Abstract
The recent emergence of monkeypox poses a life-threatening challenge to humans and has become one of the global health concerns after COVID-19. Currently, machine learning-based smart healthcare monitoring systems have demonstrated significant potential in image-based diagnosis including brain tumor identification and lung cancer diagnosis. In a similar fashion, the applications of machine learning can be utilized for the early identification of monkeypox cases. However, sharing critical health information with various actors such as patients, doctors, and other healthcare professionals in a secure manner remains a research challenge. Motivated by this fact, our paper presents a blockchain-enabled conceptual framework for the early detection and classification of monkeypox using transfer learning. The proposed framework is experimentally demonstrated in Python 3.9 using a monkeypox dataset of 1905 images obtained from the GitHub repository. To validate the effectiveness of the proposed model, various performance estimators, namely accuracy, recall, precision, and F1-score, are employed. The performance of different transfer learning models, namely Xception, VGG19, and VGG16, is compared against the presented methodology. Based on the comparison, it is evident that the proposed methodology effectively detects and classifies the monkeypox disease with a classification accuracy of 98.80%. In future, multiple skin diseases such as measles and chickenpox can be diagnosed using the proposed model on the skin lesion datasets.
Keywords: Monkeypox, Blockchain, IPFS, Machine learning, Transfer learning
Introduction
The expansion of pandemics and epidemics in today’s hyper-connected globe is a concern brought on by the intricate interactions among several causes, notably ecological, environmental, and socioeconomic issues [1]. While the world is severely ruptured by the succession of COVID-19 pandemic waves, the recent emergence of the monkeypox outbreak has raised serious health concerns owing to its unprecedented spread across many countries [2]. Monkeypox is a highly contagious zoonotic disease that belongs to the Orthopoxvirus genus family and transmits to humans by touching or consumption of an infected animal [3]. Although the virus has been exceptionally prevalent since 1970, and the preponderance of cases was reported in regions of Central and West Africa [4]. In 2022, the outbreak of monkeypox was reiterated in the United Kingdom (UK), originating from a British resident with a Nigeria traveling history [5]. The monkeypox virus is predominant in 12 endemic states, as reported by the World Health Organization (WHO); nevertheless, occurrences of monkeypox have recently been confirmed in 12 non-endemic states [6].
Recent estimates from the Centers for Disease Control and Prevention (CDC) claim that there have been over 59,606 cases of monkeypox worldwide, with 19 deaths as of the time of writing [7]. The non-endemic states notified nearly 200 confirmed instances of the monkeypox virus as of May 2022. The predominant clinical manifestations of the monkeypox virus include severe headache, fever, backache, muscle aches, rashes, enlarged lymph nodes, and shivering. Nevertheless, these signs and symptoms are not specific to a particular disease, making a definite diagnosis and treatment of monkeypox, a challenging task for practitioners.
Owing to the emergence of such pandemics, the number of patients is significantly rising, thereby making patients’ health record management a challenging task. Electronic health records (EHR) transform traditional health management tasks in a multitude of ways [8]. EHR keeps medical records in a digital format that is in line with the care and can be instantaneously accessed and securely disseminated across various entities. However, several concerns about security and privacy related to user health data reduce the adoption of EHR in any healthcare framework design as the information stored in EHR is highly sensitive [9]. Blockchain, the new giant of Industry 4.0, has attracted massive attention from the industry and academic community and has the potential to give a new dimension to the healthcare industry [10]. Blockchain optimizes health record management tasks by providing unprecedented computational efficiency and maintaining trust. Blockchain technology steers to ensure the privacy of health data because of various key features including seamless distributed storage, immutability, authorization, accountability, and many more [11]. Blockchain is a distributed ledger that typically relies on the underlying smart contracts concept which enforces various constraints for users and healthcare professionals for accessing sensitive information.
Driven by the prevalence of emerging blockchain technology across numerous industries, this study aims to design a secured blockchain-enabled healthcare monitoring system using transfer learning. The envisioned solution is expected to circumvent the security challenges of traditional healthcare solutions and assist the healthcare professionals in identifying and classifying monkeypox cases and maintaining the users’ health information. Specifically, the significant contributions of the presented research are highlighted as follows:
Leveraging blockchain to facilitate electronic health records management, accessibility, and data sharing operations using smart contracts and interplanetary file system (IPFS).
A model based on transfer learning is utilized to retrieve the information related to the monkeypox from the image dataset.
Finally, an extensive empirical investigation is carried out to corroborate our presented approach using blockchain and transfer learning.
The rest of the paper is organized into different sections. Section 2 provides the state-of-the-art works outlined by previous researchers in the healthcare domain. The proposed methodology for early detection of monkeypox is presented in Sect. 3. Section 4 discusses the experimental setup and relevant results of the proposed methodology. Finally, the presented work is summarized in Sect. 5 with some future inferences.
Related works
This section presents an overview of state-of-the-art research contributions in machine learning-based decision-support techniques and blockchain-inspired healthcare systems. Numerous researchers and industry experts have utilized the potential of machine learning and deep learning architectures for accurate prediction and analysis with varying mechanisms to ensure the security and privacy of user data. Relying on these perspectives, we categorized the pertinent work into two subsections, described below.
Machine learning in healthcare
Intelligent healthcare systems have aided in the development of efficacious solutions. In the past few decades, intelligent systems based on machine learning and deep learning have been explored in various healthcare applications. Owing to the high prevalence of these techniques in healthcare applications, we explore the related research in this subsection. In [12], the authors used pre-trained models over the Monkeypox Skin Lesion Dataset (MSLD). The study found that ResNet50 achieved the highest accuracy of 82.96%, followed by VGG16 and an ensemble system (combined ResNet50 and VGG16 with InceptionV3), which achieved overall accuracies of 81.48 and 79.26%, respectively. Although this was the first study to analyze the dataset, the evaluation metrics could still be improved. Further, the authors failed to apply any hyper-parameter tuning methods to improve the accuracy results. In their research on the MSLD dataset, Gairola et al. [13] employed different ensemble systems that combined AlexNet and VGG16 with a Naive-Bayes classifier and GoogLeNet and VGG16 with a Random Forest classifier. Both ensembles yielded accuracies of 95.55%. However, the study did not mention the optimizers utilized to train the deep models. Authors in [14] employed SVM and K-NN machine learning techniques, along with transfer learning deep models like ResNet50 and Visual Transformer (ViT). The study found that the Visual Transformer was the best-performing model, achieving an accuracy of 93% and an F1-score of 0.92. However, the authors did not assess the AUROC score for the models. Uzun Ozsahin et al. [15] collected images of monkeypox and chickenpox by combining the MSLD dataset with publicly accessible case reports. They utilized a 9-layered CNN and other pre-trained deep learning models such as AlexNet, VGG16, and VGG19. The CNN model attained outstanding test accuracy of 99.6% and a weighted average precision, recall, and F1 score of 0.99. Likewise, similar studies were conducted by authors in [16–20]. A comparative summary of related works is presented in Table 1.
Table 1.
A comparative summary of related works
| Reference | Dataset | Approach | Accuracy (%) | F1-score | Classes |
|---|---|---|---|---|---|
| [12] | Monkeypox skin lesion dataset (MSLD) | ResNet50 | 82.96 | 0.84 | 2 |
| [13] | MSLD | AlexNet & VGG16 using NB | 95.55 | 0.952 | 2 |
| [14] | MSLD | Visual transformer (ViT) | 93 | 0.92 | 2 |
| [15] | MSLD and publicly available case reports | 9-layered CNN | 99.6 | 0.99 | 2 |
| [16] | MSLD | ResNet50 | 94 | 0.93 | 2 |
| [17] | MSLD | MobileNetV2 | 91.11 | 0.9 | 2 |
| [18] | Monkeypox-dataset | Modified VGG16 | 97 | 0.97 | 2 |
| [19] | Monkeypox skin image dataset | Ensemble system | 83 | 0.71 | 6 |
| [20] | Collected through web-scraping | VGG16 | 96 | 0.92 | 4 |
| [25] | Monkeypox-dataset | Ensemble system | 87.13 | 0.854 | 4 |
| [26] | Monkeypox-dataset | Ensemble system | 84.2 | 0.842 | 4 |
| [27] | Monkeypox skin images dataset (MSID) | GoogLeNet | 98.8 | 0.764 | 2 |
| [28] | MSID | MobileNetV2 | 98.25 | 0.9825 | 2 |
| [29] | MSID | modified denseNet-201 | 98.91 | 0.9891 | 4 |
| [30] | Monkeypox skin image dataset | EfficientNetB3 | 87 | 0.9 | 6 |
| Proposed | MSLD | Modified ResNet50 | 98.8 | 0.988 | 2 |
Blockchain-enabled healthcare monitoring systems
In recent years, blockchain-based security solutions have attracted significant interest due to their ability to offer robust security for the storage and exchange of data with the least computation. Further, a multitude of blockchain variations, including private and public blockchains, has been explored in the healthcare industry [21]. This subsection explores several essential characteristics of blockchain-assisted health systems, as well as current relevant research. The very first proposal for a blockchain-enabled system to distribute and maintain health records was proposed by Azaria et al. [22]. Though the proposed work was not validated, and it also did not take into account the integration of multiple sources. Nguyen et al. [23] designed a blockchain-based secured medical cyber-physical system with ResNet improvised classification model. The presented framework was demonstrated in a simulated environment. The experimental results revealed the improved performance of the proposed model compared to alternative approaches. However, the utilization of hyper-parameter tuning techniques for performance improvement was not considered as a part of their proposed solution. A privacy-preserving critical response management approach that reacts to a patient’s emergency state was proposed by Yu et al. [24]. In addition, the suggested solution was entirely reliant on a central third party. However, the failure of the entire system lies in the event of system overloading.
After conducting an extensive literature review in the healthcare domain, several research gaps have been identified:
Researchers have not explicitly studied the assessment of monkeypox prediction in a real-time scenario.
The majority of research carried out in the current work is restricted to the use of traditional deep-learning techniques.
The inclusion of blockchain technology for secured data management is an additional component that has been lightly investigated in past research.
The existing work failed to provide real-time processing due to the embedded computation overhead of blockchain. Therefore, an effort has been made to utilize smart contracts to automate the complete process.
Proposed framework
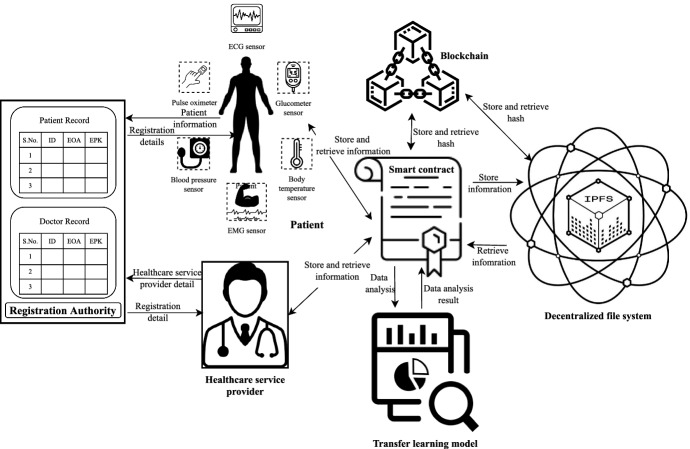
This section presents the working of the proposed blockchain-enabled health monitoring system for the early detection of monkeypox disease. Figure 1 illustrates the basic working of the proposed architecture with the communication links between different entities. The complete flow of designed work is divided into the following phases:
In the initial phase, users register themselves to the smart contract, including patients and health service providers. Upon successful registration, the registration authority stores their personal information and generated key-pair.
Prior user authentication is a crucial step in ensuring the security and privacy of data stored on the blockchain and IPFS. Authentication confirms the identity of a user attempting to access the system and grants or denies access accordingly.
Once the user has been successfully authenticated, the system moves on to the next phase, which involves data analysis and model learning. This phase is critical in gaining insights and knowledge from the collected data.
In the fourth phase of the system, the smart contract is responsible for storing the encrypted transaction data from the authenticated user along with the analyzed results to the IPFS. Once the encrypted transaction data and analyzed results are stored in IPFS, a unique hash string is returned by IPFS. This hash string is used to identify and access the stored information. By using the hash string to identify and access the stored information, the system provides a secure and tamper-proof method for storing and retrieving data. This ensures that the data remain confidential and cannot be tampered with by unauthorized parties.
In the system, after the hash string is returned by IPFS in the fourth phase, the generated hash values are stored in a blockchain. By storing the hash values in the blockchain, the system provides a permanent record of the data that has been stored in IPFS
Our proposed architecture comprises several basic building blocks, and the working of each component is explained in detail in the following subsection.
Fig. 1.
Proposed system model
Blockchain framework
In the study, we have considered a public blockchain environment with the similar configuration setting as Ethereum. The proposed approach considers both patients and doctors as Ethereum users, which means that they can utilize Ethereum’s functionalities to interact with the smart contract. The Ethereum blockchain allows users to execute smart contracts, which are self-executing programs that automatically facilitate the negotiation and execution of the terms of a contract. Each entity, i.e., the patient and the doctor, must register themselves as an Externally Owned Account (EOA) under a smart contract to become a recognized user.
An EOA is a type of account in Ethereum that is controlled by a private key, which is used to digitally sign transactions that the user wants to send to the network. This private key is unique to each entity and is only known to them, thereby providing a secure means of authentication. When registering as an EOA, each entity generates its unique Ethereum Address (EA) that serves as its user identity. The EA is a 42-character string of letters and numbers that is used to receive and send funds and interact with smart contracts. It is important to note that the EA is unique to each user and is publicly visible on the blockchain, but it does not reveal the user’s actual identity.
Once an entity has registered as an EOA and generated its EA, it can invoke an eligible function on the smart contract by sending a transaction to the blockchain using its private key. The smart contract processes this transaction and executes the corresponding function, thereby allowing the user to interact with the system. This approach provides a secure and decentralized way of accessing healthcare data and services while ensuring that only authorized users are able to access the system.
Similar to [31], elliptic curve key generation is used to generate the public–private key pair for each Ethereum user. Elliptic curve cryptography is a public-key cryptography that is based on the mathematics of elliptic curves over finite fields. We have considered a specific elliptic curve that is the secp256k1 curve, which is defined by the equation over a finite field where the generate key size is 256 bits. In the elliptic curve cryptography, an elliptic curve is defined over the finite field , where is a large prime number and E represents the integer points on the curve. The curve has a generator point, denoted as , which generates other points on the curve using elliptic curve point multiplication. To generate a public–private key pair, a random integer is securely generated as the private key. The respective public key is calculated as , where the multiplication is performed using the elliptic curve point multiplication method. This method has a time complexity of and is computationally efficient. The resulting point on the curve is the public key, which is shared publicly, while the private key is kept secret. This key pair is used to sign transactions and messages, verify digital signatures, and authenticate users on the Ethereum blockchain. For a user , its corresponding public and private keys are represented by and , respectively.
In the system, the smart contract is recognized by its corresponding Contract Account (CA). The smart contract is created by the contract owner, who writes the conditions and functionality that will be executed by the smart contract. The smart contract is then deployed on the Ethereum blockchain, which involves sending a transaction to the network that creates the smart contract and assigns it an address. Once the smart contract has been successfully deployed, a copy of the smart contract is stored on each Ethereum node, which is a computer that runs the Ethereum software and helps maintain the network. The Ethereum Virtual Machine (EVM) is then utilized to execute the required functionality of the smart contract. The EVM is a virtual machine that runs on each Ethereum node and is responsible for executing smart contract code in a secure and deterministic way.
Each action performed by the smart contract is published on the blockchain, which allows for the transparency of information and services. This means that every transaction that interacts with the smart contract, such as registering a user or storing data on IPFS, is recorded on the blockchain and can be viewed by anyone. This provides a transparent and auditable system, as all parties can view the actions performed by the smart contract and ensure that the system is functioning as intended. The use of a smart contract provides additional security to the system, as the code is executed automatically and without the need for intermediaries or third-party services. This reduces the risk of errors or manipulation of the system, as all actions are performed in a transparent and automated manner.
One of the other important processes is block validation. When a new block is created, it must be validated by the network’s nodes to ensure that it follows the rules and protocols of the Ethereum blockchain. The process of validating a block involves several steps, including verifying that the transactions in the block are valid, ensuring that the block meets the network’s consensus rules, and confirming that the miner who created the block has the right to do so. Once a block is validated, it is added to the blockchain and becomes part of the immutable ledger of Ethereum transactions. The traditional proof mechanism used in Ethereum blockchain is the Proof-of-Work (PoW) consensus algorithm. However, the PoW algorithm has some drawbacks that make it less efficient in terms of computational complexity and energy consumption. For instance, the PoW algorithm requires a significant amount of computational work to validate transactions, which results in high energy consumption and computational costs. This makes it less suitable for applications that require high throughput, low latency, and low transaction costs. To reduce the added computational complexity of the PoW algorithm, we have adopted Proof of Stake (PoS) algorithm. The PoS algorithm, for example, relies on validators to stake their own cryptocurrency as collateral to validate transactions. Validators are randomly selected to validate transactions based on their stake, which incentivizes them to act honestly and validate transactions accurately. This reduces the computational complexity and energy consumption of the network, as validators do not need to solve complex mathematical problems to validate transactions.
Registration authority
The registration authority is an entity used to collect and store the basic details of patients and hospital service providers such as doctors, surgeons, and nurses. Each user can register to a smart contract only one time, and different roles are assigned to them based on their functionality. Smart contract generates a unique EA for each user. After smart contract registration, their information is stored by the registration authority for all future reference. Registration authority provides a unique identity to each entry. Besides the user ID, the registration authority also collects other relevant information. For patients, this information includes patients’ names, addresses, gender, age, etc., whereas for health service providers, information includes name, qualification, address, etc. Algorithm 1 shows the step-wise step procedure of user registration with the computational complexity of .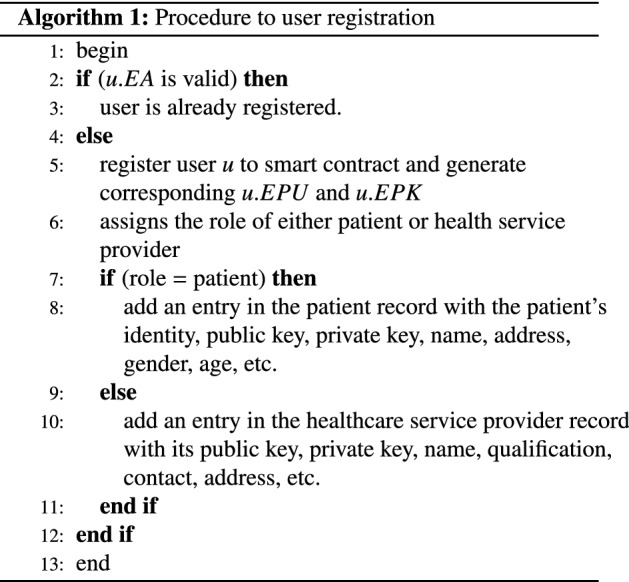
Smart contract
The smart contract is the main component and plays a significant role in the proposed model. It manages the network in a decentralized manner by controlling the functionality of each peer individually. This helps prevent the drawbacks of the centralized controllers such as single point of failure. Smart contract works in a similar way as a traditional contract written in a programming language where predefined functionalities are triggered by the occurrence of certain events [32]. The smart contract is often referred to as an “autonomous agent” because it operates independently of any particular user or organization. Any Ethereum node can trigger a smart contract by using an Externally Owned Account (EOA), which is essentially a public–private key pair associated with a particular user. In addition, a smart contract can be triggered by any message received from another smart contract, allowing for complex interactions between different parts of the network.
In the proposed blockchain-enabled framework, communication between users is processed using a public channel, which poses a security risk as it may be susceptible to eavesdropping and modification by attackers. To address this issue, the framework employs a user authentication mechanism that leverages a public–private key structure. Each user is assigned a unique public–private key pair, which is used to store and retrieve their personal information. When a user wishes to access the decentralized storage, they must first authenticate themselves to the smart contract by providing their private key. If the authentication process is successful, the smart contract grants the user access to the storage according to their assigned roles. On the other hand, if the authentication fails, the smart contract rejects the user’s request and block them for any further communication. This helps to ensure that only authorized users are able to access the decentralized storage and that any attempts by unauthorized users to do so are prevented.
By using a public–private key structure and an authentication mechanism, the proposed framework provides a secure and reliable way for users to access decentralized storage without compromising the privacy and security of their personal information. This helps to address the potential risks associated with the use of a public communication channel and ensures that only authorized users can interact with the system
The procedure of user authentication is begun with the creation of an authentication token (). A unique authentication is generated every time when a user wishes to access a piece of information through the smart contract. A one-way hash function is used over several user-related information with a current time stamp to calculate given as follows:
In the next step, the user sends the following encrypted message to the smart contract. Here, encryption is performed with the user’s private key:
After receiving the encrypted message, the smart contract first uses the public key of the user to decrypt the message and retrieve the original information.
Thereafter, the smart contract checks whether the request received is transmitted from an existing user or not. If not, then smart-contract blocks this request and aborts all the operations. Otherwise, it checks information further for user authenticity. The smart contract uses the same information and hashing algorithm to generate the authentication token again, say . If , then the smart contract can ensure the requested user is authenticated. Algorithm 2 depicts the stepwise procedure of user authentication by smart contract and registration authority. Computational complexity of user authentication is .
Interplanetary file system (IPFS)
The proposed framework leverage a decentralized storage system such as IPFS is encouraged because of the mutual support of IPFS and Ethereum-based smart contract. The traditional centralized cloud storage system has the following drawbacks. Centralized storage systems are prone to a single point of failure. Therefore, distributed storage systems are encouraged to increase data portability and flexibility and reduce the chance of data loss. Second is the high support of IPFS for large files. Blockchain-based storage systems have limited storage space, and storing large files can be a challenge. IPFS addresses this challenge by breaking down large files into smaller chunks, and distributing them across different locations in the network. This approach helps to ensure that large files can be stored and accessed efficiently, without overburdening the storage capacity of any single node in the network. In contrast to traditional memory location-based storage systems, IPFS uses content-based addressing. When a file is stored in IPFS, it is assigned a unique cryptographic hash value, which serves as the file’s address. This approach helps to eliminate duplicate entries, since files with the same content will have the same hash value. It also allows users to easily verify the integrity of files, since any changes to the file will result in a different hash value. Additionally, IPFS maintains a history of each file version, allowing users to access previous versions of a file if necessary.
In the proposed work, the smart contract provides a secure and authenticated exchange of image data among patients and hospitals. IPFS stores the encrypted image information in a distributed manner, and generated hashes are stored over the immutable blockchain network. This hash value is used further to access data from IPFS. Only a registered and successfully authenticated user can access the stored information through the smart contract.
Data submitted by the user are processed by the smart contract and stored in IPFS following successful user authentication using Algorithm 2. Once the data have been correctly stored, IPFS returns a different cryptographic hash, making it challenging to modify the data. Created hashes are stored in blockchains to further increase the security of sensitive data and make data alteration impossible.
Security analysis
The proposed blockchain-enabled healthcare monitoring system for diagnosis of monkeypox disease includes several security measures to protect the privacy and integrity of the data. One of the key security measures is the use of hash values to store and verify the integrity of files on the blockchain. Hash values are generated using a one-way function, which means that it is computationally infeasible to obtain the original values from the hash. This ensures that the data stored on the blockchain cannot be tampered with or modified without detection.
To access the decentralized storage system, smart contract uses public–private key cryptography, which ensures that only authorized users can access the system. This means that only users with the correct private key can retrieve the data stored on the blockchain, and unauthorized users are prevented from accessing the system.
Role-based access control is also used to restrict users from retrieving unauthorized data. This ensures that sensitive information about patients is protected and only authorized users can access the information they need. In addition to these measures, the proposed system also encrypts data before storing it on the IPFS. This means that even if an attacker gains access to the data, they will not be able to read or modify it without the decryption key.
Data preprocessing
The success of any machine learning model depends heavily on the quality of the data used for training. Therefore, it is important to preprocess the data before feeding it into the classification model. In this study, we used a monkeypox dataset of 1905 images obtained from the GitHub repository. The preprocessing steps taken are as follows:
Data cleaning: We carefully examined the dataset and removed any irrelevant or noisy data such as images that are not related to monkeypox or that are corrupted. We also removed duplicates to ensure the training data was unique.
Data Augmentation: To increase the size of the dataset and improve the robustness of the classification model, we applied data augmentation techniques. This involves applying transformations such as rotation, flipping, and scaling to the original images to create new training data.
Image resizing: We resized all the images in the dataset to a standard size of pixels. This was necessary to ensure that all images had the same dimensions and could be used as input to the deep learning model.
Train-test split: Finally, we split the preprocessed dataset into training and testing sets with a ratio of . The training set was used to train the classification model, while the testing set was used to evaluate the performance of the model.
Overall, the data preprocessing steps were crucial in ensuring the quality and suitability of the dataset for training the deep learning model. The resulting dataset was well-structured and diverse, which allowed the model to learn and generalize effectively.
Transfer learning
Transfer learning is a machine learning technique where a model trained on one task is reused as a starting point for another related task. Convolutional Neural Networks (CNNs) are a type of deep neural network that are commonly used in computer vision tasks, such as image classification. Transfer learning with CNNs involves using a pre-trained CNN as a starting point for a new image classification task, by reusing the convolutional layers to extract features from images and training new fully connected layers to classify the images. This approach can reduce the amount of training data and time required to achieve good performance on the new task. The basic idea is that a model that has already learned to extract useful features from one type of data can be fine-tuned on a new dataset to perform a different task. It is a powerful technique that has gained immense popularity in the field of medical image processing in recent years [33]. It involves leveraging pre-trained deep neural network models on a large dataset to solve problems in a new domain with smaller datasets. These include AlexNet, Visual Geometry Group (VGG), DenseNet, Inception-v4, and ResNet. Stepwise step working of designed transfer learning-based classification is given in Algorithm 3.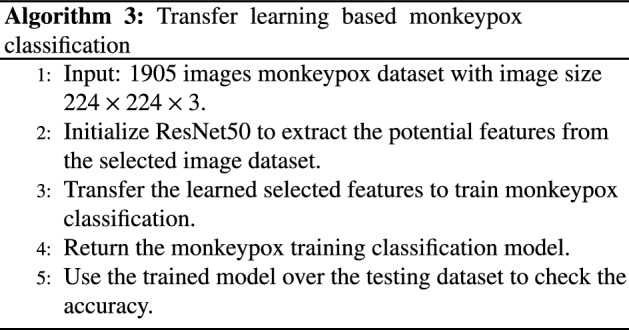
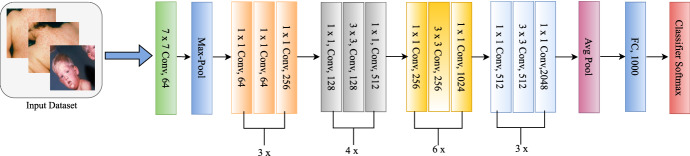
In the present work, modified fine-tuned RestNet50 is used for the classification task. ResNet50 is an abbreviation for a residual network with 50 hidden layers, as shown in Fig. 2. Resnet50 is similar to VGG16, with the added benefit of identity mapping. As depicted in Fig. 2, ResNet estimates the change in prediction accuracy from one layer to the next [34].
Fig. 2.
Proposed transfer learning architecture
ResNet mitigates the vanishing gradient issue by including an alternative gradient flow line. Through the use of identity mapping, ResNet can skip over a CNN weight layer if it is not required. It is a good way to prevent the issue of overfitting the training data. There are 50 layers in ResNet50.
To fine-tune the ResNet50 model on our dataset, we replaced its last fully connected layer with a new one having the same number of output classes. Initially, we froze the weights of the convolutional layers in the ResNet50 backbone and trained only the fully connected layers on our dataset for several epochs. Subsequently, we unfroze the convolutional layers and continued training the entire model with a lower learning rate to fine-tune the weights of the convolutional layers on our dataset. We use several methods for augmenting the training data with additional information to increase the model’s accuracy. We enhance the performance of the ResNet50 model by adding specialized global average pooling (GAP), dropout, and dense softmax classification node layers.
Simulation results
This section explains the experimental results of the proposed framework and evaluates the performance over different evaluation metrics.
Smart contract implementation
This section discusses the details of the smart contract implemented in the proposed framework. The proposed smart contract is implemented on Ethereum Remix IDE [35] using solidity programming language [36]. Remix provides a virtual platform to validate, verify and deploy any smart contract on a similar real-world environment. Solidity provides a wide range of built-in data types to facilitate different functionalities of the smart contract. Mainly two actors (patients and healthcare service providers) are involved in the proposed smart contract where each one is recognized by their 20 bytes unique Ethereum address. Inbuilt address datatype is used to store Ethereum addresses. Some other useful features of the solidity-based smart contract include mapping, balance, modifiers, and constructors. Constructor is used in initializing different actors, whereas mapping data structure is used to map an Ethereum address to the set of information such as the actor’s role, public key, and other personal data. Modifiers restrict the access of actors based on their respective roles.
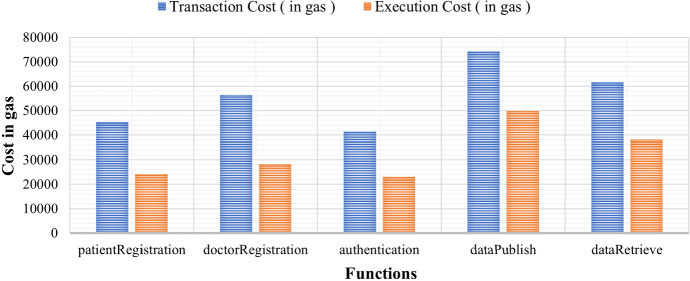
Initially, the contract owner deploys a smart contract using its own Ethereum address followed by the execution of several user-defined functions such as patientRegistration, doctorRegistration, authentication, dataPublish, and dataRelease. The performance of a deployed smart contract is measured in terms of the gas cost associated with each transaction and function call execution that indicates the amount of money needed to perform the same operation in a real Ethereum Network. Remix provides an easy-to-use feature to approximate the transaction cost and execution cost which is directly proportional to the complexity of functions, numbers of input and output parameters, and smart contract status. To reduce the overall amount of cost, we have tried to reduce the complexity and designed simple functions as much as possible. Figure 3 shows the transaction cost to execute essential functions. Out of all five functions, user registration and authentication consume less gas compared to data storage and retrieval. Besides, from Fig. 3, it is also observed that the transaction cost is always higher than the execution cost.
Fig. 3.
Smart contract cost evaluation
Transfer learning classification
Humans are highly susceptible to dying from monkeypox, so early detection is crucial. It is crucial to develop a computer-aided diagnostics system for categorizing various skin-related diseases. This paper proposes a deep neural network model called ResNet50 for classifying monkeypox and non-monkeypox images.
Data collection
The monkeypox dataset is publicly available and can be obtained from the GitHub repository. It was created by assembling images collected from websites, newspapers, and online portals and currently contains around 1905 images after data augmentation [37]. The dataset is created by collecting images from multiple open-source and online portals that do not impose any restrictions on use, even for commercial purposes, providing a safer path to use and disseminate such data when constructing and deploying any ML model. Figure 4 represents the sample dataset containing monkeypox and non-monkeypox images, and Table 2 summarizes the dataset.
Fig. 4.

Few sample images of MonkeyPox dataset
Table 2.
Dataset summary
| Dataset | Number of classes | Class name | Number of image | Size of image |
|---|---|---|---|---|
| Monkeypox skin lesion dataset (MSLD) | 2 | Monkeypox_augmented | 587 | |
| Others_augmented | 838 |
Performance metrics
To validate the performance of the proposed methodology, various performance evaluation measures are employed. These include accuracy, precision, recall, and F1-score. Table 3 describes various performance metrics for image classification.
Table 3.
Performance evaluation measures
| S.No | Performance measures | Description | Mathematical Expression |
|---|---|---|---|
| 1 | Accuracy | The network’s competence to correctly classify different classes | Accuracy |
| 2 | Recall | Recall determines the number of positive class predictions made from all positive data points | Recall |
| 3 | Precision | Precision quantifies the number of positive class predictions that are positive | Precision |
| 4 | F1-score | Measures the harmonic mean of precision and recall | score |
The value of these metrics is computed using the confusion matrix, comprising of True Positive (TP), True Negative (TN), False Positive (FP), and False Negative (FN) values [38]. The generic structure of the confusion matrix is presented in Table 4.
Table 4.
Confusion matrix for binary classification
| Actual | |||
|---|---|---|---|
| Correct | Incorrect | ||
| Predicted | Correct | True Positive | False Positive |
| Incorrect | False Negative | True Negative | |
Parameter settings
In order to classify diseases accurately, we use the network architecture of the ResNet50 model and apply the fine-tuning transfer-learning concept by first freezing the initial layers of the model and then fine-tuning their weights. To improve the model’s accuracy during training, we use a variety of data augmentation techniques.
By adding specialized global average pooling (GAP), dropout, and dense softmax classification node layers, we improve the performance of the ResNet50 model. Here, we compared various deep-learning models that have already been trained to classify cases of monkeypox. We looked at how well the pre-trained models VGG16, VGG19, and Xception performed. Model over-fitting was seen to be an issue with these pre-trained models. Promising results were obtained on a modified fine-tuned Resnet50 model after we attempted to address the issue of model over-fitting by employing augmentation techniques and adding layers of global average pooling, dropout, and dense softmax.
We have used three pre-trained models such as VGG16, VGG19, and Xception to classify the augmented dataset into two classes such as monkeypox and non-monkeypox. For model simulation, the parameters taken are presented in Table 5. The considered input image size is 224*224*3. We have used an ADAM optimizer for getting optimized results. The learning rate for all the architectures is taken as 0.001 and Categorical cross-entropy as loss function. Due to limited hardware resources, the number of epochs is fixed to a value of 10. The softmax function is used for classification (Table 6).
Table 5.
Simulation parameters
| Parameters | Value |
|---|---|
| Optimizer | ADAMS |
| Learning rate | 0.001 |
| Loss function | Categorical cross-entropy |
| Metrics | Accuracy |
| Number of epochs | 10 |
| Model | Sequential |
| Input image size | 224*224*3 |
| Pooling | AvgPool |
| Number of classes | 2 |
| Activation function in FC (Fully Connected) layer | ReLu |
| The activation function in output (Classification) layer | SoftMax |
| Batch Size | 32 |
Table 6.
Trainable and non-trainable parameters for proposed model
| Model | Total parameters | Trainable parameters | Non-trainable parameters |
|---|---|---|---|
| Xception | 72,243,242 | 51,381,762 | 20,861,480 |
| VGG19 | 32,870,978 | 12,846,594 | 20,024,384 |
| VGG16 | 27,561,282 | 12,846,594 | 14,714,688 |
| Proposed | 24,637,826 | 1,050,114 | 23,587,712 |
Results and discussion
In this paper, we present a modified fine-tuned Resnet50 model that successfully distinguishes between monkeypox and other types of lesions. The study’s findings corroborated the effectiveness of our proposed model for use in the monkeypox classification task. In order to construct a trustworthy computer-assisted diagnostic system for early monkeypox diagnosis, our future research will focus on training and testing on additional datasets and verifying the efficacy of our proposed model. The classification accuracy of our proposed model is 98.8%. Future research could deepen the investigation by examining even more complex architectural layouts and developing even more finely tuned models.
The results obtained in various transfer learning-based architectures along with the proposed model are shown in Table 7. The obtained performance matrix such as accuracy, precision, recall, and F1- score in Xception, VGG16, VGG19, and our proposed model is (0.7619, 0.7653, 0.7619 and 0.7561), (0.8928, 0.8934, 0.8928, 0.8930), (0.9404, 0.9477, 0.9404, 0.9407) and (0.9880, 0.9884, 0.9880, 0.9881). Compared to other transfer learning architectures, the Xception model is not performing well for the monkeypox dataset. Our proposed model achieved the highest classification accuracy.
Table 7.
Results of various transfer learning models
| Model | Accuracy | Precision | Recall | F1-score |
|---|---|---|---|---|
| Xception | 0.7619 | 0.7653 | 0.7619 | 0.7561 |
| VGG16 | 0.8928 | 0.8934 | 0.8928 | 0.8930 |
| VGG19 | 0.9404 | 0.9477 | 0.9404 | 0.9407 |
| Proposed | 0.9880 | 0.9884 | 0.9880 | 0.9881 |
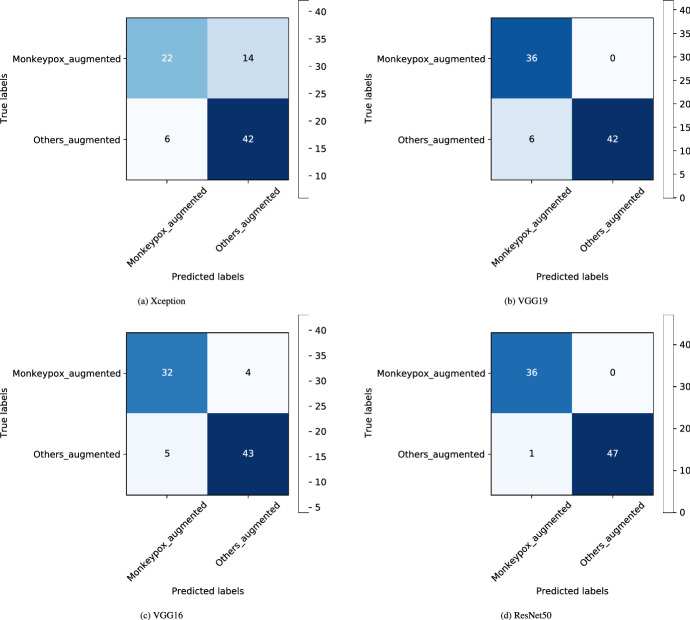
The confusion matrices for Xception, VGG16, VGG19 and our proposed model are shown in figures 5a, b, c and d, respectively.
Fig. 5.
Shows confusion matrix obtained in TL architecture a Xception, b VGG19, c VGG16 and d ResNet50
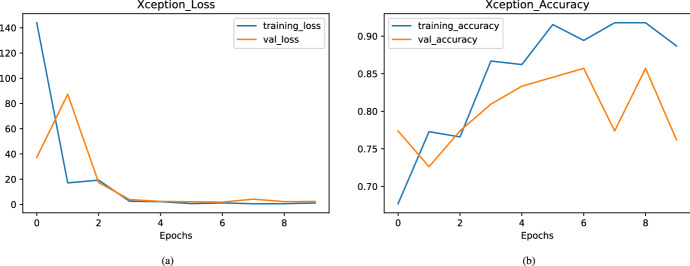
Figure 6 shows the predicted class with annotations. Figure (7a, b) shows the loss and accuracy curves obtained in Xception architecture. It can be seen that after the third epoch loss converges and it is extremely low. In the Xception model, there is a big difference between training and validation accuracy. So, overall we can say this model is not performing well over the given dataset.
Fig. 6.

Predicted samples by our proposed model
Fig. 7.
Achieved loss and accuracy over different epochs in Xception model
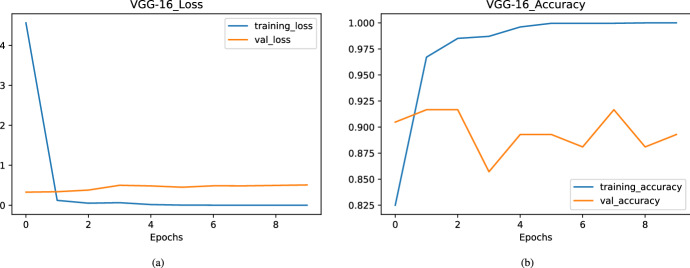
Figure (9a, b) shows loss and accuracy curve obtained in VGG16 architecture. Here, after the first epoch loss converges and it is extremely low. In this architecture, although validation accuracy is good. However, there is a quite difference between training and validation accuracy. So, overall we can say this model is performing relatively better than the Xception model over the given dataset.
Fig. 9.
Achieved loss and accuracy over different epochs in VGG16 model
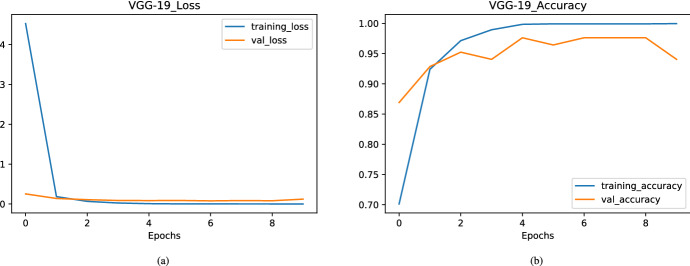
Figure (8a, b) shows loss and accuracy curve obtained in VGG19 architecture. Here, after the first epoch loss converges and it is extremely low. In this architecture, the difference between training and validation accuracy is very low. So, overall we can say this model is performing relatively better than both Xception and VGG16 models over the given dataset. But still, we are looking for our proposed model that gives accuracy higher than these architectures.
Fig. 8.
Achieved loss and accuracy over different epochs in VGG19 model
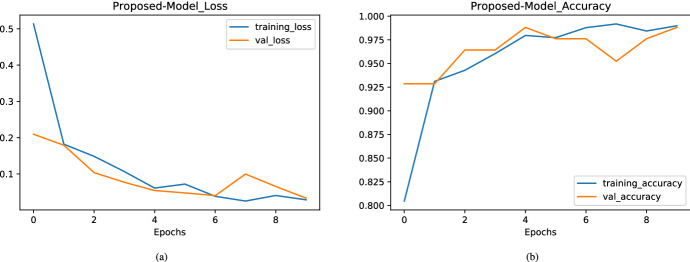
Figure (10(a), b) depicts the loss and accuracy curve obtained in our proposed model. Here, after the fourth epoch loss converges and it is extremely low. In this model, the difference between training and validation accuracy is very low and validation accuracy is very high. In nutshell, we can say this model is performing best over the given dataset.
Fig. 10.
Achieved loss and accuracy over different epochs in proposed model
Conclusion and future work
This paper proposed a secured blockchain-enabled framework for the early detection of monkeypox. The proposed framework comprises four key enablers, namely registration authority, smart contract, decision-making, and interplanetary file system (IPFS). Initially, various key actors including patients and healthcare service providers register with the registration authority for ensuring secured communication with a blockchain network. The registration authority and IPFS are entrusted with the responsibility of storing the electronic health records of the different stakeholders of the system. The second key component, the smart contract legitimately controls the transactions of sensitive information between the stakeholders under specific terms. The decision model forms the heart and soul of the entire system which is responsible for the in-time detection of monkeypox cases. In the proposed framework, we leverage the potential of transfer learning to propose an efficient decision-making model. Besides, the performance of the proposed decision model is evaluated against a set of classification metrics, including accuracy, recall, precision, and F1-score. The performance assessment of our suggested scheme reveals that the proposed blockchain improvised network is well-structured and robust against network attacks. In future, various advanced machine learning models will be explored to improve the performance of decision-making and detect other skin lesion diseases such as measles and chickenpox.
Author Contributions
AG was involved in conceptualization, methodology, and writing—original draft. MB contributed to data curation, formal analysis, and validation. VJ was involved in writing, review & editing, visualization, and project administration
Funding
No funding was received.
Data availability
The datasets generated during and/or analyzed during the current study are available from the corresponding author upon reasonable request.
Declarations
Conflict of interest
There is no conflict of interest involved in conducting this research.
Ethical approval
No ethical approval is required for conducting the study.
Footnotes
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
References
- 1.Smith KF, Goldberg M, Rosenthal S, Carlson L, Chen J, Chen C, Ramachandran S. Global rise in human infectious disease outbreaks. J Royal Soc Interface. 2014;11(101):20140950. doi: 10.1098/rsif.2014.0950. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 2.Rizk JG, Lippi G, Henry BM, Forthal DN, Rizk Y. Prevention and treatment of monkeypox. Drugs. 2022;82(9):957–9. doi: 10.1007/s40265-022-01742-y. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 3.Hraib M, Jouni S, Albitar MM, Alaidi S, Alshehabi Z. The outbreak of monkeypox, an overview. Ann Med Surg. 2022;2022:104069. doi: 10.1016/j.amsu.2022.104069. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 4.Khatri G, Mir SL, Hasan MM, et al. Outbreak of monkeypox in south east Asia; spotlight on Bangladesh, Pakistan and India. Ann Med Surg. 2022;82:104361. doi: 10.1016/j.amsu.2022.104361. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 5.Fatima N, Mandava K. Monkeypox-a menacing challenge or an endemic? Ann Med Surg. 2022;79:103979. doi: 10.1016/j.amsu.2022.103979. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 6.Uwishema O, Adekunbi O, Peñamante CA, Bekele BK, Khoury C, Mhanna M, Nicholas A, Adanur I, Dost B, Onyeaka H. The burden of monkeypox virus amidst the covid-19 pandemic in Africa: a double battle for Africa. Ann Med Surg. 2022;80:104197. doi: 10.1016/j.amsu.2022.104197. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 7.2022 Outbreak cases and data | monkeypox | poxvirus | cdc. https://www.cdc.gov/poxvirus/monkeypox/response/2022/index.html
- 8.Gupta A, Singh A. An intelligent healthcare cyber physical framework for encephalitis diagnosis based on information fusion and soft-computing techniques. New Gener Comput. 2022;40:1093–1123. doi: 10.1007/s00354-022-00175-1. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 9.Jayabalan J, Jeyanthi N. Scalable blockchain model using off-chain ipfs storage for healthcare data security and privacy. J Parallel Distrib Comput. 2022;164:152–167. doi: 10.1016/j.jpdc.2022.03.009. [DOI] [Google Scholar]
- 10.Islam N, Faheem Y, Din IU, Talha M, Guizani M, Khalil M. A blockchain-based fog computing framework for activity recognition as an application to e-healthcare services. Future Gener Comput Syst. 2019;100:569–578. doi: 10.1016/j.future.2019.05.059. [DOI] [Google Scholar]
- 11.Gupta S, Malhotra V, Singh SN (2020) Securing iot-driven remote healthcare data through blockchain, In: Advances in data and information sciences, Springer, pp. 47–56
- 12.Ali SN, Ahmed M, Paul J, Jahan T, Sani S, Noor N, Hasan T et al. (2022) Monkeypox skin lesion detection using deep learning models: A feasibility study, arXiv preprint arXiv:2207.03342
- 13.Gairola AK, Kumar V (2022) Monkeypox disease diagnosis using machine learning approach, In: 2022 8th International Conference on Signal Processing and Communication (ICSC), IEEE, pp. 423–427
- 14.Kundu D, Siddiqi UR, Rahman MM (2022) Vision transformer based deep learning model for monkeypox detection, In: 2022 25th International Conference on Computer and Information Technology (ICCIT), IEEE, pp. 1021–1026
- 15.Uzun Ozsahin D, Mustapha MT, Uzun B, Duwa B, Ozsahin I. Computer-aided detection and classification of monkeypox and chickenpox lesion in human subjects using deep learning framework. Diagnostics. 2023;13(2):292. doi: 10.3390/diagnostics13020292. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 16.ÖrenÇ S, Emrullah A, Özerdem MS Utilizing the ensemble of deep learning approaches to identify monkeypox disease, Dicle Üniversitesi Mühendislik Fakültesi Mühendislik Dergisi 13(4):685–691
- 17.Sahin VH, Oztel I, Yolcu Oztel G. Human monkeypox classification from skin lesion images with deep pre-trained network using mobile application. J Med Syst. 2022;46(11):79. doi: 10.1007/s10916-022-01863-7. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 18.Ahsan MM, Uddin MR, Luna SA (2022) Monkeypox image data collection, arXiv preprint arXiv:2206.01774
- 19.Hussain MA, Islam T, Chowdhury FUH, Islam BR (2022) Can artificial intelligence detect monkeypox from digital skin images?, BioRxiv 2022–08
- 20.Alrusaini OA. Deep learning models for the detection of monkeypox skin lesion on digital skin images. Int J Adv Comput Sci Appl. 2023;14(1):55. doi: 10.14569/IJACSA.2023.0140170. [DOI] [Google Scholar]
- 21.Mamun Q. Blockchain technology in the future of healthcare. Smart Health. 2022;23:100223. doi: 10.1016/j.smhl.2021.100223. [DOI] [Google Scholar]
- 22.Azaria A, Ekblaw A, Vieira T, Lippman A, Medrec: Using blockchain for medical data access and permission management, In: (2016) 2nd International Conference on Open and Big Data (OBD). IEEE 2016:25–30
- 23.Nguyen GN, Le Viet NH, Elhoseny M, Shankar K, Gupta B, Abd El-Latif AA. Secure blockchain enabled cyber-physical systems in healthcare using deep belief network with resnet model. J Parallel Distrib Comput. 2021;153:150–160. doi: 10.1016/j.jpdc.2021.03.011. [DOI] [Google Scholar]
- 24.Yu W, Liu Z, Chen C, Yang B, Guan X. Privacy-preserving design for emergency response scheduling system in medical social networks. Peer to Peer Netw Appl. 2017;10(2):340–356. doi: 10.1007/s12083-016-0429-4. [DOI] [Google Scholar]
- 25.Sitaula C, Shahi TB. Monkeypox virus detection using pre-trained deep learning-based approaches. J Med Syst. 2022;46(11):78. doi: 10.1007/s10916-022-01868-2. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 26.Gülmez B. Monkeypoxhybridnet: a hybrid deep convolutional neural network model for monkeypox disease detection. Int Res Eng Sci. 2022;3:49–64. [Google Scholar]
- 27.Abdelhamid AA, El-Kenawy E-SM, Khodadadi N, Mirjalili S, Khafaga DS, Alharbi AH, Ibrahim A, Eid MM, Saber M. Classification of monkeypox images based on transfer learning and the al-biruni earth radius optimization algorithm. Mathematics. 2022;10(19):3614. doi: 10.3390/math10193614. [DOI] [Google Scholar]
- 28.Akin KD, Gurkan C, Budak A, KarataŞ H. Classification of monkeypox skin lesion using the explainable artificial intelligence assisted convolutional neural networks. Avrupa Bilim ve Teknoloji Dergisi. 2022;40:106–110. [Google Scholar]
- 29.Bala D, Hossain MS, Hossain MA, Abdullah MI, Rahman MM, Manavalan B, Gu N, Islam MS, Huang Z. Monkeynet: a robust deep convolutional neural network for monkeypox disease detection and classification. Neural Networks. 2023;161:757–775. doi: 10.1016/j.neunet.2023.02.022. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 30.Dwivedi M, Tiwari RG, Ujjwal N (2022) Deep learning methods for early detection of monkeypox skin lesion, In: 2022 8th International Conference on Signal Processing and Communication (ICSC), IEEE, pp. 343–348
- 31.Dwivedi SK, Amin R, Vollala S. Smart contract and ipfs-based trustworthy secure data storage and device authentication scheme in fog computing environment. Peer Peer Netw Appl. 2022;16:1–21. [Google Scholar]
- 32.Jain V, Kumar B. Combinatorial auction based multi-task resource allocation in fog environment using blockchain and smart contracts. Peer Peer Netw Appl. 2021;14(5):3124–3142. doi: 10.1007/s12083-021-01161-y. [DOI] [Google Scholar]
- 33.Bhagat M, Kumar D. A comprehensive survey on leaf disease identification & classification. Multimed Tools Appl. 2022;81(23):33897–33925. doi: 10.1007/s11042-022-12984-z. [DOI] [Google Scholar]
- 34.Theckedath D, Sedamkar R. Detecting affect states using vgg16, resnet50 and se-resnet50 networks. SN Comput Sci. 2020;1(2):1–7. doi: 10.1007/s42979-020-0114-9. [DOI] [Google Scholar]
- 35.Remix - Ethereum IDE. remix.ethereum.org
- 36.Dannen C. Introducing Ethereum and solidity. Springer; 2017. [Google Scholar]
- 37.https://github.com/mahsan2/Monkeypox-dataset-2022, (Accessed on 05/10/2022)
- 38.Powers DM (2020) Evaluation: from precision, recall and f-measure to roc, informedness, markedness and correlation, arXiv preprint arXiv:2010.16061
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
The datasets generated during and/or analyzed during the current study are available from the corresponding author upon reasonable request.