Summary
Security and privacy have always been key concerns for individuals in various edge-assisted services. In this paper, we present a feasible quantum solution to an important primitive of secure multiparty computations, i.e., Secure Multiparty Logical AND (SMLA), in which n participants can securely compute logical AND of n private bits. In order to ensure perfect security and achieve good feasibility, we introduce a semi-honest edge server and two non-collusive fog nodes, and design a secure and feasible edge-assisted quantum protocol for SMLA, which cleverly utilizes Secure Multiparty XOR to implement SMLA group by group. Furthermore, we focus on applications of this quantum primitive protocol and design two quantum protocols for Multiple Private Set Intersection and Anonymous One-vote Veto. Compared with classical related protocols, our proposed quantum protocols obtain higher security, which can be guaranteed by the basic principles of quantum mechanics.
Subject areas: Quantum Metrology and Physics
Graphical abstract
Highlights
-
•
A quantum protocol for computing XOR of multiple private bits is proposed
-
•
A quantum protocol for computing logical AND of multiple private bits is built
-
•
Two application protocols of proposed quantum AND protocol are designed
Quantum Metrology and Physics
Introduction
With the rapid development of cloud/edge computing, there have appeared various cloud-based and edge-based applications, e.g., cloud-based data storage1 and edge-based data services (outsourcing services).2 Furthermore, in order to control the access to the data stored in the cloud/edge, generally, it needs to encrypt the data before uploading them by using novel cryptographic algorithms, e.g., attribute-based encryption3,4 and identity-based proxy re-encryption.5,6 However, it is difficult for most classical cryptographic algorithms to ensure long-term security of the data stored in the remote cloud due to upcoming quantum computers and fast quantum algorithms.7,8,9 Especially, quantum supremacy (or quantum advantage) has been demonstrated,10,11 so classical cryptography will certainly face lots of threats and challenges.
Furthermore, as an important branch of modern cryptography, quantum cryptography can ensure information-theoretical security and accordingly provide long-term security, which are guaranteed by the principles of quantum mechanics.12 Quantum cryptography was formally introduced by C.H. Bennett, et al. in 1984 by first presenting BB84 quantum key distribution (QKD) protocol.13 Since that, quantum cryptography has attracted a lot of scientific attention from the cryptography community. Besides QKD, quantum cryptography covers a wide range of research areas, e.g., quantum secret sharing,14 quantum perfect encryption,15 quantum signature,16 quantum secure direct communication,17 quantum key agreement,18 and so on.
On the other hand, secure multiparty computation (SMC), which allows a group of mutually distrustful participants to compute a joint function of their respective private inputs without revealing private input of each participant, has various applications in data sharing and privacy-preserving settings, such as electronic voting,19 electronic auction,20 and federated learning.21 Correspondingly, there have appeared many quantum solutions to all kinds of specific SMC problems, e.g., quantum anonymous voting,22 quantum sealed-bid auction,23 quantum private set intersection,24 quantum secret permutating,25 and so on.
In this paper, to enhance security and privacy, we attempt to construct primitive protocols of SMC by introducing quantum information technologies, i.e., to construct quantum protocols for computing bitwise logical XOR and AND (i.e., product) of multiple private bits, which can be adopted to implement more complicated functions as basic blocks. When designing quantum primitive protocols, we mainly focus on two factors: higher security and better feasibility. In order to achieve these goals, we employ single photons as quantum resources, and accordingly perform single-photon operators and measurements. Finally, we investigate novel applications of these quantum primitive protocols in edge-based environments.
Our main contributions in this paper are summarized as follows.
-
(1)
We first present a quantum protocol for computing XOR of multiple private bits with single photons and single-photon measurements, i.e., Edge-assisted Secure Multiparty XOR (ESMX) Quantum Protocol, which can guarantee information-theoretical security.
-
(2)
Based on proposed ESMX quantum protocol, we further present a feasible edge-assisted quantum protocol for computing logical AND (i.e., logical product) of multiple private bits by grouping and computing group by group, i.e., Edge-assisted Quantum Protocol for Secure Multiparty Logical AND (SMLA), which can ensure information-theoretical security.
-
(3)
We design two application protocols of Edge-assisted Quantum Protocol for SMLA, i.e., Quantum Protocol for Multiparty Private Set Intersection (MPSI) and Quantum Protocol for Anonymous One-vote Veto (AOV), which can achieve perfect security and good feasibility.
Related works
Secure Multiparty Logical AND
Logical AND (i.e., logical product) is an important and fundamental arithmetic operation in evaluating Boolean expressions or Boolean functions. Recently, we defined a new SMC problem in ref.,26 i.e., Secure Multiparty Logical AND (SMLA for short), in which multiple participants can jointly compute bitwise logical AND of their respective private bits. As a primitive of SMC, there are many promising applications of SMLA in distributed cryptographic tasks, e.g., Secret Sharing and Private Set Intersection (PSI)/Union. In ref.,26 we proposed a novel quantum SMLA protocol by using phase-matching quantum conference key agreement and perfect quantum encryption. In this previously proposed quantum SMLA protocol, the most critical process is to adopt three-qubit Toffoli gates to generate -qubit entangled states. However, it is still difficult to prepare and transmit high-fidelity entangled states in high-dimensional Hilbert space. So, it is of great significance to find a feasible and efficient quantum solution to SMLA.
Multiparty Private Set Intersection
In 2004, M.J. Freedman et al.27 first defined PSI, in which two participants jointly compute the intersection of two private sets without revealing any private set, and presented a PSI protocol by using homomorphic encryption and oblivious polynomial evaluation.
In 2016, Shi et al.28 first designed a cheat-sensitive quantum protocol for PSI based on phase-encoded quantum privacy query, which could output the intersection of two private sets. Furthermore, in order to reveal less privacy information, Shi et al. presented a constant-round quantum protocol for PSI Cardinality (PSI-CA),29 which could output the intersection cardinality of two private sets, instead of any element of the intersection. Compared with the classical related protocols, this quantum PSI-CA protocol has higher security and lower communication complexity. However, it requires additional assumptions for the cardinality of two private sets,29 which might limit its wider applications. Later, in ref.,30 Shi successfully discarded these assumptions and presented a robust quantum PSI-CA protocol without any limitation.
However, these previously proposed quantum protocols still need the complicated oracle operators. Furthermore, in order to enhance the feasibility, Shi et al. introduced a non-collusive third party to assist two legitimate parties to compute the intersection cardinality based on single photons31 and Bell states.32 Most recently, Liu et al. designed an improved PSI-CA protocol with single photons by using Bloom filter.33
In addition, Shi et al.,34 Zhang et al.,35 and Wang et al.36 generalized two-party PSI-CA to multi-party PSI-CA and presented the corresponding multi-party quantum PSI-CA (PUI-CA) protocols. To the best of our knowledge, currently, there is not any quantum protocol for MPSI.
Like QKD, the feasibility of quantum PSI/PSI-CA protocols is the focus of research. However, there are two intractable problems to implement these existing quantum PSI/PSI-CA protocols: one is to find a fully trusted third party in the cyber or virtual world and the other is to implement the complicated (oracle) operators and measurements in high-dimensional Hilbert space.
Please note that an oracle operator is an arbitrary unitary transformation theoretically in arbitrary n-dimension Hilbert space as a “black box”. For example, . Here, the operator can be viewed as an oracle operator. Generally, for an oracle operator, we focus on what it does and we do not consider how to implement it. Therefore, it has always been our goal to design the practical and feasible quantum PSI/PSI-CA protocols with the present quantum technology.
Anonymous voting
The first electronic voting protocol based on classical cryptography was proposed by David Chaum in 1981.19 Subsequently, there appeared many electronic voting protocols.37,38,39,40 Similarly, in order to resist the attack of quantum computers, quantum voting has attracted extensive attention of scholars.
In 2006, Hillery presented two quantum voting models,41 i.e., traveling ballot model and distributed ballot model. In 2007, Vaccaro et al. defined the basic security properties that quantum voting should meet.42 Later, there were lots of well-known quantum voting protocols satisfying different security properties.43,44,45,46
In 2015, Rahaman et al. presented an anonymous veto protocol without any trusted third party.47 In this protocol, suppose that there are a group of jury members, who need to take a unanimous decision, but at the same time want their individual decisions to remain secret, i.e., without disclosing the identity of possible vetoing member. Rahaman’s protocol utilizes generalized multi-qubit Greenberger-Horne-Zeillinger (GHZ) states as quantum resources. However, it is very difficult to implement this multi-qubit GHZ state. In 2021, Wu et al. proposed a novel anonymous veto protocol based on polarized single photons.48 Wu’s protocol needs a semi-honest server to assist all voters to complete this cryptographic task, but a dishonest server can reveal partial privacy information.
Results and discussion
Proposed protocols
We first describe the definition of SMLA as follows.
Definition 126
SMLA: Suppose that there are () participants: , , …, , each of which owns a private bit . After executing the SMLA protocol, it outputs , where and is the logical AND operation. In addition, this protocol should satisfy the following requirements:
Correctness
If all parties honestly execute this protocol, then the final output is equal to , i.e., the output is correct.
Privacy
Anyone else but the participant cannot get any private information about except the final output .
Fairness
Under no circumstances one participant should have an advantage over another or other parties to get the final output or more private information.
Please note that logical AND is equivalent to logical product, i.e., Furthermore, only if all s are equal to 1, then . Otherwise .
In addition, it is widely known that perfect secure two-party computations, including classical two-party computation (e.g., bit commitment or oblivious transfer), cannot be implemented in theory by the no-go results.49,50,51 However, in our defined ESMX Quantum Protocol and Edge-assisted Quantum Protocol for SMLA there are more than two participants, which are not belong to secure two-party computations. As we know, though it is impossible to implement unconditionally secure two-party computations, there are unconditionally secure multi-party computations (), e.g., Shamir’s secret sharing and quantum secret sharing. We do not try to evade this type of attack, but our proposed protocols are not bound by the no-go theorem.
System model
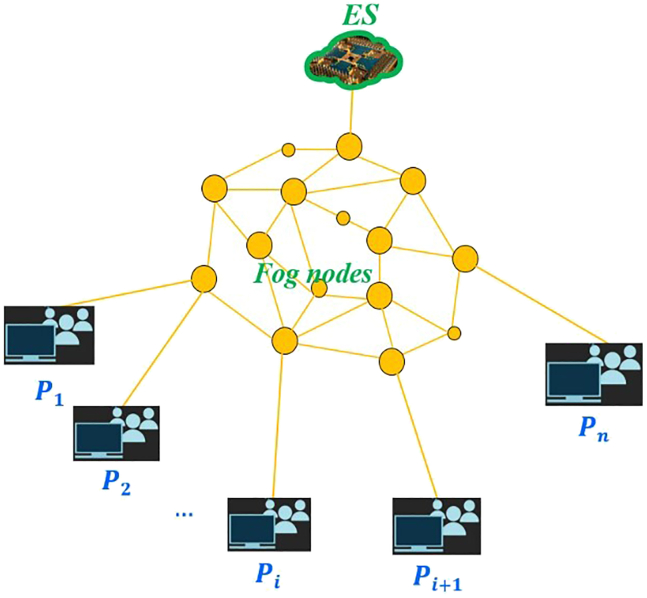
In our system model, suppose that there is an edge server (ES for short), several fog nodes (e.g., and ), and participants: , , …, . Here, the ES is taken as a mini cloud and a fog node is defined as a quantum computing and routing device, and further the ES and participants can communicate by the quantum network composed of several fog nodes, as shown in Figure 1.
Figure 1.
System model
In this model, each participant () has a private bit and the ES and the fog nodes will assist participants to compute the logical AND of all private bits. Furthermore, we assume that all participants (including the ES and the fog nodes) are semi-honest and any two-third parties (i.e., the fog nodes or the ES) are non-collusive. In addition, we assume that there are authenticated quantum channels and authenticated classical channels between any two neighboring parties.
Finally, our security goal is to ensure the privacy of each participant, i.e., the privacy of the input bit .
Protocols
Here, we first present an edge-assisted quantum protocol for securely computing XOR of private bits with single photons and single-photon measurements, which will be utilized later in proposed quantum protocol for computing SMLA.
Edge-assisted Secure Multiparty XOR Quantum Protocol
Step 1. All participants including the ES agree on a small integer , where , e.g., or 5.
Step 2. The ES generates single photons: , , …, and , where each single photon () is randomly in one of four polarized states {|0⟩, |1⟩, |+⟩, |⎯⟩}.
Step 3. After the ES records the initial states of all single photons, he sends the photon sequence {, , …, } to the participant through authenticated quantum channel.
Step 4. After receiving the photon sequence sent from the ES, the participant performs the operator on each single photon for , where , and and are defined by
| (Equation 1) |
| (Equation 2) |
By Equations 1 and 2, we can easily deduce that and . Please note that both and are randomly and privately selected by the participant .
Step 5. After performing the corresponding operators, the participant further sends all single photons to the next participant through authenticated quantum channel.
Step 6. After receiving single photons sent from the previous participant , the participant executes the similar procedure: to first perform the operator on the th single photon for and then send all single photons to the next participant through authenticated quantum channel.
Step 7. The similar process will be executed times in total. Finally, the participant performs the corresponding operators and sends all single photons back to the ES through authenticated quantum channel.
Step 8. After receiving single photons, i.e., , , …, and , the ES measures each photon in the initial basis for . Furthermore, if the measured result of each photon is the same as the initial state, then the ES sets . Otherwise, he sets .
Step 9. The ES informs all participants of selecting successful events among all events corresponding to single photons as follows: Each participant () opens their partial secrets, i.e., for , while he keeps the other secrets, i.e., for . Furthermore, all participants select out successful events, satisfying the condition of , where is the sequence number of the successful event.
Step 10. All participants select out a successful event as the encoding event and other successful events as the checking events. Here, we assume that the sequence number of the encoding event is .
Step 11. For all checking events, all participants ask the ES to announce the corresponding s. Then, all participants open their corresponding s for . Furthermore, all participants determine whether is equal to for all checking events. If for any checking event, then they will terminate this protocol. Otherwise, they will continue to execute the next step.
Step 12. For the encoding event, each participant () computes and sends to the ES through authenticated classical channel, where is his private input.
Please note that we assume that each participant and the ES have a common key distributed by QKD protocol in advance, and they encrypt the classical message with the key by the one-time pad method.
Step 13. The ES computes and outputs as the final XOR of all private bits.
In the next section, we will focus on how to efficiently solve SMLA with feasible quantum resources, operators, and measurements. On the one hand, in order to ensure the feasible solution of SMLA, we try to divide all participants into different groups, where each group just includes three participants. Furthermore, we compute the logical AND of three private bits group by group. If all AND results of all groups are equal to 1, then the final AND of all private bits is equal to 1. Otherwise, it is certainly equal to 0. On the other hand, in order to achieve the feasibility, we attempt to compute the logical AND of each group by using different XORs in the corresponding group. For example, we consider a group with three private bits: , , and . Clearly, if we know that , and , , and , then we can easily deduce that (i.e., ). Otherwise .
Based on the aforementioned proposed XOR protocol, i.e., ESMX Quantum Protocol, we further present Edge-assisted Quantum Protocol for SMLA, which is described in detail as follows.
Edge-assisted Quantum Protocol for SMLA
Step 1 (Grouping). ①All participants publicly agree on the number of groups , where is the number of all participants, and a small integer , such that . ②Each participant generates a -bit secret as follows: For , he prepares a photon in the superposition state and then measures it in the computational basis, i.e., {, }; If the measured result is in , then , and otherwise. Here denotes the th bit of the secret . ③According to his/her secret , each participant is privately divided into the th group.
Please note that there are groups initially. Since , there are about groups and each group has about 3 participants due to uniformness and randomness of quantum measurements.
Step 2 (Counting). ① Each participant () generates a 0/1 vector with components, where the th components is equal to 1 if he/she belongs to the th group, and all other components are equal to 0. For example, if there are 4 groups in total and he/she belongs to the third group, then his private vector is equal to (0,0,1,0). Furthermore, he/she takes his/her private vector as an 8-nary vector and computes the corresponding integer . For example, (0,0,1,0) is corresponding to the integer 8.
Note: In order to avoid the carry, we utilize 8-nary vectors to encode private information, since each group has about 3 participants.
②Each participant () privately generates a polynomial function of degree () over ():
| (Equation 3) |
where and .
③Each participant () computes the shares of all participants by the polynomial function:
| (Equation 4) |
④Each participant () sends the share to the corresponding participant for () through authenticated classical channels.
⑤Each participant () computes the summation of his own shares:
| (Equation 5) |
Furthermore, he/she sends to the ES through authenticated classical channel.
⑥After the ES receiving shares, he can recover the following secret by using the Lagrange interpolation method:
| (Equation 6) |
That is,
| (Equation 7) |
As an 8-nary integer, conversely, is converted by the ES to a -component vector (, , …, ), where the th component represents the number of participants in the th group (Note. ).
Step 3 (Amending). ①If , then the ES will play the role of a virtual participant whose input bit is equal to 1 and be added into the th group until . ②If , then all participants in the th group will be subdivided into two subgroups by the similar grouping procedures in Step 1. Accordingly, the number of group (i.e., ) will be increased by 1. After amending the number of participants per group, we will assume that each group just has three participants in the next steps and there are groups in total, i.e., .
Step 4 (Ordering). The ES calls all participants to execute the following procedures: //determining the computing order of each participant in each group.
For do
{①Each participant in the th group randomly generates a 3-component vector, where only one component is equal to 1, and the other components are equal to 0, e.g., (0,1,0), (1,0,0), or (0,0,1). However, the other participants not in the th group generate the same 3-component vector: (0,0,0). Here, we assume that each group exactly has 3 participants and there are participants (i.e., ).
②The ES called all participants to parallelly execute ESMX Quantum Protocols to compute the XORs of the corresponding components of private vectors, as shown in Figure 2.
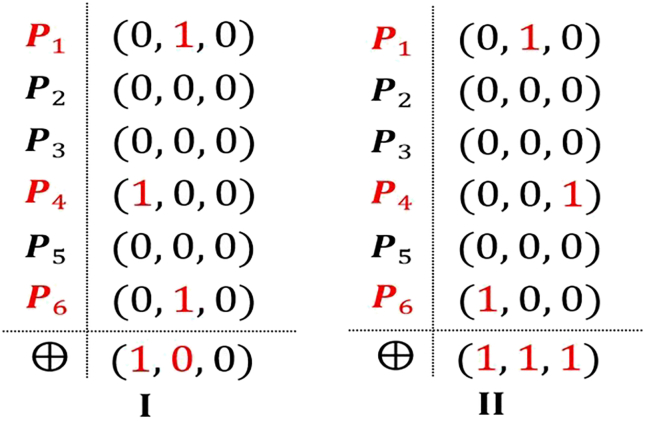
Figure 2.
An example of computing the XORs to verify the uniqueness of the position indexes
I and II denote the unsuccessful case and the successful case, respectively, where , , and belong to a group.
③If the XORs are not equal to 111, then it implies that the position indexes of the components which are equal to 1 selected by different participants in the th group are not unique. For example, three vectors are (0,1,0), (1,0,0), and (0,1,0), respectively, and all other vectors are (0,0,0). Accordingly, the XORs are (1,0,0), not (1,1,1). Furthermore, the ES informs all participants of regenerating their respective vectors of this group to again verify the uniqueness (i.e., go to ①).
④If the XORs are equal to 111, then it means that the position indexes of the components which are equal to 1 selected by different participants in the th group are unique. Accordingly, the position indexes will be treated as the computing orders in the later computing step.
For example, there are three participants: , , and , in the th group, and they generate three 3-component vectors: (0,1,0), (1,0,0), and (0,0,1), respectively. Obviously, the XORs are equal to 111, so the computing orders of three participants will be corresponding to 2, 1, and 3. Furthermore, the private inputs of three participants in the th group will be denoted as , , and , respectively. That is, , , and . Clearly, each participant in this group only knows his/her computing order, while other participants including the ES cannot know it.
}
Step 5 (Computing). Here, we assume that there are groups in total and each group has exactly 3 participants. Please note that each participant knows which group he/she belongs to and knows his/her computing order in the group, but others cannot know this private information. The ES calls all participants to execute the following procedures:
For do {//computing group by group
①The ES asks the fog node to assist all participants to securely compute , i.e., , where , , and denote private bits of three participants in the th group. That is, call all participants to execute ESMX Quantum Protocol, where all participants in the th group input their real private bits while other participants input 0.
Furthermore, sends to the ES through secure classical channel. Similarly, each fog node and the ES have a common key distributed by QKD protocol in advance, and they encrypt the classical message with the key by the one-time pad method.
If , then the ES returns 0 (and ends this protocol). That is, not all of , , and are equal to 1. So, we can deduce that . If , then they will continue to execute the next procedures.
② The ES asks the fog node to assist all participants to securely compute , , and , where , , and denote private bits of three participants in the th group. That is, call all participants to execute ESMX Quantum Protocol three times, where the participants in the th group input their real private bits or 0, while other participants input 0. Please note that each participant in this group knows his/her computing order.
Furthermore, computes and sends to the ES through secure classical channel.
If is not equal to 0, then the ES returns 0 (and ends this protocol). That is, .
}//end for.
Finally, if the ES does not return 0 in the aforementioned For loop, then it implies that the logical AND of each group is equal to 1. So, . That is, the ES finally outputs 1.
Analysis
In this section, we will analyze the correctness and the security of proposed quantum protocols. We first analyze the correctness and the security of ESMX Quantum Protocol, which are described as Theorem 1 and Theorem 2.
Theorem 1
When all parties honestly executing this protocol, ESMX Quantum Protocol is correct.
Proof. According to this protocol, we can get from Step 12 and from Step 13. So, we can further get
| (Equation 8) |
Furthermore, we investigate the relation between the initial state of any photon prepared by the ES and the corresponding final state after all participants performing their respective operators. Without loss of generality, we assume the initial state and the final state of the th photon are denoted as and , respectively. According to this protocol, we can get
| (Equation 9) |
Given from Equations 1 and 2, we can easily get the following equation
| (Equation 10) |
Accordingly, we can deduce the following equation
| (Equation 11) |
where if is odd number, and otherwise. Since , we can get
| (Equation 12) |
Later, all participants select out the successful events, which satisfy the condition of . That is, for the successful events, it should satisfy
| (Equation 13) |
In addition, Pauli operator can also be written as
| (Equation 14) |
Furthermore, {, , , }. Accordingly, we can get
| (Equation 15) |
| (Equation 16) |
| (Equation 17) |
| (Equation 18) |
So, for the encoding event, we can easily deduce
| (Equation 19) |
Finally, according to Equations 8 and 19, we can get
| (Equation 20) |
Therefore, ESMX Quantum Protocol is correct.
Theorem 2
When all parties honestly execute the protocol, ESMX Quantum Protocol is information-theoretically secure.
Proof.
In our proposed XOR quantum protocol, each participant first performs the operator on every receiving photons and then forwards it to the next participant through authenticated quantum channel. Later, after successful post-selections, each participants hides by using , i.e., he/she sends to the ES through secure and authenticated classical channel.
We first prove that proposed protocol can ensure information-theoretical security of the secret selected randomly by each participant. By Ref. 15, if the output state is a totally mixed state for every input state , the quantum protocol is information-theoretically secure, that is, the relation of the input state and the output state should satisfy the following condition:
| (Equation 21) |
where is the density matrix of every input state of single qubit and is the corresponding unitary operator applied to the input state. Here, the subscript of the operator is equivalent to the key utilized to encrypt the input state .
Furthermore, by our proposed XOR quantum protocol, all possible input states of any single photon prepared by the ES should be in one of four polarized states {, , , }.
If the input state is in , i.e., , then we can get
| (Equation 22) |
If the input state is in , i.e., , then we can get
| (Equation 23) |
If the input state is in , i.e., , then we can get
| (Equation 24) |
If the input state is in , i.e., , then we can get
| (Equation 25) |
From (Equation 22), (Equation 23), (Equation 24), (Equation 25), we can see that the output of the qubit (i.e., after the participant performing private operator) is always a totally mixed state. Therefore, it is equivalent to a perfect quantum encryption, in which it encrypts one qubit by using two bits. Since is selected privately and randomly by each participant and his/her performing operator on each transmitted photon is equivalent to implementing a perfect quantum encryption, anyone else except himself/herself cannot get any private information about , i.e., is information-theoretically secure.
Later, each participant sends to the ES through secure classical channel. Since the ES or any eavesdropper cannot get any private information about except for (), so it is also equivalent to encrypt with the key based on the classical one-time pad method.
In addition, the condition of the successful event must satisfy , where is randomly selected by the -th participant for the -th photon. Clearly, the probability of the successful events among all events is equal to . In order to ensure there exist at least a successful event as the encoding event, so . Furthermore, to ensure the security of quantum channels against outsider eavesdroppers, our proposed quantum XOR protocol still needs other successful events as the checking events except the encoding event. For the checking events, all participants ask the ES to open the corresponding measured result and further check the honesty of the ES and determine whether there is an outside eavesdropper. Generally, we can set . For example, . Accordingly, there is about a successfully encoding event and two successfully checking events. If is too small, then it cannot ensure the security of quantum channels.
Therefore, our proposed XOR quantum protocol can ensure the information-theoretical security of each private input, i.e., .
Furthermore, we analyze the correctness and the security of Edge-assisted Quantum Protocol for SMLA, which are described as Theorem 3, Theorem 4, and Theorem 5.
Theorem 3
When all parties honestly executing this protocol, Edge-assisted Quantum Protocol for SMLA is correct.
Proof. This protocol includes five steps: grouping, counting, amending, ordering, and computing. Furthermore, we analyze the correctness of each step in detail.
-
(1)
Grouping: In this step, each participant can get a -bit secret by performing single-photon measurements times, where and . Here, and are determined by all parties in advance. Furthermore, each participant will be privately divided into the th group, and accordingly there are groups initially. Please note that single-photon measurements of each participant are independent. What’s more, due to uniformness and randomness of quantum measurements, each group has about 3 participants and there are approximate groups (), which achieve the desired aims.
-
(2)
Counting: According to his/her grouping secret , each participant can generate a -component vector and further compute the corresponding integer of the vector as an 8-nary vector . Then, all participants utilize Shamir Secret Sharing to compute the summation, . Furthermore, as an 8-nary integer, in turn, is converted to a -component vector (, , …, ). In fact, we implement the summation of their respective vectors by using the conversion between 8-nary vector and integer. There are about 3 participants per group, while we use 8-nary conversion, so there is no carry when computing the bitwise summation of these vectors. In addition, if the participant belongs to the th group, then his/her 8-nary vector is (0, …,0,1,0,…0), i.e., only the th component is equal to 1 and other components are equal to 0. Accordingly, we can easily deduce that the th component of finally converted vector is equal to the summation of the th components of all 8-nary vectors because there is no carry. Therefore, the th component just represents the number of participants in the th group.
-
(3)
Amending: After the second step, the ES knows the vector (, , …, ), each of which represents the number of participants in each group. Furthermore, if , then the ES will be added into the th group as a virtual participant, whose input is set to 1. As we know, for any . So, though there is a virtual participant with an input of 1, the final AND remains unchanged. In addition, if , then all participants in this group will be subdivided into two subgroups by the similar grouping procedures. Accordingly, the number of groups will be increased by 1. Finally, after amending the number of participants per group, each group just has three participants.
-
(4)
Ordering: The correctness of this step can refer to Figure 2. Given from Figure 2, we can know that if the XORs of the position indexes are equal to 111 (please see Figure 2-II), it implies that the position indexes of 3 participants in a certain group are unique, so their corresponding position indexes can be treated as their computing orders in the next computing step.
-
(5)
Computing: On the one hand, the logical AND of a certain group is equal to 0, then we can easily deduce the final AND is equal to 0. Furthermore, if all logical ANDs of all groups are equal to 1, then we can know the final AND is equal to 1. On the other hand, for each group, there are exactly 3 participants. We assume their private inputs are , , and , respectively, where . If “” and “, , and ”, then we can easily deduce that . Accordingly, .
To sum up, when all parties honestly executing this protocol, Edge-assisted Quantum Protocol for SMLA is correct.
Theorem 4
Suppose that all parties honestly executing this protocol and any two-third parties, i.e., the fog nodes or the ES, are non-collusive, Edge-assisted Quantum Protocol for SMLA is information-theoretically secure.
Proof. Similarly, we analyze the security of each step as follows.
-
(1)
Grouping: In this step, each participant performs a measurement on a superposition state to generate a random bit, where the superposition state is prepared by himself/herself. Accordingly, there are two kinds of possible results, and , like flipping a coin. Clearly, grouping of each participant is done by himself/herself. So, the measured result is fully unknown to anyone else except himself/herself. Therefore, the grouping information of each participant is perfectly private, i.e., it is information-theoretically secure.
-
(2)
Counting: In this step, all participants jointly compute the summation by using Shamir Secret Sharing. So, the security of this step is guaranteed by Shamir Secret Sharing, which had been proven to be information-theoretically secure.
-
(3)
Amending: Adding a virtual participant or subdividing a group cannot reveal any private information about grouping of each participant.
-
(4)
Ordering: In a certain group, each private 0/1 vector with 3 components is selected privately and randomly by himself/herself. Later, the ES assists three participants in the group to compute the bitwise XORs of all vectors with 3 components, including 3 real but private vectors and zero vectors, by executing ESMX Quantum Protocol three times, which has been proven to be information-theoretically secure. So, the computing order of each participant in the group is perfectly private.
-
(5)
Computing: In this step, the ES asks two fog nodes to assist all participants to compute “”, and “, , and ” by executing ESMX Quantum Protocol four times. Every time ESMX Quantum Protocol is executed, it always requires that all participants take part in the computation, where the participants whose private bits are contained in the target formula (task) input real bits, while other participants input 0. That is, all participants exchange information only by using ESMX Quantum Protocol. In addition, the ES only knows that and , but he cannot get , , or . Therefore, ESMX Quantum Protocol ensures the security of this step.
To sum up, when all parties honestly executing this protocol, Edge-assisted Quantum Protocol for SMLA is information-theoretically secure.
Theorem 5
Edge-assisted Quantum Protocol for SMLA is fair.
Proof. On the one hand, there is nothing to connect the initial order of each participant (e.g., of ) with the privacy of input bits and the probability of getting the final output, because each participant cannot get any private information of others due to information-theoretical security and he/she can get the correct output at a probability of 100% when all parties honestly execute this protocol. On the other hand, each participant executes the same procedures, e.g., grouping, counting, ordering, and computing. So, each participant in our protocol is perfectly peer entity and he/she has the same probability to get the final output. Therefore, this protocol is fair.
Applications
There are many promising applications of SMLA in novel data services, e.g., privacy-preserving scientific computing in cloud-assisted smart grids and federated learning in blockchain-based Internet of Things. In this section, we mainly focus on its applications in MPSI and AOV.
Multiparty Private Set Intersection
Definition 2 (Multiparty Private Set Intersection)
Suppose that there are participants: , , …, (, each of which has a private set over . After executing this protocol, a designated edge server (i.e., ES) outputs . Similarly, it should satisfy the following requirements:
Correctness
If all parties honestly execute this protocol, then the final output is equal to , i.e., the output is correct.
Privacy
Anyone else but the participant cannot get any private information about except the final output .
Fairness
Under no circumstances one participant should have an advantage over another or other parties to get the final output or more private information.
There are important and wide applications of MPSI in modern society, e.g., privacy-preserving smart advertisement and recommendation system, privacy-preserving individual credit information query among many banks, and privacy-preserving data statistics in contact tracing for health authorities to fight the outbreaks of highly contagious diseases.
In the following section, we will present a novel quantum protocol for MPSI based on Edge-assisted Quantum Protocol for SMLA.
Quantum Protocol for MPSI
Step 1. Each participant () secretly encodes his/her private set over into a 0/1 vector with components: , where if belongs to for , and otherwise.
Step 2. The ES executes the following procedures:
Set .// denotes the intersection, which is empty initially.
For to do {
The ES asks for all participants to compute by using Edge-assisted Quantum Protocol for SMLA, where is the private input of the participant for .
If then . }
Step 3. Finally, the ES outputs the intersection , i.e., .
Correctness
If , i.e., , then . That is, . Accordingly, . Therefore, this protocol is correct.
Security
Clearly, Edge-assisted Quantum Protocol for SMLA ensures perfect privacy of each participant. Furthermore, all participants are equivalent entities, and they can get the final output with equal opportunities. So, it is also fair.
Anonymous One-vote Veto
Definition 3 (Anonymous One-vote Veto)
Suppose that there are voters: , , …, (), each of which has a private input () corresponding to his voting will. That is, if , then it means that the voter will vote “for the proposal”; otherwise, he will vote “against the proposal” (i.e., ). After executing this protocol, a designated edge server (i.e., ES) outputs 0 if there is at least one vote of “against the proposal”, and 1 otherwise. In addition, it should satisfy the following requirements:
Correctness
If all parties honestly execute this protocol, then the final output is equal to , i.e., if any (against the proposal), then (failure).
Privacy
Anyone else but the voter cannot get any private information about except the final output . Here, perfect privacy implies anonymity, i.e., no one can know who votes the vote .
Fairness
Under no circumstances one participant should have an advantage over another or other parties to get the final output or more private information.
Furthermore, as a basic block, we utilize Edge-assisted Quantum Protocol for SMLA to build an efficient quantum AOV protocol, which can achieve the information-theoretical security.
Quantum Protocol for AOV
Step 1. According to his/her voting will, each voter () generates a private bit : If he/she want to vote “for the proposal”, then ; Otherwise, , i.e., he/she wants to vote “against the proposal”.
Step 2. The ES asks for all voters to compute by using Edge-assisted Quantum Protocol for SMLA, where is the private input of the voter for .
Step 3. The ES finally outputs . If , it means it is successful; Otherwise, it is unsuccessful (i.e., failure).
Correctness
Clearly, due to . If , then it shows that it finally vetos the proposal (i.e., unsuccessful) because at least one voter votes “against the proposal” (i.e., there is at least one which is equal to 0). So, our aforementioned proposed quantum protocol is correct.
Security
Similarly, Edge-assisted Quantum Protocol for SMLA ensures perfect privacy of each voter. Of course, we cannot know who votes the veto or the approval, i.e., it is anonymous. In addition, all voters are equivalent entities, and they can get the final output with equal opportunities. So, it is also fair.
Performance evaluation
Performance analysis
In previous sections, we first propose a quantum primitive protocol for computing XOR, i.e., ESMX Quantum Protocol, and based on the proposed quantum primitive protocol, we further present another quantum primitive protocol for computing AND, i.e., Edge-assisted Quantum Protocol for SMLA. As a basic block, these quantum primitive protocols can be utilized to compute bitwise logical operations (e.g., XOR, AND and OR) of multiple private bits, and further generated to privately compute any (Boolean) function of multiple private inputs.
Here, we first analyze necessary quantum resources, operators and measurements performed by the first quantum primitive protocol, i.e., ESMX Quantum Protocol. Theoretically, it evenly costs 4 single photons to compute 1-bit XOR (i.e., ), where 2 single photons are corresponding to two successful events and one of two successful events is the encoding event while the other is the checking event. Furthermore, each participant needs to perform 4 operators (e.g., ) on correspondingly transmitted photons and forward them. There are participants in total. So, the quantum communication complexity is qubits (i.e., it achieves the linear communication complexity). Finally, the ES performs 4 single-photon measurements in the basis of {|0⟩, |1⟩} or {|+⟩, |⎯⟩}. In addition, this primitive protocol can be easily generalized to compute multiple-bit XORs in parallel, i.e., it increases the value of the parameter , and remains multiple encoding events.
Second, we analyze necessary quantum resources, operators and measurements required by the second quantum primitive protocol, i.e., Edge-assisted Quantum Protocol for SMLA, which includes five steps: grouping, counting, amending, ordering, and computing. In the step of grouping, each participant prepares single photons and performs single-photon measurements, where . In the step of counting, it is a completely classical process due to Shamir Secret Sharing protocols, which needs to transmit classical messages. In the step of amending, due to good uniformness and randomness of quantum measurements, most of groups do not need to run the amending procedure, while very few groups do it. Furthermore, if the number of the participants in a certain group is less than 3, then it is a fully classical amending process (i.e., no quantum process); if it is greater than 3, then it only needs the participants in this group to regenerate several single photons and perform single-photon measurements. In the step of ordering, the main cost is to execute ESMX Quantum Protocol times, where . Please note that it needs to execute this primitive protocol 4.5 (i.e., ) times evenly to get a successfully computing order per group and there are groups in total. In the step of computing, the main cost is also to execute ESMX Quantum Protocol times.
In a word, there is no any quantum communication in the first three steps, while it exchanges quantum messages (i.e., qubits) only by using ESMX Quantum Protocol in the last two steps and further it needs to execute this primitive protocol times in each step, where . Therefore, the quantum communication complexity of this primitive protocol is qubits.
In addition, we can deduce that Quantum Protocol for MPSI and Quantum Protocol for AOV need to execute Edge-assisted Quantum Protocol for SMLA times and once, respectively. Accordingly, the quantum communication complexities of these two protocols are and qubits, respectively.
Furthermore, we give a comparison between our proposed quantum protocol for SMLA and previously proposed quantum protocol for SMLA in ref. 26 from quantum resources, quantum operators, quantum measurements, transmitted qubits, and so on, as listed in Table 1.
Table 1.
Comparisons between two quantum protocols for SMLA
| Protocols | Quantum resources | Quantum operators | Quantum measurements | Transmitted qubits | TP |
|---|---|---|---|---|---|
| Shi et al.26 | O(n)-qubit entangled states |
O(n) 3-qubit T- gates |
O(n) single-qubit measurements |
O(n) qubits | QC |
| Our proposed protocol | O(n)-qubit single photons |
O(n) 1-qubit P-gates and H-gates |
O(n) single-photon measurements |
O(n2) qubits | ES |
Note. P-gate, H-gate, and T-gate denote Pauli gate, Hadamard gate, and Toffoli gate, respectively. TP, QC, and ES represent Third Party, Quantum Cloud, and Edge Server, respectively.
Given from Table 1, we can see that the transmitted qubits of the proposed protocol are more than those of ref.,26 i.e., the communication cost of the proposed protocol is higher than that of ref.26 However, it is still difficult to implement the scheme of ref. 26 with the present technologies, due to its necessary quantum resources, quantum operators and quantum measurement. Accordingly, our new proposed quantum protocol for SMLA is more feasible than previously proposed protocol with the present quantum processing technology, since this new protocol only needs single photons and corresponding single-photon operators and measurements, instead of multiple-qubit entangled states and multiple-qubit quantum operators in high-dimensional Hilbert space. At present, it is still difficult to implement 3-qubit Toffoli gate,52 which is necessary quantum operators in ref.26 In addition, previously proposed quantum protocol for SMLA in ref. 26 still needs the help of quantum conference key agreement to generate a secure key among all participants in advance. In a word, our new proposed quantum protocol for SMLA achieves better feasibility by sacrificing easy quantum resources (i.e., single photons).
In addition, we give detailed comparisons of related quantum protocols on multi-party/two-party PSI (MPSI/PSI), which outputs the intersection of multiple/two private sets, or multi-party/two-party PSI Cardinality (MPSI-CA/PSI-CA), which outputs the cardinality of the intersection of multiple/two private sets, listed in Table 2. Similarly, the communication complexity of our proposed MPSI quantum protocol is not the best in Table 2, but our protocol has better feasibility than other related protocols, because our protocol only needs single photons as quantum resources, and performs single-photon operators and measurements in 2-dimension Hilbert space, instead of high-dimension Hilbert space.
Table 2.
Comparisons of related quantum protocols for PSI
| Protocols | Quantum resources | Quantum operators | Quantum measurements | Transmitted qubits | Output |
|---|---|---|---|---|---|
| Shi et al.24 | 2logN-qubit entangled states | 2-qubit CNOT gates |
Projective measurements in N-dimension Hilbert space | O(N) qubits | MPSI-CA |
| Shi et al.26 | n-qubit entangled states | 3-qubit Toffoli gates | Projective measurements in 2-dimension Hilbert space | O(nN) qubits | MPSI-CA |
| Shi et al.28 | logN-qubit superposition states | logN-qubit Oracle operators | Projective measurements in N-dimension Hilbert space | O(logN) qubits | PSI |
| Shi et al.29 | 2logN-qubit entangled states | logN-qubit Oracle operators | Projective measurements in N-dimension Hilbert space | O(logN) qubits | PSI-CA |
| Our quantum MPSI protocol | single-qubit photons | 1-qubit Pauli gates and Hadamard gates | Projective measurements in 2-dimension Hilbert space | O(nN) qubits | MPSI |
Simulated experiments
Here, we attempt to do simulated experiments about new proposed quantum primitive protocols in Qiskit of IBM (Qiskit-0.35.0; Python-3.8.13; OS-Linux) to verify the correctness and the feasibility of these protocols.
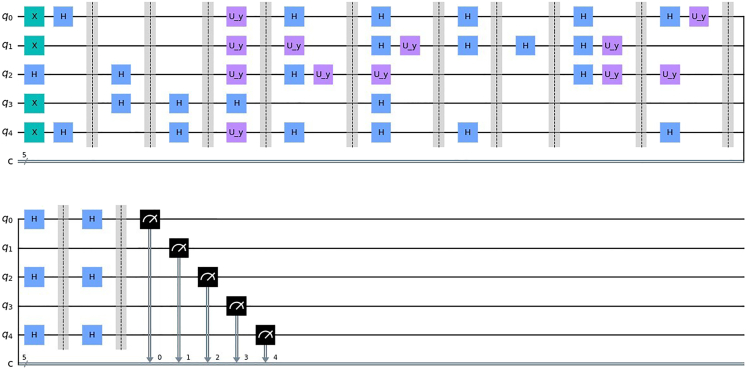
First, we simulate ESMX Quantum Protocol. Figure 3 gives an example to compute XOR of 11 private bits with five qubits, i.e., and , where the second qubit and the fourth qubit are corresponding to successful events and further one of two successful events is treated as the encoding event (e.g., ) while the other is taken as the checking event (e.g., ). Finally, all simulated results verify the correctness and feasibility of the first quantum primitive protocol, i.e., ESMX Quantum Protocol.
Figure 3.
Quantum circuits of computing XOR among 11 participants
Furthermore, we mainly simulate grouping in Edge-assisted Quantum Protocol for SMLA. In the grouping step, we first prepare lots of single-qubits in , then we directly measure them in the computational basis. The statistical results of 1000 experiments are listed in Table 3, where there are 12 participants in these experiments. From Table 2, we can see that the probabilities of the measured results of 00, 01, 10, and 11 are 0.256, 0.249, 0.246, and 0.249, respectively. Accordingly, there are 3.072, 2.988, 2.952, and 2.988 participants on average in the first, second, third, and fourth group, respectively. That is, there are about 3 participants per group due to good advantages of quantum measurements, e.g., uniform, independent, and random.
Table 3.
Grouping experiments
| Measured results | 00 (The 1st group) | 01 (The 2ND group) | 10 (The 3rd group) | 11 (The 4th group) |
|---|---|---|---|---|
| 0.256 | 0.249 | 0.246 | 0.249 | |
| 3.07 | 2.988 | 2.952 | 2.988 |
Note. and denote the probability of the measured result and the average number of the participants in the corresponding group.
Finally, based on the feasibility and the correctness of ESMX Quantum Protocol, we can easily see that Edge-assisted Quantum Protocol for SMLA is also feasible and correct.
In a word, all simulated experiments verify the correctness and the feasibility of our proposed quantum primitive protocols.
Conclusions
In summary, we first presented two quantum primitive protocols, including ESMX Quantum Protocol and Edge-assisted Quantum Protocol for SMLA, which could be adopted widely in privacy-preserving settings with multiple participants as basic blocks. In these quantum primitive protocols, we take single photons as quantum resources and perform single-photon operators and measurements. So, it is feasible and efficient to implement these quantum protocols with the present quantum technologies. Furthermore, based on these quantum primitive protocols, we designed two application protocols, i.e., Quantum Protocol for MPSI and Quantum Protocol for AOV. Compared with classical related protocols, our proposed quantum protocols obtain higher security (i.e., information-theoretical security and long-term security), which can be guaranteed by the basic principles of quantum mechanics.
Our work further shows that quantum cryptography can not only ensure data security (e.g., QKD) but also protect user privacy (e.g., PSI). Especially, like mathematical cryptography, we can construct various kinds of quantum protocols based on quantum mechanics to meet different applications in novel cloud/edge environments.
Limitations of the study
As discussed previously, we only conducted simulated experiments. This work was limited by a real experimental environment. Further, proposed quantum protocols should be performed in real quantum devices to verify their feasibilities.
STAR★Methods
Key resources table
Resource availability
Lead contact
Futher information and requests for resouces should be directed to the lead contact Run-hua Shi (rhshi@ncepu.edu.cn).
Materials availability
This study did not generate new unique reagents.
Experimental model and subject details
We simulated the key process of proposed quantum protococols in Qiskit of IBM (Qiskit-0.35.0; Python-3.8.13; OS-Linux), which is available at: https://qiskit.org/documentation/getting_started.html.
Acknowledgments
This work was supported by National Natural Science Foundation of China (No.61772001).
Author contributions
Study conception, design, and writing of the manuscript: R-H.S. Analysis and discussion: R-H.S. and X-Q.F. Experiments: X-Q.F. All authors reviewed the manuscript.
Declaration of interests
All authors declare no competing interests.
Inclusion and diversity
We support inclusive, diverse, and equitable conduct of research.
Published: May 29, 2023
Contributor Information
Run-hua Shi, Email: rhshi@ncepu.edu.cn.
Xia-qin Fang, Email: xiaqin.fang@ncepu.edu.cn.
Data and code availability
This study has no data and code available.
References
- 1.Xue J., Xu C., Zhao J., et al. Identity-based public auditing for cloud storage systems against malicious auditors via blockchain. Sci. China Inf. Sci. 2019;62:32104. [Google Scholar]
- 2.Huang Y., Xu H., Gao H., et al. SSUR: an approach to optimizing virtual machine allocation strategy based on user requirements for cloud data center. IEEE Trans. Green Commun. Netw. 2021;5:670–681. [Google Scholar]
- 3.Li Z., Sharma V., Ma C., Ge C., Susilo W. Ciphertext-policy attribute-based proxy re-encryption via constrained PRFs. Sci. China Inf. Sci. 2021;64:169301. [Google Scholar]
- 4.Sun J., Xiong H., Nie X., Zhang Y., Wu P. On the security of privacy-preserving attribute-based keyword search in shared multi-owner setting. IEEE Trans. Dependable Secure Comput. 2021;18:1–2519. [Google Scholar]
- 5.Ge C., Liu Z., Xia J., Fang L. Revocable identity-based broadcast proxy Re-encryption for data sharing in clouds. IEEE Trans. Dependable Secure Comput. 2021;18:1214–1226. [Google Scholar]
- 6.Wang K., Yu J., Liu X., Guo S. A pre-authentication approach to proxy Re-encryption in big data context. IEEE Trans. Big Data. 2021;7:657–667. [Google Scholar]
- 7.Grover L.K. A fast quantum mechanical algorithm for database search. Proc. ACM Symposium on Theory of Computing (STOC 1996) 1996:212–219. [Google Scholar]
- 8.Shor P.W. Algorithms for quantum computation – discrete logarithms and factoring. Proc. 35th Annual Symposium on Foundations of Computer Science. 1994:124–134. [Google Scholar]
- 9.Jaiswal A., Kumar S., Kaiwartya O., Kashyap P.K., Kanjo E., Kumar N., Song H. Quantum learning-enabled green communication for next-generation wireless systems. IEEE Trans. Green Commun. Netw. 2021;5:1015–1028. [Google Scholar]
- 10.Arute F., Arya K., Babbush R., Bacon D., Bardin J.C., Barends R., Biswas R., Boixo S., Brandao F., Buell D.A., et al. Quantum supremacy using a programmable superconducting processor. Nature. 2019;574:505–510. doi: 10.1038/s41586-019-1666-5. [DOI] [PubMed] [Google Scholar]
- 11.Zhong H.S., Wang H., Deng Y.H., Chen M.C., Peng L.C., Luo Y.H., Qin J., Wu D., Ding X., Hu Y., et al. Quantum computational advantage using photons. Science. 2020;370:1460–1463. doi: 10.1126/science.abe8770. [DOI] [PubMed] [Google Scholar]
- 12.Nielsen M.A., Chuang I.L. Cambridge University Press; 2000. Quantum Computation and Quantum Information. [Google Scholar]
- 13.Bennett C.H., Brassard G. IEEE; 1984. Quantum cryptography: public key distribution and coin tossing; pp. 175–179. (Proc. IEEE International Conference on Computers, Systems, and Signal Processing). [Google Scholar]
- 14.Shi R., Huang L., Yang W., Zhong H. Quantum secret sharing between multiparty and multiparty with Bell states and Bell measurements. Sci. China Phys. Mech. 2010;53:2238–2244. [Google Scholar]
- 15.Boykin P.O., Roychowdhury V. Optimal encryption of quantum bits. Phys. Rev. 2003;67:042317. [Google Scholar]
- 16.Lou X., Wang Y., Long H., Yang Y., Li J. Sequential quantum multiparty signature based on quantum fourier transform and chaotic system. IEEE Access. 2020;8:13218–13227. [Google Scholar]
- 17.Sun Z., Song L., Huang Q., Yin L., Long G., Lu J., Hanzo L. Toward practical quantum secure direct communication: a quantum-memory-freee protocol and code design. IEEE Trans. Commun. 2020;68:5778–5792. [Google Scholar]
- 18.Shi R.H., Zhong H. Multi-party quantum key agreement with Bell states and Bell measurements. Quant. Inf. Process. 2013;12:921–932. [Google Scholar]
- 19.Chaum D.L. Untraceable electronic mail, return addresses and digital pseudonyms. Commun. ACM. 1981;24:84–90. [Google Scholar]
- 20.Alvarez R., Nojoumian M. Comprehensive survey on privacy-preserving protocols for sealed-bid auctions. Comput. Secur. 2020;88:101502. [Google Scholar]
- 21.Guo X. IEEE 5th International Conference on Information Systems and Computer Aided Education (ICISCAE) IEEE; 2022. Implementation of a blockchain-enabled federated learning model that supports security and privacy comparisons. [Google Scholar]
- 22.Wang Q., Yu C., Gao F., Qi H., Wen Q. Self-tallying quantum anonymous voting. Phys. Rev. 2016;94:022333. [Google Scholar]
- 23.Shi R.H. Quantum sealed-bid auction without a trusted third party. IEEE Trans. Circ. Syst. I. 2021;68:4221–4231. [Google Scholar]
- 24.Shi R.H., Li Y.F. Quantum private set intersection cardinality protocol with application to privacy-preservin condition query. IEEE Trans. Circ. Syst. I. 2022;69:2399–2411. [Google Scholar]
- 25.Shi R.H., Li Y.F. Quantum secret permutating protocol. IEEE Trans. Comput. 2023;72:1223–1235. [Google Scholar]
- 26.Shi R.H., Li Y.F. Quantum protocol for secure multiparty logical and with application to multiparty private set intersection cardinality. IEEE Trans. Circ. Syst. I. 2022;69:5206–5218. [Google Scholar]
- 27.Freedman M.J., Nissim K., Pinkas B. Proc. Advances in Cryptology – Eurocrypt 2004, LNCS, 3027. 2004. Efficient private matching and set intersection; pp. 1–19. [Google Scholar]
- 28.Shi R.H., Mu Y., Zhong H., Cui J., Zhang S. An efficient quantum scheme for Private Set Intersection. Quant. Inf. Process. 2016;15:363–371. [Google Scholar]
- 29.Shi R.H., Mu Y., Zhong H., Zhang S., Cui J. Quantum private set intersection cardinality and its application to anonymous authentication. Inf. Sci. 2016;370–371:147–158. [Google Scholar]
- 30.Shi R.H. Efficient quantum protocol for private set intersection cardinality. IEEE Access. 2018;6:73102–73109. [Google Scholar]
- 31.Shi R.H. Quantum Private computation of cardinality of set intersection and union. Eur. Phys. J. D. 2018;72:221. [Google Scholar]
- 32.Shi R.H., Zhang M. A feasible quantum protocol for private set intersection cardinality. IEEE Access. 2019;7:72105–72112. [Google Scholar]
- 33.Liu B., Ruan O., Shi R., Zhang M. Quantum private set intersection cardinality based on Bloom filter. Sci. Rep. 2021;11:17332. doi: 10.1038/s41598-021-96770-1. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 34.Li H.S., Fan P., Xia H.Y., Peng H., Song S. Quantum implementation circuits of quantum signal representation and type conversion. IEEE Trans. Circ. Syst. I. 2019;66:341–354. [Google Scholar]
- 35.Zhang C., Long Y., Sun Z., Li Q., Huang Q. Three-party quantum private computation of cardinalities of set intersection and union based on GHZ states. Sci. Rep. 2020;10:22246. doi: 10.1038/s41598-020-77579-w. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 36.Wang S., Feng C., Yin S., Feng Z., Tang J., Liu N., Yang F., Yang X., Wang Y. Quantum protocols for private set intersection cardinality and union cardinality based on entanglement swapping. Nat. Prod. Res. 2021;35:3514–3518. doi: 10.1080/14786419.2019.1710702. [DOI] [PubMed] [Google Scholar]
- 37.Mu Y., Varadharajan V. Proceedings of the 14th Annual Computer Security Applications Conference. 1998. Anonymous secure E-voting over a network; p. 293. [DOI] [Google Scholar]
- 38.Chan R.Y., Wong J.C., Chan A.C. In: Qing S., Eloff J.H.P., editors. Vol. 47. Springer; 2000. Anonymous Electronic Voting System with Non-Transferable Voting Passes. (Information Security for Global Information Infrastructures. SEC 2000. IFIP - The International Federation for Information Processing). [DOI] [Google Scholar]
- 39.Chafe S.S., Bangad D.A., Sonune H. In: ICT Systems and Sustainability. Tuba M., Akashe S., Joshi A., editors. Vol. 1270. Springer; 2020. Blockchain-Based E-V. Protocol. (Advances in Intelligent Systems and Computing). [DOI] [Google Scholar]
- 40.Sliusar V., Fyodorov A., Volkov A., et al. Proceedings of 2021 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering. IEEE; 2021. Blockchain technology application for electronic voting systems; pp. 26–29. [DOI] [Google Scholar]
- 41.Hillery M. Quantum voting and privacy protection: first steps. SPIENewsroom. 2006 doi: 10.1117/2.1200610.0419. [DOI] [Google Scholar]
- 42.Vaccaro J.A., Spring J., Chefles A. Quantum protocols for anonymous voting and surveying. Phys. Rev. 2007;75:012333. [Google Scholar]
- 43.Zhang S., Wang S.l., Wang Q., Shi R.h. Quantum anonymous voting protocol with the privacy protection of the candidate. Int. J. Theor. Phys. 2019;58:3323–3332. [Google Scholar]
- 44.Liu B.X., Jiang D.H., Liang X.Q., Zhang Y.H. A novel quantum voting scheme based on BB84-state. Int. J. Theor. Phys. 2021;60:1339–1349. [Google Scholar]
- 45.Li Y.R., Jiang D.H., Zhang Y.H., Liang X.Q. A quantum voting protocol using single-particle states. Quant. Inf. Process. 2021;20:110. [Google Scholar]
- 46.Wang Q., Liu J., Li Y., Yu C., Pan S. Quantum Bell states-based anonymous voting with anonymity trace. Quant. Inf. Process. 2021;20:142. [Google Scholar]
- 47.Rahaman R., Kar G. GHZ correlation provides secure Anonymous Veto Protocol. arXiv. 2015 doi: 10.48550/arXiv.1507.00592. Preprint at. [DOI] [Google Scholar]
- 48.Wu S., Sun W., Wang Q., Che R., Hu M., Ding Z., Xue X. A secure quantum protocol for anonymous one-vote veto voting. IEEE Access. 2021;9:146841–146849. [Google Scholar]
- 49.Lo H.K. Insecurity of quantum secure computations. Phys. Rev. 1997;56:1154–1162. [Google Scholar]
- 50.Mayers D. Unconditionally secure quantum bit commitment is impossible. Phys. Rev. Lett. 1997;78:3414–3417. [Google Scholar]
- 51.Buhrman H., Christandl M., Schaffner C. Complete insecurity of quantum protocols for classical two-party computation. Phys. Rev. Lett. 2012;109:160501. doi: 10.1103/PhysRevLett.109.160501. [DOI] [PubMed] [Google Scholar]
- 52.Kim Y., Morvan A., Nguyen L.B., Naik R.K., Jünger C., Chen L., Kreikebaum J.M., Santiago D.I., Siddiqi I. High-fidelity three-qubit Toffoli gate for fixed-frequency superconducting qubits. Nat. Phys. 2022;18:783–788. [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
This study has no data and code available.