Abstract
This research introduces a systematic and multidisciplinary agent-based model to interpret and simplify the dynamic actions of the users and communities in an evolutionary online (offline) social network. The organizational cybernetics approach is used to control/monitor the malicious information spread between communities. The stochastic one-median problem minimizes the agent response time and eliminates the information spread across the online (offline) environment. The performance of these methods was measured against a Twitter network related to an armed protest demonstration against the COVID-19 lockdown in Michigan state in May 2020. The proposed model demonstrated the dynamicity of the network, enhanced the agent level performance, minimized the malicious information spread, and measured the response to the second stochastic information spread in the network.
Keywords: Systems thinking, Complexity theory, System dynamics, Organizational cybernetics, Stochastic one-median problem, Misinformation mitigation, COVID-19, Information diffusion delay, Agent-based model
Introduction
The complexities in monitoring, controlling, and analyzing the spread of so-called conspiracy theories, misinformation, disinformation, and fake news on social networks (in this research, we call malicious information) make it a challenging and NP-hard problem to solve. Many users in social networks have dynamic interactions, where the actions of the users impact both online and offline (“Robinhood, Reddit CEOs to Testify Before Congress on GameStop” 2021). For example, misinformation intends to mislead society during COVID-19. It has been challenging to track the traveling information across social networks, analyze the impacted user and communities, and measure the consequences of misinformation over time (“Robinhood, Reddit CEOs to Testify Before Congress on GameStop” 2021) (Wasson 2005). However, limiting the spread of misinformation in the context of COVID-19 is extremely important. The information may start from rumors spreading conspiracy theories and then quickly influence the social media network. The misinformation could distract the understanding of many online/offline communities and, later proven false, could bring harmful consequences for individuals and society over time (Shahi et al. 2021).
Moreover, to analyze the online/offline environments, we would need fast and automated response strategies. Over the last few years, many methods have been proposed to study the spread and limitation of misinformation between communities, individuals, and online/offline social networks. Authors in Shahi et al. (2021) proposed an exploratory study into the propagation and content of misinformation on Twitter. Likewise, other scholars studied limiting the spread of misinformation in social networks by adopting accurate information rather than the false information campaign on online social networks, as investigated in Budak et al. (2011). Also, misinformation spreads on social media, where the elements governing misinformation circulating among Facebook’s users consuming information related to scientific and conspiracy news, addressed by Vicario et al. (2016). However, optimizing the spread of misinformation is an NP-hard problem due to the structures of social networks (Budak et al. 2011). This analysis involves many variables like the behavior of the users and communities, information propagation across the social media networks, and the dynamicity of the reactions. Likewise, traditional graph theories such as the centrality and modularity methods fall short of identifying the focal information spreaders in online social media networks (Şen et al. 2016).
In this paper, we implemented a systematic model to enhance the analysis process in dynamic social networks. This research introduces advanced Systems Thinking model into the social network analysis. A systems design model can visualize or conceptualize any actions in the social network environment and perform a situational assessment of social network conditions. The major challenge in this multidisciplinary model is formulating, developing, and synthesizing solutions that can respond to user operational needs and constraints. Similarly, this systems design should evaluate and select the optimal solutions with acceptable risk to satisfy the social network stakeholders’ operational needs. Also, it could provide the best values, enhance the agent performance, observe the performance or the lack thereof, and analyze the contributory causes and effects in the social network (Wasson 2005).
For this research, we utilized the Organizational Cybernetic Approach (OCA) (Mann 2004) to control the communications between communities in online and offline social networks and the stochastic one-median problem (Ahituv and Berman 1988) to minimize the response time to any stochastic malicious information spread across the network. The resultant approach measures the performance of the operation level’s reaction to the information spread and better decision-making. Furthermore, the proposed model should select the optimal solutions that provide acceptable strategies to enhance the operational actions to respond to the misinformation on social media networks. In addition, this research makes several contributions to mitigating the COVID-19-related misinformation spread. In the first contribution, we determine the upper bound (worst case scenario) of the misinformation spreaders in dynamic online communities. The second contribution is to implement a procedure to evaluate the performance and availability of the agents interacting with online and offline social networks. The third contribution is to introduce a mathematical model to minimize the response time to COVID-19 misinformation spread on social networks and evaluate metrics that would reduce the agents’ time to respond to any new misinformation spread in networks.
The rest of the paper is organized as follows. Literature review in Sect. 2, Sect. 3 explains the solution strategy, Sect. 4 discusses the results, and Sect. 5 presents the conclusion and future work.
Related work
In this section, we survey the current state of the research relevant to systems thinking and model, agent-based models in social networks, and the operational levels methods applied to solve real-world problems.
Alassad et al. (Alassad et al. 2020) presented an agent-based and theoretical approach to applying systems thinking and modeling in social networks. Using a Twitter network, the authors implemented systems thinking methods to illustrate noncooperative actions from two organizations to influence online and offline environments. The agent-based model employed to study the dynamics of COVID-19 information spread (Rajabi et al. 2021), where Epstein’s hypothesis “coupled contagion dynamics of fear and disease” was used to explore fear-driven behavior adaptations and their impact on efforts to combat the COVID-19 pandemic. Similarly, the machine learning approaches applied to study and detect the online fake news and misinformation related to the COVID-19 pandemic (Bojjireddy et al. 2021), a multi-dimensional method implemented by organic the fake news. Likewise, social support, text mining, and media richness theories were employed to explore the different types of misinformation dissemination on social networks. The online rumor reversal model was introduced by Wang et al. (2021). The genetic algorithm-based rumor mitigation and precedence-based competitive cascade model propagated competing for rumor and counter-rumor cascades in online social networks. These models were used to find the minimal set of seed users for the counter-rumor.
Moreover, utilizing the agent-based models has advantages in detecting COVID-19-related misinformation on social media. Such models would control the complexity of the analysis and the costs of fact-checking or annotation over time. In addition, the agent-based models can control and scale up real-world experiments, and nonlinear dynamics can be introduced, which poses a significant problem in conventional experiments (Retzlaff et al. 2021). Also, agent-based models were used to investigate the formation of opinions in interacting communities and whether polarization or separation emerged from this interaction (Hegselmann and Krause 2002). Likewise, agent-based models can better explore the behavior of the users- and large-scale communities and construct formal models where the large-scale or global behavior is required to verify the model against the real-world phenomenon (Jones Jan. 2007).
Additionally, agent-based models study fear as an essential factor in users’ behavior during an epidemic, as investigated in Jones Jan. (2007). Finally, (Lorenz et al. 2021) used agent-based models to study the different behavioral outcomes from social theories, psychological theories, and empirical data that can be used to validate the model's results in the real world. The agent-based models were implemented in the social network (Steinbacher, et al. 2021), including different components that enable agents to make decisions, involve different environments, and adjust the rules/policies in real time.
Many other empirical studies introduced systems thinking and modeling methods as advanced classes of intelligence paths to solve many complex social network problems, as (Şen et al. 2016) explained. In this field, the Casual Feedback method presented in the paper (VanderWeele and An 2013) investigated some of the variables needed in complex systems modeling and analysis. Muchnik et al. (Muchnik et al. 2013) focused on implementing power laws in social networks and large-scale communities. Du et al. (Du et al. 2018) explained the boundary conditions approach in systems thinking and modeling. Control theory (Weng, et al. 2013) and information theory (Peng et al. 2017) are implemented to supplement the decision based on the game theories in social networks (Chan and McCarthy 2014), where authors stated that these combinations could bring optimized solutions and enable them to model different agent-based complex problems.
Furthermore, to optimize the decisions of the agent levels in real-time, many operational methods are available to model the stochastic incidents and the interactions between operation teams and the environments’ stochastic incidents in different areas. For example, how do we enhance the performance of the operation team in a fire department to respond to an accident, travel and clear the crash, and void the traffic during rush hours? How do we enhance the operation level to react to any shutdown in a telecommunication network and restore the service quickly to reduce the losses in the network? Hakimi (Hakimi 1964) proposed the -median location model to locate the optimal depots of the operation level when a particular set of failures occur in the infrastructure networks. In this research, the author minimized the shortest path between nodes and reduced the number of hubs in the network. Patterson et al. (Patterson 1995) proposed a relaxed -median model by allowing different service regions to overlap and reducing the loss of calls in a telecommunication network. Love et al. (Love et al. 1988) proposed a model to illustrate the interactions between operation levels, where the -median algorithm is represented as a bipartite graph.
On the other hand, Odoni (“Facility-Location Models”, in Location, Transport and Land-Use 2005) stated that the -median model could build a queuing situation affected by extended arc operations. However, Chan et al. (Chan 2005) suggested that this model becomes analytically complex when the number of operation centers goes beyond one location. In an alternative study, Ahituv et al. (Ahituv and Berman 1988) proposed a model to partition the network into smaller subnetworks, each capable of independent operation.
For this research, we are implementing the stochastic one-median problem to enhance the performance of the operation level in response to abnormal information spread in social networks. However, the unpredictability in the behaviors of the online users, the dynamics of the communities, and the massive growth in social networks over time increased the complexity of the analysis, which makes the above methods fall short in modeling the behavior of online communities. For this analysis, multidisciplinary approaches are needed to incorporate comprehensive strategies to analyze the local relationships among users and communications between communities over time and allocate all positive/negative feedback from the online users to online/offline environments. For this purpose, we proposed a systematic agent-based approach to enhance the communication between the online environment and the organization/operation level to reduce the spread of malicious information across the network, monitor/record the information flow among online communities/users over time, and responses to information spread in real-time.
Methodology
In this section, the Systems Thinking methods are applied to simplify the interactions in a dynamic social network.
Problem definition
Consider a social network consisted of the distinct nodes sets, and the set of edge (links) represented by directed node pair combinations going from community to community . Communities are associated with numerical values representing the number of intra edges () between communities and . represents the communities’ maximum rate of the malicious information spread , and is the proportion rate of operation level that can be monitored in the network.
With the complexities in social network analysis and the unpredicted behavior of online users and communities, this research should be able to track down the users’ actions, measure the agents' performance, and monitor the dynamic environment in real time. Given all the above and utilizing the systems thinking and operational methods, the challenge is to design and model a system able to simplify the social network interactions, minimize the malicious information spread between communities, enhance the performance of the operation level, provide the implementation level of service in monitoring the (offline) online social networks, and optimize the community selections that minimize the response time to any malicious information spread in .
Data collection
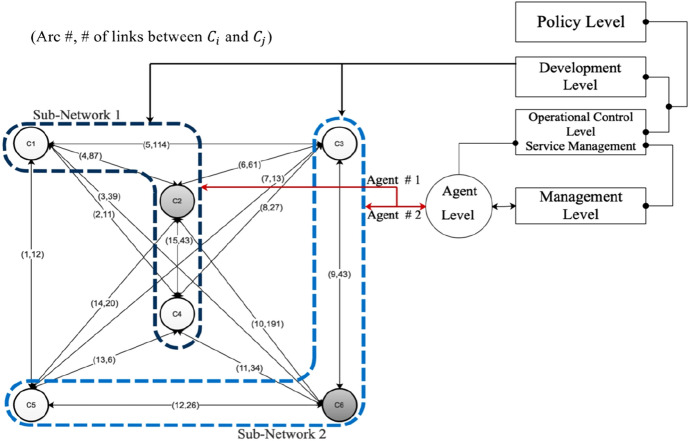
This research used a Twitter API and a Python script to collect posted tweets during the Covid-19 pandemic. For this purpose, we used Python libraries like Scarpy (Chan 2005) and Tweepy (Girvan and Newman 2002). Also, we obtained a preset list of co-hashtags related to different events on the Twitter Network. The collected co-hashtags network was connected to #MichiganProtest, #MiLeg, #Endthelockdown, and #LetMiPeopleGo hashtags from April 1st through May 20th, 2020 (Alassad et al. 2020). The behavior recorded polarized actions regarding COVID-19-related topics on Twitter, where some communities spread misinformation about the COVID-19 lockdowns in Michigan State. This dataset revealed 3,632 nodes with 352 communities using the Modularity method (Girvan and Newman 2002). The data collected resulted in a 16,383 Tweets network with 9,985 unique User Ids as shown in Fig. 1. The model focuses on the top five communities, as these were the communities that included the highest number of interactions between users. Figure 2 shows the Twitter network for the COVID-19 anti-lockdown protest in Michigan, where the top five communities with the highest number of users represent all other minor communities. Over the protest campaign from May 12th through May 15th, users on either side of the movements, pro-gun and pro-peace, posted tweets related to influence and boosting dissemination of their agenda analysis. It is worth mentioning here that the model's findings do not depend on the data sample size; the only change that would occur if we add more data or if we remove, for that matter, for this model, is the number of communities that change. As the number of communities changes, the interaction between the communities shown in Fig. 1 will change.
Fig. 1.
Organizational cybernetic approach
Fig. 2.

Twitter network for the COVID-19 anti-lockdown protest in Michigan State. through are the top five communities with the highest number of users, and represents all other small communities
Organizational cybernetic approach (OCA)
Organizational cybernetics is a systems thinking method that controls communication between systems and environments, including negative and positive feedback and unexpected behaviors from all users and communities in social network systems. It simplifies the analysis of the increased dynamicity in the entire system (Mann 2004), simultaneously recording changes in the behaviors of all parts of the system and the environment (Budak et al. 2011). OCA should help all levels monitor online social networks, perfectly optimize outcomes, and inject new inputs into the environment concerning the dynamic changes (outputs) and feedback from online social networks simultaneously.
The OCA is structured to communicate with the online environment and monitor, record feedback, and build strategies to enhance communication with the online/offline social settings, as shown in Fig. 1.
OCA includes different levels to implement goals like (developing and managing plans to limit the misinformation spread, assigning agents to interact with the social network environments and monitor the sources of the misinformation spread, evaluating the performance of the agents, and developing a new output strategy based on the environment's negative or positive feedback). Below we explain the different levels in the OCA’s structure as we explained the operation level in Sect. 3.3.1.
The management level is used to ensure fluency in the misinformation mitigation process. This level should send reports related to the mitigation processes, agents’ performance, and other related words to the control level.
The development level analyzes the core information received from the operational control level, management level, and social network environments.
The policy level should articulate the identity and purposes of the entire misinformation mitigation process and reflect the whole network’s strategy.
Operation level system (agent level)
This system is considered to be system one in OCA. It must be as accessible as possible to allow its elements to interact with their environments efficiently (Mann 2004). The operation level must maintain equity in monitoring significant communities across the network, considering factors such as reporting behaviors or posts in the network (Chan 2005). The operation level must always report to management and control levels after completing a response to any malicious information post or before starting a new action. Also, this level needs to monitor processes to respond to any negative information spread continuously. In addition, the monitoring process and the arrangements with each malicious information spread should be in a first-in-first-out (FIFO) order.
Moreover, the monitoring process achieved at this level can be broken down into different operation elements and shifts of working hours based on fixed time frames. In this research, the agent level in OCA would not travel between communities.
Still, the purpose is to reflect in the real-world (moderators, automated processes, etc.) to help find and highlight the critical communities in a complex social network structure. Any component of the operation level may interact with the network differently, such as sharing information between different levels or blocking malicious users’ accounts from the networks in real time.
Stochastic one-median problem
This operational method helps with stochastic information spreads in dynamic networks where the operation and the response to the malicious information may be undetected. This method is helpful when customers use the network more than physically interacting with the offline environment or online social networks (Ahituv and Berman 1988).
In this research, we utilized the stochastic one-median problem to enhance the performance, maximize the operation levels' efforts, and help select the best combinations of communities for the best monitoring process. The stochastic monitoring process can be implemented using the following model, where the expected response time to abnormal behaviors is measured in Eq. (1).
| 1 |
| 2 |
| 3 |
| 4 |
is the sum of the mean- queuing-delay and the mean response time as shown in Eq. (2). Equation (3) is to define , where is the community in the network, is the rate of the proportion monitoring process, is the mean total response time (starting from the first moment the abnormal behavior is detected), is the second stochastic moment of the total response time to any new information spread. Equation (4) is to define , where is the number of communities in the network, represents the maximum rate of malicious information spread of the communities , and is the shortest path between community , and community .
Results
We used the Michigan dataset for this research to test the model's performance. The main reason was related to the real-time actions among the online and offline communities and the importance of this protest during the COVID-19 pandemic. Preliminary analysis revealed that users from either side of the spectrum were engaged in an online tug of war and conducting influence operations to promote their agenda. While armed protesters posted tweets to influence the network to maximize the armed participants joining the protest, users from the other side of the spectrum tweeted to stop such a movement and reminded participants to use more peaceful options. To simplify the analysis, we chose to focus on the top five communities, as these were the communities with the highest number of users. Also, the model will represent all other small communities in one node to include any actions from (to) these communities in the solution procedure.
In addition, the policy level in OCA is assumed to use only two monitoring (operation) centers in the network (), where each center will monitor less than (< 55%) of the entire network.
The model focuses on the top five communities, as these were the communities that included the highest number of interactions between users. It is worth mentioning here that the model's findings do not depend on the data sample size. This means the possibilities of information exchanges will increase or decrease based on the difference in the data sample. Other than that, the model that has been developed will remain unaffected, the time it takes to run the model remains unaffected, the conclusion remains unaffected, and everything remains unaffected after changing the data. The only change is that the graph you look at in Fig. 1 becomes more or less connected. In addition, to simplify the network representation, the model will consider/represent all small communities in one node, accounting for any behavior or misinformation spread source from these small communities, where the model will not change any linking behavior.
Experimental results
The results in this section were based on multiple steps explained as follows:
Step 1: Clustering the network into smaller communities based on the Modularity method (Girvan and Newman Jun. 2002) as presented in Fig. 2.
Step 2: Measuring the intra-edges between all six communities presented in Fig. 2, representing the values as shown in Fig. 1.
Step 3: Measuring the maximum malicious information spread (if all users in the community were spreading malicious action) proportion rate (), for all six communities as shown in Fig. 1.
Step 4: Since we assumed (), this step divides the network into two sub-networks based on the values shown in Fig. 1. Monitoring Center number one ( is for sub-network one including (,,), and Monitoring Center number two ( is for sub-network two including (,,). Each operation level (monitoring center) will cover less than 55% of the entire network as a maximum spreading rate.
Step 5: Apply the stochastic one-median model presented in Sect. 3.3.2. The outcomes will provide possible solutions to minimize the response time from each monitoring center.
Table 1 shows nine possible answers, where the best communities’ combinations allocation solution to reduce the response time to information spread would be at and . These two communities are responsible for large amounts of information flow from (to) other communities in the network. However, the solution procedure would ignore the communities that received the negative response time (infinity).
Table 1.
Possible solution combinations
| (hours) | |
|---|---|
| & | 7.699 & 0.618 |
| & | 7.699, & 1.399 |
| & | 7.699 & 1.944 |
| & | & 0.618 |
| & | & 0.618 |
| & | & 1.399 |
| & | & 1.399 |
| & | & 1.944 |
| & | & 1.944 |
Moreover, the outcomes show the possible community combinations solutions for both agent levels to minimize the misinformation spread response time. Table 1 presents sorted nine possible solutions measured, where the best communities’ combinations in the network for both agent levels to monitor were identified. In addition, based on the outcomes, the model assigned agent level #1 to monitor and respond to misinformation spread in and agent level #2 should respond to misinformation spread in . The agents could minimize the response time and limit COVID-19-related misinformation when they first handle the information in these communities. These two communities include many users and are responsible for a high volume of information units exchanged from (to) other communities in the network, as measured in step 2.
The model didn’t select these locations due to their scales and position in the network structure. However, suppose the policy level allocates monitoring centers to these communities based on the calculation. In that case, they cannot perform any response to malicious information spread at other locations due to the heavy number of users and community activities. For example, in case the policy level in OCA assigns agents to handle information spread in communities , & , or any other combinations mentioned in Table 1, then the agents will fall behind due to local solutions and the communities’ structures. All the calculations are provided in Appendix A.
In summary, the research's theoretical and practical implications include a multi-disciplinary model integrating the operation methods and the organization's cybernetic methods to reduce misinformation in social media network analysis. Also, the model can monitor the changes in the communities’ behavior, measure the agents' performance, and adjust the mitigation strategies in real time. Likewise, the model can handle complex social network analysis regardless of the size and number of network users. Similarly, the proposed model would enhance the managers' decisions and optimize their resource allocation based on the size of the social network structure.
Conclusion
The recent challenges in social network analysis projected the necessity to use multidisciplinary approaches such as advanced Systems Thinking and operational methods. In this research, the main challenges were to model a systematic agent-based model to reduce the spread of malicious information in dynamic real-world social networks. Also, in this research, we modeled the stochastic one-median problem to enhance the agent's performance and minimize the response time to any malicious information spread on a Twitter network. Likewise, a dynamic monitoring protocol could improve the network performance, reduce the response time, optimize the resources, help to understand the complex structure of the social networks and create effective agents to mitigate misinformation spread in social networks.
For future work, we will study the intra-edges’ reliability and measure the increase/decrease of information spread in dynamic networks. This will allow us to use different delay time assumptions and build an efficient frontier to illustrate the performances of the operation level. Also, we plan to model a stochastic social network analysis where communities in both online and offline environments are experiencing multi malicious information spread between the communities at the same time.
Acknowledgements
This research is funded in part by the U.S. National Science Foundation (OIA-1946391, OIA-1920920, IIS-1636933, ACI-1429160, and IIS-1110868), U.S. Office of the Under Secretary of Defense for Research and Engineering (FA9550-22-1-0332), U.S. Office of Naval Research (N00014-10-1-0091, N00014-14-1-0489, N00014-15-P-1187, N00014-16-1-2016, N00014-16-1-2412, N00014-17-1-2675, N00014-17-1-2605, N68335-19-C-0359, N00014-19-1-2336, N68335-20-C-0540, N00014-21-1-2121, N00014-21-1-2765, N00014-22-1-2318), U.S. Air Force Research Laboratory, U.S. Army Research Office (W911NF-20-1-0262, W911NF-16-1-0189, W911NF-23-1-0011), U.S. Defense Advanced Research Projects Agency (W31P4Q-17-C-0059), Arkansas Research Alliance, the Jerry L. Maulden/Entergy Endowment at the University of Arkansas at Little Rock, and the Australian Department of Defense Strategic Policy Grants Program (SPGP) (award number: 2020-106-094). Any opinions, findings, and conclusions or recommendations expressed in this material are those of the authors and do not necessarily reflect the views of the funding organizations. The researchers gratefully acknowledge the support.
Biographies
Mustafa Alassad
After graduating with his master’s degree in systems engineering from UA Little Rock in 2017, Dr. Alassad chose to continue in his education in this field and enrolled in the Ph.D. program. He was introduced to COSMOS in the Spring of 2018. His research interests include Operational Research, Community Clustering, Multi-Agents Game Theory, Decomposition optimization, and Focal Structures analysis with applications to social networking focusing on techniques to determine an intensive set of users spreading conspiracy theories in online social networks.
Muhammad Nihal Hussain
Is a Lead Data Scientist at Equifax working at the intersection of entity resolution and fraud detection. Previously, worked as a postdoctoral fellow at COSMOS lab at University of Arkansas at Little Rock. His research interest include multi-platform disinformation campaigns, cross-media information diffusion, crowd manipulation strategies on content-centric social media platforms (Blogs and YouTube). During his tenure at COSMOS, Dr. Hussain studied several online campaigns ranging from analyzing content-centric platforms to extract opinions and adversarial narrative around NATO’s various events and exercises to understanding role of individual social media platforms in a complex multi-platform campaign, published 6 book chapters, 2 journal articles, over 30 peer-reviewed articles and delivered tutorials and invited talks on blogosphere analysis at SBP-BRiMS, NATO TIDE Sprint and “Social media course” organized by NATO STRATCOM COE in Riga, Latvia. He currently volunteers as a peer reviewer for several ACM, IEEE, IARIA, Springer and Elsevier journals, and serves on the program and organizing committee for SBP-BRiMS conferences and DEVIANCE workshops since 2020.
Nitin Agarwal
Obtained B-Tech from Indian Institute of Information Technology with university-wide second rank in 2003 and Ph.D. from Arizona State University with outstanding dissertation recognition in 2009. He is presently the Jerry L. Maulden-Entergy Endowed Chair and Distinguished Professor of Information Science at the University of Arkansas – Little Rock and founding director of the Collaboratorium for Social Media and Online Behavioral Studies (COSMOS). At COSMOS, he is leading projects with a combined funding of over $20 million from an array of U.S. federal agencies including Department of Defense, DARPA, Department of State, National Science Foundation and plays a significant role in the long-term partnership between UA Little Rock and the Department of Homeland Security. He has published 10 books and over 200 articles in top-tier peer-reviewed forums including the NATO’s Defense StratCom Journal, with several best paper awards and nominations. He was recognized as one of 'The New Influentials: 20 In Their 20 s' by Arkansas Business in 2012. He was recognized with the University-wide Faculty Excellence Award in Research and Creative Endeavors by UALR in 2015. Dr. Agarwal received the Social Media Educator of the Year Award at the 21st International Education and Technology Conference in 2015. In 2017 the Arkansas Times featured Dr. Agarwal in their special issue on "Visionary Arkansans”. Dr. Agarwal was nominated as International Academy, Research and Industry Association (IARIA) Fellow in 2017, an Arkansas Academy of Computing (AAoC) Fellow in 2018, and an Arkansas Research Alliance (ARA) Fellow in 2018. He was recognized with the student advocate award in 2019 by UALR. His research aims to push the boundaries of our understanding of digital and cyber social behaviors that emerge and evolve constantly in the modern information and communication platforms. He developed publicly available social media analysis tools (Blogtracker and YouTubeTracker), assisting various defense agencies worldwide. His work has been covered by local, national, and international media including Bloomberg, US News, KUAR, Arkansas Business, Arkansas Times, Arkansas Democrat Gazette, and many others. Over the last several years, Dr. Agarwal has spoken at various public and professional, national and international forums such as the NATO’s StratCom COE (Riga, Latvia), DARPA, US Department of State, US Naval Space and Warfare (SPAWAR), US Pentagon’s Strategic Multilevel Assessment groups, US National Academies of Sciences Engineering and Medicine, US Office of the Director of National Intelligence, Facebook Asia Pacific HQ, Twitter Asia Pacific HQ, US Embassy in Singapore, Singapore Ministry of Communication and Information, NATO Senior Leadership meetings. He is a member of IEEE. Visit https://profiles.ualr.edu/na10/ for more details.
Appendix A
Here we list the set of deterministic assumptions required for the solution procedure.
The operation level response time to any malicious information spread is deterministic () messages/hour.
The maximum time required to detect, response, and finish any malicious information spread case is normally distributed case/hours.
The second and new stochastic malicious information spread is deterministic.
The communities are active in the network over time and do not disappear.
The communities are assumed to be either spreading malicious information or not.
This step is associated with two assumptions (=55 and =2).
Sub-Network 1: includes communities , ,
| Community # 1 () | |
|---|---|
| Community # 2 () | |
| Community # 4 () | |
Sub-Network 2: includes communities , , .
| Community # 3 () | |
|---|---|
| Community # 6 () | |
| Community # 5 () | |
Funding
National Foundation for Science and Technology Development,OIA-1946391
Footnotes
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- “Facility-Location Models,” in Location, Transport and Land-Use, Springer-Verlag, 2005, pp. 21–119.
- “Robinhood, Reddit CEOs to Testify Before Congress on GameStop.” [Online]. Available: https://www.investopedia.com/robinhood-reddit-ceos-to-testify-in-congress-on-gamestop-gme-5112714. [Accessed: 16-Feb-2021].
- N. Ahituv and O. Berman, Operations Management of Distributed Service Networks. 1988.
- M. Alassad, M. N. Hussain, and N. Agarwal, “How to Control Coronavirus Conspiracy Theories in Twitter? A Systems Thinking and Social Networks Modeling Approach,” in 2020 IEEE International Conference on Big Data (Big Data), 2020, pp. 4293–4299
- S. Bojjireddy, S. A. Chun, and J. Geller, “Machine Learning Approach to Detect Fake News, Misinformation in COVID-19 Pandemic,” ACM Int. Conf. Proceeding Ser., pp. 575–578, 2021.
- C. Budak, D. Agrawal, and A. El Abbadi, “Limiting the spread of misinformation in social networks,” Proc. 20th Int. Conf. World Wide Web, WWW 2011, pp. 665–674, 2011.
- Chan Y. “Measuring Spatial Separation: Distance, Time, Routing, and Accessibility”, in Location. Transport and Land-Use: Springer-Verlag; 2005. pp. 120–209. [Google Scholar]
- Chan Y, McCarthy J. Game-Theoretic paradigms in collaborative research: part 2-experimental design. Int J Soc Syst Sci. 2014;6(4):348–364. doi: 10.1504/IJSSS.2014.066644. [DOI] [Google Scholar]
- Del Vicario M, et al. The spreading of misinformation online. Proc Natl Acad Sci. 2016;113(3):554–559. doi: 10.1073/pnas.1517441113. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Du B, Lian X, Cheng X. Partial differential equation modeling with Dirichlet boundary conditions on social networks. Bound Value Probl. 2018;2018(1):1–11. doi: 10.1186/s13661-018-0964-4. [DOI] [Google Scholar]
- Even S, Itai A, Shamir A. On the complexity of timetable and multicommodity flow problems. SIAM J Comput. 1976;5(4):691–703. doi: 10.1137/0205048. [DOI] [Google Scholar]
- Girvan M, Newman MEJ. Community structure in social and biological networks. Proc Natl Acad Sci. 2002;99(12):7821–7826. doi: 10.1073/pnas.122653799. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Hakimi SL. Optimum locations of switching centers and the absolute centers and medians of a graph. Oper Res. 1964;12(3):450–459. doi: 10.1287/opre.12.3.450. [DOI] [Google Scholar]
- R. Hegselmann and U. Krause, 2002 “Opinion dynamics and bounded confidence models, analysis, and simulation *,” J. Artifical Soc. Soc. Simul., vol. 5, no. 3,.
- Jones E. Generative social science: studies in agent-based computational modeling. J Ecol Anthropol. 2007;11(1):76–80. [Google Scholar]
- Lorenz J, Neumann M, Schröder T. Individual attitude change and societal dynamics: computational experiments with psychological theories. Psychol Rev. 2021;128(4):623. doi: 10.1037/rev0000291. [DOI] [PubMed] [Google Scholar]
- R. Love, J. Morris, and G. Wesolowsky, “Facilities location,” 1988.
- C. J. H. Mann, Systems Thinking – Creative Holism for Managers, vol. 33, no. 8. 2004.
- Muchnik L, et al. Origins of power-law degree distribution in the heterogeneity of human activity in social networks. Sci Rep. 2013;3(1):1–8. doi: 10.1038/srep01783. [DOI] [PMC free article] [PubMed] [Google Scholar]
- T. S. Patterson, “Dynamic Maintenance Scheduling for a Stochastic Telecommunication Network: Determination of Performance Factors.,” Air Force Institute of Technology Air University, 1995.
- Peng S, Yang A, Cao L, Yu S, Xie D. Social influence modeling using information theory in mobile social networks. Inf Sci (ny) 2017;379:146–159. doi: 10.1016/j.ins.2016.08.023. [DOI] [Google Scholar]
- Rajabi A, Mantzaris AV, Mutlu EC, Garibay OO. Investigating dynamics of COVID-19 spread and containment with agent-based modeling. Appl Sci. 2021;11(12):5367. doi: 10.3390/app11125367. [DOI] [Google Scholar]
- Retzlaff CO, Ziefle M, Calero Valdez A. “The history of agent-based modeling in the social sciences”. Lect Notes Comput Sci. 2021;12777:304–319. doi: 10.1007/978-3-030-77817-0_22. [DOI] [Google Scholar]
- Şen F, Wigand R, Agarwal N, Tokdemir S, Kasprzyk R. Focal structures analysis: identifying influential sets of individuals in a social network. Soc Netw Anal Min. 2016;6(1):17. doi: 10.1007/s13278-016-0319-z. [DOI] [Google Scholar]
- Shahi GK, Dirkson A, Majchrzak TA. An exploratory study of COVID-19 misinformation on Twitter. Online Soc Networks Media. 2021;22:100104. doi: 10.1016/j.osnem.2020.100104. [DOI] [PMC free article] [PubMed] [Google Scholar]
- Steinbacher M, et al. 2021 “Advances in the agent-based modeling of economic and social behavior”. SN Bus Econ. 2021;17(1):1–24. doi: 10.1007/s43546-021-00103-3. [DOI] [PMC free article] [PubMed] [Google Scholar]
- VanderWeele TJ, An W. “Social Networks and Causal Inference”, in Handbook of causal analysis for social research. Dordrecht: Springer; 2013. pp. 353–374. [Google Scholar]
- Wang X, Li Y, Li J, Liu Y, Qiu C. A rumor reversal model of online health information during the Covid-19 epidemic. Inf Process Manag. 2021;58(6):102731. doi: 10.1016/j.ipm.2021.102731. [DOI] [PMC free article] [PubMed] [Google Scholar]
- C. Wasson, System analysis, design, and development: Concepts, principles, and practices. 2005.
- L. Weng et al., “The role of information diffusion in the evolution of social networks,” in Proceedings of the ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, 2013, vol. Part F128815, pp. 356–364.