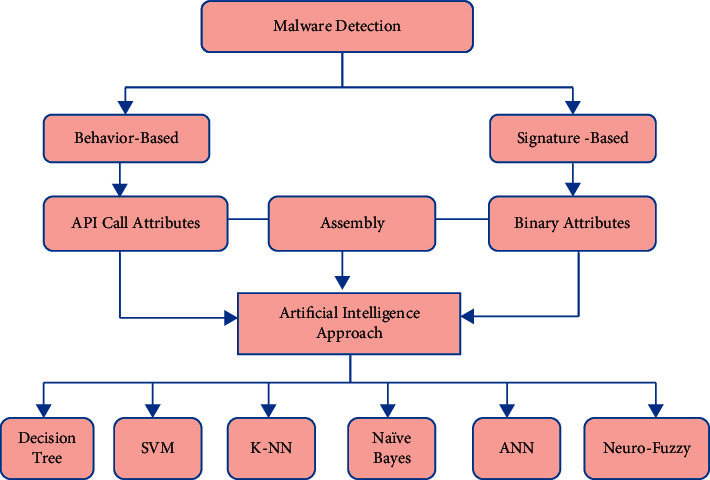
Malware detection methods.
