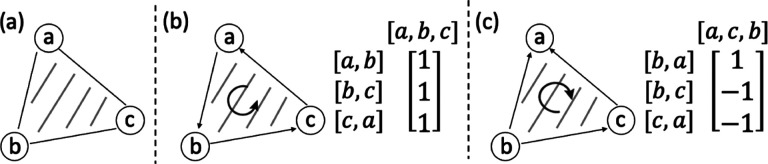Abstract
The graph traversal edit distance (GTED), introduced by Ebrahimpour Boroojeny et al. (2018), is an elegant distance measure defined as the minimum edit distance between strings reconstructed from Eulerian trails in two edge-labeled graphs. GTED can be used to infer evolutionary relationships between species by comparing de Bruijn graphs directly without the computationally costly and error-prone process of genome assembly. Ebrahimpour Boroojeny et al. (2018) propose two ILP formulations for GTED and claim that GTED is polynomially solvable because the linear programming relaxation of one of the ILPs always yields optimal integer solutions. The claim that GTED is polynomially solvable is contradictory to the complexity results of existing string-to-graph matching problems.
We resolve this conflict in complexity results by proving that GTED is NP-complete and showing that the ILPs proposed by Ebrahimpour Boroojeny et al. do not solve GTED but instead solve for a lower bound of GTED and are not solvable in polynomial time. In addition, we provide the first two, correct ILP formulations of GTED and evaluate their empirical efficiency. These results provide solid algorithmic foundations for comparing genome graphs and point to the direction of heuristics.
1. Introduction
Graph traversal edit distance (GTED) [1] is an elegant measure of the similarity between the strings represented by edge-labeled Eulerian graphs. For example, given two de Bruijn assembly graphs [2], computing GTED between them measures the similarity between two genomes without the computationally intensive and possibly error-prone process of assembling the genomes. Using an approximation of GTED between assembly graphs of Hepatitis B viruses, Ebrahimpour Boroojeny et al. [1] group the viruses into clusters consistent with their taxonomy. This can be extended to inferring phylogeny relationships in metagenomic communities or comparing heterogeneous disease samples such as cancer. There are several other methods to compute a similarity measure between strings encoded by two assembly graphs [3–6]. GTED has the advantage that it does not require prior knowledge on the type of the genome graph or the complete sequence of the input genomes. The input to the GTED problem is two unidirectional, edge-labeled Eulerian graphs, which are defined as:
Definition 1 (Unidirectional, edge-labeled Eulerian Graph). A unidirectional, edge-labeled Eulerian graph is a connected directed graph , with node set , edge multiset , constant-size alphabet , and single-character edge labels , such that contains an Eulerian trail that traverses every edge exactly once. The unidirectional condition means that all edges between the same pair of nodes are in the same direction.
Such graphs arise in genome assembly problems (e.g. the de Bruijn subgraphs). Computing GTED is the problem of computing the minimum edit distance between the two most similar strings represented by Eulerian trails each input graph.
Problem 1 (Graph Traversal Edit Distance (GTED) [1]). Given two unidirectional, edge-labeled Eulerian graphs and , compute
| (1) |
Here, trails(G) is the collection of all Eulerian trails in graph G, str(t) is a string constructed by concatenating labels on the Eulerian trail , and edit is the edit distance between strings and .
Ebrahimpour Boroojeny et al. [1] claim that GTED is polynomially solvable by proposing an integer linear programming (ILP) formulation of GTED and arguing that the constraints of the ILP make it polynomially solvable. This result, however, conflicts with several complexity results on string-to-graph matching problems. Kupferman and Vardi [7] show that it is NP-complete to determine if a string exactly matches an Eulerian tour in an edge-labeled Eulerian graph. Additionally, Jain et al. [8] show that it is NP-complete to compute an edit distance between a string and strings represented by a labeled graph if edit operations are allowed on the graph. On the other hand, polynomial-time algorithms exist to solve string-to-string alignment [9] and string-to-graph alignment [8] when edit operations on graphs are not allowed.
We resolve the conflict among the results on complexity of graph comparisons by revisiting the complexity of and the proposed solutions to GTED. We prove that computing GTED is NP-complete by reducing from the HAMILTONIAN PATH problem, reaching an agreement with other related results on complexity. Further, we point out with a counter-example that the optimal solution of the ILP formulation proposed by Ebrahimpour Boroojeny et al. [1] does not solve GTED.
We give two ILP formulations for GTED. The first ILP has an exponential number of constraints and can be solved by subtour elimination iteratively [10, 11]. The second ILP has a polynomial number of constraints and shares a similar high-level idea of the global ordering approach [11] in solving the Traveling Salesman problem [12].
In Qiu and Kingsford [13], Flow-GTED (FGTED), a variant of GTED is proposed to compare two sets of strings instead of two strings encoded by graphs. FGTED is equal to the edit distance between the most similar sets of strings spelled by the decomposition of flows between a pair of predetermined source and sink nodes. The similarity between the sets of strings reconstructed from the flow decomposition is measured by the Earth Mover’s Edit Distance [13, 14]. FGTED is used to compare pan-genomes, where both the frequency and content of strings are essential to represent the population of organisms. Qiu and Kingsford [13] reduce FGTED to GTED, and via the claimed polynomial-time algorithm of GTED, argue that FGTED is also polynomially solvable. We show that this claim is false by proving that FGTED is also NP-complete.
While the optimal solution to ILP proposed in Ebrahimpour Boroojeny et al. [1] does not solve GTED, it does compute a lower bound to GTED. We characterize the cases when GTED is equal to this lower bound. In addition, we point out that solving this ILP formulation finds a minimum-cost matching between closed-trail decompositions in the input graphs, which may be used to compute the similarity between repeats in the genomes. Ebrahimpour Boroojeny et al. [1] claim their proposed ILP formulation is solvable in polynomial time by arguing that the constraint matrix of the linear relaxation of the ILP is always totally unimodular. We show that this claim is false by proving that the constraint matrix is not always totally unimodular and showing that there exists optimal fractional solutions to its linear relaxation.
We evaluate the efficiency of solving ILP formulations for GTED and its lower bound on simulated genomic strings and show that it is impractical to compute GTED on larger genomes.
In summary, we revisit two important problems in genome graph comparisons: Graph Traversal Edit Distance (GTED) and its variant FGTED. We show that both GTED and FGTED are NP-complete, and provide the first correct ILP formulations for GTED. We also show that the ILP formulation proposed by [1] is a lower bound to GTED. We evaluate the efficiency of the ILPs for GTED and its lower bound on genomic sequences. These results provide solid algorithmic foundations for continued algorithmic innovation on the task of comparing genome graphs and point to the direction of approximation heuristics.
2. GTED and FGTED are NP-complete
2.1. Conflicting results on computational complexity of GTED and string-to-graph matching
The natural decision versions of all of the computational problems described above and below are clearly in NP. Under the assumption that , the results on the computational complexity of GTED and string-to-graph matching claimed in Ebrahimpour Boroojeny et al. [1] and Kupferman and Vardi [7], respectively, cannot be both true.
Kupferman and Vardi [7] show that the problem of determining if an input string can be spelled by concatenating edge labels in an Eulerian trail in an input graph is NP-complete. We call this problem Eulerian Trail Equaling Word. We show in Theorem 1 that we can reduce ETEW to GTED, and therefore if GTED is polynomially solvable, then ETEW is polynomially solvable. The complete proof is in Appendix A.1.
Problem 2 (Eulerian Trail Equaling Word [7]). Given a string , an edge-labaled Eulerian graph G, find an Eulerian trail t of G such that str(t) = s.
Theorem 1. If then .
Proof sketch. We first convert an input instance to ETEW into an input instance to GTED by (a) creating graph that only contains edges that reconstruct string and (b) modifying into by extending the anti-parallel edges so that is unidirectional. We show that if , there must be an Eulerian trail in that spells , and if must not contain an Eulerian trail that spells . □
Hence, an (assumed) polynomial-time algorithm for GTED solves ETEW in polynomial time. This contradicts Theorem 6 of Kupferman and Vardi [7] of the NP-completeness of ETEW (under ).
2.2. Reduction from Hamiltonian Path to GTED and FGTED
We resolve the contradiction by showing that GTED is NP-complete. The details of the proof are in Appendix A.2.
Theorem 2. GTED is NP-complete.
Proof sketch. We reduce from the Hamiltonian Path problem, which asks whether a directed, simple graph contains a path that visits every vertex exactly once. Here simple means no self-loops or parallel edges. The reduction is almost identical to that presented in Kupferman and Vardi [7], and from here until noted later in the proof the argument is identical except for the technicalities introduced to force unidirectionality (and another minor change described later).
Let be an instance of Hamiltonian Path, with vertices. We first create the Eulerian closure of , which is defined as where
| (2) |
Here, each vertex in is split into and , and is a newly added vertex. is the union of the following sets of edges and their labels:
, labeled a,
, labeled b,
, labeled ,
, labeled ,
, labeled c,
, labeled b.
is an Eulerian graph by construction but contains anti-parallel edges. We further create from by adding dummy nodes so that each pair of antiparallel edges is split into two parallel, length-2 paths with labels , where is the original label.
We also create a graph that has the same number of edges as and spells out a string
| (3) |
We then argue that G has a Hamiltonian path if and only if spells out the string , which uses the same line of arguments and graph traversals as in Kupferman and Vardi [7]. We then show that if and only if spells . □
Following a similar argument, we show that FGTED is also NP-complete, and its proof is in Appendix A.3.
Theorem 3. FGTED is NP-complete.
3. Revisiting the correctness of the proposed ILP solutions to GTED
In this section, we revisit two proposed ILP solutions to GTED by Ebrahimpour Boroojeny et al. [1] and show that the optimal solution to these ILP is not always equal to GTED.
3.1. Alignment graph
The previously proposed ILP formulations for GTED are based on the alignment graph constructed from input graphs. The high-level concept of an alignment graph is similar to the dynamic programming matrix for the string-to-string alignment problem [9].
Definition 2 (Alignment graph). Let be two unidirectional, edge-labeled Eulerian graphs. The alignment graph is a directed graph that has vertex set and edge multi-set that equals the union of the following:
Vertical edges for and ,
Horizontal edges for and ,
Diagonal edges for and .
Each edge is associated with a cost by the cost function .
Each diagonal edge in an alignment graph can be projected to and in and , respectively. Similarly, each vertical edge can be projected to one edge in , and each horizontal edge can be projected to one edge in .
We define the edge projection function that projects an edge from the alignment graph to an edge in the input graph . We also define the path projection function that projects a trail in the alignment graph to a trail in the input graph . For example, let a trail in the alignment graph be , and is a trail in .
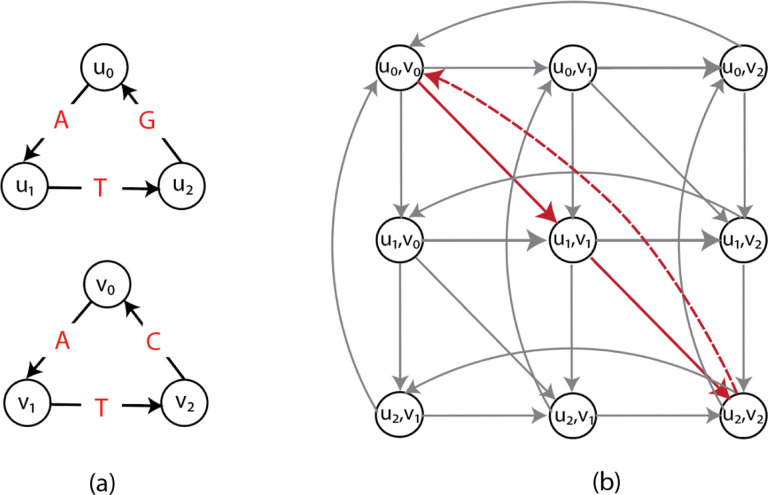
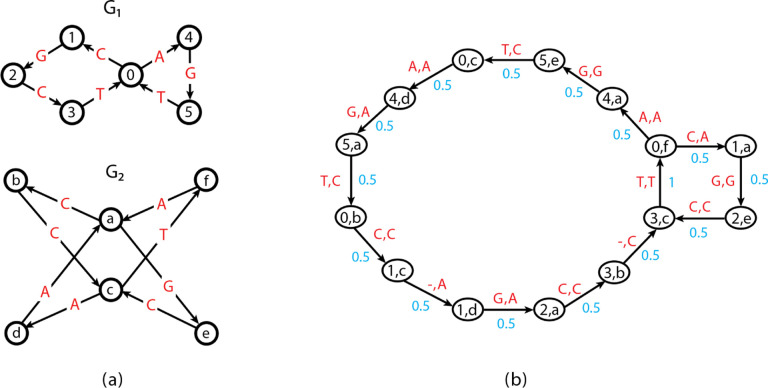
An example of an alignment graph is shown in Figure 1(b). The horizontal edges correspond to gaps in strings represented by , vertical edges correspond to gaps in strings represented by , and diagonal edges correspond to the matching between edge labels from the two graphs. In the rest of this paper, we assume that the costs for horizontal and vertical edges are 1, and the costs for the diagonal edges are 1 if the diagonal edge represents a mismatch and 0 if it is a match. The cost function can be defined to capture the cost of matching between edge labels or inserting gaps. This definition of alignment graph is also a generalization of the alignment graph used in string-to-graph alignment [8].
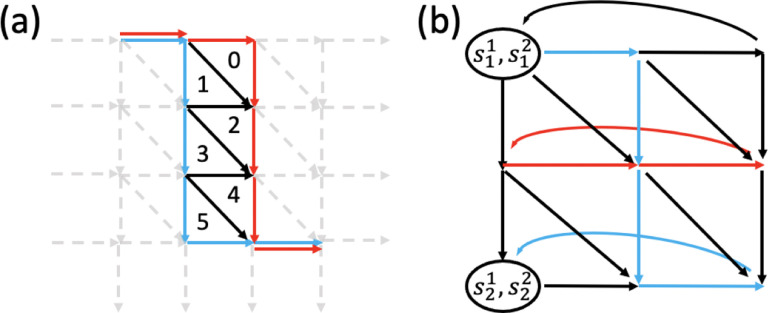
Figure 1:
(a) An example of two edge labeled Eulerian graphs G1 (top) and G2 (bottom). (b) The alignment graph A(G_1,G_2). The cycle with red edges is the path corresponding to GTED(G_1,G_2). Red solid edges are matches with cost 0 and red dashed-line edge is mismatch with cost 1.
3.2. The first previously proposed ILP for GTED
Lemma 1 in Ebrahimpour Boroojeny et al. [1] provides a model for computing GTED by finding the minimum-cost trail in the alignment graph. We reiterate it here for completeness.
Lemma 1 ([1]). For any two edge-labeled Eulerian graphs and ,
| (4) |
where is the total edge cost of , and is the projection from to .
An example of such a minimum-cost trail is shown in Figure 1(b). Ebrahimpour Boroojeny et al. [1] provide the following ILP formulation and claim that it is a direct translation of Lemma 1:
| (5) |
| (6) |
| (7) |
| (8) |
Here, is the edge set of . A is the negative incidence matrix of size , and is an indicator function that is 1 if edge in projects to edge in the input graph (and 0 otherwise). We define the domain of each to include all non-negative integers. However, due to constraints (7), the values of are limited to either 0 or 1. We describe this ILP formulation with the assumption that both input graphs have closed Eulerian trails, which means that each node has equal numbers of incoming and outgoing edges. We discuss the cases when input graphs contain open Eulerian trails in Section 4.
While the ILP in (5)–(8) allows the solutions to select disjoint cycles in the alignment graph, the projection of edges in these disjoint cycles does not correspond to a single string represented by either of the input graphs. We show that the ILP in (5)–(8) does not solve GTED by giving an example where the objective value of the optimal solution to the ILP in (5)–(8) is not equal to GTED.
Construct two input graphs as shown in Figure 2(a). Specifically, spells circular permutations of TTTGAA and spells circular permutations of TTTAGA. It is clear that GTED under Levenshtein edit distance. On the other hand, as shown in Figure 2(a), an optimal solution in contains two disjoint cycles with nonzero values that have a total edge cost equal to 0. This solution is a feasible solution to the ILP in (5)–(8). It is also an optimal solution because the objective value is zero, which is the lower bound on the ILP in (5)–(8). This optimal objective value, however, is smaller than GTED. Therefore, the ILP in (5)–(8) does not solve GTED since it allows the solution to be a set of disjoint components.
Figure 2:
(a) The subgraph in the alignment graph induced by an optimal solution to the ILP in (5)–(8) and the ILP in (11)–(12) with input graphs on the left and top. The red and blue edges in the alignment graph are edges matching labels in red and blue font, respectively, and are part of the optimal solution to the ILP in (5)–(8). The cost of the red and blue edges are zero. (b) The subgraph induced by x^”init” with s_1=u_1 and s_2=v_1 according to the ILP in (11)–(12). The rest of the edges in the alignment graph are omitted for simplicity.
3.3. The second previously proposed ILP formulation of GTED
We describe the second proposed ILP formulation of GTED by Ebrahimpour Boroojeny et al. [1]. Following Ebrahimpour Boroojeny et al. [1], we use simplices, a notion from geometry, to generalize the notion of an edge to higher dimensions. A k-simplex is a k-dimensional polytope which is the convex hull of its vertices. For example, a 1-simplex is an undirected edge, and a 2-simplex is a triangle. We use the orientation of a simplex, which is given by the ordering of the vertex set of a simplex up to an even permutation, to generalize the notion of the edge direction [15, p. 26]. We use square brackets [•] to denote an oriented simplex. For example, denotes a 1-simplex with orientation , which is a directed edge from to , and denotes a 2-simplex with orientation corresponding to the vertex ordering . Each -simplex has two possible unique orientations, and we use the signed coefficient to connect their forms together, e.g. .
For each pair of graphs and and their alignment graph , we define an oriented 2-simplex set which is the union of:
for all and , or
for all and ,
We use the boundary operator [15, p. 28], denoted by , to map an oriented k-simplex to a sum of oriented -simplices with signed coefficients.
| (9) |
where denotes the vertex is to be deleted. Intuitively, the boundary operator maps the oriented -simplex to a sum of oriented -simplices such that their vertices are in the k-simplex and their orientations are consistent with the orientation of the k-simplex. For example, when , we have:
| (10) |
We reiterate the second ILP formulation proposed in Ebrahimpour Boroojeny et al. [1]. Given an alignment graph and the oriented 2-simplex set ,
| (11) |
Entries in and correspond to 1-simplices and 2-simplices in and , respectively. is a boundary matrix where each entry is the signed coefficient of the oriented 1-simplex (the directed edge) in corresponding to in the boundary of the oriented 2-simplex in corresponding to . The index for each 1-simplex or 2-simplex is assigned based on an arbitrary ordering of the 1-simplices in or the 2-simplices in . An example of the boundary matrix is shown in Figure 3. is the cost of each edge. is a vector where each entry corresponds to a 1-simplex in with nonzero entries that represent one Eulerian trail in each input graph. is a feasible solution to the ILP. Let be the source of the Eulerian trail in , and be the sink of the Eulerian trail in . Each entry in is defined by
| (12) |
If the Eulerian trail is closed in can be any vertex in . An example of is shown in Figure 2(b).
Figure 3:
(a) A graph that contains an unoriented 2-simplex with three unoriented 1-simplices. (b), (c) The same graph with two different ways of orienting the simplices and the corresponding boundary matrices.
We provide a complete proof in Section B of the Appendix that the ILP in (5)–(8) is equivalent to the ILP in (11)–(12). Therefore, the example we provided in Section 3.2 is also an optimal solution to the ILP in (11)–(12) but not a solution to GTED. Thus, the ILP in (11)–(12) does not always solve GTED.
4. New ILP solutions to GTED
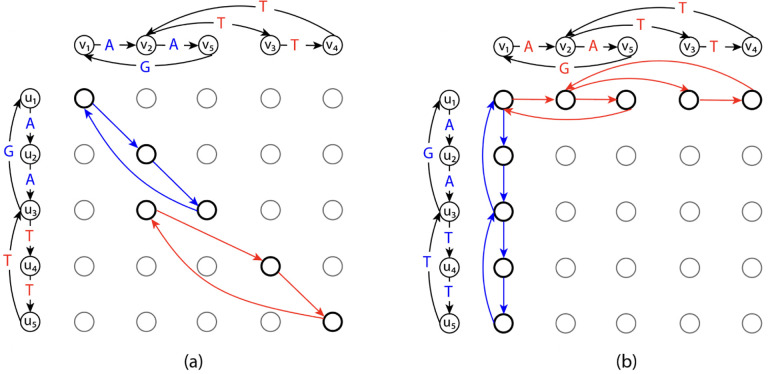
To ensure that our new ILP formulations are applicable to input graphs regardless of whether they contain an open or closed Eulerian trail, we add a source node and a sink node to the alignment graph. Figure 4 illustrates three possible cases of input graphs.
If only one of the input graphs has closed Eulerian trails, wlog, let be the input graph with open Eulerian trails. Let and be the start and end of the Eulerian trail that have odd degrees. Add edges and to for all nodes (Figure 4(a)).
If both input graphs have closed Eulerian trails, let and be two arbitrary nodes in and , respectively. Add edges and for all nodes and to (Figure 4(b)).
If both input graphs have open Eulerian trails, add edges and , where and are start and end nodes of the Eulerian trails in , respectively (Figure 4(c)).
Figure 4:
Modified alignment graphs based on input types. (a) G_1 has open Eulerian trails while G_2 has closed Eulerian trails. (b) Both G_1 and G_2 have closed Eulerian trails. (c) Both G_1 and G_2 have open Eulerian trails. Solid red and blue nodes are the source and sink nodes of the graphs with open Eulerian trails. “s” and “t” are the added source and sink nodes. Colored edges are added alignment edges directing from and to source and sink nodes, respectively.
According to Lemma 1, we can solve GTED by finding a trail in that satisfies the projection requirements. This is equivalent to finding a trail in that satisfies constraints:
| (13) |
where if the alignment edge projects to in . An optimal solution to GTED in the alignment graph must start and end with the source and sink node because they are connected to all possible starts and ends of Eulerian trails in the input graphs.
Since a trail in is a flow network, we use the following flow constraints to enforce the equality between the number of in- and out-edges for each node in the alignment graph except the source and sink nodes.
| (14) |
| (15) |
| (16) |
Constraints (13) and (16) are equivalent to constraints (7) and (6), respectively. Therefore, we rewrite the ILP in (5)–(8) in terms of the modified alignment graph.
| (lower bound ILP) |
As we show in Section 3.2, constraints (13)–(16) do not guarantee that the ILP solution is one trail in , thus allowing several disjoint covering trails to be selected in the solution and fails to model GTED correctly. We show in Section 5 that the solutions to this ILP is a lower bound to GTED.
According to Lemma 1 in Dias et al. [11], a subgraph of a directed graph with source node and sink node is a trail if and only if it is a flow network and every strongly connected component (SCC) of the subgraph has at least one edge outgoing from it. Thus, in order to formulate an ILP for the GTED problem, it is necessary to devise constraints that prevent disjoint SCCs from being selected in the alignment graph. In the following, we describe two approaches for achieving this.
4.1. Enforcing one trail in the alignment graph via constraint generation
Section 3.2 of Dias et al. [11] proposes a method to design linear constraints for eliminating disjoint SCCs, which can be directly adapted to our problem. Let be the collection of all strongly connected subgraphs of the alignment graph . We use the following constraint to enforce that the selected edges form one trail in the alignment graph:
| (17) |
where is the set of edges in the strongly connected subgraph and is the set of edges such that belongs to and does not belong to indicates that is in the subgraph of constructed by all edges with positive , and guarantees that there exists an out-going edge of that is in the subgraph.
We use the same technique as Dias et al. [11] to linearize the “if-then” condition in (17) by introducing a new variable for each strongly connected component:
| (18) |
| (19) |
| (20) |
| (21) |
To summarize, given any pair of unidirectional, edge-labeled Eulerian graphs and and their alignment graph GTED is equal to the optimal solution of the following ILP formulation:
| (exponential ILP) |
This ILP has an exponential number of constraints as there is a set of constraints for every strongly connected subgraph in the alignment graph. To solve this ILP more efficiently, we can use the procedure similar to the iterative constraint generation procedure in Dias et al. [11]. Initially, solve the ILP with only constraints (13)–(16). Create a subgraph, , induced by edges with positive . For each disjoint SCC in that does not contain the sink node, add constraints (18)–(21) for edges in the SCC and solve the new ILP. Iterate until no disjoint SCCs are found in the solution.
4.2. A compact ILP for GTED with polynomial number of constraints
In the worst cases, the number of iterations to solve (exponential ILP) via constraint generation is exponential. As an alternative, we introduce a compact ILP with only a polynomial number of constraints. The intuition behind this ILP is that we can impose a partially increasing ordering on all the edges so that the selected edges forms a trail in the alignment graph. This idea is similar to the Miller-Tucker-Zemlin ILP formulation of the Travelling Salesman problem (TSP) [12].
We add variables that are constrained to provide a partial ordering of the edges in the trail and set the variables to zero for edges that are not selected in the trail. Intuitively, there must exist an ordering of edges in a trail such that for each pair of consecutive edges and , the difference in their order variable and is 1. Therefore, for each node that is not the source or the sink, if we sum up the order variables for the incoming edges and outgoing edges respectively, the difference between the two sums is equal to the number of selected incoming/outgoing edges. Lastly, the order variable for the edge starting at source is 1, and the order variable for the edge ending at sink is the number of selected edges. This gives the ordering constraints as follows:
| (22) |
| (23) |
| (24) |
| (25) |
We enforce that all variables and for all .
The “if-then” statement in Equation (22) can be linearized by introducing an additional binary variable for each edge [11, 16]:
| (26) |
| (27) |
| (28) |
Here, is an indicator of whether . The coefficient is the number of edges in the alignment graph and also an upper bound on the ordering variables. When , and does not impose constraints on . When , and does not impose constraints on .
4.3. Correctness of (compact ILP) for GTED
To show that the optimal objective value of (compact ILP) is equal to GTED, we show that the optimal solutions to (compact ILP) always form one connected component.
Lemma 2. Let and be ILP variables. Let be a subgraph of that is induced by edges with . If and satisfy constraints (13)–(25) for all is connected with one trail from s to t that traverses each edge in exactly once.
Proof. We prove the lemma in 2 parts: (1) all nodes except and in have an equal number of in- and out-edges, (2) contains only one connected component.
The first statement holds because the edges of form a flow from to , and is enforced by constraints (16).
We then show that does not contain isolated subgraphs that are not reachable from or . Due to constraint (16), the only possible scenario is that the isolated subgraph is strongly connected. Suppose for contradiction that there is a strongly connected component, , in that is not reachable from or .
The sum of the left hand side of constraint (23) over all vertices in is
| (29) |
| (30) |
However, the right-hand side of the same constraints is always positive. Hence we have a contradiction. Therefore, has only one connected component. □
Due to Lemma 1 and Lemma 2, given input graphs and and the alignment graph GTED is equal to the optimal objective of
| (compact ILP) |
5. Closed-trail Cover Traversal Edit Distance
While the (lower bound ILP) and the ILP in (11)–(12) do not solve GTED, the optimal solution to these ILPs is a lower bound of GTED. These ILP formulations also solve an interesting variant of GTED, which is a local similarity measure between two genome graphs. We call this variant Closed-trail Cover Traversal Edit Distance (CCTED). In the following, we provide the formal definition of the CCTED problem and then show that the (lower bound ILP) is the correct ILP formulation for solving CCTED.
We first introduce the min-cost item matching problem between two multi-sets. Let two multi-sets of items be and , and, wlog, let . Let be the cost of matching either an empty item or an item in with an item in . Given and the cost function , min-cost matching problem finds a matching, , such that each item in is matched with exactly one distinct item in and the total cost of the matching, , is minimized.
The min-cost item matching problem is similar to the Earth Mover’s Distance defined in [17, except that only integral units of items can be matched and the cost of matching an empty item with another item is not constant. Similar to the Earth Mover’s Distance, the min-cost item matching problem can be computed using the ILP formulation of the min-cost max-flow problem [13, 14]. When the cost is the edit distance, the cost to match with a string is equal to the length of the string.
Define traversal edit distance, edit as the edit distance between the strings constructed from a pair of trails and . In other words, . CCTED is defined as:
Problem 3 (Closed-Trail Cover Traversal Edit Distance (CCTED)). Given two unidirectional, edge-labeled Eulerian graphs and with closed Eulerian trails, compute
| (31) |
Here, denotes the collection of all possible sets of edge-disjoint, closed trails in , such that every edge in belongs to exactly one of these trails. Each element of can be interpreted as a cover of using such trails. is a min-cost matching between two covers using the traversal edit distance as the cost.
CCTED is likely a more suitable metric comparison between genomes that undergo large-scale rearrangements. This analogy is to the relationship between the synteny block comparison [3] and the string edit distance computation, where the former is more often used in interspecies comparisons and in detecting segmental duplications [18, 19] and the latter is more often seen in intraspecies comparisons.
Following similar ideas as Lemma 1, we can compute CCTED by finding a set of closed trails in the alignment graph such that the total cost of alignment edges is minimized, and the projection of all edges in the collection of selected trails is equal to the multi-set of input graph edges.
Lemma 3. For any two edge-labeled Eulerian graphs and ,
| (32) |
| (33) |
where is a collection of trails and is the total cost of edges in trail .
Proof. Given any pair of covers and and their min-cost matching based on the edit distance , we can project each pair of matched closed trailed to a closed trail in the alignment graph. For a matching between a trail and the empty item , we can project it to a closed trail in the alignment graph with all vertical edges if the trail is from or horizontal edges if the trail is from . The total cost of the projected edges must be greater than or equal to the objective (32). On the other hand, every collection of trails that satisfy constraint (33) can be projected to a cover in each of the input graphs, and . Hence equality holds. □
5.1. The ILP formulation for CCTED
We show that the ILP in (5)–(8) proposed by Ebrahimpour Boroojeny et al. [1] solves CCTED.
Theorem 4. Given two input graphs and , the optimal objective value of the ILP in (5)–(8) based on is equal to CCTED.
Proof. As shown in the proof of Lemma 3, any pair of edge-disjoint, closed-trail covers in the input graph can be projected to a set of closed trails in , which satisfied constraints (6)–(8). The objective of this feasible solution, which is the total cost of the projected closed trails, equals CCTED. Therefore, CCTED is greater than or equal to the objective of the ILP in (5)–(8).
Conversely, we can transform any feasible solutions of the ILP in (5)–(8) to a pair of covers of and . We can do this by transforming one closed trail at a time from the subgraph of the alignment graph, induced by edges with ILP variable . Let be a closed trail in . Let and be two closed trails in and that are projected from . We can construct an alignment between and from by adding match or insertion/deletion columns for each match or insertion/deletion edges in accordingly. The cost of the alignment is equal to the total cost of edges in by the construction of the alignment graph. We can then remove edges in from the alignment graph and edges in and from the input graphs, respectively. The remaining edges in and and still satisfy the constraints (6)–(8). Repeat this process and we get a total cost of that aligns pairs of closed trails that form covers of and . This total cost is greater than or equal to CCTED.
5.2. CCTED is a lower bound of GTED
Since the constraints for (lower bound ILP) are a subset of (exponential ILP), a feasible solution to (exponential ILP) is always a feasible solution to (lower bound ILP). Since two ILPs have the same objective function, for any pair of graphs. Moreover, when the solution to (lower bound) ILP forms only one connected component, the optimal value of (lower bound ILP) is equal to GTED.
Theorem 5. Let be the subgraph of induced by edges with in the optimal solution to lower bound ILP. There exists that has exactly one connected component if and only if .
Proof. We first show that if , then there exists that has one connected component. A feasible solution to (exponential ILP) is always a feasible solution to (lower bound ILP), and since , an optimal solution to (exponential ILP) is also an optimal solution to (lower bound ILP), which can induce a subgraph in the alignment graph that only contains one connected component.
Conversely, if induces a subgraph in the alignment graph with only one connected component, it satisfies constraints (18)–(21) and therefore is feasible to the ILP for GTED (exponential ILP). Since , this solution must also be optimal for GTED. □
In practice, we may estimate GTED approximately by the solution to (lower bound ILP). As we show in Section 6, the time needed to solve (lower bound ILP) is much less than the time needed to solve GTED. However, in adversarial cases, could be zero but GTED could be arbitrarily large. We can determine if the is a lower bound on GTED or exactly equal to GTED by checking if the subgraph induced by the solution to (lower bound ILP) has multiple connected components.
5.3. NP-completeness of CCTED
We prove that the CCTED problem (Problem 3) is NP-complete by reducing from the Eulerian Trail Equaling Word problem [7].
Theorem 6. Computing CCTED is NP-complete.
Proof. Let Eulerian graph and be an instance of the Eulerian Tour Equaling Word problem. Construct two graphs, and . If contains open Eulerian trails, add an edge directing from the sink of the graph to the source of the graph. Let the label of the added edge be # that does not appear in . Let the modified graph be . If contains closed Eulerian trails, let be the same as . Let be a graph that contains one cycle with edges, where is the edge set of . Assign labels to the edges in such that the cycle in spells if contains closed Eulerian trails, otherwise.
If must contain at least one closed Eulerian trail that spells some circular permutation of . If CCTED is not zero, it means that must not match Eulerian trails in . □
6. Empirical evaluation of the ILP formulations for GTED and its lower bound
6.1. Implementation of the ILP formulations
We implement the algorithms and ILP formulations for (exponential ILP), (compact ILP) and (lower bound ILP). In practice, the multi-set of edges of each input graph may contain many duplicates of edges that have the same start and end vertices due to repeats in the strings. We reduce the number of variables and constraints in the implemented ILPs by merging the edges that share the same start and end nodes and record the multiplicity of each edge. Each variable is no longer binary but a non-negative integer that satisfies the modified projection constraints (13):
| (34) |
where is the multiplicity of edge in . Let be the strongly connected component in the subgraph induced by positive , now is no longer upper bounded by . Therefore, constraints (19) is changed to
| (35) |
where is the maximum total multiplicities of edges in the strongly connected subgraph in each input graph that is projected from .
Likewise, constraints (27) that set the upper bounds on the ordering variables also need to be modified as the upper bound of the ordering variable for each edge no longer represents the order of one edge but the sum of orders of copies of that are selected, which is at most . Therefore, constraint (27) is changed to
| (36) |
The rest of the constraints remain unchanged.
We ran all our experiments on a server with 48 cores (96 threads) of Intel(R) Xeon(R) CPU E5–2690 v3 @ 2.60GHz and 378 GB of memory. The system was running Ubuntu 18.04 with Linux kernel 4.15.0. We solve all the ILP formulations and their linear relaxations using the Gurobi solver [20] using 32 threads.
6.2. GTED on simulated TCR sequences
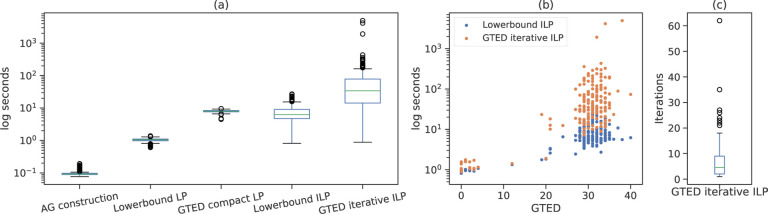
We construct 20 de Bruijn graphs with using 150-character sequences extracted from the V genes from the IMGT database [21]. We solve the linear relaxation of (compact ILP), (exponential ILP) and (lower bound ILP) and their linear relaxation on all 190 pairs of graphs. We do not show results for solving (compact ILP) for GTED on this set of graphs as the running time exceeds 30 minutes on most pairs of graphs.
To compare the time to solve the ILP formulations when GTED is equal to the optimal objective of (lower bound ILP), we only include 168 out of 190 pairs where GTED is equal to the lower bound (GTED is slightly higher than the lower bound in the remaining 22 pairs). On average, it takes 26 seconds wall-clock time to solve (lower bound ILP), and 71 seconds to solve (exponential ILP) using the iterative algorithm. On average, it takes 9 seconds to solve the LP relaxation of (compact ILP) and 1 second to solve the LP relaxation of (lower bound ILP). The time to construct the alignment graph for all pairs is less than 0.2 seconds. The distribution of wall-clock running time is shown in Figure 5(a). The time to solve (exponential ILP) and (lower bound ILP) is generally positively correlated with the GTED values (Figure 5(b)). On average, it takes 7 iterations for the iterative algorithm to find the optimal solution that induces one strongly connected subgraph (Figure 5(c)).
Figure 5:
(a) The distribution of wall-clock running time for constructing alignment graphs, solving the ILP formulations for GTED and its lower bound, and their linear relaxations on the log scale. (b) The relationship between the time to solve (lower bound ILP), (exponential ILP) iteratively and GTED. (c) The distribution of the number of iterations to solve exponential ILP. The box plots in each plot show the median (middle line), the first and third quantiles (upper and lower boundaries of the box), the range of data within 1.5 inter-quantile range between Q1 and Q3 (whiskers), and the outlier data points.
In summary, it is fastest to compute the lower bound of GTED. Computing GTED exactly by solving the proposed ILPs on genome graphs of size 150 is already time consuming. When the sizes of the genome graphs are fixed, the time to solve for GTED and its lower bound increases as GTED between the two genome graphs increases. In the case where GTED is equal to its lower bound, the subgraph induced by some optimal solutions of (lower bound ILP) contains more than one strongly connected component. Therefore, in order to reconstruct the strings from each input graph that have the smallest edit distance, we generally need to obtain the optimal solution to the ILP for GTED. In all cases, the time to solve the (exponential ILP) is less than the time to solve the (compact ILP).
6.3. GTED on difficult cases
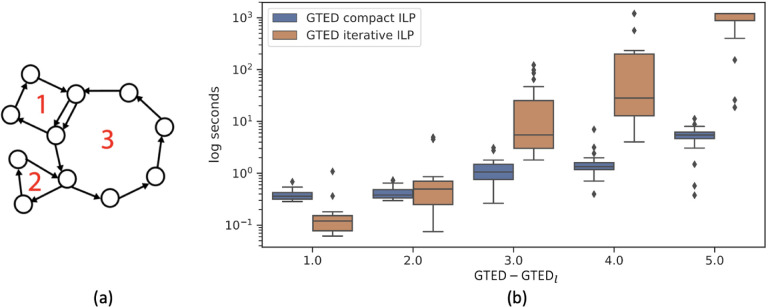
Repeats, such as segmental duplications and translocations [22, 23] in the genomes increase the complexity of genome comparisons. We simulate such structures with a class of graphs that contain simple cycles of which peripheral cycles are attached to the -th central cycle at either a node or a set of edges (Figure 6(a)). The input graphs in Figure 2 belong to this class of graphs that contain 2 cycles. This class of graphs simulates the complex structural variants in disease genomes or the differences between genomes of different species.
Figure 6:
(a) An example of a 3-cycle graph. Cycle 1 and 2 are attached to cycle 3. (b) The distribution of wall-clock time to solve the compact ILP and the iterative (exponential ILP) on 100 pairs of 3-cycle graphs.
We generate pairs of 3-cycle graphs with varying sizes and randomly assign letters from to edges. We compute the lower bound of GTED and GTED using (lower bound ILP) and (compact ILP), respectively. We denote the lower bound of GTED computed by solving (lower bound ILP) as GTEDl. We group the generated 3-cycle graph pairs based on the value of and select 20 pairs of graphs randomly for each value ranging from 1 to 5. The maximum number of edges in all selected graphs is 32.
We show the difficulty of computing GTED using the iterative algorithm on the 100 selected pairs of 3-cycle graphs. We terminate the ILP solver after 20 minutes. As shown in Figure 6, as the difference between GTED and increases, the wall-clock time to solve (exponential ILP) for GTED increases faster than the time to solve (compact ILP) for GTED. For pairs on graphs with , on average it takes more than 15 minutes to solve (exponential ILP) with more than 500 iterations. On the other hand, it takes an average of 5 seconds to solve (compact ILP) for GTED and no more than 1 second to solve for the lower bound. The average time to solve each ILP is shown in Table S1. In summary, on the class of 3-cycle graphs introduced above, the difficulty to solve GTED via the iterative algorithm increases rapidly as the gap between GTED and increases. Although (exponential ILP) is solved more quickly than (compact ILP) for GTED when the sequences are long and the GTED is equal to (Section 6.2), (compact ILP) may be more efficient when the graphs contain overlapping cycles such that the gap between GTED and is larger.
7. Conclusion
We point out the contradictions in the result on the complexity of labeled graph comparison problems and resolve the contradictions by showing that GTED, as opposed to the results in Ebrahimpour Boroojeny et al. [1], is NP-complete. On one hand, this makes GTED a less attractive measure for comparing graphs since it is unlikely that there is an efficient algorithm to compute the measure. On the other hand, this result better explains the difficulty of finding a truly efficient algorithm for computing GTED exactly. In addition, we show that the previously proposed ILP of GTED [1] does not solve GTED and give two new ILP formulations of GTED.
While the previously proposed ILP of GTED does not solve GTED, it solves for a lower bound of GTED, and we show that this lower bound can be interpreted as a more “local” measure, CCTED, of the distance between labeled graphs. Further, we characterize the LP relaxation of the ILP in (11)–(12) and show that, contrary to the results in Ebrahimpour Boroojeny et al. [1], the LP in (11)–(12) does not always yield optimal integer solutions.
As shown previously [1, 13], it takes more than 4 hours to solve (lower bound ILP) for graphs that represent viral genomes that contain ≈ 3000 bases with a multi-threaded LP solver. Likewise, we show that computing GTED using either (exponential ILP) or (compact ILP) is already slow on small genomes, especially on pairs of simulated genomes that are different due to segmental duplications and translations. The empirical results show that it is currently impossible to solve GTED or its lower bound directly using this approach for bacterial- or eukaryotic-sized genomes on modern hardware. The results here should increase the theoretical interest in GTED along the directions of heuristics or approximation algorithms as justified by the NP-hardness of finding GTED.
Acknowledgements
The authors would like to thank the members of the Kingsford Group for their helpful comments throughout this project, in particular Guillaume Marçais. The authors thank Marina L Knittel, Jacob M Gilbert, and Cenk Sahinalp for their insightful discussion on the NP-completeness of CCTED. This work was supported in part by the US National Science Foundation [DBI-1937540, III-2232121], the US National Institutes of Health [R01HG012470] and by the generosity of Eric and Wendy Schmidt by recommendation of the Schmidt Futures program.
Appendix A. Proofs for the NP-completeness of GTED
A.1. Reduction from ETEW to GTED
We provide below the complete proof for Theorem 1.
Theorem 1. If GTED ∈ then ETEW ∈.
Proof. Let be an instance of ETEW. Construct a directed, acyclic graph (DAG), , that has only one path. Let the path in be and the edge label of be . Clearly, is a unidirectional, edge-labeled Eulerian graph, is the only Eulerian trail in , and .
For the graph from the ETEW instance, which may not be unidirectional, create another graph that contains all of the nodes and edges in except the anti-parallel edges. Let , where is a character that is not in . For each pair of anti-parallel edges and in , add four edges by introducing new vertices to . Let and . Let for every newly introduced vertex. has at most twice the number of edges as and is Eulerian and unidirectional.
Define the cost of changing a character from to for to be 0 if and 1 otherwise. “−” is the gap character indicating an insertion or a deletion. Define with to be 1. Define to be 0.
Use the (assumed) polynomial-time algorithm for GTED to ask whether under edit distance . If yes, then let be the 0-cost alignment of the strings spelled out by the trails in and , respectively. The non-gap characters of must spell out since there is only one Eulerian trail in . Because the alignment cost is 0, any − (gap) characters in must be aligned with characters in and any non-gap characters in must be aligned to the same character in . The trail in that spells can be transformed to a trail that spells by collapsing the edges with character labels, and .
If must not contain an Eulerian trail that spells . Otherwise, such a trail could be extended to a trail introducing some characters that could be aligned to with zero cost by aligning gaps with characters.
Hence, an (assumed) polynomial-time algorithm for GTED solves ETEW in polynomial time. □
A.2. Reduction from Hamiltonian Path to GTED
We provide below the complete proof for Theorem 2.
Theorem 2. GTED is NP-complete.
Proof. We reduce from the Hamiltonian Path problem, which asks whether a directed, simple graph contains a path that visits every vertex exactly once. Here simple means no self-loops or parallel edges. Let be an instance of Hamiltonian Path, with vertices. The reduction is almost identical to that presented in Kupferman and Vardi [7], and from here until noted later in the proof the argument is identical except for the technicalities introduced to force unidirectionality (and another minor change described later). The first step is to construct the Eulerian closure of , which is defined as where
| (37) |
and is the union of the following sets of edges and their labels:
, labeled a,
, labeled b,
, labeled c,
, labeled c,
, labeled c,
, labeled b.
Since is connected and every outgoing edge in has a corresponding antiparallel incoming edge, is Eulerian. It is not unidirectional, so we further create from by adding dummy nodes to each pair of antiparallel edges and labelling the length-2 paths so created with , where is the original label of the split edge (a, b, or c) and # is some new symbol (shared between all the new edges). We call these length-2 paths introduced to achieve unidirectionality “split edges”.
We now argue that has a Hamiltonian path iff has an Eulerian trail that spells out
| (38) |
If such an Eulerian trail exists, then the trail starts with spelling the string , which corresponds to a Hamiltonian trail in since it visits exactly “vertex split edges” (type , labeled a#) and each vertex split edge can be used only once (since it is an Eulerian trail). Further, successively visited vertices must be connected by an edge in since those are the only b# split edges in (except those leaving , but must not be involved in spelling out , since entering requires using a split edge labeled c#).
For the other direction, if a has a Hamiltonian path , then walking that sequence of vertices in will spell out . This path will cover all edges and the edges that are on the Hamiltonian path. Retracing the path so far in reverse will use split edges labeled c#, consuming the term in and covering all nodes’ reverse vertex edges (since the path is Hamiltonian). The reverse path also covers the edges corresponding to reverse Hamiltonian path edges. Our Eulerian trail is now “at” node .
What remains is to complete the Eulerian walk covering (a) edges and their antiparallel counterparts corresponding to edges in that were not used in the Hamiltonian path, and (b) the edges adjacent to node . To do this, define be the vertices in for which edge exists and is not the predecessor of along the Hamiltonian path. For each , traverse the split edge labeled c# to then traverse the forward split edge labeled b# back to . This results in a string . Once the predecessors of are exhausted, traverse the split edge labeled c# from into node and then traverse the split edge labeled b# to . This again generates a c#b# string. Repeat the process, covering the edges of ’s predecessors and returning to to move to the next node along the Hamiltonian path for each node . After covering the predecessors of , go to through the remaining edges in and and , which completes the Eulerian tour. This covers all the edges of . The word spelled out in this last section of the Eulerian trail is a sequence of repetitions of c#b#, with one repetition for each edge that is not in the Hamiltonian path and all of the edges in and for entering and leaving each node , with a total of repetitions, which is the final term in .
This ends the slight modification of the proof in Kupferman and Vardi [7], where the differences are (a) the introduction of the # characters and (b) using the exponent of the final part of instead of as in Kupferman and Vardi [7] since we create -edges only to vertices. (This second change has no material effect on the proof, but reduces the length of the string that must be matched.)
Now, given an instance of Hamiltonian Path, with vertices, we construct as above (obtaining a unidirectional Eulerian graph) and create graph that only represents string . Note that and and can be constructed in polynomial time. if and only if an Eulerian path in spells out , since there can be no indels or mismatches. By the above argument, an An eulerian tour that spells out exists if and only if has a Hamiltonian path. □
A.3. FGTED is NP-complete
Problem 4 (Flow Graph Traversal Edit Distance (FGTED) [13]). Given unidirectional, edge-labeled Eulerian graphs and , each of which has distinguished source and sink vertices, compute
| (39) |
where flow is the collection of all possible sets of trail decomposition of saturating flow from to , strset is the multi-set of strings constructed from trails in .
Theorem 3. FGTED is NP-complete.
Proof. Let be an instance of the Hamiltonian Cycle problem. Let be the number of vertices in . Construct the Eulerian closure of and split the anti-parallel edges. Let the new graph be . Attach a source and a sink node to an arbitrary node by adding edge and with labels s and t, respectively.
Construct a string , such that
| (40) |
Create a graph that only contains one path with labels on the edges of the path that spell the string . The union of the set of trails in any flow decomposition of is equal to a set of Eulerian trails, , that starts at and ends at . All Eulerian trails in are also closed Eulerian trails of that starts and ends at .
Using the same line of argument in the proof of Theorem 2, an Eulerian trail in that spells is equivalent to a Hamilton Cycle in . In addition, if and only if all Eulerian trails in spell out . Therefore, if , then there is a Hamiltonian Cycle in . Otherwise, then there must not exist a Hamiltonian Cycle in . □
Appendix B. Equivalence between two ILPs proposed by Ebrahimpour Boroojeny et al.
The analysis provided by Ebrahimpour Boroojeny et al. [1] states that the LP relaxation of the ILP in (5)–(8) does not always yield integer solutions, but the LP relaxation of the ILP in (11)–(12) always yields integer solutions. This suggests that the two LP relaxations have difference feasibility regions for . We show that these two LP relaxations are actually equivalent in Theorem 7, Further, we show that the ILP in (5)–(8) and the ILP in (11)–(12) are also equivalent. Since the ILP in (5)–(8) does not solve for as shown in 3.2, we conclude that the ILP in (11)–(12) also does not solve .
Theorem 7. Given two unidirectional, edge-labeled Eulerian graphs , the feasibility region of in the LP relaxation of the ILP in (11)–(12) is the same as the feasibility region of in the LP relaxation of the ILP in (5)–(8).
Let be the alignment graph of and , and let be its two-simplex set. First, we have the following result:
Lemma 4. Let be a vector such that the -th entry of is equal to 0 for all . The vector satisfies the constraints (6)–(7) if the vector satisfies the constraints (6)–(7).
Proof. Let be the 2-simplex corresponding to the entry of . Based on the construction of has two forms: or . Without loss of generality, we assume . We can prove this lemma by using the same way when . Since
We have
where , and is a vector such that all the entries are 0 except that the one corresponding to edge is 1. we also let be a vector such that all the entries are 0 except that the one corresponding to vertex is 1. Therefore, we have
where , and . Hence, satisfies the constraint (6) if satisfies the constraint (6).
In addition, since , and:
and for other ,
and for other ,
, and for other ,
we have:
,
,
for any other and .
Therefore, , meaning that satisfies the constraint (7) if satisfies the constraint (7). □
With Lemma 4, we prove that any feasible solution of in (11) is a feasible solution of (5)–(8). First, it is easy to check that satisfies the constraints (6)–(7). For each feasible solution of in (11), since , by iteratively using Lemma 4, we get that satisfies the constraints (6)–(7). Since for all is a constraint existing in both linear relaxations, is a feasible solution of (5)–(8).
We now show that any feasible solution of (5)–(8) is a feasible solution of (11). Let be a feasible solution of (5)–(8). We show that is also a feasible solution of (11) by proving that can be converted to in (11) via the boundary operator . First, if there is a diagonal edge in such that , then it can be replaced by the horizontal edge followed by the vertical edge by using one boundary operation on the 2-simplex . Hence, can be converted to a new vector , such that , and all the other entries in are the same as those in . It is easy to check that is also a feasible solution of (5)–(8). Therefore, without loss of generality, we assume to be a vector such that all the entries corresponding to diagonal edges in are zero.
We then prove that any can be converted to in (11) via the boundary operator. Let the source and the sink node of in be and , where is the source node of and is the sink node of . When the Eulerian trail is closed (meaning that it is an Eulerian tour) in , we let be an arbitrary vertex in can be seen as a trail (tour) in that starts from , walks along an Eulerian trail of via all the horizontal edges ,
and then walks along an Eulerian trail of via all the vertical edges ,
until the sink node . Here is an Eulerian trail of and is an Eulerian trail of . We use to denote the trail from to that is the concatenation of and . It is easy to see that each edge in is unique.
As shown in Qiu and Kingsford [13, is a flow of with the additional constraint (7). Therefore, according to the flow decomposition theorem [24, p. 80], can be decomposed into a finite set of weighted paths in from to , which is denoted as , and a finite set of weight cycles in , which is denoted as . Each path or cycle only contains horizontal and vertical edges.
For path , we use a vector to represent ,
| (41) |
By using the boundary operator, each path can actually be converted to a new trail such that each edge in is also an edge in . To prove this, we consider the following two cases:
If walks along all the horizontal edges followed by all the vertical edges, then every edge in is an edge in . To see that, let be an horizontal edge in , since starts from has the form where . Since corresponds to the Eulerian trail of , for each , we have . Therefore . We can use the same way to prove when is a vertical edge. Note that in this case, the number of horizontal edges or vertical edges can be zero.
If not, then we let , and let be the vertical edge with the smallest index . There exists an integer such that are all vertical edges and is an horizontal edge. We denote each vertical edge as and denote as . It is easy to see that when . By using the boundary operator, this subpath can be replaced by another subpath with one horizontal edge followed by vertical edges:
Now we have a new path, denoted as , in which the smallest index of the vertical edges becomes . Figure 7(a) shows an example, in which the blue line represents the subpath of and the red line represents the new subpath in .
Figure 7:
(a) An example of converting three vertical edges followed by one horizontal edge (blue line) to one horizontal edge followed by three vertical edges (red line). It can be done by doing boundary operations on 2-simplices labeled from 0 to 5. (b) An example of a cycle path (red line) and its auxiliary trail (blue line).
To create a new vector that represents , we first create a zero vector , and from to , we iteratively update via the following equations:
| (42) |
The vector is the one that represents .
Since the length of is finite, by doing such a transformation a finite number of times, we can convert to a new path such that walks along all the horizontal edges first followed by all the vertical edges, therefore each edge in is also an edge in . We use the vector to represent where is the number of transformations. Apperantly, when . Let , we have .
For cycle , we also use a vector to represent ,
| (43) |
Let be an arbitrary chosen node in , we construct a trail that passes as follows:
From , walk along until the node . It corresponds to a part of an Eulerian trail of .
From , walk along an Eulerian trail of to . It must passes the node .
From , walk along the remaining part of the Eulerian trail of to the node .
Figure 7(b) shows an example, in which the blue line represents and the red line represents .
We use to denote the vector representing . The combination of and , represented by the vector creates a new trail (may have repeated edges) from to : (1) walk along from to (2) walk along from to itself, and (3) walk along the remaining part of from to . By using the same way as we described above, each or can be converted to a new trail in which each edge is also an edge in . We use or to represent the new trail accordingly, therefore, we have and . Likewise, when .
We define a new vector such that:
Therefore, is a vector converted from via boundary operations. is equal to because:
when since when for each .
As we have proved above, the boundary operator preserves the constraints (6)–(7). Therefore, satisfies the constraints (6)–(7) since is a feasible solution of (5)–(8). Combined with the first point, we have that if and otherwise, meaning that .
Hence, for each feasible solution of (5)–(8), we have:
meaning that is also a feasible solution of (11).
We proved that the feasibility region of in (11) is the same as the feasibility region of in (5)–(8), and since the objective functions of these two linear relaxations are the same, the optimal solutions of them are equal.
By employing the same approach and taking into account that if all edge weights in a flow network are non-negative integers, the flow decomposition theorem guarantees that the network can be decomposed into a finite set of weighted paths and cycles, each with positive integer weight, we can prove that the ILP in (5)–(8) and the ILP in (11)–(12) are also equivalent.
Based on the proof, we can conclude that the way to index the vertices or edges in the alignment graph, or the 2-simplices in , will not affect the equivalence result. Additionally, different choices of orientations for the 2-simplices in will also not impact the equivalence result. This is because for any two sets and containing the same 2-simplices with the same indices but different orientations, if is a feasible solution of the ILP in (11)–(12) (or its relaxation) that corresponds to , then is a feasible solution of the ILP in (11)–(12) (or its relaxation) that corresponds to , where when has the same orientation as , and when has the opposite orientation to . Therefore, it is acceptable to specify a particular orientation for each 2-simplex when defining .
Appendix C. The linear relaxation of the ILP in (11)–(12) does not always yield integer solutions
C.1. is not necessarily totally unimodular
A linear programming formulation always yields integer solutions if its constraint matrix is totally unimodular, which means that all of its square submatrices have determinants of 0, −1 or 1 [25]. To show that the constraint matrix of the LP relaxation of the ILP in (11)–(12) is not totally unimodular, we first write the LP in standard form.
In a standard form of a LP, all variables are greater than, or equal to 0. Since vectors in the LP relaxation of the ILP in (11)–(12) can contain negative entries, we decompose it into . Given alignment graph and , we can now write the standard form of the LP in (11)–(12) as
| (44) |
Hence the constraint matrix of the LP relaxation is . According to the characteristics of a totally unimodular matrix [26, p. 280] is not totally unimodular if is not totally unimodular. We show that is not TU when the input graphs satisfy the constraints given in the following theorem.
Theorem 8. Given two unidirectional, edge-labeled Eulerian graphs and where and , the boundary matrix constructed from and is not totally unimodular if there is a vertex or such that there are at least 3 unique edges in or that are incident to . Here, unique edges are edges that connect to at one end but have different endpoints at the other end.
Proof. To prove that the boundary matrix is not TU, we only need to show that it is not TU under one specific chosen orientation for 1− and 2-simplices, as well as one specific chosen set of indices for 1− and 2-simplices. This is because changing the orientations or indices of 1-simplices in or 2-simplices in corresponds to permuting rows and columns of or multiplying rows and columns of by −1, which preserves the total unimodularity [26, p. 280].
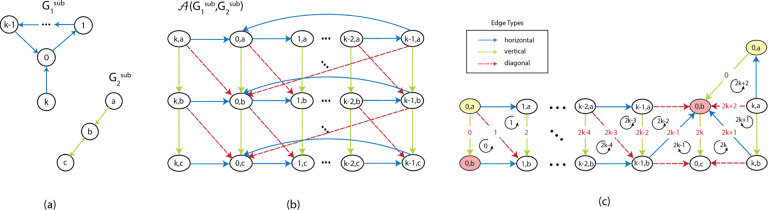
Without loss of generality, let be a node that is incident to at least 3 unique edges. Since is an Eulerian graph, must be part of a cycle in . Also, there must exist another node and an edge between and in either direction, such that the edge between and is not contained in cycle (Figure 8 (a)). Suppose the number of nodes in the cycle is due to the unidirectionality constraint), and let the cycle . Since a specific choice of 1-simplex orientations does not affect the total unimodularity of the boundary matrix, we assume the edge between and is without loss of generality. We use to denote the subgraph with and . Since and is a connected graph, there exist two consecutive, directed edges in . We use to denote the subgraph of with and . The alignment graph is formed with and and is a subgraph of , therefore, each subgraph of is also a subgraph of . Similarly, the 2-simplex set is a subset of .
Figure 8:
(a) Subgraphs and of input graphs and . Dots represent a path from node 1 to with middle nodes omitted. (b) The alignment graph with different edges labeled with colors. (c) A subgraph of the alignment graph in (b) with edges and triangles numbered. Dots represent horizontal and diagonal edges omitted. The same vertices that are repeated in (c) are marked with yellow and red filling colors.
We extract a sequence of 2-simplices (Figure 8(c)), , from ) via following steps:
Extract all oriented 2-simplices and for from . Flip the orientations of for all , obtaining . Use to denote , and to denote .
Add to the sequence another five oriented 2-simplices from in the order as specified:
In total, we extract a sequence of oriented 2-simplices, , such that and share one edge. The extracted 2-simplices and their orientations as well as all shared edges are shown in Figure 8(c). We flip the orientations of solely to ensure that the submatrix constructed below has a simple form, which makes it easier to compute the determinant.
Based on , we obtain , a submatrix of where each roll corresponds to a shared edge and each column corresponds to a 2-simplex in . The entry values of are the signed coefficients of each selected 1-simplex from the boundaries of selected 2-simplices.
The determinant of is:
Since the determinant of is −2, and is a submatrix of , is not totally unimodular. □
The minimal pair of input graphs that satisfy the conditions in Theorem 8 is a graph with one 3-node cycle and one additional edge incident to the cycle and an acyclic, connected graph with three nodes. In practice, most non-trivial edge-labeled Eulerian graphs satisfy these conditions.
According to the definitions in Dey et al. [25], the subgraph used to construct in the above proof (Figure 8(c)) is a Möbius subcomplex, and is a -Möbius cycle matrix (MCM). Theorem 8 also establishes that there may exist a Möbius subcomplex in an alignment graph, which corrects the false claim made in Lemma 2 in [1].
Theorem 2 in Ebrahimpour Boroojeny et al. [1] attempts to employ a more algebraic approach to attempt to demonstrate that is TU by establishing that the alignment graph is a Möbius-free product space. However, the property of being Möbius-free globally does not imply the absence of Möbius subcomplexes locally. As we show in Theorem 8, although the alignment graph is homotopically equivalent to the one-dimensional circle, which is Möbius-free, it still contains a Möbius subcomplex.
C.2. The LP yields optimal fractional solutions
The fact that is not totally unimodular does not guarantee that the LP in (11)–(12) has a fractional optimal objective value. In this section, we prove that the LP in (11)–(12) does not always yield integer optimal solutions by constructing a specific example with a fractional optimal objective value.
Theorem 9. The LP in (5)–(8) and the LP in (11)–(12) do not always yield optimal integer solutions.
We prove the above theorem by giving an example where the LP in (5)–(8) yields a fractional optimal solution. Since by Theorem 7, two LPs are equivalent, it follows that the LP in (11)–(12) also yields the same fractional optimal solution.
Construct and such that their edges and edge labels are equal to the ones specified in Figure 9 (a). Let the edge multi-set of be . We assign an edge cost to 0 if the edge matches two equal characters and 1 otherwise. Construct vector and set entries corresponding to edges in Figure 9 (b) to 0.5 except edge to which the corresponding entry is set to 1. Set the rest of the entries of to 0.
Figure 9:
An example of a fractional optimal solution to the LP in (11)–(12) and the LP in (5)–(8). (a) A pair of input graphs to the LP in (5)–(8) and the LP in (5)–(8). Letters in red are edge labels. (b) A subgraph of that is induced by alignment edges with non-zero weights (blue font) in an optimal solution to the LPs. The letters in red show the matching between the edge labels or between edge labels and gaps.
Lemma 5. is an optimal solution to the LP in (5)–(8) constructed with and .
Proof. We prove the optimality of via complementary slackness. We first write the LP in (5)–(8) in standard form.
| (45) |
Here, is a vector of size where each entry is cost of edge . The constraint matrix of the primal LP (45) has columns and rows, where is the vertex set of , and and are edge multi-sets of the input graphs. The first rows correspond to the constraints specified in (6). The rest of the rows correspond to the constraints in (7) that enforce the projected multi-set of edges to be equal to the multi-set of edges in each input graph. Since the input graphs both contain Eulerian tours, the vector has size , where the first entries are zeroes and the rest of the entries are 1 s.
We write the dual form of LP (45) as follows.
| (46) |
Let the objective value of LP (45) given a as input is , and the objective value of LP (46) given a as input is . To show that is an optimal solution to the LP in (5)–(8), we need to show that there exists a feasible solution to the dual LP, , that satisfies the complementary slackness conditions and that .
Since each alignment edge has two endpoints and is projected to at most one edge in each graph, there are at most 4 non-zero entries in each column of . The variables in of the dual form can be interpreted in three parts. Each of the first entries of can be assigned to each vertex in the alignment graph, and the next entries can be assigned to edges in and the last entries can be assigned to edges in . There are constraints in the dual LP, and the -th constraint can be assigned to one edge in the alignment graph has cost . Therefore, each constraint that is assigned to a horizontal or a vertical edge can be written as
| (47) |
where if is a horizontal edge, and if is a vertical edge. and are the entries that are assigned to the vertices that are the start and end of edge , and are the entries that assigned to the .
Similarly, each constraint that is assigned to a diagonal edge is
| (48) |
We can verify that is a feasible solution of the primal form (45) by checking if constraints (6)–(7) are satisfied. The primal objective value can be computed in a straightforward way, and we can obtain .
According to complementary slackness conditions, since for edges shown in Figure 9(b), the corresponding constraints in the dual LP (46) must be tight, meaning that the equality must hold in these constraints. The rest of the dual constraints could have slacks.
Let the subgraph of shown in Figure 9(b) be . Denote the cycle that traverses from to be and the 4-node cycle that traverses be . Denote the concatenation of two cycles with . The projected cycle from to is
| (49) |
The projected cycle from to is
| (50) |
Sum up all the constraints that are assigned edge where . Since these edges form a cycle, we get:
| (51) |
| (52) |
| (53) |
| (54) |
The summed edge cost is 7 as there are 7 edges that are either mismatch edges or vertical edges.
All entries that correspond to vertices are free variables and are in every constraint. After fixing the variables that satisfy constraint (54), the rest of the variables can be set to satisfy the dual cosntraint. We now obtain which is a feasible solution to the dual LP.
The only entries in that could have non-zero dual costs are those that correspond to edges in and . Since these corresponding dual costs are all 1,
□
Since the costs of alignment graph edges are all integers, the fact that the LP in (11)–(12) and the LP in (5)–(8) yield fractional optimal objective values mean that they must yield fractional solutions and assign fractional values to entries in . Theorem 9 follows. Since the LP in (11)–(12) yields fractional solutions and GTED is always an integer, solving the LP in (11)–(12) does not solve GTED.
Appendix D. The average wall-clock time to solve ILPs on 3-cycle graphs
Table S1:
The average wall-clock time to solve (lower bound ILP), (exponential ILP), (compact ILP) and the number of iterations for pairs of 3-cycle graphs for each GTED - GTEDl.
| GTED - GTEDl | (lower bound ILP) runtime (s) | GTED iterative runtime (s) | Iterations | GTED compact runtime (s) |
|---|---|---|---|---|
| 1.0 | 0.06 | 0.17 | 3.55 | 0.39 |
| 2.0 | 0.05 | 0.87 | 13.00 | 0.43 |
| 3.0 | 0.08 | 25.41 | 67.60 | 1.24 |
| 4.0 | 0.07 | 205.59 | 179.10 | 1.70 |
| 5.0 | 0.08 | 943.68 | 502.85 | 5.37 |
Footnotes
The source code to reproduce experimental results is available at https://github.com/Kingsford-Group/gtednewilp/.
Conflict of Interest: C.K. is a co-founder of Ocean Genomics, Inc.
References
- [1].Boroojeny Ali Ebrahimpour, Shrestha Akash, Sharifi-Zarchi Ali, Gallagher Suzanne Renick, Sahinalp S. Cenk, and Chitsaz Hamidreza. Graph traversal edit distance and extensions. Journal of Computational Biology, 27(3):317–329, 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [2].Pevzner Pavel A, Tang Haixu, and Waterman Michael S. An Eulerian path approach to DNA fragment assembly. Proceedings of the National Academy of Sciences of USA, 98(17):9748–9753, 2001. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [3].Polevikov Evgeny and Kolmogorov Mikhail. Synteny paths for assembly graphs comparison. In 19th International Workshop on Algorithms in Bioinformatics (WABI 2019). Schloss Dagstuhl-Leibniz-Zentrum fuer Informatik, 2019. [Google Scholar]
- [4].Minkin Ilia and Medvedev Paul. Scalable pairwise whole-genome homology mapping of long genomes with Bubbz. IScience, 23(6):101224, 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [5].Mangul Serghei and Koslicki David. Reference-free comparison of microbial communities via de Bruijn graphs. In Proceedings of the 7th ACM international conference on bioinformatics, computational biology, and health informatics, pages 68–77, 2016. [Google Scholar]
- [6].Huntsman Steve and Rezaee Arman. De Bruijn entropy and string similarity. arXiv preprint arXiv:1509.02975, 2015. [Google Scholar]
- [7].Kupferman Orna and Vardi Gal. Eulerian paths with regular constraints. In Faliszewski Piotr, Muscholl Anca, and Niedermeier Rolf, editors, 41st International Symposium on Mathematical Foundations of Computer Science (MFCS 2016), volume 58 of Leibniz International Proceedings in Informatics (LIPIcs), pages 62:1–62:15, Dagstuhl, Germany, 2016. Schloss Dagstuhl-Leibniz-Zentrum fuer Informatik. ISBN 978-3-95977-016-3. [Google Scholar]
- [8].Jain Chirag, Zhang Haowen, Gao Yu, and Aluru Srinivas. On the complexity of sequence-to-graph alignment. Journal of Computational Biology, 27(4):640–654, 2020. [Google Scholar]
- [9].Needleman Saul B and Wunsch Christian D. A general method applicable to the search for similarities in the amino acid sequence of two proteins. Journal of Molecular Biology, 48(3):443–453, 1970. [DOI] [PubMed] [Google Scholar]
- [10].Dantzig George, Fulkerson Ray, and Johnson Selmer. Solution of a large-scale traveling-salesman problem. Journal of the Operations Research Society of America, 2(4):393–410, 1954. [Google Scholar]
- [11].Dias Fernando HC, Williams Lucia, Mumey Brendan, and Tomescu Alexandru I. Minimum flow decomposition in graphs with cycles using integer linear programming. arXiv preprint arXiv:2209.00042, 2022. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [12].Miller Clair E, Tucker Albert W, and Zemlin Richard A. Integer programming formulation of traveling salesman problems. Journal of the ACM (JACM), 7(4):326–329, 1960. [Google Scholar]
- [13].Qiu Yutong and Kingsford Carl. The effect of genome graph expressiveness on the discrepancy between genome graph distance and string set distance. Bioinformatics, 38:i404–i412, 2022. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [14].Rubner Yossi, Tomasi Carlo, and Guibas Leonidas J. The Earth Mover’s distance as a metric for image retrieval. International Journal of Computer Vision, 40(2):99–121, 2000. [Google Scholar]
- [15].Munkres James R. Elements of algebraic topology. CRC Press, 2018. [Google Scholar]
- [16].Bradley Stephen P, Hax Arnoldo C, and Magnanti Thomas L. Applied mathematical programming. Addison-Wesley, 1977. [Google Scholar]
- [17].Pele Ofir and Werman Michael. A linear time histogram metric for improved sift matching. In Computer Vision-ECCV 2008: 10th European Conference on Computer Vision, Marseille, France, October 12–18, 2008, Proceedings, Part III 10, pages 495–508. Springer, 2008. [Google Scholar]
- [18].Bourque Guillaume, Pevzner Pavel A, and Tesler Glenn. Reconstructing the genomic architecture of ancestral mammals: lessons from human, mouse, and rat genomes. Genome Research, 14(4):507–516, 2004. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [19].Vollger Mitchell R, Guitart Xavi, Dishuck Philip C, Mercuri Ludovica, Harvey William T, Gershman Ariel, Diekhans Mark, Sulovari Arvis, Munson Katherine M, Lewis Alexandra P, et al. Segmental duplications and their variation in a complete human genome. Science, 376(6588):eabj6965, 2022. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [20].Gurobi Optimization, LLC. Gurobi Optimizer Reference Manual, 2023. URL https://www.gurobi.com.
- [21].Lefranc Marie-Paule. IMGT, the international ImMunoGeneTics information system. Cold Spring Harbor Protocols, 2011(6):595–603, 2011. [DOI] [PubMed] [Google Scholar]
- [22].Li Yilong, Roberts Nicola D, Wala Jeremiah A, Shapira Ofer, Schumacher Steven E, Kumar Kiran, Khurana Ekta, Waszak Sebastian, Korbel Jan O, Haber James E, et al. Patterns of somatic structural variation in human cancer genomes. Nature, 578(7793): 112–121, 2020. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [23].Darai-Ramqvist Eva, Sandlund Agneta, Müller Stefan, Klein George, Imreh Stefan, and Kost-Alimova Maria. Segmental duplications and evolutionary plasticity at tumor chromosome break-prone regions. Genome Research, 18(3):370–379, 2008. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [24].Ahujia Ravindra K, Magnanti Thomas L, and Orlin James B. Network flows: Theory, algorithms and applications. New Jersey: Prentice-Hall, 1993. [Google Scholar]
- [25].Dey Tamal K, Hirani Anil N, and Krishnamoorthy Bala. Optimal homologous cycles, total unimodularity, and linear programming. SIAM Journal on Computing, 40(4): 1026–1044, 2011. [Google Scholar]
- [26].Schrijver Alexander. Theory of linear and integer programming. John Wiley & Sons, 1998. [Google Scholar]