Abstract
This paper investigates the security–reliability of simultaneous wireless information and power transfer (SWIPT)-assisted amplify-and-forward (AF) full-duplex (FD) relay networks. In practice, an AF-FD relay harvests energy from the source (S) using the power-splitting (PS) protocol. We propose an analysis of the related reliability and security by deriving closed-form formulas for outage probability (OP) and intercept probability (IP). The next contribution of this research is an asymptotic analysis of OP and IP, which was generated to obtain more insight into important system parameters. We validate the analytical formulas and analyze the impact on the key system parameters using Monte Carlo simulations. Finally, we propose a deep learning network (DNN) with minimal computation complexity and great accuracy for OP and IP predictions. The effects of the system’s primary parameters on OP and IP are examined and described, along with the numerical data.
Keywords: physical layer security (PLS), self-energy recycling, full duplex (FD), outage probability (OP), intercept probability (IP), deep learning network (DNN)
1. Introduction
The Internet of Things (IoT) is the term employed to describe the interconnection of all physical items with the Internet through information sensing devices for the purpose of information exchange, i.e., the way in which physical objects communicate with one another to accomplish intelligent identification and administration. The future beyond 5G (B5G) IoT and massive machine-type communication (mMTC) will face difficult issues due to massively networked smart gadgets [1]. This is mostly due to the varied quality of service (QoS) provided by the enormous number of such devices for 5G-enabled big IoT networks. As a result of the huge IoT, wireless communication networks will face a variety of issues, including fundamental energy consumption, the use of high-frequency resources, and more [2].
Many approaches have been suggested to boost spectral efficiency (SE) performance. Full-duplex (FD) relaying techniques can, among others, roughly quadruple the SE compared to half-duplex (HD) relaying [3,4,5,6,7]. Additionally, the authors in [8] used orthogonal frequency division multiple access (OFDMA) technology to expand FD relaying into a multi-user scenario. Recent developments in antenna and transceiver design in FD have demonstrated a high potential for eliminating the self-interference (SI) channel up to the receiver noise floor [9]. By utilizing the physical isolation and separation of the transmitter and receiver, the SI channel can lessen passive cancelation. The SI signal in the received transmission is actively suppressed [10]. The FD relay broadcasts information, and the broadcast characteristics of the wireless medium offer a tremendous problem in guaranteeing secure and reliable communications in the face of adversaries [11,12]. As a result, secure transmission becomes a critical problem that cannot be overlooked. Several transmission techniques for enhancing the secrecy rate were presented [13,14,15,16] to prevent secret communications from being eavesdropped in FD relay networks. In [17], the authors investigated a communication network in which a source seeks to interact with an FD destination while being overheard by an eavesdropper. The author in [18] studied the secrecy outage probability (SOP) of the multiple FD decode and forward (DF) relay networks under imperfect channel state information (CSI). In this case, relay selection was applied, which proved to be better than the HD-based strategy. An overview of physical layer security (PLS) schemes for FD co-operative systems was presented in [19]. Furthermore, in a situation with untrusted relays, a source-based jamming strategy was presented, in which the source sends a composite signal comprising the secret and jamming signals to increase secrecy. The authors in [20] examined the scenarios involving different relays and the effects of antenna designs and jamming signals on security. In [21], the authors presented the SOP of an FD jamming relay method, where the source sends data to the relay while sending the jamming signals to the eavesdroppers. Furthermore, the authors in [22] studied a two-hop FD-DF relaying scheme with secrecy rates and optimal power allocation. Finally, Moya. et al. proposed a co-operative network where the FD destination transmits the jamming signal to several amplify-and-forward (AF) untrusted relays in [23].
Energy harvesting (EH) is a workable solution to the problem of limited operation time [24,25,26,27,28,29]. EH can extend the life of the IoT network or even make it self-sufficient by harvesting energy from the environment, such as vibration, solar, and wind [30]. Since it can harvest energy from radio frequency (RF) signals, providing a more reliable energy supply, wireless power transfer (WPT) offers a more realistic solution to the limited period of operation problem [31,32,33]. Researchers have further incorporated the WPT properties into wireless communication systems, known as simultaneous wireless information and power transfer (SWIPT), by taking into account the fact that RF signals may transport both information and energy [34,35,36]. For instance, Chen et al., in [37], investigated limited feedback multi-antenna systems, wherein the trade-off between wireless energy and information transfer was considered. In addition, the authors maximized energy harvesting by using adaptive energy beamforming according to instantaneous CSI. The two protocols for EH, which are time switching (TS) and power splitting (PS), were explored in [38,39], respectively. A part of the time or power of the received signal is utilized for energy harvesting in TS or PS protocols, whereas the remainder is used for information processing. The PLS in the SWIPT network has attracted a lot of researchers, as in [40,41,42]. The secrecy performance of a single-input multiple-output (SIMO) SWIPT system was explored in [40], in which the base station broadcasts information to the receiver while simultaneously transferring energy to numerous energy-harvesting receivers. The authors in [41] presented a strong, secure transmission system for multiple-input single-output (MISO) SWIPT networks. In [42], the authors offered an effective transmission solution for multiple-input multiple-output (MIMO) wiretap channels, in which the non-concave issue was first turned into a convex optimization and then solved by dealing with its dual problem.
Deep learning has recently evolved as a strong data-driven strategy to solve a variety of complex issues, such as image processing, pattern recognition, and wireless communication applications [43]. The authors in [44] designed a deep neural network (DNN) model to forecast coverage probability in random wireless networks. It should be highlighted that the DNN model outperforms the mathematical method, which is only appropriate for oversimplified network settings. Moreover, in [45], the authors employed a DNN model to predict the SOP and demonstrate the shortest running time for SOP prediction across simulation and analytical findings in unmanned aerial vehicle networks. Zheng et al., in [46], studied the combination of adjusted, deep deterministic policy gradient (A-DDPG) and convex optimization to optimize the long-term secondary throughput in RF-powered ambient backscatter-assisted hybrid underlay cognitive radio networks.
1.1. Related Work and Motivation
A lot of the current literature has studied the PLS in co-operative relaying networks. In [47], the authors studied the problem of security in untrusted FD relaying using the AF protocol system by applying a source-jamming scheme. However, the author did not consider EH to help improve the lifetime of the device. The authors in [48] investigated security performance in an AF relaying FD system in the presence of a passive eavesdropper. In [49], the authors investigated reliability and security in an AF relaying system in the presence of an eavesdropper. Furthermore, the authors considered friendly jammers to improve the security of the system. However, the authors in [48,49] did not consider FD in co-operative relaying to improve the SE of the system. In addition, the authors of [47,48,49] did not apply a DNN in order to reduce the overall energy consumption through an offline training process. In addition, Table 1 shows a comparison of our work with related works.
Table 1.
Comparison of our work with the related work.
Motivated by the challenges described above, we consider the security–reliability of a SWIPT-assisted FD relay in IoT networks. The FD relay harvests energy based on the PS protocol. In particular, the FD relay is also assumed to have the ability for self-energy recycling to increase the average transmittance power. In addition to harvesting the energy from the source’s broadcast signal, the self-interference energy can be recovered and reused [50]. In addition, we apply the DNN method to predict the security–reliability of the proposed system.
1.2. Contributions
The main contributions of this paper are listed as follows:
We propose a novel SWIPT-assisted AF-FD relay network to evaluate security and reliability trade-offs. In particular, in order to increase EH, the relay can harvest energy from the source and reuse the self-interference channel based on the PS protocol to attain battery-free operation;
We derive the approximate OP for legitimate communications and the approximate IP for the eavesdropper’s channel. The asymptotic expressions for the OP and IP are also examined to give some insight into the system configuration under consideration. In order to verify the derived expressions, Monte-Carlo simulation is adopted;
The suggested DNN performs almost as well as the simulation while drastically lowering the computing complexity. In comparison to existing machine learning-based regression models for OP/IP prediction, our suggested DNN technique has the lowest root mean square error (RMSE) and takes the shortest time to execute. When system attributes and channel circumstances vary, the data rate of the considered system can be customized based on the estimated OP/IP.
1.3. Organization
Section 2 describes the system model. Section 3 expresses the performance analysis. Section 4 shows the asymptotic analysis. Section 5 proposes the DNN network. Section 6 presents numerical results. Finally, a conclusion for the obtained results is presented in Section 7.
2. System Model
The proposed system model for wireless communication, in which one source node, S, communicates with one destination node, D, via the help of one FD relay node, R, in the presence of an eavesdropper node, E, that wants to take the information from both R and S is shown in Figure 1. In order to enhance the performance at D, we assumed that S could transmit its signal directly to D and via the relay R. Because of the limited energy, R will need to harvest wireless energy from S and employ the self-energy recycling technique, as seen in [50], and then adopt the total harvested energy to transmit the source data to D using the AF mode. In the AF mode, R amplifies and then forwards the received signal from S to D. Moreover, Table 2 shows the main parameters of our paper.
Figure 1.
System model.
Table 2.
Main Parameters.
| Notation | Definition |
|---|---|
| The transmit power at S | |
| The transmit power at R | |
| The transmit signal at S with | |
| The transmit signal at R with | |
| The conversion efficiency with | |
| The PS ratio with | |
| The target rate | |
| , , , | The AWGN with variance |
| The path loss exponent | |
| The distance from S to D | |
| The distance from S to R | |
| The distance from S to E | |
| The distance from R to D | |
| The distance from R to E | |
| The expectation operator | |
| The modified Bessel function of the second kind with -th order: |
2.1. Energy Harvesting Model
In the energy harvesting phase, in order to implement self-energy recycling (S-ER), the total harvested energy at R can be expressed as [50]
| (1) |
Then, the transmit power of R can be formulated as
| (2) |
It is worth noting from (2) that when . In practice, is much less than 1 due to passive interference cancellation (IC), such as from antenna isolation, so the denominator in (2) is positive [52].
2.2. Fading Channel Model
Let us denote , , , , and as the channel coefficients of the direct link from source node S to destination node D, and links, respectively. We also denote as the self-interference coefficient between the transmit and receive antennas of relay node R. Assume that are Rayleigh fading channels; channel gains are exponential random variables (RVs) for which the cumulative distribution function (CDF) is given as
| (3) |
To take into account the simple path loss model, the parameters can be formulated as follows:
| (4) |
The RV is also modeled as complex Gaussian RV, and hence is also an exponential RV. Then, its CDF is given by
| (5) |
Then, the probability density function (PDF) of is given by
| (6) |
where
2.3. Transmission Model
In the information transmission phase, the received signal at R is given as follows:
| (7) |
Moreover, in this phase, the received signal at D and E are respectively given by:
| (8) |
| (9) |
In our proposed system, the AF protocol is applied. Hence, after receiving the information from S, R will amplify this information to D and E by the given amplification factor , as follows:
| (10) |
By combining (7), (8), (9), and (10), we obtain the received signal at D and E as follows:
| (11) |
and
| (12) |
The received signal-to-interference plus noise ratio (SINR) at D and E in this phase can be, thus, calculated using the following expressions:
| (13) |
and
| (14) |
By substituting (2) into (13) and (14) and then carrying out some algebra, the SINR at D and E can be rewritten as
| (15) |
| (16) |
where denotes the average transmited signal-to-noise ratio (SNR).
In our proposed model, the direct link is considered. Hence, in the broadcast phase, D can be received, and the direct signal from S and E can overhear this signal when S broadcasts to R and D. As a result, the received signal at D and E can be thus expressed by
| (17) |
| (18) |
The SNR at D and E in this phase can be computed respectively by
| (19) |
| (20) |
Finally, by adopting the selection-combining (SC) technique at the receiver, the end-to-end SNR at D and E can be respectively claimed as
| (21) |
| (22) |
3. Performance Analysis
In this section, the performance of the proposed system is studied. In particular, the closed-form outage probability (OP) and intercept probability (IP) are derived.
3.1. Outage Probability Analysis
The OP of the system can be expressed by
| (23) |
where is the threshold, and is the target rate. From (21) and (23), the OP can be rewritten as
| (24) |
Based on (24), can be figured out as
| (25) |
Next, can be, thus, computed by
| (26) |
where . From (26), there are two cases to calculate . In the first case, when , we obtain . In the second case, when , we obtain . Then, in case , can be calculated as
| (27) |
In order to find , first, we have to derive the CDF of . As a result, we claim
| (28) |
By applying [53] (Eq. 3.324.1), we obtain
| (29) |
where is the modified Bessel function of the second kind with -th order. From (26) and (29), can be found as
| (30) |
where . Unfortunately, the integral in presents a tough task in terms of finding a closed-form expression. Therefore, we apply the Gaussian-Chebyshev quadrature in [54] to approximate this. As a result, can be obtained by
| (31) |
where . Finally, by substituting (25) and (31) into (23), the OP can be, thus, obtained as
| (32) |
3.2. Intercept Probability Analysis
The considered system will be wiretapped if E can successfully decode the received signals from the source and relay [55,56]. Therefore, the IP is given by
| (33) |
As a similar proof for OP, the IP can be achieved by
| (34) |
where .
4. Asymptotic Analysis
In this section, we develop the asymptotic equations for OP as the transmitted SNR approaches infinity, i.e., , to give us more insights into the performance analysis of the network under consideration.
4.1. Op Analysis
When , can be rewritten as
| (35) |
Then, the OP can be obtained by
| (36) |
4.2. Ip Asymptotic Analysis
As a result, in this case, the IP also can be obtained by
| (37) |
5. Dnn Network
In this section, we propose a DNN to predict the OP and IP without relying on the statistical model, whereas the traditional analysis and Monte Carlo simulations need an accurate statistical model. In addition, when the system model is complicated, and it is difficult to use the mathematical derivation technique, the DNN model, which is a data-driven approach, becomes an alternate answer. Therefore, the DNN will help the proposed system to achieve a short run time.
5.1. The DNN Design Description
First, we create a DNN model as a regression issue. As illustrated in Figure 2, the DNN model consists of an input layer, numerous hidden layers, and an output layer. The following is a summary of how each layer contributes to training the DNN model:
Data is sent to the input layer so that the DNN model may determine how the system parameters relate to the relevant OP/IP. The number of neurons in the input layer is, therefore, equal to the number of parameters and does not serve as an activation function;
The number of hidden layers primarily determines the relationship between the input and output data. In order to accurately calculate the relationship, each connection in each hidden neuron has a separate weight and bias. In order to enhance computational effectiveness, each hidden neuron also has a nonlinear activation function;
The output layer combines the findings of various hidden layers to predict OP/IP. As a result, there is just one neuron in the output layer. The neuron in the output layer lacks an activation function, much like the input layer.
Figure 2.
A diagram of the DNN architecture.
Furthermore, we have 10 neurons corresponding to 10 parameters, as shown in Table 3 for the input layer. In the hidden layers, each layer k with has neurons, and it employs the exponential linear unit (ELU) activation function, which can be given as [57,58]
| (38) |
where denotes the constant value initialized to 1. Since the regression problem tries to estimate an output value without additional conversion, the output layer comprises one neuron that uses the linear activation function to produce the predicted OP/IP value, .
Table 3.
Theparameters for DNN training and testing.
| Input | Value | Input | Value |
|---|---|---|---|
| 2 | [2,4] | ||
| 1.5 | 0.8 | ||
| 1 | 0.25 | ||
| 0.5 | [0.5,1] | ||
| 1 | [−5,25] |
5.2. Dataset Setup
In this subsection, we generate dataset as a row vector for each sample i, i.e., Data , where is the feature vector containing all the inputs from the parameters listed in Table 3. Each feature is utilized to produce real-value OP/IP sets from (23) and (33); this is input into the simulation, and a unique matching is returned. In conclusion, we built the dataset by generating samples, concatenating them, and then dividing this into a new dataset with 80% for training , 10% for validation , and 10% for testing . Moreover, we set the DNN model to have four hidden layers and 128 hidden neurons, which is implemented in Python 3.11.4 using Keras 2.8.0 and TensorFlow 2.8.0. Furthermore, the DNN model is trained in 100 epochs. The deep model is specifically constructed using hardware with an AMDRyzen Threadripper 3970X 32-core CPU and an Nvidia GeForce RTX-2070 super GPU for rapid training and experiment simulations.
The estimation accuracy of the DNN model is calculated using the mean-square error (MSE), which is formally stated as . Furthermore, the appropriate weights and biases for each connection are determined by applying the Adam optimizer [59]. The difference between the natural and predicted OP/IP values throughout the full test set, which is specified as , is measured by using the RMSE in the OP/IP prediction.
6. Numerical Results
In this section, we provide the analysis findings to evaluate the proposed system in terms of OP and IP, as well as the simulation results, by using the Monte Carlo approach, as per [60,61], to validate our analytical derivations. The main parameter can be shown in Table 3, except for some specific cases.
In Figure 3, we utilize the validation set to evaluate the accuracy of the training. As can be observed, when increasing the epoch and number of hidden layers, the MSE decreased. Moreover, the MSE in the four hidden layers is the best case. Although the DNN model contains four hidden layers that may generalize the dataset and improve network capacity, the second and third hidden layers are unable to learn the intricate patterns in a high-dimensional dataset, resulting in a large MSE.
Figure 3.
MSE convergence in training and evaluating the DNN with varying the hidden layers.
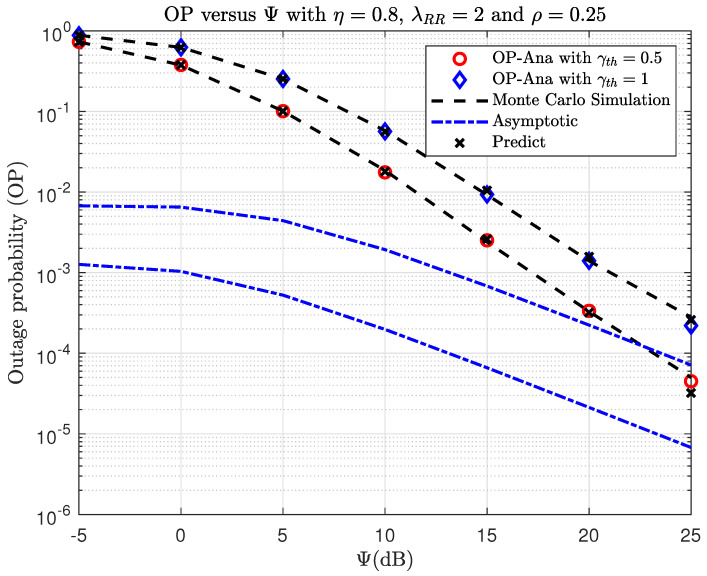
Figure 4 and Figure 5 show the OP and IP versus (dB) with different . As observed, the OP and IP curves correspond exactly to the Monte Carlo simulation results. By looking at Figure 4, the OP performance decreases if the increases. When is large, the SINR will significantly improve, and this will make the OP performance better. In Figure 5, it can be observed that as increases, the IP performance also increases. This is expected because an eavesdropper is more likely to overhear the message when the transmission power at S is higher. At a high SNR, i.e., , it can be seen that the asymptotic OP and IP curves closely match the actual findings. Specifically, the IP converges to the asymptotic value when (dB), whereas the OP converges to the asymptotic value at a higher ((dB), which cannot be seen in Figure 4). In addition, it can be shown that the DNN-based prediction results are very similar to the simulation and analysis results for OP and IP, demonstrating the superior prediction capabilities of the DNN.
Figure 4.
TheOP versus (dB) when varying with , , and .
Figure 5.
TheIP versus (dB) when varying with , , and .
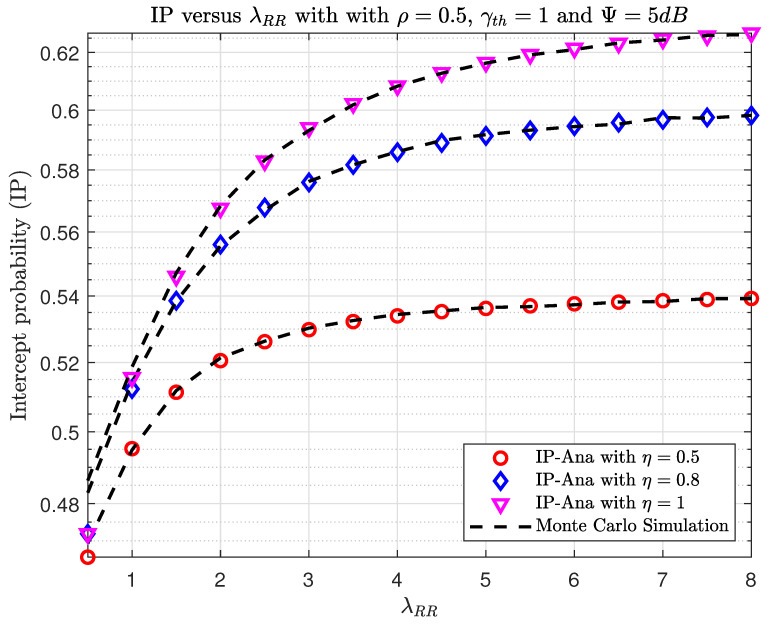
In Figure 6 and Figure 7, we plot the OP and IP versus with different . In Figure 6, increasing the between the transmitting and receiving antennas at the relay decreases the OP. It can be explained by the fact that increasing will make the in (15) larger; hence, the OP will be better. Moreover, when increasing energy efficiency , the average transmit power at R will be higher, and this will then lead to an improvement in OP. Furthermore, when increasing and , the SINR at E becomes larger. Thus, the possibility of E eavesdropping on information from S and R is also very high. So, the problem is that we have to trade-off between security and reliability in terms of OP and IP. This means that if the system wants to operate well, we must accept high eavesdropping information and vice versa.
Figure 6.
The OP versus when varying with , , and (dB).
Figure 7.
The IP versus when varying with , , and (dB).
In Figure 8 and Figure 9, we plot the OP and IP versus (dB) with different PS factors, . First, The higher the value in Figure 8, the better the OP. This is explained by the fact that the higher the value, the more the transmitted power of source S is assigned. Second, it is easy to observe that the OP decreases when the PS factor increases. Third, it can be seen that for a small ((dB)), the use of a large PS factor is more beneficial. Reversely, at higher , the smaller is better. The reason is as follows. For the high-noise environment case, higher transmitted power at the relay is needed to guarantee successful communication. That means more energy needs to be harvested at the relay, so a larger is better. On the other hand, if is large, then the decoding of the message at the relay is more important. That means we should select the smaller . As can be observed in Figure 9, the intercept performance improves when increases. This is expected because the eavesdropper has a better chance of overhearing the communication with a greater source transmit power, S. When is large enough, the IP can converge to one. The eavesdropper’s IP increases as the PS factor increases, which is due to the high transmitted power of relay R.
Figure 8.
TheOP versus (dB) when varying with , , and .
Figure 9.
TheIP versus (dB) when varying with , , and .
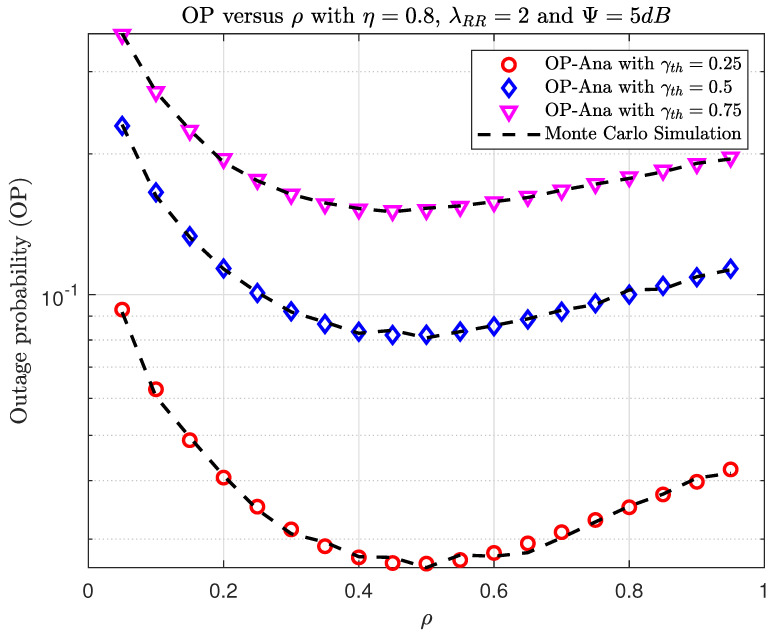
Figure 10 and Figure 11 show the OP and IP versus with different , respectively. The value is significant since it determines not only the quantity of gathered energy at the relay but also the data transfer. First, we can observe in Figure 10 that increasing the target data required leads to an increase in OP. Second, when , the system achieves the best OP performance. In addition, when increases the interception, performance increases, and when increasing , this will decrease the interception performance, similar to Figure 5.
Figure 10.
TheOP versus when varying with , , and (dB).
Figure 11.
The IP versus when varying with , , and (dB).
7. Conclusions
We investigated the security and reliability of SWIPT-assistance and self-energy recycling in an AF-FD relay network consisting of an EH relay and a destination in the presence of an eavesdropper. We also evaluated the performance of the security–reliability trade-offs in terms of the OP and IP. Furthermore, Monte Carlo simulation was utilized to verify and examine the influence of the system settings on network performance, as well as the accuracy of the analytical formulations. The OP/IP asymptotic analysis was also performed to offer some insight into the system characteristics. Deep learning was developed as a novel method for predicting the system’s OP and IP with minimal computing complexity and good accuracy, which has not been investigated previously. The numerical findings demonstrated that when utilizing DNN prediction, the OP and IP outcomes were almost identical to the Monte-Carlo simulation and analysis results. As a result, deploying a DNN as a black box might be viewed as a potentially promising and effective technique for evaluating system performances via a low-latency inference procedure that avoids the derivation of complicated closed-form expressions in actual network contexts.
Author Contributions
Q.-S.N. and B.M.L. conceived the study idea. A.-T.L. and T.N.N. derived the mathematical framework and proofread the manuscript. B.V.M. performed data curation and software. D.-H.T. and T.-L.L. investigated the system model. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Funding Statement
This work was supported by the Basic Science Research Program through the National Research Foundation of Korea (NRF), funded by the Korean government (MSIT) under Grant NRF-2023R1A2C1002656 and supported by the MSIT (Ministry of Science and ICT), Korea under Grant IITP-2023-RS-2022-00156345 (ICT Challenge and Advanced Network of HRD Program).
Footnotes
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
References
- 1.Jacob S., Menon V.G., Joseph S., Vinoj P., Jolfaei A., Lukose J., Raja G. A novel spectrum sharing scheme using dynamic long short-term memory with CP-OFDMA in 5G networks. IEEE Trans. Cogn. Commun. Netw. 2020;6:926–934. doi: 10.1109/TCCN.2020.2970697. [DOI] [Google Scholar]
- 2.Chinnadurai S., Yoon D. Energy efficient MIMO-NOMA HCN with IoT for wireless communication systems; Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC); Jeju, Republic of Korea. 17–19 October 2018; pp. 856–859. [Google Scholar]
- 3.Wei Z., Zhu X., Sun S., Huang Y., Dong L., Jiang Y. Full-duplex versus half-duplex amplify-and-forward relaying: Which is more energy efficient in 60-GHz dual-hop indoor wireless systems? IEEE J. Sel. Areas Commun. 2015;33:2936–2947. doi: 10.1109/JSAC.2015.2481211. [DOI] [Google Scholar]
- 4.Razlighi M.M., Zlatanov N. Buffer-aided relaying for the two-hop full-duplex relay channel with self-interference. IEEE Trans. Wirel. Commun. 2017;17:477–491. doi: 10.1109/TWC.2017.2767582. [DOI] [Google Scholar]
- 5.Nguyen B.C., Pham T.Q., Thang N.N., Hoang T.M., Tran P.T. Improving the performance of wireless half-duplex and full-duplex relaying networks with intelligent reflecting surface. J. Frankl. Inst. 2023;360:3095–3118. doi: 10.1016/j.jfranklin.2023.01.030. [DOI] [Google Scholar]
- 6.Nguyen T.T., Hoang V.T., Tran M.H., Le T.T.H., Tran X.N. Secrecy performance analysis of UAV-based full-duplex two-way relay NOMA system. Perform. Eval. 2023;161:102352. doi: 10.1016/j.peva.2023.102352. [DOI] [Google Scholar]
- 7.Nguyen T.L., Nguyen T.L., Nguyen V.V., Phu T.T. Outage Performance of Full-Duplex Unmanned Aerial Vehicle-aided co-operative Non-orthogonal Multiple Access. Adv. Electr. Electron. Eng. 2023;21:1–8. [Google Scholar]
- 8.Ng D.W.K., Lo E.S., Schober R. Dynamic resource allocation in MIMO-OFDMA systems with full-duplex and hybrid relaying. IEEE Trans. Commun. 2012;60:1291–1304. doi: 10.1109/TCOMM.2012.031712.110233. [DOI] [Google Scholar]
- 9.Mohammadi M., Shi X., Chalise B.K., Ding Z., Suraweera H.A., Zhong C., Thompson J.S. Full-Duplex Non-Orthogonal Multiple Access for Next Generation Wireless Systems. IEEE Commun. Mag. 2019;57:110–116. doi: 10.1109/MCOM.2019.1800578. [DOI] [Google Scholar]
- 10.Chen X., Liu G., Ma Z., Zhang X., Fan P., Chen S., Yu F.R. When Full Duplex Wireless Meets Non-Orthogonal Multiple Access: Opportunities and Challenges. IEEE Wirel. Commun. 2019;26:148–155. doi: 10.1109/MWC.2019.1800369. [DOI] [Google Scholar]
- 11.Dong L., Han Z., Petropulu A.P., Poor H.V. Improving Wireless Physical Layer Security via Cooperating Relays. IEEE Trans. Signal Process. 2010;58:1875–1888. doi: 10.1109/TSP.2009.2038412. [DOI] [Google Scholar]
- 12.Wang D., Bai B., Chen W., Han Z. Achieving High Energy Efficiency and Physical-Layer Security in AF Relaying. IEEE Trans. Wirel. Commun. 2016;15:740–752. doi: 10.1109/TWC.2015.2477510. [DOI] [Google Scholar]
- 13.Shim K., Do T.N., Nguyen T.V., da Costa D.B., An B. Enhancing PHY-Security of FD-Enabled NOMA Systems Using Jamming and User Selection: Performance Analysis and DNN Evaluation. IEEE Internet Things J. 2021;8:17476–17494. doi: 10.1109/JIOT.2021.3080425. [DOI] [Google Scholar]
- 14.Lim J.T., Kim T., Bang I. Impact of Outdated CSI on the Secure Communication in Untrusted In-Band Full-Duplex Relay Networks. IEEE Access. 2022;10:19825–19835. doi: 10.1109/ACCESS.2022.3151792. [DOI] [Google Scholar]
- 15.Hoang T.M., Dung L.T., Nguyen B.C., Tran X.N., Kim T. Secrecy Outage Performance of FD-NOMA Relay System With Multiple Non-Colluding Eavesdroppers. IEEE Trans. Veh. Technol. 2021;70:12985–12997. doi: 10.1109/TVT.2021.3123134. [DOI] [Google Scholar]
- 16.Li X., Jiang J., Wang H., Han C., Chen G., Du J., Hu C., Mumtaz S. Physical Layer Security for Wireless-Powered Ambient Backscatter Cooperative Communication Networks. IEEE Trans. Cogn. Commun. Netw. 2023;9:927–939. doi: 10.1109/TCCN.2023.3270425. [DOI] [Google Scholar]
- 17.Zheng G., Krikidis I., Li J., Petropulu A.P., Ottersten B. Improving Physical Layer Secrecy Using Full-Duplex Jamming Receivers. IEEE Trans. Signal Process. 2013;61:4962–4974. doi: 10.1109/TSP.2013.2269049. [DOI] [Google Scholar]
- 18.Ding Q., Liu M., Deng Y. Secrecy Outage Probability Analysis for Full-Duplex Relaying Networks Based on Relay Selection Schemes. IEEE Access. 2019;7:105987–105995. doi: 10.1109/ACCESS.2019.2932135. [DOI] [Google Scholar]
- 19.Nguyen B.V., Jung H., Kim K. Physical Layer Security Schemes for Full-Duplex Cooperative Systems: State of the Art and Beyond. IEEE Commun. Mag. 2018;56:131–137. doi: 10.1109/MCOM.2017.1700588. [DOI] [Google Scholar]
- 20.Lv L., Zhou F., Chen J., Al-Dhahir N. Secure Cooperative Communications With an Untrusted Relay: A NOMA-Inspired Jamming and Relaying Approach. IEEE Trans. Inf. Forensics Secur. 2019;14:3191–3205. doi: 10.1109/TIFS.2019.2912337. [DOI] [Google Scholar]
- 21.Chen G., Gong Y., Xiao P., Chambers J.A. Physical Layer Network Security in the Full-Duplex Relay System. IEEE Trans. Inf. Forensics Secur. 2015;10:574–583. doi: 10.1109/TIFS.2015.2390136. [DOI] [Google Scholar]
- 22.Elsaid L., Jiménez-Rodríguez L., Tran N.H., Shetty S., Sastry S. Secrecy Rates and Optimal Power Allocation for Full-Duplex Decode-and-Forward Relay Wire-Tap Channels. IEEE Access. 2017;5:10469–10477. doi: 10.1109/ACCESS.2017.2712766. [DOI] [Google Scholar]
- 23.Moya Osorio D.P., Benitez Olivo E.E., Alves H. Secrecy Performance for Multiple Untrusted Relay Networks Using Destination-Based Jamming with Direct Link; Proceedings of the 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC); Bologna, Italy. 9–12 September 2018; pp. 1–5. [Google Scholar]
- 24.Saeed N., Celik A., Al-Naffouri T.Y., Alouini M.S. Localization of energy harvesting empowered underwater optical wireless sensor networks. IEEE Trans. Wirel. Commun. 2019;18:2652–2663. doi: 10.1109/TWC.2019.2906309. [DOI] [Google Scholar]
- 25.Ha D.H., Nguyen T.N., Tran M.H.Q., Li X., Tran P.T., Voznak M. Security and Reliability Analysis of a Two-Way Half-Duplex Wireless Relaying Network Using Partial Relay Selection and Hybrid TPSR Energy Harvesting at Relay Nodes. IEEE Access. 2020;8:187165–187181. doi: 10.1109/ACCESS.2020.3030794. [DOI] [Google Scholar]
- 26.Tin P.T., Dinh B.H., Nguyen T.N., Ha D.H., Trang T.T. Power Beacon-Assisted Energy Harvesting Wireless Physical Layer Cooperative Relaying Networks: Performance Analysis. Symmetry. 2020;12:106. doi: 10.3390/sym12010106. [DOI] [Google Scholar]
- 27.Nguyen T.N., Tran P.T., Vozňák M. Power splitting–based energy-harvesting protocol for wireless-powered communication networks with a bidirectional relay. Int. J. Commun. Syst. 2018;31:e3721. doi: 10.1002/dac.3721. [DOI] [Google Scholar]
- 28.Nguyen T.N., Tran M., Nguyen T.L., Ha D.H., Voznak M. Multisource Power Splitting Energy Harvesting Relaying Network in Half-Duplex System over Block Rayleigh Fading Channel: System Performance Analysis. Electronics. 2019;8:67. doi: 10.3390/electronics8010067. [DOI] [Google Scholar]
- 29.Liu X., Xu B., Wang X., Zheng K., Chi K., Tian X. Impacts of Sensing Energy and Data Availability on Throughput of Energy Harvesting Cognitive Radio Networks. IEEE Trans. Veh. Technol. 2023;72:747–759. doi: 10.1109/TVT.2022.3204310. [DOI] [Google Scholar]
- 30.Hou L., Tan S., Zhang Z., Bergmann N.W. Thermal energy harvesting WSNs node for temperature monitoring in IIoT. IEEE Access. 2018;6:35243–35249. doi: 10.1109/ACCESS.2018.2851203. [DOI] [Google Scholar]
- 31.Tin P.T., Nguyen T.N., Tran D.H., Voznak M., Phan V.D., Chatzinotas S. Performance Enhancement for Full-Duplex Relaying with Time-Switching-Based SWIPT in Wireless Sensors Networks. Sensors. 2021;21:3847. doi: 10.3390/s21113847. [DOI] [PMC free article] [PubMed] [Google Scholar]
- 32.Li X., Wang Q., Liu M., Li J., Peng H., Piran M.J., Li L. Cooperative Wireless-Powered NOMA Relaying for B5G IoT Networks With Hardware Impairments and Channel Estimation Errors. IEEE Internet Things J. 2021;8:5453–5467. doi: 10.1109/JIOT.2020.3029754. [DOI] [Google Scholar]
- 33.Zhang R., Ho C.K. MIMO broadcasting for simultaneous wireless information and power transfer. IEEE Trans. Wirel. Commun. 2013;12:1989–2001. doi: 10.1109/TWC.2013.031813.120224. [DOI] [Google Scholar]
- 34.Nguyen H.N., Dang H.P., Le S.P., Le T.D., Do D.T., Voznak M., Zdralek J. Enabling D2D transmission mode with energy harvesting and information transfer in heterogeneous networks. Adv. Electr. Electron. Eng. 2018;16:178–184. doi: 10.15598/aeee.v16i2.2393. [DOI] [Google Scholar]
- 35.Phan V.D., Nguyen T.L., Phu T.T., Nguyen V.V. Reliability-Security in Wireless-Powered Cooperative Network with Friendly Jammer. Adv. Electr. Electron. Eng. 2023;20:584–591. doi: 10.15598/aeee.v20i4.4511. [DOI] [Google Scholar]
- 36.Sun W., Song Q., Zhao J., Guo L., Jamalipour A. Adaptive Resource Allocation in SWIPT-Enabled Cognitive IoT Networks. IEEE Internet Things J. 2022;9:535–545. doi: 10.1109/JIOT.2021.3084472. [DOI] [Google Scholar]
- 37.Chen X., Yuen C., Zhang Z. Wireless energy and information transfer tradeoff for limited-feedback multiantenna systems with energy beamforming. IEEE Trans. Veh. Technol. 2013;63:407–412. doi: 10.1109/TVT.2013.2274800. [DOI] [Google Scholar]
- 38.Huynh T.P., Son P.N., Voznak M. Exact Throughput Analyses of Energy-Harvesting Cooperation Scheme with Best Relay Selections Under I/Q Imbalance. Adv. Electr. Electron. Eng. 2017;15:585–590. doi: 10.15598/aeee.v15i4.2302. [DOI] [Google Scholar]
- 39.Nguyen T.N., Duy T.T., Tran P.T., Voznak M. Performance evaluation of user selection protocols in random networks with energy harvesting and hardware impairments. Adv. Electr. Electron. Eng. 2016;14:372–377. doi: 10.15598/aeee.v14i4.1783. [DOI] [Google Scholar]
- 40.Pan G., Tang C., Li T., Chen Y. Secrecy performance analysis for SIMO simultaneous wireless information and power transfer systems. IEEE Trans. Commun. 2015;63:3423–3433. doi: 10.1109/TCOMM.2015.2458317. [DOI] [Google Scholar]
- 41.Feng R., Li Q., Zhang Q., Qin J. Robust secure transmission in MISO simultaneous wireless information and power transfer system. IEEE Trans. Veh. Technol. 2014;64:400–405. doi: 10.1109/TVT.2014.2322076. [DOI] [Google Scholar]
- 42.Wu W., Wang B. Efficient transmission solutions for MIMO wiretap channels with SWIPT. IEEE Commun. Lett. 2015;19:1548–1551. doi: 10.1109/LCOMM.2015.2451179. [DOI] [Google Scholar]
- 43.Al-Garadi M.A., Mohamed A., Al-Ali A.K., Du X., Ali I., Guizani M. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. IEEE Commun. Surv. Tutor. 2020;22:1646–1685. doi: 10.1109/COMST.2020.2988293. [DOI] [Google Scholar]
- 44.El Hammouti H., Ghogho M., Zaidi S.A.R. A machine learning approach to predicting coverage in random wireless networks; Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps); Abu Dhabi, United Arab Emirates. 9–13 December 2018; pp. 1–6. [Google Scholar]
- 45.Bao T., Zhu J., Yang H.C., Hasna M.O. Secrecy outage performance of ground-to-air communications with multiple aerial eavesdroppers and its deep learning evaluation. IEEE Wirel. Commun. Lett. 2020;9:1351–1355. doi: 10.1109/LWC.2020.2990337. [DOI] [Google Scholar]
- 46.Zheng K., Jia X., Chi K., Liu X. DDPG-Based Joint Time and Energy Management in Ambient Backscatter-Assisted Hybrid Underlay CRNs. IEEE Trans. Commun. 2023;71:441–456. doi: 10.1109/TCOMM.2022.3221422. [DOI] [Google Scholar]
- 47.Saman A., Nathan R., Yindi J., Malin P. Source-Based Jamming for Physical-Layer Security on Untrusted Full-Duplex Relay. IEEE Commun. Lett. 2019;23:842–846. [Google Scholar]
- 48.Pandey A., Yadav S. Physical layer security in cooperative amplify-and-forward relay networks over mixed Nakagami-m and double Nakagami-m fading channels: Performance evaluation and optimisation. IET Commun. 2020;14:95–104. doi: 10.1049/iet-com.2019.0584. [DOI] [Google Scholar]
- 49.Nguyen T.N., Tran D.H., Van Chien T., Phan V.D., Voznak M., Tin P.T., Chatzinotas S., Ng D.W.K., Poor H.V. Security–reliability tradeoff analysis for SWIPT-and AF-based IoT networks with friendly jammers. IEEE Internet Things J. 2022;9:21662–21675. doi: 10.1109/JIOT.2022.3182755. [DOI] [Google Scholar]
- 50.Nguyen T.N., Duy T.T., Tran P.T., Voznak M., Li X., Poor H.V. Partial and full relay selection algorithms for AF multi-relay full-duplex networks with self-energy recycling in non-identically distributed fading channels. IEEE Trans. Veh. Technol. 2022;71:6173–6188. doi: 10.1109/TVT.2022.3158340. [DOI] [Google Scholar]
- 51.Lee D. Secrecy Analysis of Relay-User Selection in AS-AF Systems Over Nakagami Fading Channels. IEEE Trans. Veh. Technol. 2021;70:2378–2388. doi: 10.1109/TVT.2021.3058262. [DOI] [Google Scholar]
- 52.Liu H., Kim K.J., Kwak K.S., Poor H.V. Power splitting-based SWIPT with decode-and-forward full-duplex relaying. IEEE Trans. Wirel. Commun. 2016;15:7561–7577. doi: 10.1109/TWC.2016.2604801. [DOI] [Google Scholar]
- 53.Gradshteyn I.S., Ryzhik I.M. Table of Integrals, Series, and Products. Academic Press; Cambridge, MA, USA: 2014. [Google Scholar]
- 54.Wei L., Wang K., Pan C., Elkashlan M. Secrecy Performance Analysis of RIS-Aided Communication System With Randomly Flying Eavesdroppers. IEEE Wirel. Commun. Lett. 2022;11:2240–2244. doi: 10.1109/LWC.2022.3198631. [DOI] [Google Scholar]
- 55.Li X., Zhao M., Liu Y., Li L., Ding Z., Nallanathan A. Secrecy Analysis of Ambient Backscatter NOMA Systems Under I/Q Imbalance. IEEE Trans. Veh. Technol. 2020;69:12286–12290. doi: 10.1109/TVT.2020.3006478. [DOI] [Google Scholar]
- 56.Nguyen T.N., Chien T.V., Tran D.H., Phan V.D., Voznak M., Chatzinotas S., Ding Z., Poor H.V. Security-Reliability Trade-Offs for Satellite-Terrestrial Relay Networks with a Friendly Jammer and Imperfect CSI. IEEE Trans. Aerosp. Electron. Syst. 2023:1–16. doi: 10.1109/TAES.2023.3282934. [DOI] [Google Scholar]
- 57.Vu T.H., Nguyen T.V., Kim S. Cooperative NOMA-Enabled SWIPT IoT Networks With Imperfect SIC: Performance Analysis and Deep Learning Evaluation. IEEE Internet Things J. 2022;9:2253–2266. doi: 10.1109/JIOT.2021.3091208. [DOI] [Google Scholar]
- 58.Clevert D.A., Unterthiner T., Hochreiter S. Fast and Accurate Deep Network Learning by Exponential Linear Units (ELUs) arXiv. 20161511.07289 [Google Scholar]
- 59.Kingma D.P., Ba J. Adam: A method for stochastic optimization. arXiv. 20141412.6980 [Google Scholar]
- 60.Van Chien T., Tu L.T., Chatzinotas S., Ottersten B. Coverage Probability and Ergodic Capacity of Intelligent Reflecting Surface-Enhanced Communication Systems. IEEE Commun. Lett. 2021;25:69–73. doi: 10.1109/LCOMM.2020.3023759. [DOI] [Google Scholar]
- 61.Hoang T.M., Huyen L.T.T., Tran X.N., Hiep P.T. Outage Probability of Aerial Base Station NOMA MIMO Wireless Communication With RF Energy Harvesting. IEEE Internet Things J. 2022;9:22874–22886. doi: 10.1109/JIOT.2022.3186065. [DOI] [Google Scholar]
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
Not applicable.